当前位置:网站首页>NewH3C——ACL
NewH3C——ACL
2022-07-04 08:14:00 【AiY..】
One 、ACL Concept
1、acl Definition : Access control list ; Used for data flow matching and filtering
2、 function :
- Access control :ACL+Packet-filter
- Route control :ACL+Route-policy
- flow control :ACL+QOS
Two 、ACL Packet filtering
1、 Definition : Check the incoming and outgoing packets one by one , Discard or allow to pass ( By default, H3C equipment allows )
Be careful : Packet filtering must be configured in a certain direction of the interface to take effect ; Only one packet filtering policy can be configured in one direction of an interface
2、 Direction of packet filtering
- Into the direction (inbount): Only filter packets that enter from the outside
- Exit direction (outbount): Only the packets sent from inside are filtered
3、 Workflow of packet filtering ACL The workflow of is sequence matching , So assign a small range of rules to a top order
A word description :
1. When the packet arrives at the interface, check whether it is applied ACL, If yes, enter matching , Otherwise release
2. according to ACL The number matches the first rule , If matching, further check the rule action , Otherwise, match with the next rule ( Release if the action allows ; Action rejection is discarded )
3. Continue matching , If it matches, check the rule action , Otherwise, match with the next one
4. All the rules don't match , Check default actions
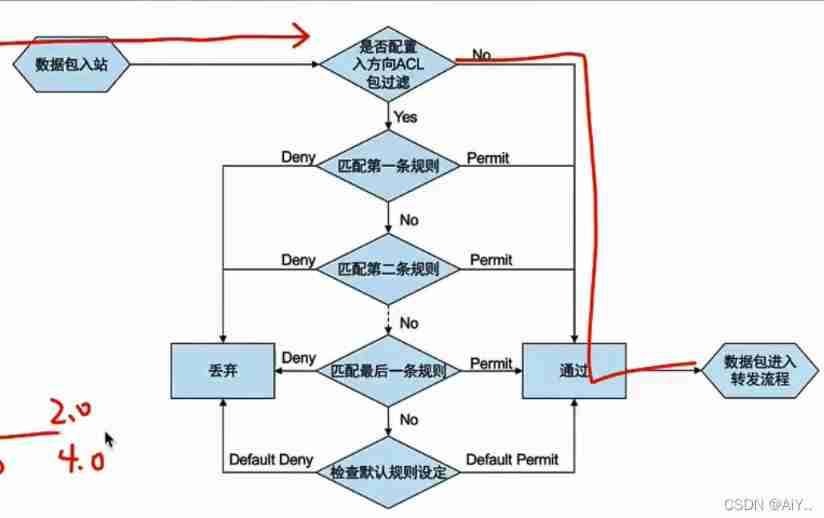
Package filtering workflow considerations
- If the default action is allow , At least one rejection rule is required ; If the default action is reject , At least one permission rule is required
- Without affecting the actual effect , Try to configure packet filtering in the incoming direction of the interface closest to the source address ( If placed in the out direction , The router has to be screened , Delay time )
4、ACL classification
(1) basic ACL:
For packets only source address Match ; For large-scale batch processing
Number 2000-2999
(2) senior ACL
Match the five tuples of the packet ( Source IP, Purpose IP, Source port , Destination port , agreement )
Number 3000-3999
3、 ... and 、ACL The experiment of
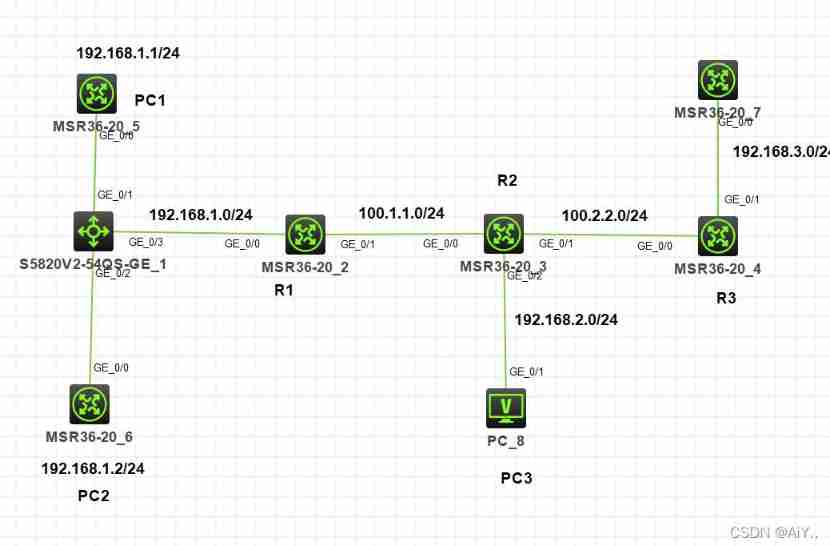
1、 The experimental requirements :
To configure ACL Achieve the following effect
192.168.1.0/24 The network segment is not allowed to access 192.168.2.0/24 Network segment , Basic ACL Realization PC1 You can visit SERVER1 Of TELNET service , But not accessible FTP service PC2 You can visit SERVER1 Of FTP service , But not accessible
TELNET service
192.168.2.0/24 The network segment is not allowed to access SERVER1, It is required to pass advanced ACL Realization
2、 The experimental steps
1、 To configure IP Address part
A little
2、R1,R2,R3 On the configuration RIP Make the routes of the whole network interconnected 
3、 stay SERVER1 Configuration on TELNET and FTP Service part 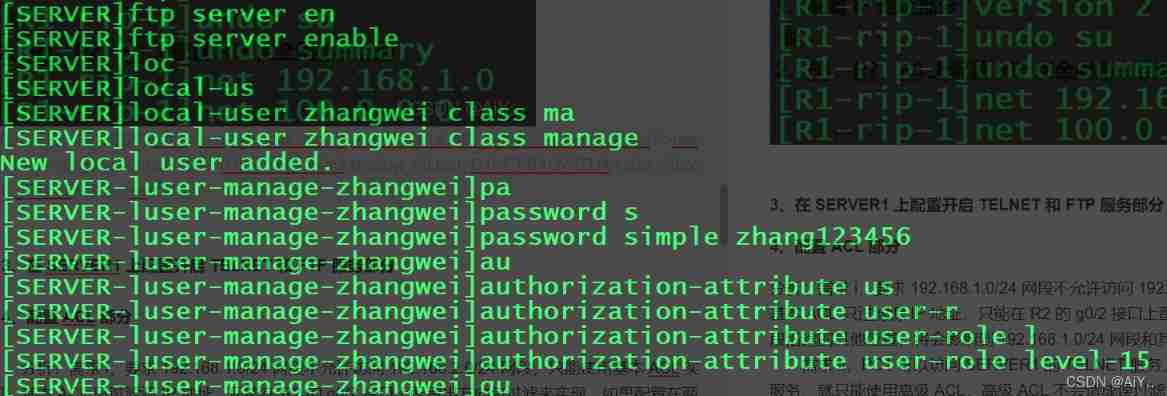
4、 To configure ACL part
analysis :
demand i, requirement 192.168.1.0/24 The network segment is not allowed to access 192.168.2.0/24 Network segment , Only basic ACL Realization . basic ACL Filter source only IP Address , Only in R2 Of g0/2 The interface is configured with directional packet filtering to realize . If it is configured in other locations along the two network segments , Will affect 192.168.1.0/24 Normal communication between network segment and other network segments
demand ii,PC1 You can visit SERVER1 Of TELNET service , But not accessible FTP service . Since you want to filter the specified services , You can only use advanced ACL, senior ACL Will not cause false filtering , So you can configure the input direction of the interface closest to the source address , That is to say R1 Of g0/1 The entry direction of the interface . in addition , because H3C Of ACL The default action for packet filtering is to allow , Therefore, no special configuration is required to allow PC1 visit SERVER1 Of TELNET, Just configure access denied FTP The rules can be
demand iii,PC2 You can visit SERVER1 Of FTP service , But not accessible TELNET service . Empathy , Only advanced ACL, Configure in R1 Of g0/1 The entry direction of the interface . And you only need to configure access denial TELNET The rules can be
Because of demand i And demand ii It is configured in the same direction of the same router and the same interface , So write the rules into the same ACL that will do
demand iv:192.168.2.0/24 The network segment is not allowed to access SERVER1, It is required to pass advanced ACL Realization . senior ACL Will not cause false filtering , So you can configure the input direction of the interface closest to the source address , That is to say R2 Of g0/2 The entry direction of the interface . in addition , There is no clear description of what services are not allowed to access , All are not allowed to access , So advanced ACL The protocol in needs to be specified as IP agreement
step 1: Create basic ACL, send 192.168.1.0/24 The network segment cannot be accessed 192.168.2.0/24 Network segment , And in R2 Of g0/2 Configure packet filtering in the outgoing direction of the interface
[R2]acl basic 2000
[R2-acl-ipv4-basic-2000]rule deny source 192.168.1.0 0.0.0.255
[R2]interface g0/2
[R2-GigabitEthernet0/2]packet-filter 2000 outbound
step 2: Create advanced ACL, send PC1 You can visit SERVER1 Of TELNET service , But not accessible FTP service ;PC2 You can visit SERVER1 Of FTP service , But not accessible TELNET service , And in R1 Of g0/1 Configure packet filtering in the input direction of the interface
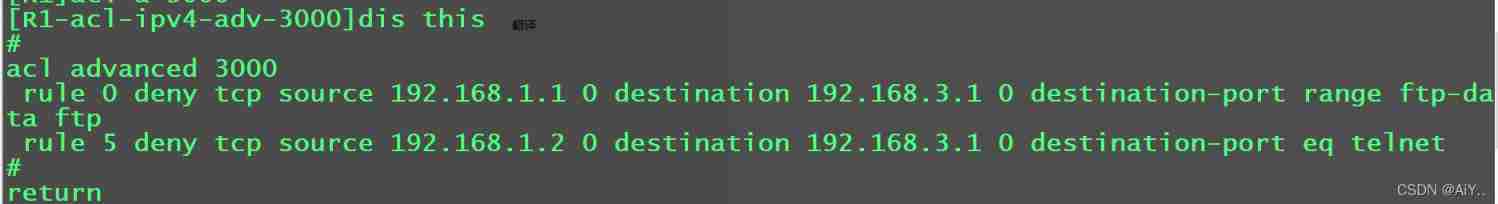
[R1]acl advanced 3000
[R1-acl-ipv4-adv-3000]rule deny tcp source 192.168.1.1 0 destination 192.168.3.1 0 destination-port range 20 21
[R1-acl-ipv4-adv-3000]rule deny tcp source 192.168.1.2 0 destination 192.168.3.1 0 destination-port eq 23
[R1]interface g0/1
[R1-GigabitEthernet0/1]packet-filter 3000 inbound
step 3: Create advanced ACL, send PC3 Cannot access SERVER1, And in R2 Of g0/2 Configure packet filtering in the input direction of the interface
[R2]acl advanced 3000
[R2-acl-ipv4-adv-3000]rule deny ip source 192.168.2.0 0.0.0.255 destination 192.168.3.1 0
[R2]interface g0/2
[R2-GigabitEthernet0/2]packet-filter 3000 inbound
5、 Effect test
step 1:PC1 and PC2 No way Ping through PC3
[PC1]ping 192.168.2.3
Ping 192.168.2.3 (192.168.2.3): 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
step 2:PC1 Can be connected SERVER1 Of TELNET, But you can't connect FTP
<PC1>telnet 192.168.3.1
Trying 192.168.3.1 ...
Press CTRL+K to abort
Connected to 192.168.3.1 ...
******************************************************************************
* Copyright (c) 2004-2017 New H3C Technologies Co., Ltd. All rights reserved.*
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
******************************************************************************
login:
<PC1>ftp 192.168.3.1
Press CTRL+C to abort.
step 3:PC2 Can be connected SERVER1 Of FTP, But you can't connect TELNET
<PC2>ftp 192.168.3.1
Press CTRL+C to abort.
Connected to 192.168.3.1 (192.168.3.1).
220 FTP service ready.
User (192.168.3.1:(none)):
<PC2>telnet 192.168.3.1
Trying 192.168.3.1 ...
Press CTRL+K to abort
Connected to 192.168.3.1 ...
step 4:PC3 You can't Ping through SERVER1
[PC3]ping 192.168.3.1
Ping 192.168.3.1 (192.168.2.3): 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
边栏推荐
- Conversion of yolov5 XML dataset to VOC dataset
- DM8 command line installation and database creation
- 【Go基础】1 - Go Go Go
- string. Format without decimal places will generate unexpected rounding - C #
- 一文了解數據异常值檢測方法
- 学习Nuxt.js
- Group programming ladder race - exercise set l1-006 continuity factor
- Convert datetime string to datetime - C in the original time zone
- 1. Kalman filter - the best linear filter
- Parallel shift does not provide any acceleration - C #
猜你喜欢
Fault analysis | MySQL: unique key constraint failure
Easy to understand: understand the time series database incluxdb

论文学习——基于极值点特征的时间序列相似性查询方法
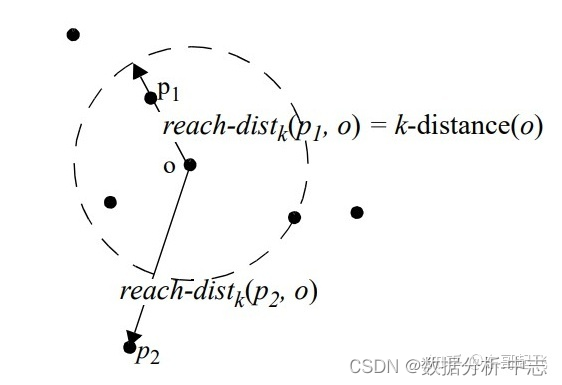
一文了解数据异常值检测方法
DM8 tablespace backup and recovery

弈柯莱生物冲刺科创板:年营收3.3亿 弘晖基金与淡马锡是股东
Practice (9-12 Lectures)

Ecole bio rushes to the scientific innovation board: the annual revenue is 330million. Honghui fund and Temasek are shareholders
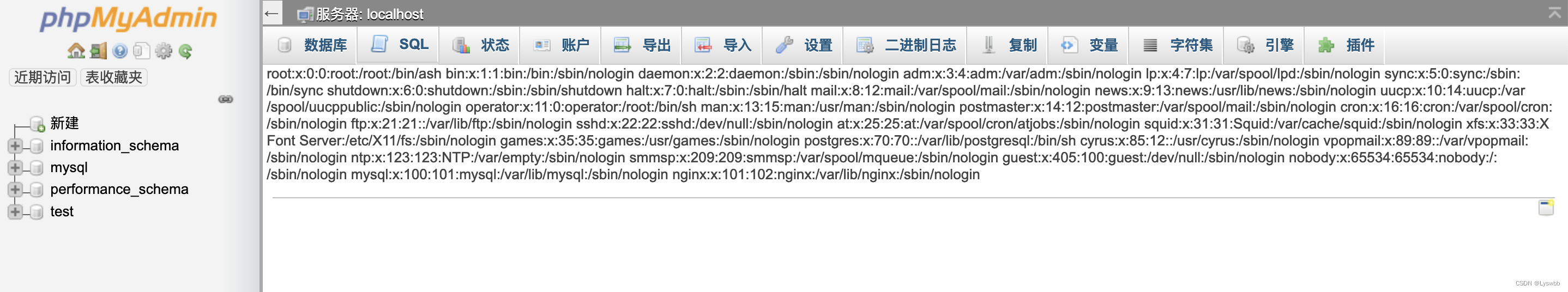
Moher college phpMyAdmin background file contains analysis traceability

Heap concept in JVM
随机推荐
Cannot click button when method is running - C #
Set and modify the page address bar icon favicon ico
DM8 database recovery based on point in time
1. Qt入门
Leetcode 146. LRU 缓存
L2-013 red alarm (C language) and relevant knowledge of parallel search
1. Kalman filter - the best linear filter
L1-030 one gang one (15 points)
ZABBIX monitoring system deployment
How to write a summary of the work to promote the implementation of OKR?
Go h*ck yourself:online reconnaissance (online reconnaissance)
Activiti常見操作數據錶關系
[Gurobi] 简单模型的建立
1、卡尔曼滤波-最佳的线性滤波器
Common components of flask
WordPress get_ Users() returns all users with comparison queries - PHP
Unity text superscript square representation +text judge whether the text is empty
时序数据库 InfluxDB 2.2 初探
Easy to understand: understand the time series database incluxdb
This article is enough for learning advanced mysql