当前位置:网站首页>The difference between memory overflow and memory leak
The difference between memory overflow and memory leak
2022-07-07 13:51:00 【Full stack programmer webmaster】
out of memory out of memory, When a program requests memory , Not enough memory for it , appear out of memory; Like applying for a integer, But save it long Number that can be saved , That's memory overflow .
Memory leak memory leak, Refers to the program after applying for memory , Unable to free requested memory space , The harm of a memory leak can be ignored , But the memory leak has serious consequences , No matter how much memory , Sooner or later it will be taken up .
memory leak Will eventually lead to out of memory!
Memory overflow is when you ask for more memory than the system can give you , The system can't meet the demand , So there's overflow .
A memory leak is when you apply to the system to allocate memory for use (new), But they don't return it after using it (delete), As a result, you can't access the memory you applied for ( Maybe you lost its address ), And the system can't assign it again to the program it needs . A plate can only hold 4 A fruit , You put on 5 individual , As a result, I fell to the ground and couldn't eat . This is overflow ! Like stacks , When the stack is full, it will cause space overflow , Call for overflow , When the stack is empty, it will cause space overflow , It's called underflow . The memory allocated is not enough to put down the sequence of data items , It's called a memory overflow .
Classify in the way that they happen , Memory leaks can be divided into 4 class :
1. Frequent memory leaks . Code with memory leaks will be executed multiple times to , Each time it is executed, it will cause a memory leak . 2. Occasional memory leak . Code that has a memory leak only happens under certain circumstances or operating procedures . Recurrent and episodic are relative . For a particular environment , What happens occasionally may become what happens frequently . So test environment and test method are very important to detect memory leak . 3. One time memory leak . Code with a memory leak will only be executed once , Or because of algorithm flaws , There will always be a single memory leak . such as , Allocate memory in the class's constructor , In the destructor, the memory is not freed , So memory leaks only happen once . 4. Implicit memory leaks . Program in the process of running the allocation of memory , But don't release memory until the end . Strictly speaking, there is no memory leak , Because eventually the program frees up all of the requested memory . But for a server program , It takes a few days to run , Weeks or even months , Not releasing memory in time can also lead to the eventual exhaustion of all the system's memory . therefore , We call such memory leaks implicit memory leaks .
From the point of view of the user using the program , Memory leaks themselves don't do any harm , As a general user , There is no memory leak at all . The real danger is the accumulation of memory leaks , This will eventually consume all the memory of the system . From this perspective , One time memory leaks don't hurt , Because it doesn't pile up , The implicit memory leak is very harmful , Because it is more difficult to detect than frequent and accidental memory leaks
Focus on the following points : 1. Check the database query , Is there a query to get all the data . Generally speaking , If you take 100000 records to memory at a time , May cause memory overflow . This problem is more hidden , Before going online , There is less data in the database , It's not easy to have problems , After the launch , There's a lot of data in the database , A query may cause memory overflow . So for Try to query the database by paging .
2. Check the code for dead loops or recursive calls .
3. Check if there is a large loop that repeatedly generates new object entities .
4. Check the database query , Is there a query to get all the data . Generally speaking , If you take 100000 records to memory at a time , May cause memory overflow . This problem is more hidden , Before going online , There is less data in the database , It's not easy to have problems , After the launch , There's a lot of data in the database , A query may cause memory overflow . Therefore, the database query should be paged as much as possible .
5. Check List、MAP Wait until the collection object is used , Problems not cleared .List、MAP The collection object will always have a reference to the object , So that these objects cannot be GC Recycling .
Step four , Use the memory view tool to dynamically view memory usage
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/113287.html Link to the original text :https://javaforall.cn
边栏推荐
- Custom thread pool rejection policy
- Esp32 series column
- 实现IP地址归属地显示功能、号码归属地查询
- 2022-7-6 初学redis(一)在 Linux 下下载安装并运行 redis
- call undefined function openssl_cipher_iv_length
- 干货|总结那些漏洞工具的联动使用
- Realize the IP address home display function and number home query
- 《厌女:日本的女性嫌恶》摘录
- Help tenants
- 社会责任·价值共创,中关村网络安全与信息化产业联盟对话网信企业家海泰方圆董事长姜海舟先生
猜你喜欢
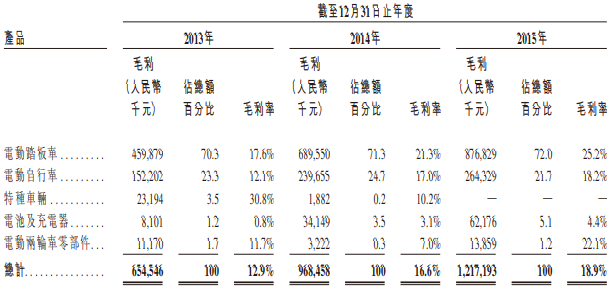
High end for 8 years, how is Yadi now?
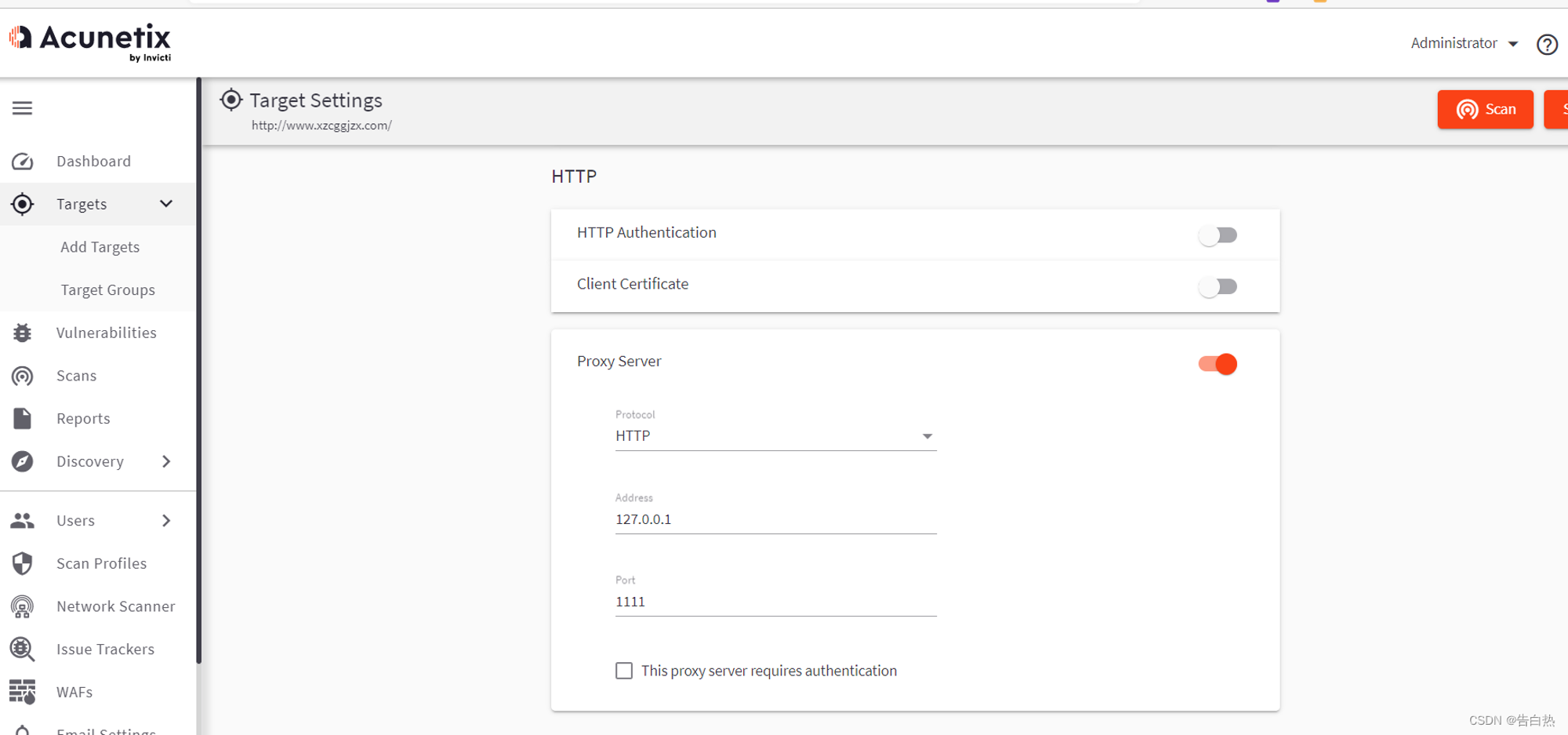
Dry goods | summarize the linkage use of those vulnerability tools
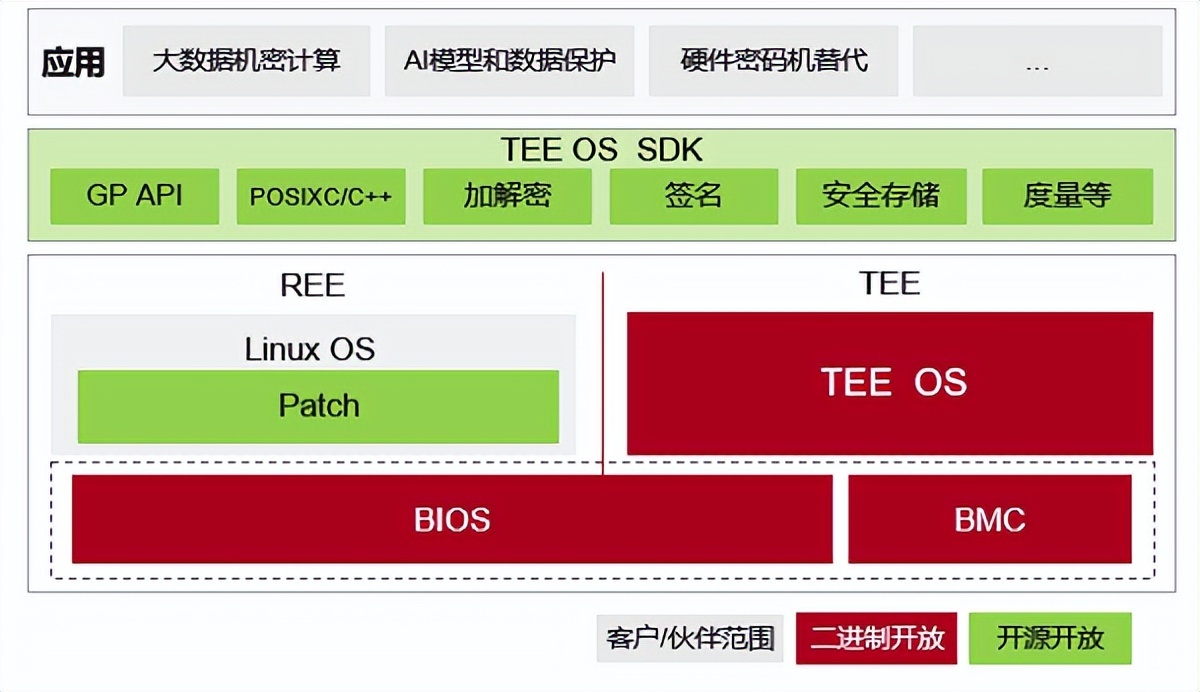
Build a secure and trusted computing platform based on Kunpeng's native security
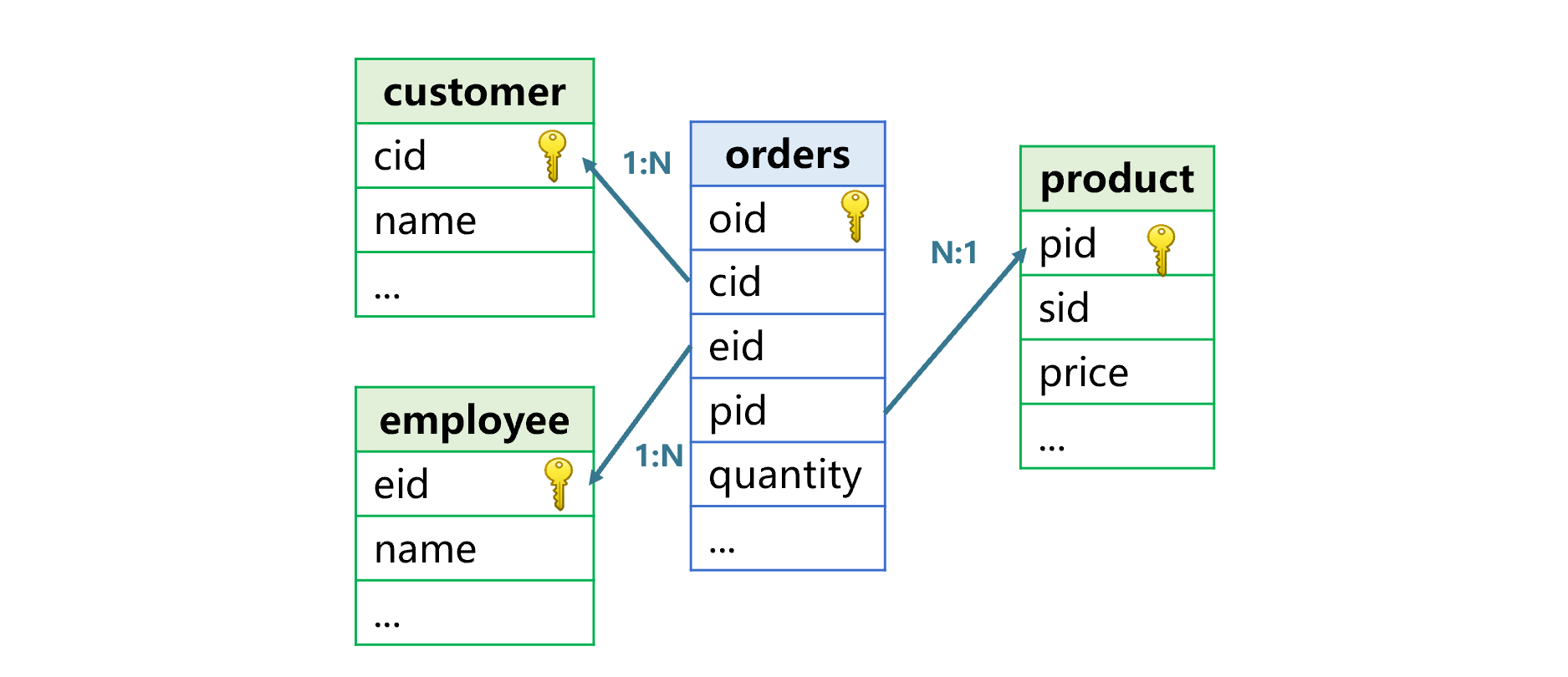
如何让join跑得更快?
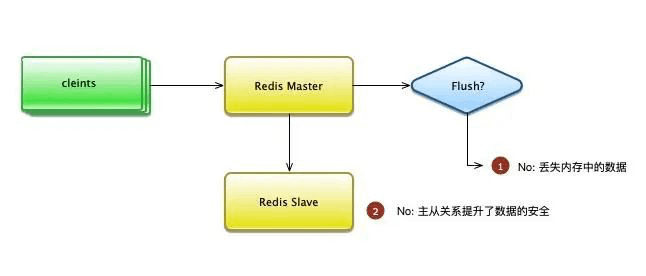
Redis can only cache? Too out!
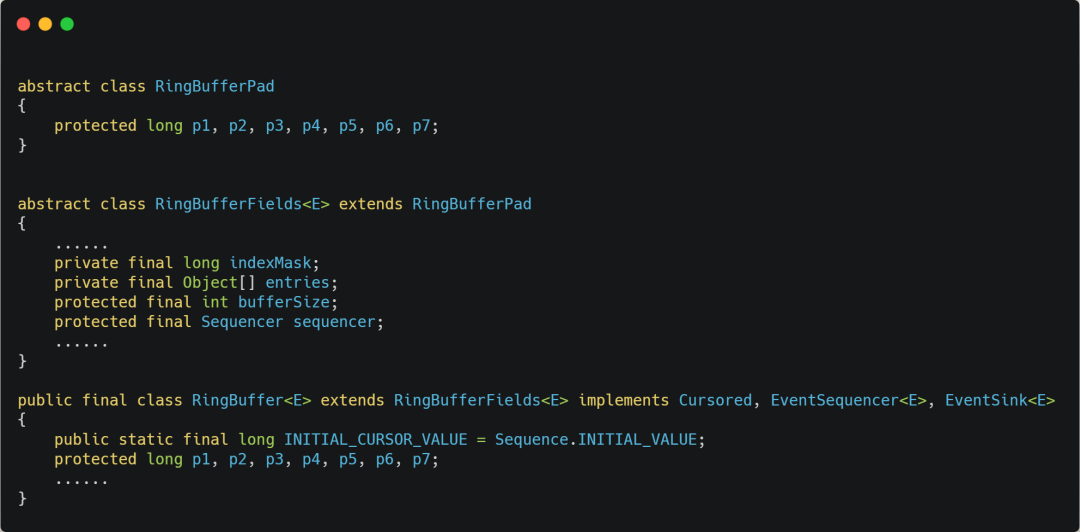
Talk about pseudo sharing

高等數學---第八章多元函數微分學1
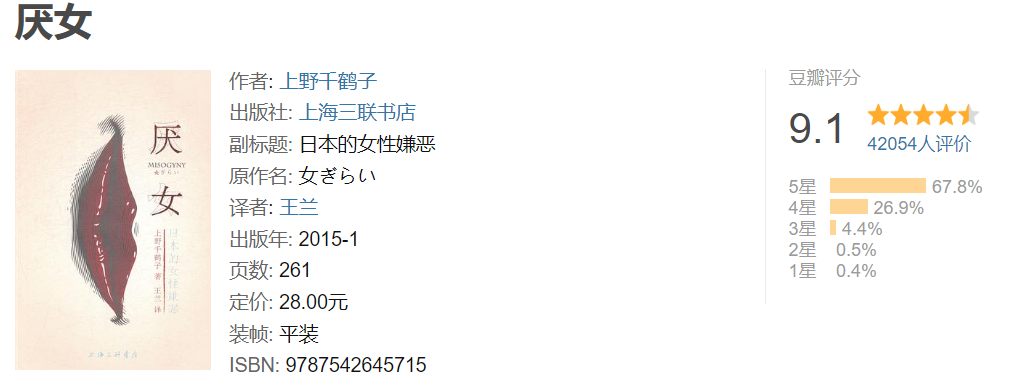
《厌女:日本的女性嫌恶》摘录
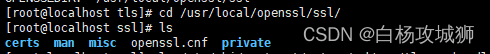
Centso7 OpenSSL error Verify return code: 20 (unable to get local issuer certificate)
Navicat run SQL file import data incomplete or import failed
随机推荐
接口自动化测试-接口间数据依赖问题解决
Best practice | using Tencent cloud AI willingness to audit as the escort of telephone compliance
【面试高频题】难度 2.5/5,简单结合 DFS 的 Trie 模板级运用题
C语言数组相关问题深度理解
ROS机器人更换新雷达需要重新配置哪些参数
Navicat运行sql文件导入数据不全或导入失败
Lavarel之环境配置 .env
《厌女:日本的女性嫌恶》摘录
Huawei image address
[1] Basic knowledge of ros2 - summary version of operation commands
[fortress machine] what is the difference between cloud fortress machine and ordinary fortress machine?
648. 单词替换 : 字典树的经典运用
118. Yanghui triangle
得物客服热线的演进之路
[daily training] 648 Word replacement
带你掌握三层架构(建议收藏)
Read PG in data warehouse in one article_ stat
Learning breakout 2 - about effective learning methods
Redis 核心数据结构 & Redis 6 新特性详
LeetCode_二分搜索_中等_153.寻找旋转排序数组中的最小值