当前位置:网站首页>Leetcode 1380. Lucky numbers in the matrix (save the minimum number of each row and the maximum number of each column)
Leetcode 1380. Lucky numbers in the matrix (save the minimum number of each row and the maximum number of each column)
2022-07-01 17:51:00 【wwxy261】

Note that all numbers are different , So there is no need to use index to judge
class Solution {
public:
vector<int> luckyNumbers (vector<vector<int>>& matrix) {
int m = matrix.size(), n = matrix[0].size();
vector<int> minRow(m, INT_MAX), maxCol(n);
for (int i = 0; i < m; i++) {
for (int j = 0; j < n; j++) {
minRow[i] = min(minRow[i], matrix[i][j]);
maxCol[j] = max(maxCol[j], matrix[i][j]);
}
}
vector<int> ans;
for (int i = 0; i < m; i++) {
for (int j = 0; j < n; j++) {
if (matrix[i][j] == minRow[i] && matrix[i][j] == maxCol[j]) {
ans.emplace_back(matrix[i][j]);
}
}
}
return ans;
}
};边栏推荐
- vulnhub靶场-Hacker_Kid-v1.0.1
- Unity3d extended toolbar
- Sword finger offer 20 String representing numeric value
- Enter wechat applet
- Is it reasonable and safe to open a securities account for 10000 shares free of charge? How to say
- How to write good code - Defensive Programming Guide
- 中国一次性卫生用品生产设备行业深度调研报告(2022版)
- 目前炒期货在哪里开户最正规安全?怎么期货开户?
- Glidefast consulting was selected as the elite partner of servicenow in 2022
- JDBC: deep understanding of Preparedstatement and statement[easy to understand]
猜你喜欢
(17) DAC conversion experiment

(28) Shape matching based on contour features

An example of data analysis of an old swatch and an old hard disk disassembly and assembly combined with the sensor of an electromagnetic press
【Try to Hack】vulnhub DC4
Setting up a time server requires the client to automatically synchronize the time of the server at 9 a.m. every day

官宣!香港科技大学(广州)获批!

Wechat applet blind box - docking wechat payment
![Integer array merge [JS]](/img/0d/70535e0eb1c299bda25159b58c70d7.png)
Integer array merge [JS]
Apache iceberg source code analysis: schema evolution
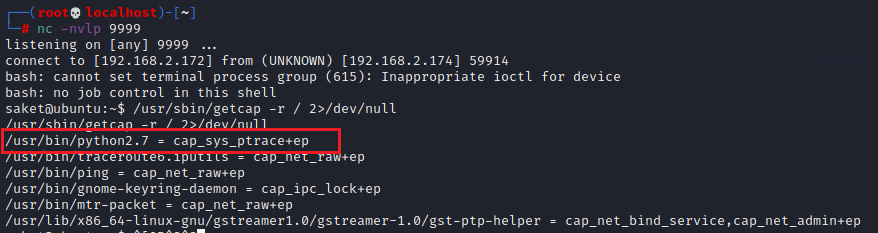
Vulnhub range hacker_ Kid-v1.0.1
随机推荐
Equipment simulation and deduction training system software
How to use JMeter function and mockjs function in metersphere interface test
In aks, use secret in CSI driver mount key vault
String的trim()和substring()详解
China metallocene polyethylene (MPE) Industry Research Report (2022 Edition)
传感器尺寸、像素、DPI分辨率、英寸、毫米的关系
徽商期货是正规期货平台吗?在徽商期货开户安全吗?
China acetonitrile market forecast and strategic consulting research report (2022 Edition)
线上开通ETF基金账户安全吗?有哪些步骤?
Redis主从实现10秒检查与恢复
Research Report on development prediction and investment direction of nylon filament sewing thread in China (2022 Edition)
Openlayers customize bubble boxes and navigate to bubble boxes
Oom caused by improper use of multithreading
China PBAT resin Market Forecast and Strategic Research Report (2022 Edition)
剑指 Offer 20. 表示数值的字符串
Zabbix报警执行远程命令
New patent applications and transfers
两数之和c语言实现[通俗易懂]
(27) Open operation, close operation, morphological gradient, top hat, black hat
开发那些事儿:EasyCVR平台添加播放地址鉴权