当前位置:网站首页>PAcP learning note 3: pcap method description
PAcP learning note 3: pcap method description
2022-07-07 13:08:00 【Mountain Ghost ballad me】
Create capture handle
pcap_open_live – Create sniff session
The task of creating sniffer sessions is very simple . So , We use pcap_open_live(3PCAP). The prototype of this function is as follows :
#include <pcap/pcap.h>
char errbuf[PCAP_ERRBUF_SIZE];
pcap_t *pcap_open_live(const char *device, int snaplen, int promisc, int to_ms, char *errbuf);
| Parameter fields | explain |
|---|---|
| The first parameter | The first parameter is the device we specified in the previous section . |
| The second parameter | snaplen It's an integer , It defines the pcap Maximum number of bytes captured . |
| The third parameter | promisc, When set to true when , Put the interface into hybrid mode ( However , Even if it is set to false, In certain circumstances , Interfaces may also be in hybrid mode , in any case ). |
| Fourth parameter | to_ms Is the read timeout in milliseconds ( value 0 Indicates that there is no timeout ; At least on some platforms , This means that you may have to wait until a sufficient number of packets arrive to see any packets , So you should use non-zero pause ) |
| Fifth parameter | ebuf Is a string , We can store any error messages in it ( Just like we use on it errbuf What we did ). |
| Return value | This function returns our session handler |
describe
pcap_open_live() Used to get the packet capture handle to view packets on the network . device Is a string , Specify the network device to open ; In possession of 2.2 Or higher version of the kernel Linux On the system , Equipment parameters “any” or NULL It can be used to capture packets from all interfaces .
snaplen Specify the snapshot length to set on the handle .
promisc Specify whether to put the interface in hybrid mode . If promisc Nonzero , Then set the hybrid mode , Otherwise, do not set .
Return value
pcap_open_live() Return on success pcap_t *, Return... On failure NULL. If you return NULL, be errbuf Appropriate error messages will be filled . When pcap_open_live() success ,errbuf It can also be set as warning text ; To test this , The caller should call pcap_open_live() The zero length string was previously stored in errbuf in , If errbuf No longer a zero length string , Then a warning is displayed to the user . hypothesis errbuf At least it can save PCAP_ERRBUF_SIZE character .
pcap_create - Create a real-time capture handle
#include <pcap/pcap.h>
char errbuf[PCAP_ERRBUF_SIZE];
pcap_t *pcap_create(const char *source, char *errbuf);
describe
pcap_create() Used to create a packet capture handle (handle) To view packets on the network . source Is a string , Specify the network device to open ; In possession of 2.2 Or higher version of the kernel Linux On the system , have access to “any” or NULL To capture packets from all interfaces .
The returned handle must be used first pcap_activate(3PCAP) Activate , Then you can use it to capture packets ; Captured options , For example, hybrid mode , Can be set on the handle before activation .
Return value
pcap_create() Return on success pcap_t *, Return... On failure NULL. If you return NULL, be errbuf Appropriate error messages will be filled . hypothesis errbuf At least it can save PCAP_ERRBUF_SIZE ( Set up your own ) character .
pcap_activate - Activate capture handle
explain
#include <pcap/pcap.h>
int pcap_activate(pcap_t *p);
describe
pcap_activate() Used to activate the packet capture handle to view packets on the network , And the options set on the handle take effect .
Return value
pcap_activate() Success without warning returns 0, Success with warning returns non 0 Comes at a time , Returns a negative value when an error occurs ; A non-zero return value indicates what warning or error condition has occurred .
Specific reference :https://www.tcpdump.org/manpages/pcap_activate.3pcap.html
Set the handle
compiler pcap_compile
To compile the program , We call pcap_compile(). The prototype defines it as :
int pcap_compile(pcap_t *p, struct bpf_program *fp, char *str, int optimize,
bpf_u_int32 netmask)
| Parameter field description | describe |
|---|---|
| The first parameter | The first parameter is our session handle (pcap_t *handle In our previous example ). |
| The second parameter | We will store The location reference of the compiled version of the filter . |
| The third parameter | Expression itself ; Format : Regular string |
| Fourth parameter | It's an integer , It determines whether the expression should “ Optimize ”(0 For false ,1 It's true —— Standard content ). |
| Fifth parameter | We must specify the netmask of the network to which the filter applies . |
| Return value | Failure to return -1, Other values are success |
catalog filter pcap_setfilter
After the expression is compiled , You can apply it . Input pcap_setfilter(). According to our explanation pcap The format of , Let's take a look at the prototype :
int pcap_setfilter(pcap_t *p, struct bpf_program *fp)
| Parameter description | describe |
|---|---|
| The first parameter | Our session handler |
| The second parameter | Is a reference to the compiled version of the expression ( Possible and pcap_compile() The second parameter of the same variable ) |
https://www.tcpdump.org/manpages/libpcap-1.10.1/pcap-filter.7.html
Actually grab packets through the handle
Packet capture function pcap_next
from pcap_t Read the next packet
Capture one packet at a time
# u_char *pcap_next(pcap_t *p, struct pcap_pkthdr *h)
const u_char *pcap_next(pcap_t *p, struct pcap_pkthdr *h);
| Specific description of parameters | explain |
|---|---|
| The first parameter | session handler |
| The second parameter | It's a pointer to the structure , This structure contains general information about packets , Especially when it was sniffed 、 The length of the packet and the length of the specific part ( for example , If it is segmented ). |
| Return value | Returns the u_char The pointer |
pcap_loop() – Process packets from real-time capture or save files
Into the loop
typedef void (*pcap_handler)(u_char *user, const struct pcap_pkthdr *h, const u_char *bytes);
int pcap_loop(pcap_t *p, int cnt, pcap_handler callback, u_char *user)
| Specific description of parameters | explain |
|---|---|
| The first parameter | The first parameter is our session handle |
| The second parameter | It's an integer , It tells pcap_loop() How many packets should it sniff before returning ( A negative value means that it should sniff until an error occurs ) |
| The third parameter | Is the name of the callback function ( Just its identifier , There are no brackets ) |
| Fourth parameter | The last parameter is useful in some applications , But many times it is simply set to NULL. Suppose that in addition to pcap_loop() Outside the parameters sent , We also have parameters we want to send to the callback function |
explain
pcap_loop() Processing comes from real-time capture or “ Save the file ” Data packets of , Until it's done cnt Data packets , from “ Save the file ” Arrive on read “ Save the file ” At the end of , call pcap_breakloop(3PCAP), Or something goes wrong . When the real-time packet buffer timeout occurs , It will not return . cnt Value -1 or 0 Equivalent to infinity , So packets will always be processed , Until another end condition appears .
In practice , When this method is called , Will enter the cycle , This loop is a loop of the local library , Because the interface is called synchronously , So I won't be stuck here all the time , Know the end of the cycle or throw exceptions .
pcap_dispatch()
pcap_dispatch() It's almost the same as pcap_loop identical . The only difference between these two functions is pcap_dispatch() Only the first packets it receives from the system will be processed , and pcap_loop() Will continue to process packets or bulk packets , Until the packet count runs out . A more in-depth discussion of the differences between them , Please refer to the manual page .
Get error messages
pcap_geterr, pcap_perror - Get or print libpcap Error message text
explain
#include <pcap/pcap.h>
char *pcap_geterr(pcap_t *p);
void pcap_perror(pcap_t *p, const char *prefix);
describe
pcap_geterr() Return to the last pcap Error text related to library error .
Be careful : In the pcap_t After closing , The pointer it returns will no longer point to a valid error message string ; You must close pcap_t Previously use or copy this string .
pcap_perror() stay stderr Print the last one on pcap Library error text , The prefix for prefix.
other
pcap_datalink - Get the link layer header type
explain
#include <pcap/pcap.h>
int pcap_datalink(pcap_t *p);
describe
pcap_datalink() Return from p Specified real-time capture or “ Save the file ” Link layer header type .
It can't be in pcap_create(3PCAP) Created pcap_activate(3PCAP) Not yet activated pcap Call on descriptor .
https://www.tcpdump.org/linktypes.html Lists pcap_datalink() Values that can be returned , And describes the packet format corresponding to these values .
Don't assume a given capture or “ Save the file ” The packet of will have any given link layer header type , For example, Ethernet DLT_EN10MB. for example ,Linux Upper “any” The device will have DLT_LINUX_SLL or DLT_LINUX_SLL2 Link layer header type , Even when opening “any” All devices on the system have some other data link types , for example DLT_EN10MB For Ethernet .
Return value
pcap_datalink() The link layer header type is returned when successful , If it is called on a capture handle that has been created but not activated, it will throw PCAP_ERROR_NOT_ACTIVATED.
Reference address :https://www.tcpdump.org/manpages/libpcap-1.10.1/pcap_datalink.3pcap.html
Reference address :
边栏推荐
- JS判断一个对象是否为空
- 2022-07-07 Daily: Ian Goodfellow, the inventor of Gan, officially joined deepmind
- JNA学习笔记一:概念
- 10 张图打开 CPU 缓存一致性的大门
- Cinnamon Applet 入门
- File operation command
- Sed of three swordsmen in text processing
- 非分区表转换成分区表以及注意事项
- Leetcode skimming: binary tree 21 (verifying binary search tree)
- 认养一头牛冲刺A股:拟募资18.5亿 徐晓波持股近40%
猜你喜欢
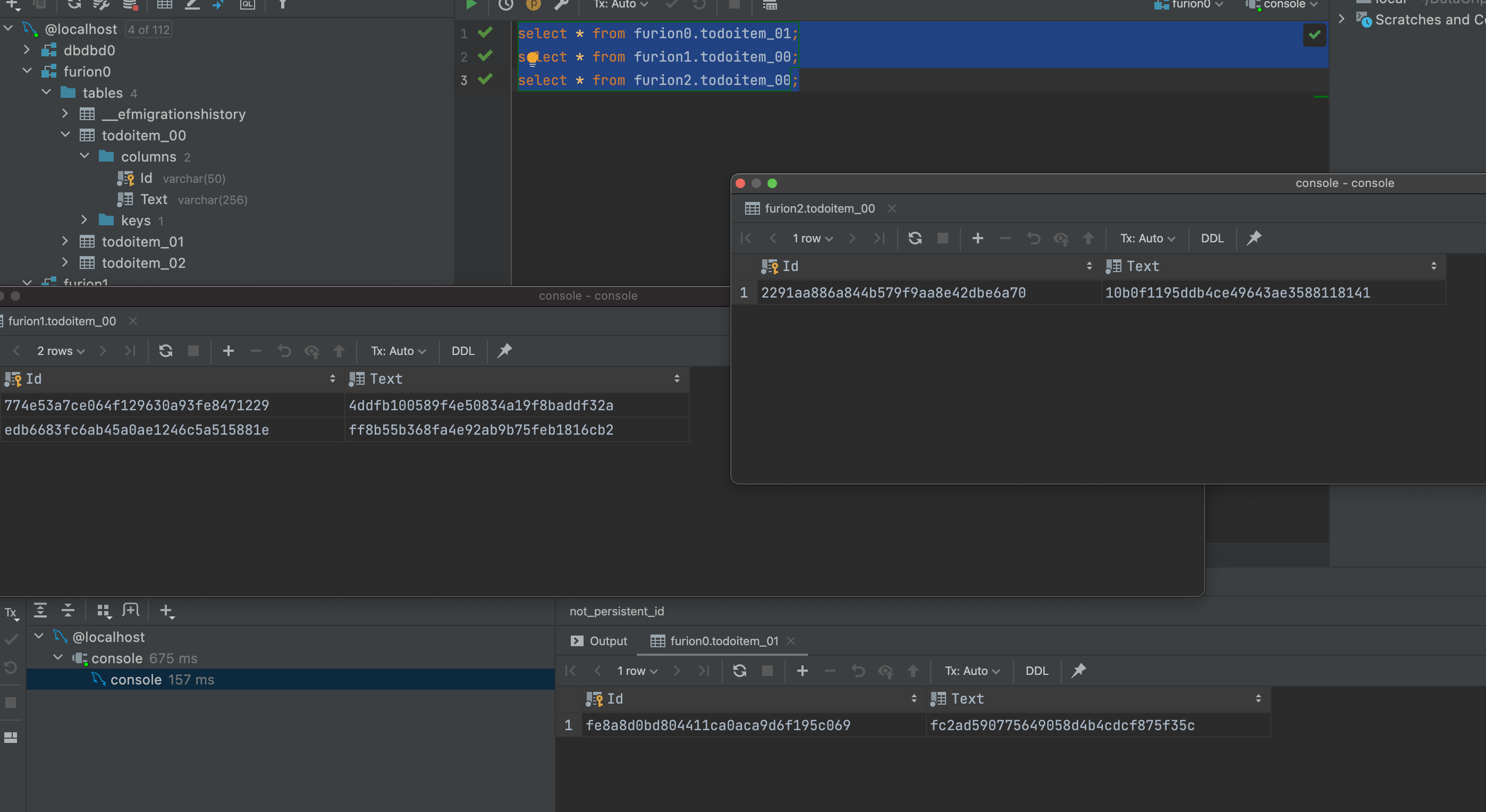
- Oui. Migration entièrement automatisée de la Sous - base de données des tableaux d'effets sous net

PACP学习笔记一:使用 PCAP 编程

Lingyunguang of Dachen and Xiaomi investment is listed: the market value is 15.3 billion, and the machine is implanted into the eyes and brain
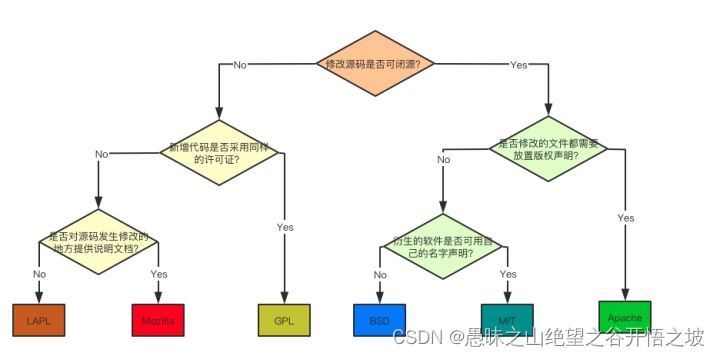
详细介绍六种开源协议(程序员须知)
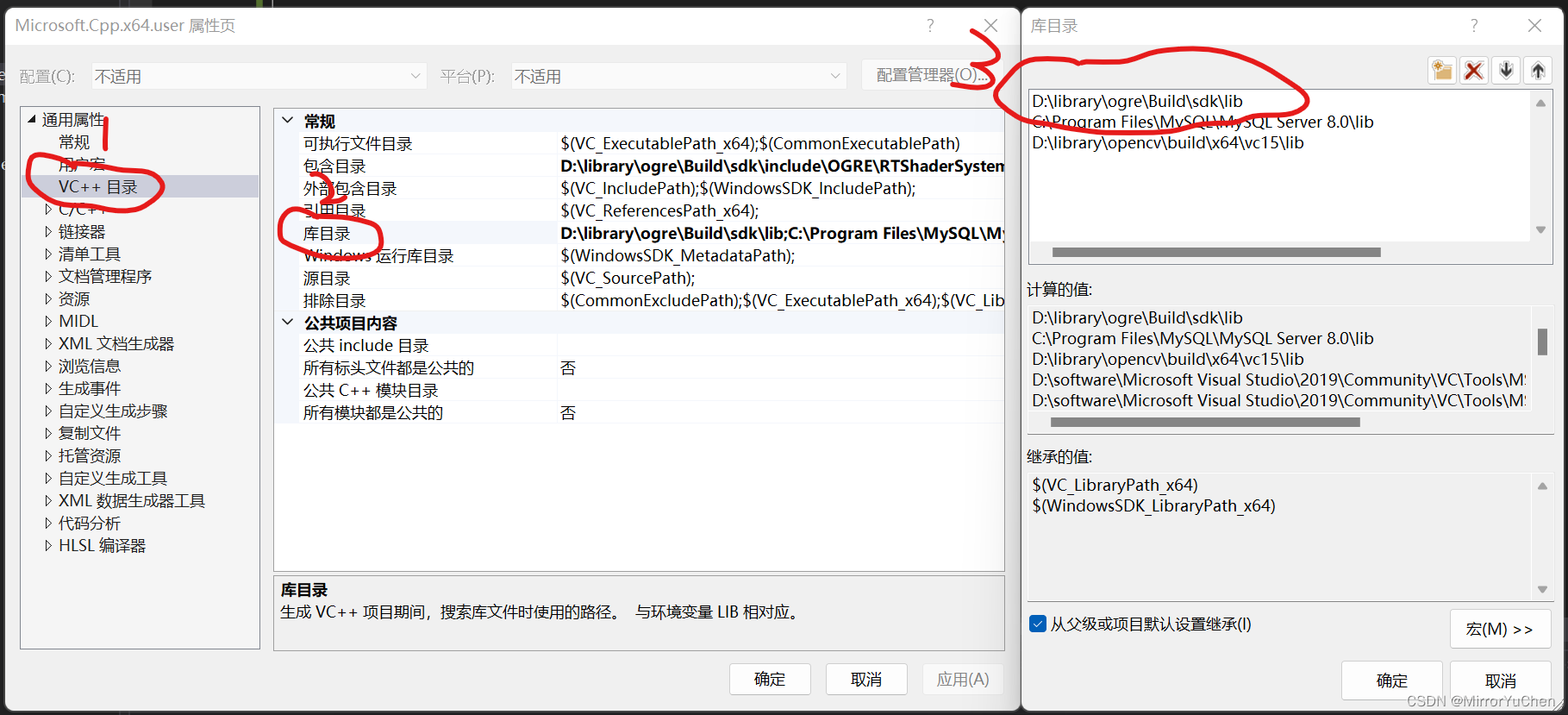
Ogre入门尝鲜

关于 appium 如何关闭 app (已解决)
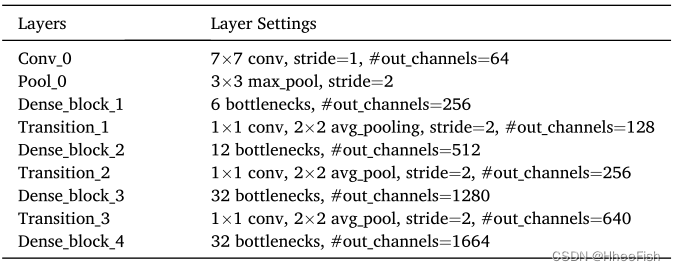
Isprs2021/ remote sensing image cloud detection: a geographic information driven method and a new large-scale remote sensing cloud / snow detection data set

Leetcode brush questions: binary tree 19 (merge binary tree)

共创软硬件协同生态:Graphcore IPU与百度飞桨的“联合提交”亮相MLPerf
智云健康上市:市值150亿港元 SIG经纬与京新基金是股东
随机推荐
. Net ultimate productivity of efcore sub table sub database fully automated migration codefirst
共创软硬件协同生态:Graphcore IPU与百度飞桨的“联合提交”亮相MLPerf
处理链中断后如何继续/子链出错removed from scheduling
Ogre入门尝鲜
JNA学习笔记一:概念
Creation and assignment of graphic objects
2022 polymerization process test question simulation test question bank and online simulation test
.Net下極限生產力之efcore分錶分庫全自動化遷移CodeFirst
AUTOCAD——大于180度的角度标注、CAD直径符号怎么输入?
ClickHouse(03)ClickHouse怎么安装和部署
Leetcode skimming: binary tree 20 (search in binary search tree)
JS中为什么基础数据类型可以调用方法
【Presto Profile系列】Timeline使用
How does MySQL create, delete, and view indexes?
“新红旗杯”桌面应用创意大赛2022
2022 examination questions and online simulation examination for safety production management personnel of hazardous chemical production units
MySQL master-slave replication
Leetcode brush question: binary tree 24 (the nearest common ancestor of binary tree)
Adopt a cow to sprint A shares: it plans to raise 1.85 billion yuan, and Xu Xiaobo holds nearly 40%
为租客提供帮助