当前位置:网站首页>Principle and configuration of RSTP protocol
Principle and configuration of RSTP protocol
2022-07-05 13:03:00 【Grey rain】
STP agreement ( Spanning tree protocol )
STP Although the protocol can solve the loop problem , But because the network topology converges slowly , It affects the quality of user communication , And if the topology of the network changes frequently , The network will also lose connectivity frequently , This leads to frequent interruption of user communication , This is what users can't stand .
because STP Deficiency ,IEEE On 2001 Published in 802.1w The standard defines RSTP.RSTP stay STP On this basis, many improvements and optimizations have been made , Make the agreement clearer 、 standard , At the same time, it also realizes the rapid convergence of the two-layer network topology .
STP Deficiency
When initialization and topology change
STP From the initial state to complete convergence, at least 30s( monitor → Study → forward )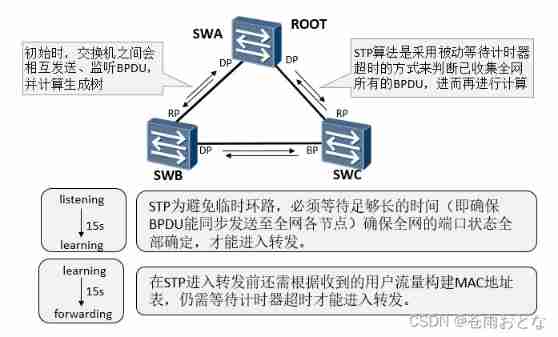
principle ( send out BPDU)
BPDU: Bridge protocol data unit
Specific parameters :root ID、COST( arrive root Cost value of )、 Bridge ID( priority +mac,4096 Multiple , The smaller the better. )、port ID( priority + Port number )
RSTP Of P/A Basic principle of mechanism
Proposal/Agreement Mechanism , The purpose is to make a designated port enter as soon as possible Forwarding state .
P/A The mechanism requires that the link between two switching devices must be in point-to-point full duplex mode . once P/A The negotiation failed , The choice of the specified port needs to wait for two Forward Delay, The negotiation process and STP equally .
In fact for STP, The selection of designated ports can be completed quickly , The main speed bottleneck is : To avoid loops , Have to wait long enough , Make the port status of the whole network all determined , That is to say, you have to wait for at least two Forward Delay, All ports can forward .
Icon 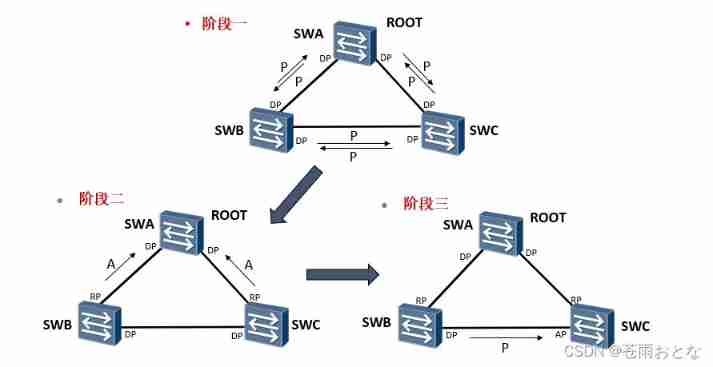
Stage 1 : The device has just started ,RSTP The protocol has just been enabled , All switches think of themselves as root bridges , Send... To other switches P In place BPDU, And send it to P The port of the message becomes DP mouth , At the same time, the interface is in Discarding state .
Stage two : Switch SWA received SWB and SWC Of P The news will be ignored , Because his bridge has the highest priority . Switch SWB and SWC received SWA Of P After the news , Because of recognition SWA Is the best root bridge , Will be based on P/A Negotiation process reply A news , And turn the sending port into RP port , At the same time, the interface is in Forwarding state .
Stage three :SWA And SWB,SWA And SWB Of P/A The negotiations have been completed , Next is SWB and SWC Of P/A negotiation .
SWB and SWC Will send the root bridge as SWA Of P Message to the other party .
SWC received SWB Of P After the news , Find out P In the news, although genqiao is the same as what he recognized , But the sender's bridge priority is higher than himself (SWB>SWC), All immediately stop sending P news , But because there are already ports RP mouth , Will not return A news .
SWB received SWC Of P After the news , Find out P In the news, although genqiao is the same as what he recognized , But the sender's bridge priority is lower than himself (SWB>SWC), Will keep sending P news .
The above status is waiting 2 individual Forward Delay After time ,SWB Port is DP port , be in Forwarding state , SWC Port is AP port , be in Discarding state .
actually SWB And SWC Negotiation between is equivalent to returning to STP The pattern of , But anyway Discarding state , It does not affect other business forwarding .
RSTP and STP
RSTP Election principles and STP Essentially the same : Election root switch - Select the root port on the non root switch - Select designated port - Select the standby port and backup port . however RSTP In the course of the election “ Initiate request - I agree with you ”(P/A Mechanism ) This confirmation mechanism , Since each step is confirmed, there is no need to rely on the timer to ensure that the network topology is acyclic before forwarding , Just think about it BPDU Send message and calculate the time of acyclic Topology ( It's usually in the order of seconds ).
P/A Synchronous blocking of mechanism
stay A Before , Block all other ports
Edge port : Not directly connected to any switch , It also does not connect with any switch indirectly through the network connected by the port
Configure the port as an edge port , Upon receipt of BPDU Will automatically give up
BPDU Protect
Application scenarios : Prevent people from forging RST BPDU Malicious attacks on switching devices , When the edge port receives the message , Will be automatically set to non edge port , And recalculate the spanning tree , Cause network shock .
Realization principle : To configure BPDU After the protection function , If the edge port receives BPDU message , The edge port will be closed immediately .
Root protection
Application scenarios : Due to the wrong configuration of maintenance personnel or malicious attacks in the network , The legitimate root bridge in the network may receive higher priority RST BPDU, Make the legal root bridge lose its root status , This causes the wrong change of network topology .
Realization principle : Once enabled Root The specified port of the protection function receives a higher priority RST BPDU when , The port status will enter Discarding state , No more forwarding . After a period of time , If the port has not received a higher priority RST BPDU, The port will automatically return to normal Forwarding state .
Root The protection function can only be configured and effective on the specified port .
TC-BPDU Attack protection
Turn on anti TC-BPDU After the message attack function , In unit time ,RSTP Process processing TC type BPDU The number of messages can be configured ( The default unit time is 2 second , The default processing times are 3 Time ). If in unit time ,RSTP Process receiving TC type BPDU The number of messages is greater than the configured threshold , that RSTP The process will only process the number of times specified by the threshold ; For others beyond the threshold TC type BPDU message , After the timer expires ,RSTP The process only processes it uniformly once . This can avoid frequent deletion MAC Address table entry , So as to achieve the purpose of protecting the switch .
Specific configuration
display stp brief // see stp Information
stp root primary // Set the primary root , The priority is automatically 0
stp root secondary // Set secondary root , The priority for 4096
stp priority xxxx // set priority
stp enable // Global on STP
stp mode rstp // To configure STP The model is RSTP
int g0/0/0
stp edged-port enable // Configure edge ports
stp edged-port default // All ports are edge ports
stp bpdu-protection // Global on BPDU protective , Use with edge ports , received bpdu Just shutdown
int g0/0/1
port link-type trunk
port trunk allow pass vlan 10
stp edgrd-port disable // Enable bpdu After protection, it is necessary to turn off other devices manually sw Edge port function of interconnection port
restart
int g0/0/3
stp root-protection // Protect the current root
experiment
HCIP experiment 01 RSTP Features and safety
This experiment simulates the redundant network environment , Complete the following configuration requirements :
1.SW1/2/3 It is the internal switch of the enterprise , Configure the name of each device as shown in the figure .
2. To configure VLAN, Requirements are as follows :
1)SW1/2/3 establish vlan10
2) take PC1 And PC2 Transfer in VLAN10, Use access link .
3)SW1/2/3 Between time trunk link , Only allowed vlan10 adopt .
3. To configure STP, Requirements are as follows :
1)SW1/2/3 Use RSTP
2) take SW1 Set to root bridge ,SW2 The device is set to secondary root , Not allowed priority Command configuration .
3) Use display stp brief Command to observe the port role and port status of the three switches .
4)SW2 And PC Configure edge ports for interconnected interfaces , Speed up convergence .
4.SW3 On the configuration STP Protection function , Requirements are as follows :
1)SW3 Enable the edge port function in the system view , Configure all ports as edge ports by default .
2)SW3 And SW1/2 The interconnected port turns off the edge port function , So as not to affect the communication between switches .
3) stay SW3 Global enable on bpdu Protection function , Prevent illegal switch access .
4) Open the illegal switch G0/0/1 Interface , see SW3 Port status of .
5. Use PC1 Long pingPC2, Then close it SW2 Of G0/0/1 mouth , Observe the link switching time .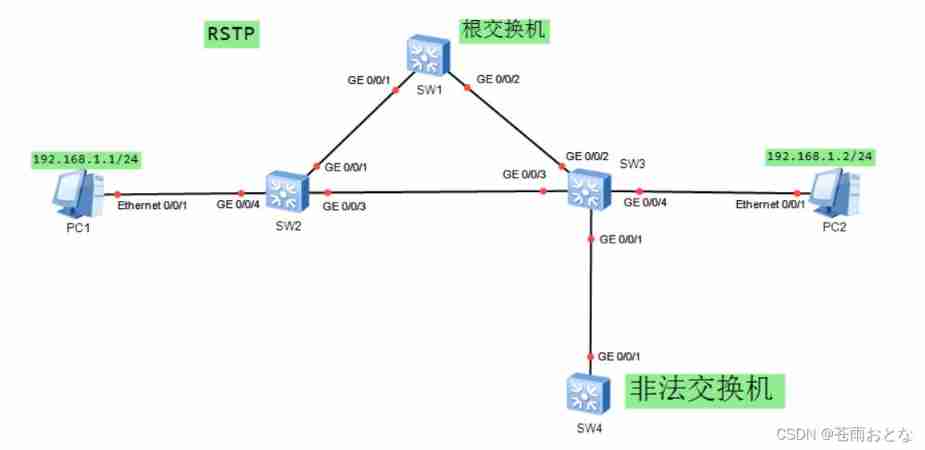
1.SW1/2/3 It is the internal switch of the enterprise , Configure the name of each device as shown in the figure .
A little
2. To configure VLAN, Requirements are as follows :
1)SW1/2/3 establish vlan10
[SW1]vlan batch 10
[SW2]vlan batch 10
[SW3]vlan batch 10
2) take PC1 And PC2 Transfer in VLAN10, Use access link .
[SW2]int g0/0/4
[SW2-GigabitEthernet0/0/4]port link-type access
[SW2-GigabitEthernet0/0/4]port default vlan 10
[SW3]int g0/0/4
[SW3-GigabitEthernet0/0/4]port link-type access
[SW3-GigabitEthernet0/0/4]port default vlan 10
3)SW1/2/3 Between time trunk link , Only allowed vlan10 adopt .
[SW1]int g0/0/1
[SW1-GigabitEthernet0/0/1]port link-type trunk
[SW1-GigabitEthernet0/0/1]port trunk allow-pass vlan 10
[SW1-GigabitEthernet0/0/1]int g0/0/2
[SW1-GigabitEthernet0/0/2] port link-type trunk
[SW1-GigabitEthernet0/0/2] port trunk allow-pass vlan 10
[SW2]int g0/0/1
[SW2-GigabitEthernet0/0/1]port link-type trunk
[SW2-GigabitEthernet0/0/1]port trunk allow-pass vlan 10
[SW2-GigabitEthernet0/0/1]int g0/0/2
[SW2-GigabitEthernet0/0/2] port link-type trunk
[SW2-GigabitEthernet0/0/2] port trunk allow-pass vlan 10
[SW3]int g0/0/2
[SW3-GigabitEthernet0/0/2]port link-type trunk
[SW3-GigabitEthernet0/0/2]port trunk allow-pass vlan 10
[SW3-GigabitEthernet0/0/2]int g0/0/3
[SW3-GigabitEthernet0/0/3] port link-type trunk
[SW3-GigabitEthernet0/0/3] port trunk allow-pass vlan 10
3. To configure STP, Requirements are as follows :
1)SW1/2/3 Use RSTP
[SW1]stp mode rstp
[SW2]stp mode rstp
[SW3]stp mode rstp
2) take SW1 Set to root bridge ,SW2 The device is set to secondary root , Not allowed priority Command configuration .
[SW1]stp root primary
[SW2]stp root secondary
3) Use display stp brief Command to observe the port role and port status of the three switches .
A little
4)SW2 And PC Configure edge ports for interconnected interfaces , Speed up convergence .
[SW2]int g0/0/4
[SW2-GigabitEthernet0/0/4]stp edged-port enable
4.SW3 On the configuration STP Protection function , Requirements are as follows :
1)SW3 Enable the edge port function in the system view , Configure all ports as edge ports by default .
[SW3]stp edged-port default
2)SW3 And SW1/2 The interconnected port turns off the edge port function , So as not to affect the communication between switches .
[SW3]int g0/0/2
[SW3-GigabitEthernet0/0/2]stp edged-port disable
[SW3-GigabitEthernet0/0/2]int g0/0/3
[SW3-GigabitEthernet0/0/3]stp edged-port disable
3) stay SW3 Global enable on bpdu Protection function , Prevent illegal switch access .
[SW3]stp bpdu-protection
4) Open the illegal switch G0/0/1 Interface , see SW3 Port status of .
[Huawei]int g0/0/1
[Huawei-GigabitEthernet0/0/1]undo shutdown \ Illegal switch interface is turned on
[SW3]display stp brief
MSTID Port Role STP State Protection
0 GigabitEthernet0/0/2 ROOT FORWARDING NONE
0 GigabitEthernet0/0/3 ALTE DISCARDING NONE
0 GigabitEthernet0/0/4 DESI FORWARDING BPDU
\ It is found that there is no connection to the illegal switch in the spanning tree G0/0/1 mouth
[SW3]int g0/0/1
[SW3-GigabitEthernet0/0/1]dis this
interface GigabitEthernet0/0/1
shutdown
\ Find out SW3 Of G0/0/1 Mouth automatic shutdown
5. Use PC1 Long pingPC2, Then close it SW2 Of G0/0/1 mouth , Observe the link switching time .
Solution strategy
( In particular , Because the simulator cannot perfectly simulate topology changes TC Caused by message mac Address table update , Therefore, the experiment will fail after switching ping common bug. need ctrl+c interrupt ping after , again ping, Or from PC2pingPC1 test .)
边栏推荐
猜你喜欢
深度长文探讨Join运算的简化和提速
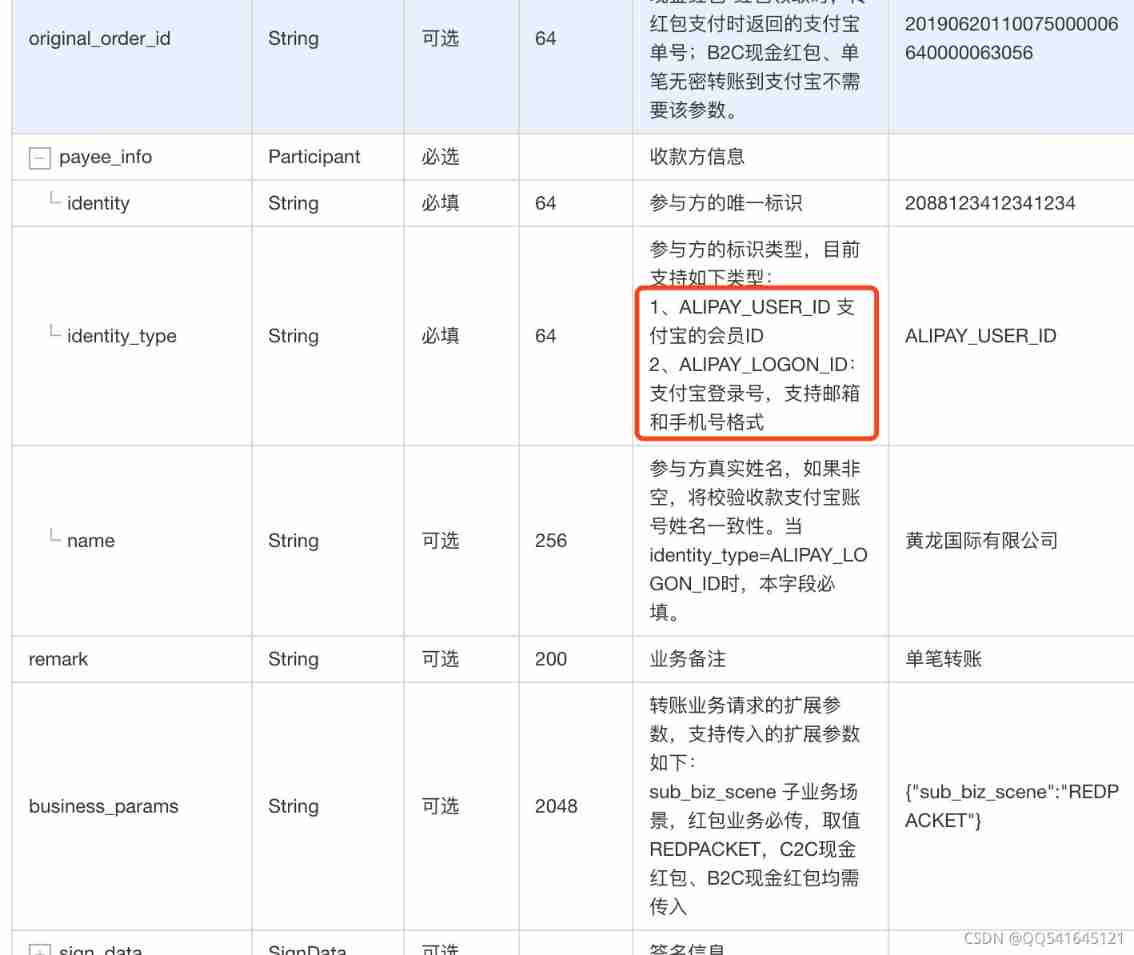
Alipay transfer system background or API interface to avoid pitfalls
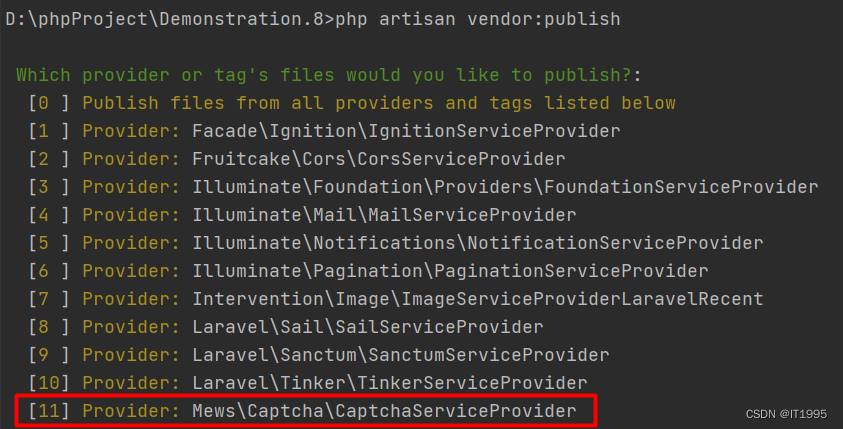
Laravel document reading notes -mews/captcha use (verification code function)

How to protect user privacy without password authentication?
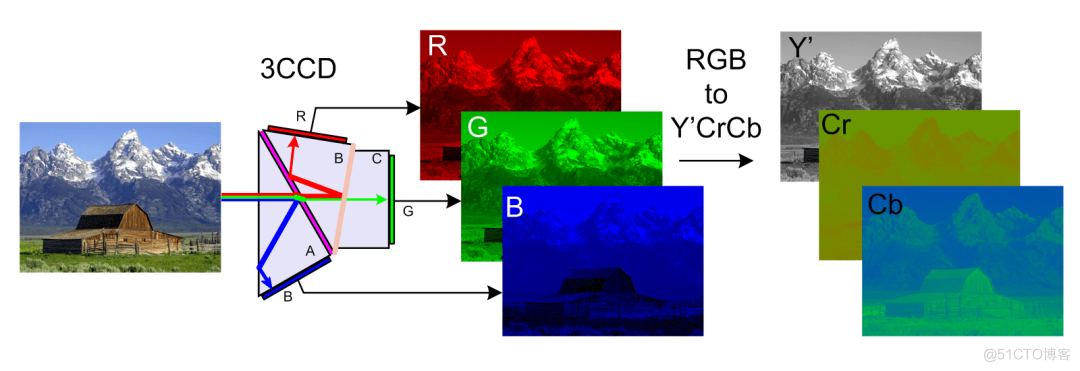
Lepton 无损压缩原理及性能分析
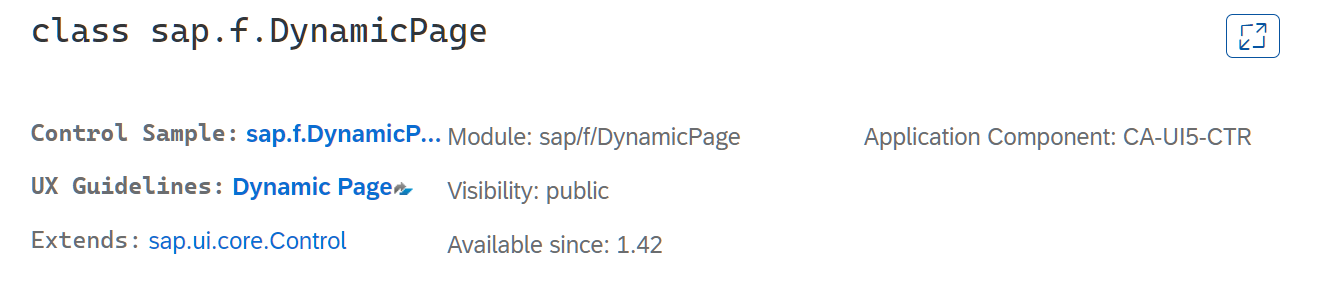
SAP UI5 DynamicPage 控件介绍
ABAP editor in SAP segw transaction code
解决 UnicodeDecodeError: ‘gbk‘ codec can‘t decode byte 0xa2 in position 107
2021-12-22 transaction record

太方便了,钉钉上就可完成代码发布审批啦!
随机推荐
CF:A. The Third Three Number Problem【关于我是位运算垃圾这个事情】
OpenHarmony应用开发之Navigation组件详解
DNS的原理介绍
2021.12.16-2021.12.20 empty four hand transaction records
滴滴开源DELTA:AI开发者可轻松训练自然语言模型
Simply take stock reading notes (3/8)
Taobao order interface | order flag remarks, may be the most stable and easy-to-use interface
Detailed explanation of navigation component of openharmony application development
2021-12-22 transaction record
stm32和电机开发(从架构图到文档编写)
Taobao product details API | get baby SKU, main map, evaluation and other API interfaces
stirring! 2022 open atom global open source summit registration is hot!
Alipay transfer system background or API interface to avoid pitfalls
《2022年中國銀行業RPA供應商實力矩陣分析》研究報告正式啟動
How do e-commerce sellers refund in batches?
SAP UI5 FlexibleColumnLayout 控件介绍
自然语言处理从小白到精通(四):用机器学习做中文邮件内容分类
Setting up sqli lab environment
非技术部门,如何参与 DevOps?
Four common problems of e-commerce sellers' refund and cash return, with solutions