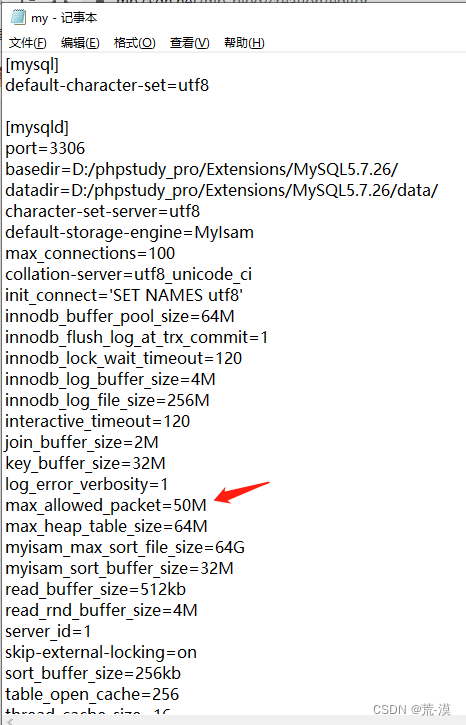
More and more enterprises begin to adopt containerized cloud native applications , From the first container application development to the process of managing thousands of containers , Security needs are also changing . therefore , Enterprises in different application stages need a clear battle map , Indicates that in the process of containerization , How to do a good job in safety construction at all stages . The following is the best battle map and solution summarized by enterprises in different application stages in actual combat , To find the safety requirements of containers in different stages .
12 Large scene container safety operation atlas
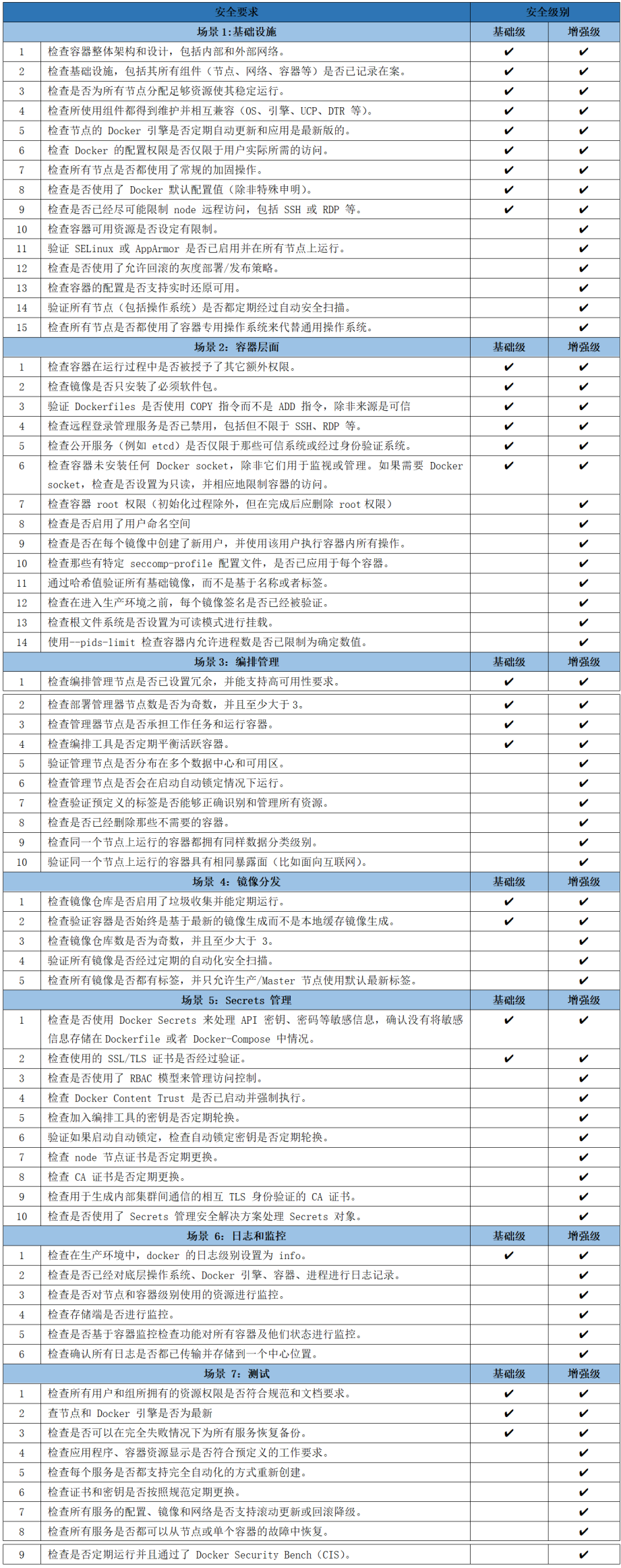

One stop container security solution
The enterprise security requirements battle map for the different containerization application stages described above , It is the best practice summarized by enterprises according to practical application . Next , Let's learn more about the specific application solutions of these two enterprises .
1、 Background and challenges
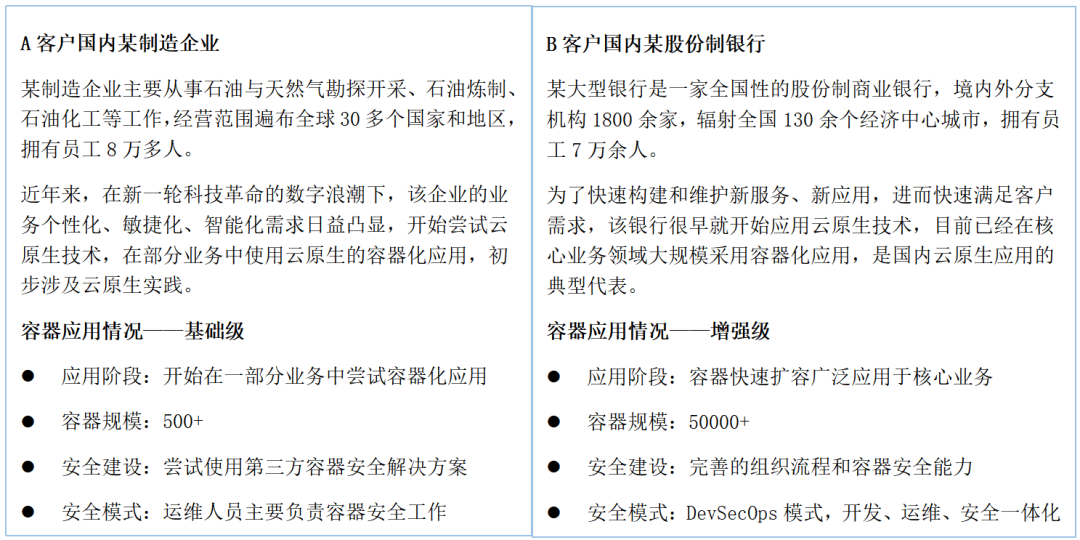
A Customer : A manufacturing enterprise —— The initial stage of container application
In order to better adapt to the flexible changes and flexible expansion of business . The customer put the containerized application into production , But it also brings its own threat vector . At this time, a core problem is cognitive bias , From developers to security experts accustomed to using traditional tools , Few people fully understand what potential safety problems may occur in containers , It also makes customers face unprecedented security challenges .
Major security challenges
Vulnerability management is difficult :
In the development process , The most important part of vulnerability management is image scanning . Some scanning tools can only find operating system vulnerabilities and vulnerabilities that only exist in certain languages , Some cannot scan every image layer or some open source software packages .
Low efficiency of compliance management :
Team members manage configuration manually , It is not only inefficient but also prone to mistakes , Customers need tools that automatically perform configuration checks to improve security and reduce operational workload .
Lack of runtime security :
After the application is put into production , Must be able to detect abnormal behavior in the application , This may be a precursor to a security incident .
B Customer : A joint-stock bank —— Container application advanced stage
With the continuous deepening of Yunyuan biochemical Application , The customer containerized more applications . At this time , The technology stack involved in containerization is constantly enriched , The number of engineers and teams is increasing . here , Complexity becomes the main problem . Complexity not only challenges security , It will also bring challenges to incident response and compliance . Therefore, the importance of visibility and automatic configuration management has multiplied , Customers need to simplify the development and operation process , And realize the automatic operation of repetitive work .
Major security challenges
More complex compliance requirements :
In the mature stage of container application , It is important to track , Customers need to know which applications or microservices need to meet what compliance requirements , And effectively check whether it meets the compliance requirements .
Service isolation and segmentation :
As the number of services increases and the compliance and security ecosystem becomes more and more complex , Proper flow isolation and segmentation between services is critical .
2、 Solution
Since the container runs very fast , Safety should be introduced into the container life cycle as early as possible ,
Embed security into the build 、 Deploy and run the entire container lifecycle , Achieve the development stage — Safe left shift and operation phase — Adaptive security .
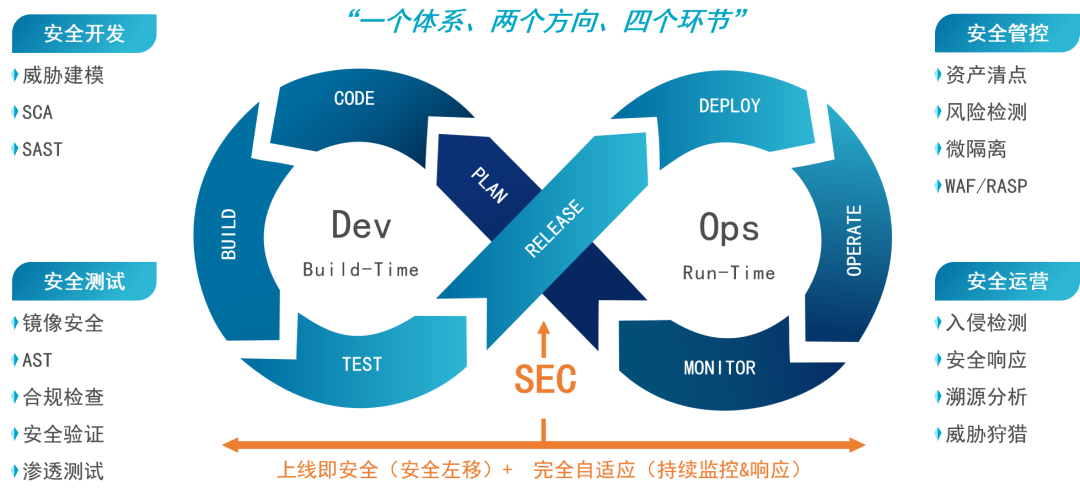
01 Construction phase
Security image scanning
Scan through container image , Detect whether there are common vulnerabilities and risks (CVE), Reduce the attack surface of the final container image . The correct mirror scanning includes the following levels :
Observe application behavior
Observe the microservice architecture during development and integration , Know what is normal behavior , This helps in threat modeling . In production , Detect abnormal behavior through threat model , In isolation .
02 Distribution phase
Review known content
The container security system needs to verify the container image when passing through the container image warehouse , Once non-compliance is found , It is necessary to intercept and isolate relevant images .
Review the risk score
Generate a risk score for each container image of each checkpoint , Standardize container life cycle , And set the minimum safety threshold for each important checkpoint , If the minimum level is not reached , The container life cycle will be controlled .
03 Deployment phase
Automatic deployment
Link the container security scheme with the deployment system , Realize unified security policy management , For the written 、 Code that supports automated deployment tasks is scanned and validated , Find vulnerabilities in the code .
Security infrastructure
Deploying a vulnerability free container on the host will still pose a security risk , Relevant reinforcement best practices need to be implemented , for example , With CIS Benchmark or company reinforcement strategy , Check for deviations from reinforcement best practices .
Log data audit
Through complete 、 Comprehensive log data audit trail , When safety risks occur, specific reasons can be investigated , And take remedial measures and implement new security strategies accordingly .
04 Operation phase
Workload inventory and visualization
Fully automated 、 Fine grained analysis of workloads , And visualize the network access behavior between workloads .
Micro isolation
Using micro isolation can control the network access of containers , And emergency response , When something goes wrong , Isolation can be used to prevent further spread of the threat .
Intrusion detection and response
Provide behavior based detection capability with multiple anchors , It can accurately detect the unique escape behavior of containers 、 be based on K8S Aggressive behavior of 、 Mining in containers 、 Horizontal penetration and other behaviors , At the same time, isolation containers are further provided 、 Kill files, etc .
Back analysis
Actively discover unknown threats through threat hunting , It's like cyberspace “ black box ”, Record various log data , It can be used to analyze various network security events , Trace the whole attack process .
3、 Customer revenue
Safety director of a manufacturing enterprise :
“ At first, we investigated many solutions , Now I'm especially glad that I chose the Ivy honeycomb container safety solution , After practice , Now the whole team recognizes its ability .”
01 Powerful image scanning ability
adopt CI Integrated plug-ins , Realization DevOps Image scanning capability , Compared with the traditional scanning tool process , It used to take nearly 1 Hours of vulnerability scanning is reduced to 6 minute , Efficiency improvement 10 times , The false alarm rate is significantly reduced , Reduce cost and increase efficiency .
02 Comprehensive container operation risk inspection
For running containers , On the one hand, the application is tested ,
Find application vulnerabilities ;
On the other hand, through nondestructive testing ,
Find the problem of weak password in application ,
Such as mysql、redis Weak password .
03 Flexible compliance baseline capabilities
Support 150+ Check the item , It can cover all inspection objects in the cluster ,
Baseline sampling ⽤ Mission check ⽅ type , Customers can flexibly target different inspection objects 、 Different business systems set flexible inspection tasks , To adapt to the complex enterprise environment .
The person in charge of security of a joint-stock bank :
“ We want to use fewer security tools , Solve as many security problems as possible . Choose Ivy honeycomb , Not only has the security capability covering the host and container levels , It can also realize data linkage with other security products , In addition to helping developers solve security problems , It also helps to improve the efficiency of the whole software development life cycle .”
01 Ultra fine grained asset inventory capability
Detailed inventory of ivy and honey comb assets 、 The comprehensive degree is far better than other similar solutions , In addition to the underlying assets 、K8S Assets are counted , just so so
For application assets and Web Make a detailed inventory of assets , Support 15 Class asset type ,1500+ The business should ⽤ distinguish .
02 Multi dimensional intrusion detection capability
Against known threats 、 A malicious act 、 Conduct comprehensive detection of abnormal behaviors , Provide behavior based detection capability with multiple anchors ,
For vulnerability escape 、 Trojans 、Webshell Such intrusion detection rate is much higher than other solutions .
03 Adaptive micro isolation capability
Ivy bee nest combs and learns through the interview relationship , Provide
⾃ Adaptive 、⾃ Migrated 、⾃ Maintenance of ⽹ Network isolation strategy ,
Provide business view ⻆ Of ⽹ Network topological relationship , Covering all kinds of cloud plains ⽣ The isolation strategy of the scene .
原网站版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/188/202207071133167353.html