当前位置:网站首页>Data flow diagram, data dictionary
Data flow diagram, data dictionary
2022-07-07 14:09:00 【sinat_ thirty-six million seven hundred and eighty-nine thousan】
Data flow diagram
One 、 Basic graphic symbols

Two 、 Design principles : We focus on three design principles of data flow graph . These three design principles are the magic weapon to solve problems .
1、 The balance principle of parent graph and child graph
The input and output data flow of the sub graph must be consistent with that of the corresponding processing of the parent graph , This is the balance between parent graph and child graph .
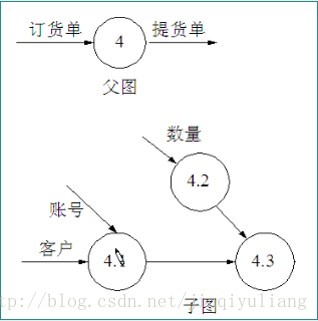
chart 1, It does not conform to the balance principle of parent graph and child graph
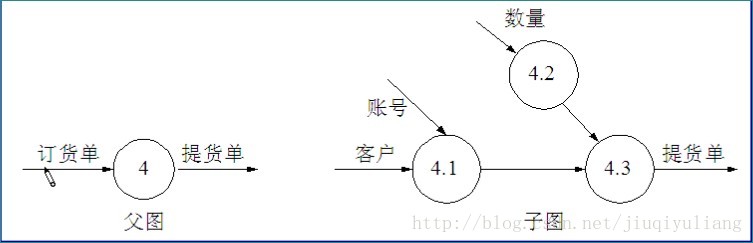
chart 2, Conform to the balance principle of parent graph and child graph
In the figure 1 in , We can see that there is an output stream in the parent graph : Bill of lading . But there is no corresponding output stream in the subgraph .
2、 The principle of data conservation
For any processing , The data in all output data streams must be directly obtained from the input data stream of the processing . Or the data that can be generated through the processing .
(1) There is no data flow between external entities

(2) There is no data flow between the external entity and the data store
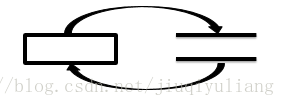
(3) There is no data flow between the data store and the data store

3、 Conservative processing principle
For the same process , The input and output names must be different . Even if their components are the same .
1. For each machining , There must be an existing input data stream . There is also an output data stream .
2. Data flow is related to processing , And must be processed .
For processing . Input is A, Output or A, It also violates the principle of data conservation , Input is the same as output , Processing has no effect .

For processing , Just input , No output , It violates the principle of data conservation .

For processing , Only output . No input , It violates the principle of data conservation . example . People cannot urinate and urinate all the time . But don't eat .

3、 ... and 、 After data flow processing , The relationship of data flow . Pictured :

The data dictionary
The data flow diagram describes the decomposition of the system . However, there is no description of the components in the figure . The data dictionary defines all named graphic elements appearing in the data flow graph as an entry in the data dictionary , Make the name of each graphic element have an exact explanation .

In the data dictionary 4 Types of entries :
1、 Data item entry : Usually the value type of the data item , Agreed value range, etc
2、 data flow : Give the definition of a data flow , List the constituent data items of the data flow .
3、 File entry : Definition of file . List the data items composed of periods
4、 Processing items : Explain every process that cannot be decomposed . Including the excitation conditions of processing . The logic of processing , Priority, etc .
application
Let me look at a multiple-choice question , This question can fully reflect all the above principles . be the leading example of . 
Let's analyze it . It's nothing more than those three principles : According to these principles .DF2 It violates the principle of data conservation , There is no data flow between external entities ,DF6 It violates the principle of data conservation , There is no data flow between the external entity and the data store ,DF7 It violates the principle of data conservation . There is no data flow between the data store and the data store ;P1 and P3 Lack of data flow . It violates the principle of conservative processing ,P4 The input and output data flow is the same . It violates the principle of conservative processing . So jointly owned 6 A mistake .
边栏推荐
- Es log error appreciation -limit of total fields
- Cesium knows the longitude and latitude of one point and the distance to find the longitude and latitude of another point
- The meaning of variables starting with underscores in PHP
- requires php ~7.1 -> your PHP version (7.0.18) does not satisfy that requirement
- Vmware共享主机的有线网络IP地址
- [1] Basic knowledge of ros2 - summary version of operation commands
- Is it safe to open an account online now? Which securities company should I choose to open an account online?
- 2022-7-7 Leetcode 34. Find the first and last positions of elements in a sorted array
- 现在网上开户安全么?那么网上开户选哪个证券公司?
- gvim【三】【_vimrc配置】
猜你喜欢
Hands on Teaching: XML modeling
最佳实践 | 用腾讯云AI意愿核身为电话合规保驾护航
118. Yanghui triangle

Help tenants
Wired network IP address of VMware shared host

Sliding rail stepping motor commissioning (national ocean vehicle competition) (STM32 master control)
.net core 关于redis的pipeline以及事务

作战图鉴:12大场景详述容器安全建设要求
![Supply chain supply and demand estimation - [time series]](/img/2c/82d118cfbcef4498998298dd3844b1.png)
Supply chain supply and demand estimation - [time series]

Battle Atlas: 12 scenarios detailing the requirements for container safety construction
随机推荐
2022-7-6 使用SIGURG来接受外带数据,不知道为什么打印不出来
ES日志报错赏析-Limit of total fields
118. 杨辉三角
How does MySQL control the number of replace?
Excellent open source system recommendation of ThinkPHP framework
现在网上开户安全么?那么网上开户选哪个证券公司?
Excuse me, I have three partitions in Kafka, and the flinksql task has written the join operation. How can I give the join operation alone
c#通过frame 和 page 切换页面
[fortress machine] what is the difference between cloud fortress machine and ordinary fortress machine?
请问,PTS对数据库压测有好方案么?
mysql导入文件出现Data truncated for column ‘xxx’ at row 1的原因
3D detection: fast visualization of 3D box and point cloud
Excuse me, as shown in the figure, the python cloud function prompt uses the pymysql module. What's the matter?
Wired network IP address of VMware shared host
Excuse me, when using Flink SQL sink data to Kafka, the execution is successful, but there is no number in Kafka
请问,如图,pyhon云函数提示使用了 pymysql模块,这个是怎么回事?
AI人才培育新思路,这场直播有你关心的
Laravel5 call to undefined function OpenSSL cipher IV length() error php7 failed to open OpenSSL extension
作战图鉴:12大场景详述容器安全建设要求
The difference between memory overflow and memory leak