In the whole information system , The computing platform serves as the base of the system , Determined the whole IT Security and credibility of the system .
Vertically , Each layer of the computing platform from bottom to top faces different security threats , Chip from 2018 Since, vulnerabilities of side channel attacks have been constantly exposed , Hardware may be physically attacked , The firmware may be tampered with and implanted into the backdoor Trojan , Applications and operating systems are the key areas of hacker attacks . Therefore, building a complete trust chain of the whole computing platform from bottom to top is the first step to ensure the security and credibility of the platform's computing power .
On the other hand , To ensure the security of data , It is necessary to ensure the safety of data in the whole life cycle . Now look at , In the whole life cycle of data , Each link has mature security technology and scheme guarantee , Only the safety in data use , It is still an industry problem . The reason is that when data is processed , It must be deterministic , And need to be understood by the handler , For example, use a key , It must be input in clear text to get definite results . This process provides an opportunity for attackers . Data security in use , It needs to be solved by privacy computing or confidential computing technology . So in the next few years, these technologies will be the core competitiveness of data security .
Secure computing platform : A base for rapid development of secure and trusted applications
In order to support customers and partners to quickly develop secure and trusted applications , Kunpeng is committed to providing complete security solutions , With Kunpeng processor and Euler OS Based on , Provide Kunpeng application enabling kit BoostKit , Including confidential calculations TrustZone Kit 、KAE A series of components such as acceleration engine , Build full stack security capabilities , Support multi scenario applications .
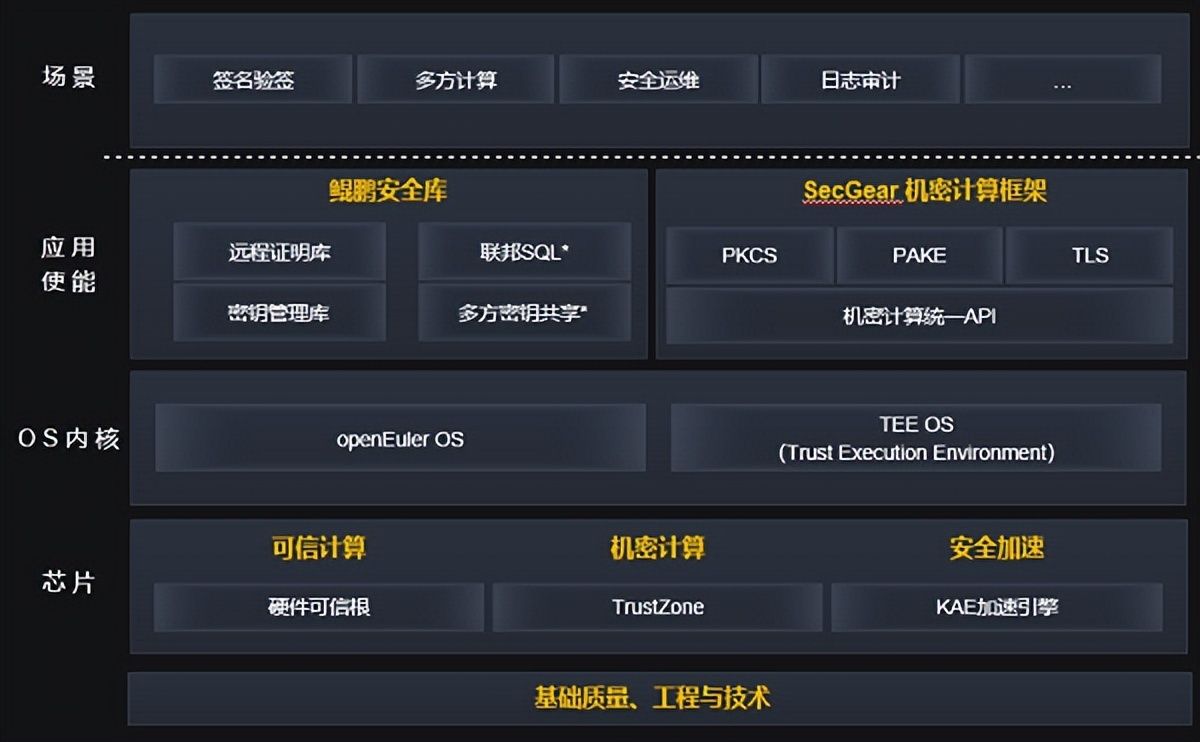
On the hardware , Kunpeng provides trusted computing 、 The three core capabilities of confidential computing and security acceleration . Trusted computing is based on the built-in trusted root of the chip to achieve safe startup and trusted measurement , Prevent the system from being tampered ; Confidential calculations are based on ARM TrustZone framework , Build a safe and reliable trusted execution environment , Make data available invisible ; The security acceleration is through the built-in “ High performance security password accelerator card ” KAE Accelerate engine implementation .
stay OS On the kernel , Kun Peng is not only openEuler Security enhancements have been made , Also for confidential calculations TrustZone A dedicated TEE Security OS,OS The security of has passed the formal verification test , And get CC EAL 4+ Safety certification , Its micro kernel is developed by Huawei , After market maturity verification , It has been running stably on hundreds of millions of end-to-end devices for more than ten years .
In the application enable layer , Kunpeng provides Kunpeng safety warehouse and secGear Confidential computing framework , Combined with hardware capabilities , Enable Kunpeng developers to quickly create secure and trusted applications .
at present , Kunpeng security solutions have covered mainstream security scenarios , In Finance 、 Operator, 、 The government and other industries have already had practical application cases .
Kunpeng Trusted Computing : Based on the built-in trusted root of the chip, we can realize safe startup and trusted measurement
We know , In a complete computing system , From the underlying hardware , To BIOS The firmware , To the operating system , There are attacks 、 The risk of tampering with and implanting backdoor Trojans . Trusted computing technology starts safely 、 Trusted startup and other technical means , Start from the trusted root of hardware , Build a bottom-up trust chain , Ensure the integrity of the whole system , Not maliciously tampered .
Kunpeng server provides a complete trusted computing solution , Take the hardware Kunpeng processor as the trusted root , Provide a complete chain of trust up , Support safe startup and trusted startup . Safe startup ensures that the system startup process follows the step-by-step verification signature , If the verification fails, stop starting the process , Turn to the safe backup version loading system , Prevent the system from operating illegally after being tampered .
Trusted startup measures each key component during system startup , And save the measurement results in trusted hardware TPM in , After the system runs, it can provide the measurement report of the system at any time , So that the third party can verify the security and trusted state of the system through remote certification . among , A remote proof development framework for dynamic measurement of system trustworthiness , Open source has contributed to openEuler Kunpeng safety vault in the community , And it is still developing and evolving . Interested friends can visit the community , Welcome to join us .
Kun Peng BoostKit Confidential computing TrustZone Kit : Enable the trusted flow of data
Secret computing technology , It is also one of the hottest data security technologies in the industry . As mentioned earlier , Confidential computing technology is mainly based on hardware chips , Build a safe and trusted execution environment , Put the data in a trusted execution environment , Also known as TEE(Trust Execution Environment) Run in , In order to protect the data in use .
At present, different chip manufacturers have launched their own confidential computing technology , such as Intel The company's SGX technology ,AMD The company's SEV Technology and ARM The company's TrustZone technology . Although their respective technical implementation methods are different , But the purpose and effect are basically the same . Compared with the traditional computing mode, it provides unconditional trust for system administrators and Computing , Computing mode using confidential computing technology , It can effectively prevent the provider of computing power , Such as the illegal acquisition of data by cloud manufacturers . In the face of threats such as malicious administrators or internal crimes , It can still effectively protect users' data at runtime .
Kunpeng adopted ARM Of TrustZone Open architecture enables a trusted execution environment , be based on CPU Time sharing multiplexing mechanism , take CPU And computing resources are divided into a secure world (TEE) And the unsafe world (REE), Put the data that needs to be protected into secure world Computing , The non secure world cannot access the secure world data .
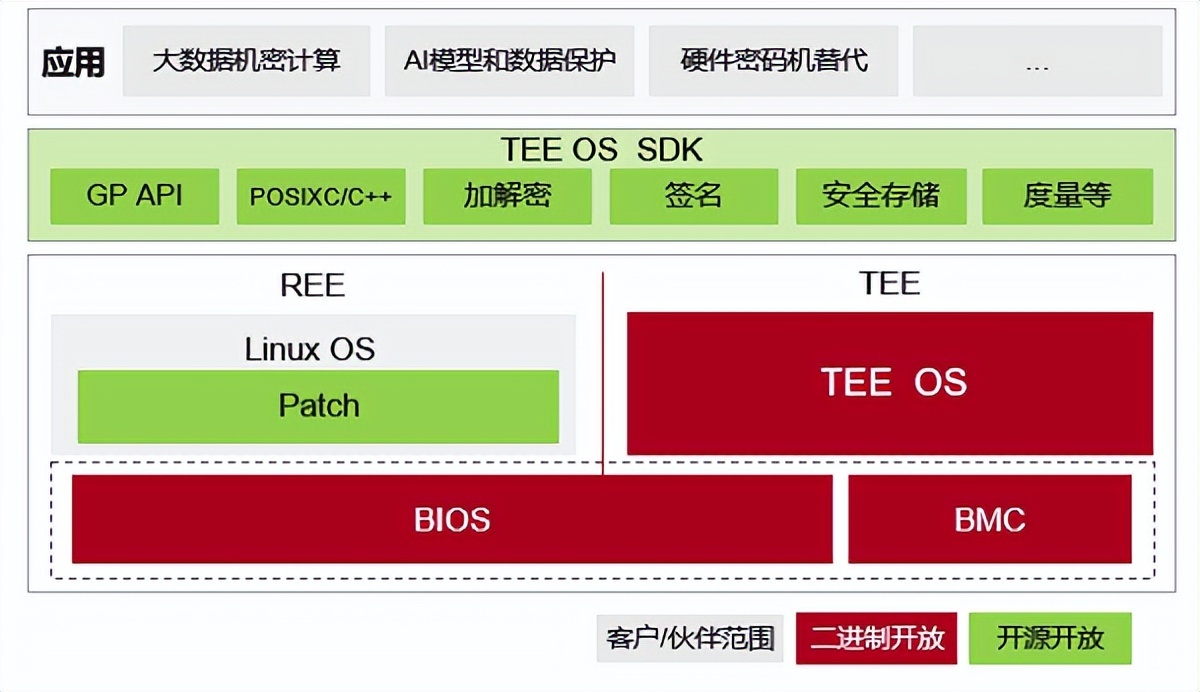
say concretely , HUAWEI
Kun Peng BoostKit Confidential computing TrustZone Kit
To provide an open development architecture , Pre installed TEE Security OS And system firmware , It also includes community open source SDK And patches .
Pre installed part , Start with the chip , Hardware requirements BIOS as well as BMC coordination , among BIOS Finish right TEE OS Decryption and verification of , Initialize safe memory and start TEE OS,BMC Provide upgrade and maintenance capabilities .
TEE OS It's Kunpeng's Secret calculation TrustZone The core components of the suite , Use the microkernel system owned by Huawei , And complete the adaptation and Optimization for the cloud application scenario of the server .TEE OS One of the main features is stability and reliability , It has been applied to mobile phones near 10 year , Serve more than 100 million users ; Second, security is guaranteed , It has been certified by a third party , obtain CC EAL4+ certificate ,CC EAL6+ Certification is also in progress .
The open source part ,REE Side Patch Provide drive and CA Development interface , Developers can compile according to their own operating system . meanwhile ,TEE SDK Provided with standard GP Interface , Unique service interface ,POSIX C as well as C++ Interface , Drivers are relatively friendly , Development convenience is also one of the characteristics of Kunpeng scheme .
In the process of confidential calculation , There is another problem that must be solved , That's it TA(Trusted Apps) The source of is unpredictable , To guarantee TEE The credibility of the environment , Avoid being contaminated by malicious applications ,TA Identity and integrity must be confirmed before operation .
Kunpeng confidential computing adopts the method of issuing Developer Certificates to customers , And realize the right to TA Control the integrity verification of . The overall process is as follows :
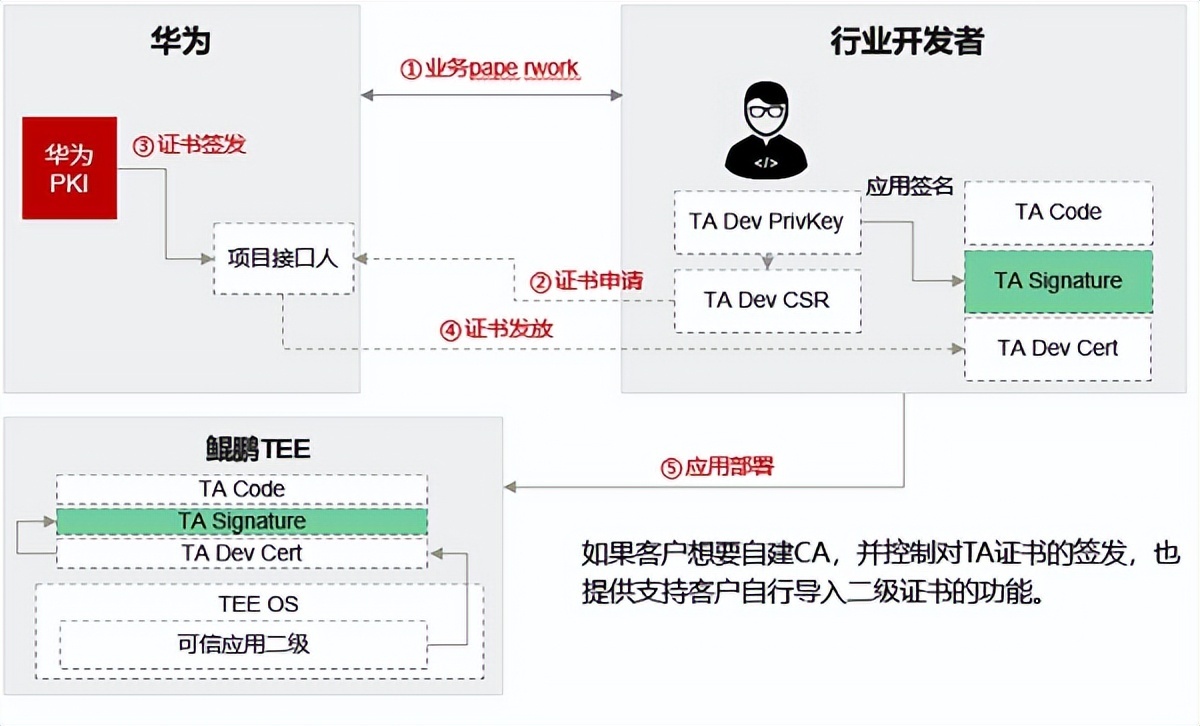
1. The developer decides to start the project , For their own TA Generate the certificate request file and submit it to the Huawei project interface ;
2. The Huawei contact person organizes the project review , After the review is passed , The interface person passes PKI Apply for a certificate , Finally, send the certificate back to the customer ;
3. Developers build TA Binary system , And use SDK Provide tools for TA Sign and encrypt , Generate the final image file .
Of course , Such a process is still a little cumbersome , In order to further simplify the development process of developers , The secondary certificate import function will be launched in the near future , Enable developers in TEE OS Import your own certificate in , Then you can directly use your own certificate to TA Conduct signature verification , It does not need to pass Huawei's signature every time the project is started , Make development more convenient .
Kun Peng BoostKit KAE To accelerate the engine : Built in processor “ High performance security accelerator ”
Kunpeng security solutions add and decompress the traditional capabilities , The encryption and decryption ability in line with international standards and the national secret algorithm in line with national standards are built into Kunpeng processor , Compared with traditional PCIe The acceleration card scheme is improved 30% above , In terms of security , Because plaintext data cannot be sent out of the chip , No data bus , Security has also been improved .

In ease of use , Kunpeng provides the corresponding software API Interface and SDK, The application layer can call directly without modification , And compatible with existing OpenSSL and Zlib And so on , Adhering to the concept of developer centered , It is extremely easy to use .
secGear Confidential computing development framework : The efficiency of security application development is increasing exponentially
At present, a major problem faced by confidential computing in the industry , Different manufacturers adopt different hardware architectures , As we said before Intel SGX、ARM TrustZone etc. . Different hardware architectures will inevitably lead to different software interfaces , This further leads to application incompatibility . Applications developed on one platform cannot be used on another platform , Facing the problem of repeated development .

and secGear Is to help developers solve this problem , Realize a set of software framework compatible with a variety of hardware , Shield developers from hardware differences . By using secGear middleware , Developers only need to adopt a unified API Carry out a development , The developed application can be deployed to a variety of different hardware , Greatly improved development efficiency , Reduce repetitive work , It can also better adapt to the actual situation of multi hardware coexistence in reality .
Besides the security technology itself , Huawei also set high standards for the safety and quality of the entire product , Be strict with . Adopt a scientific and systematic method to incorporate safety and credibility assurance activities into the whole life cycle of product development process , Ensure the safety, credibility and sustainability of products .
Huawei has formed an efficient safety engineering capability management process by referring to the best practices in the industry . At every stage of product development and design , Corresponding safety activities , From the analysis of safety requirements in the product concept stage , To the safety design in the design stage , Then to security development 、 Security testing , Finally, continuous maintenance after product release , Try not to leave blind spots , Reduce the safety risk of the product , For customers , Provide developers with products of the highest safety quality , Relieve the worries of the future .
This article shares Kunpeng security solutions , We hope that it can bring enlightenment and value to customers and partners to create industry security solutions , I also hope that interested friends can further participate in Kunpeng's project , Develop and build a more complete safety ecosystem together .
原网站版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/188/202207071055163353.html