当前位置:网站首页>[cloud native | kubernetes] actual battle of ingress case (13)
[cloud native | kubernetes] actual battle of ingress case (13)
2022-07-05 11:44:00 【Lanson】
Ingress Case actual combat
One 、 Basic configuration
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: itlanson-ingress
namespace: default
spec:
rules:
- host: itlanson.com
http:
paths:
- path: /
pathType: Prefix
backend: ## Specify the back-end service that needs to respond
service:
name: my-nginx-svc ## kubernetes Clustered svc name
port:
number: 80 ## service Port number
pathType detailed :
Prefix: Based on/separated URL Path prefix matching . Matching is case sensitive , And complete the elements in the path one by one . The path element refers to the path element created by/List of labels in the path separated by the separator . If each p All request paths p Element prefix of , Then request and path p matching .Exact: Exactly match URL route , And case sensitive .ImplementationSpecific: For this path type , The matching method depends on IngressClass. The specific implementation can regard it as a separatepathTypeDealing with or relating toPrefixorExactThe type is treated the same .
ingress The rules will take effect to all in accordance with IngressController Of a machine nginx To configure .
Two 、 Default backend
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: itlanson-ingress
namespace: default
spec:
defaultBackend: ## Specify all unmatched default backend
service:
name: php-apache
port:
number: 80
rules:
- host: itlanson.com
http:
paths:
- path: /abc
pathType: Prefix
backend:
service:
name: my-nginx-svc
port:
number: 80
effect
itlanson.com Under the Not /abc All requests at the beginning , All will be here defaultBackend
Not itlanson.com All requests under the domain name , It's going to be defaultBackend
nginx Global configuration for
kubectl edit cm ingress-nginx-controller -n ingress-nginx
Edit configuration plus
data: Configuration item : Configuration values
All configuration item references
https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/configmap Based on the environment variable
3、 ... and 、 The path to rewrite
Rewrite - NGINX Ingress Controller
Rewrite function , It is often used in scenes with front and back separation
The front end sends a message to the server / Request mapping front-end address .
The back end sends a message to the server /api The request comes to the corresponding service . But back-end services don't /api Start path of , So we need to ingress-controller Automatic string cutting
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations: ## Write well annotion
#https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/
nginx.ingress.kubernetes.io/rewrite-target: /$2 ### Which part only
name: rewrite-ingress-02
namespace: default
spec:
rules: ## Write the rules
- host: itlanson.com
http:
paths:
- backend:
service:
name: php-apache
port:
number: 80
path: /api(/|$)(.*)
pathType: Prefix
Four 、 To configure SSL
TLS/HTTPS - NGINX Ingress Controller
Generate Certificate :( You can also go to Qingyun to apply for a free certificate for configuration )
$ openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout ${KEY_FILE:tls.key} -out ${CERT_FILE:tls.cert} -subj "/CN=${HOST:itlanson.com}/O=${HOST:itlanson.com}"
kubectl create secret tls ${CERT_NAME:itlanson-tls} --key ${KEY_FILE:tls.key} --cert ${CERT_FILE:tls.cert}
## The example command is as follows
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.cert -subj "/CN=it666.com/O=it666.com"
kubectl create secret tls it666-tls --key tls.key --cert tls.cert
apiVersion: v1
data:
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURJekNDQWd1Z0F3SUJBZ0lKQVB6YXVMQ1ZjdlVKTUEwR0NTcUdTSWIzRFFFQkN3VUFNQ2d4RWpBUUJnTlYKQkFNTUNXbDBOalkyTG1OdmJURVNNQkFHQTFVRUNnd0phWFEyTmpZdVkyOXRNQjRYRFRJeE1EVXhNREV5TURZdwpNRm9YRFRJeU1EVXhNREV5TURZd01Gb3dLREVTTUJBR0ExVUVBd3dKYVhRMk5qWXVZMjl0TVJJd0VBWURWUVFLCkRBbHBkRFkyTmk1amIyMHdnZ0VpTUEwR0NTcUdTSWIzRFFFQkFRVUFBNElCRHdBd2dnRUtBb0lCQVFDbkNYa0wKNjdlYzNjYW5IU1V2VDR6YXZmMGpsOEFPWlBtUERhdUFRTElEby80LzlhV2JPSy9yZm5OelVXV3lTRFBqb3pZVApWa2xmQTZYRG1xRU5FSWRHRlhjdExTSlRNRkM5Y2pMeTlwYVFaaDVYemZId0ZoZXZCR1J3MmlJNXdVdk5iTGdWCmNzcmRlNXlKMEZYOFlMZFRhdjhibzhjTXpxN2FqZXhXMWc1dkxmTWZhczAvd2VyVk9Qc0ZmS3RwZ1dwSWMxMXEKekx6RnlmWHNjcVNhVTV2NFo5WHFqQjRtQjhZZ043U2FSa2pzU0VsSFU4SXhENEdTOUtTNGtkR2xZak45V2hOcAp6aG5MdllpSDIrZThQWE9LdU8wK2Jla1MrS3lUS2hnNnFWK21kWTN0MWJGenpCdjFONTVobTNQTldjNk9ROTh3CkYrQk9uUUNhWExKVmRRcS9BZ01CQUFHalVEQk9NQjBHQTFVZERnUVdCQlNzSUFvMHZ4RFZjVWtIZ1V1TFlwY0wKdjBFSERqQWZCZ05WSFNNRUdEQVdnQlNzSUFvMHZ4RFZjVWtIZ1V1TFlwY0x2MEVIRGpBTUJnTlZIUk1FQlRBRApBUUgvTUEwR0NTcUdTSWIzRFFFQkN3VUFBNElCQVFDSjFEdGJoQnBacTE1ODVEMGlYV1RTdmU3Q2YvQ3VnakxZCjNYb2gwSU9sNy9mVmNndFJkWXlmRFBmRDFLN0l4bElETWtUbTVEVWEyQzBXaFY5UlZLU0poSTUzMmIyeVRGcm8Kc053eGhkcUZpOC9CU1lsQTl0Tk5HeXhKT1RKZWNtSUhsaFhjRlEvUzFaK3FjVWNrTVh6UHlIcFl0VjRaU0hheQpFWVF2bUVBZTFMNmlnRk8wc2xhbUllTFBCTWhlTDNnSDZQNlV3TVpQbTRqdFR1d2FGSmZGRlRIakQydmhSQkJKCmZjTGY5QjN3U3k2cjBDaXF2VXQxQUNQVnpSdFZrcWJJV1d5VTBDdkdjVDVIUUxPLzdhTE4vQkxpNGdYV2o1MUwKVXdTQzhoY2xodVp3SmRzckNkRlltcjhTMnk0UDhsaDdBc0ZNOGorNjh1ZHJlYXovWmFNbwotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2QUlCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktZd2dnU2lBZ0VBQW9JQkFRQ25DWGtMNjdlYzNjYW4KSFNVdlQ0emF2ZjBqbDhBT1pQbVBEYXVBUUxJRG8vNC85YVdiT0svcmZuTnpVV1d5U0RQam96WVRWa2xmQTZYRAptcUVORUlkR0ZYY3RMU0pUTUZDOWNqTHk5cGFRWmg1WHpmSHdGaGV2QkdSdzJpSTV3VXZOYkxnVmNzcmRlNXlKCjBGWDhZTGRUYXY4Ym84Y016cTdhamV4VzFnNXZMZk1mYXMwL3dlclZPUHNGZkt0cGdXcEljMTFxekx6RnlmWHMKY3FTYVU1djRaOVhxakI0bUI4WWdON1NhUmtqc1NFbEhVOEl4RDRHUzlLUzRrZEdsWWpOOVdoTnB6aG5MdllpSAoyK2U4UFhPS3VPMCtiZWtTK0t5VEtoZzZxVittZFkzdDFiRnp6QnYxTjU1aG0zUE5XYzZPUTk4d0YrQk9uUUNhClhMSlZkUXEvQWdNQkFBRUNnZ0VBTDZ0Tlp6Q0MrdnB6cWRkd2VEcjhtS1JsckpXdkVxeVFaOW5mMnI4Ynpsd3IKdi9jTHB1dWJrTnBLZWx0OWFVNmZ1RlFvcDRZVmRFOG5MRlpocGNmVXd4UjNLV1piQ0dDZWVpSXdGaFIzVFloSApHb25FaE43WkxYSlVjN3hjemh5eTFGSTFpckZ5NFpoWVNTQXltYzdFSXNORFFKRVJ5ajdsdWF1TkNnOFdtWFdPCmd0OHIzZHVTazNHV2ZZeGdWclFZSHlGTVpCbUpvNDliRzVzdGcwR01JNUZRQXord3RERlIyaWk2NkVkNzBJOUwKYXJNMHpQZkM3Tk1acmhEcHVseVdVYWNXRDY1V1g1Yys5TnpIMW15MEVrbjJGOWQzNXE1czZRakdTVElMVXlhbwpJUVl5bGU0OVdKdlV4YjN2YTZ1OTVBUHAyWFFVaFEyS09GcGxabncwTVFLQmdRRFN2cDAzYlBvQVlEb3BqWGlxCndxemxKdk9IY2M4V3ZhVytoM0tvVFBLZ1dRZWpvVnNZTFEzM2lMeXdFY0FXaWtoSzE2UjVmTkt5VUFRZ2JDNm4KNTdkcUJ3L1RqYlV2UGR6K0llMnNKN1BlSlpCQktXZUNHNjBOeGgzUDVJcSsxRHVjdExpQTBKdVZyOUlaUzdqSApJOVpUMitDMTNlNkRlZkJaajFDb0ZhemJ1UUtCZ1FESzZCaVkzSk5FYVhmWVpKUzh1NFViVW9KUjRhUURBcmlpCjFGRlEzMDFPOEF0b1A2US9IcjFjbTdBNGZkQ3JoSkxPMFNqWnpldnF4NEVHSnBueG5pZGowL24yTHE3Z2x6Q2UKbVlKZFVVVFo0MkxJNGpWelBlUk1RaGhueW9CTHpmaEFYcEtZSU1NcmpTd1JUcnYyclRpQkhxSEZRbDN6YngvKwptcjdEVWtlR053S0JnRllPdEpDUGxiOVZqQ3F2dEppMmluZkE0aTFyRWcvTlBjT0IrQlkxNWRZSXhRL1NzaW83Cks3cnJRWEg4clo0R3RlS3FFR1h6ek80M3NwZXkxWktIRXVUZklWMVlQcWFkOG9Kc1JHdktncTZ5VkNmbnluYmMKNmx2M2pQRDUrSlpZZ0VkTG5SUXRHM3VTb283bDF2eXE2N2l1enlJMUVGTHNGblBjRENtM1FERXhBb0dBSDQrdQprOGhybDg2WDk2N2RlK1huTkhMSEZwbDBlNHRtME4wWnNPeXJCOFpLMy9KV1NBTXVEVU9pUzRjMmVCZHRCb0orClNqSy9xWXRTeEhRb3FlNmh6ZU5oRkN2Nnc3Q0F2WXEvUG1pdnZ2eWhsd0dvc3I1RHpxRFJUd091cFJ2cXE0aUsKWU9ObnVGU0RNRVlBOHNQSzhEcWxpeHRocGNYNVFnOHI4UkhSVWswQ2dZQlF3WFdQU3FGRElrUWQvdFg3dk1mTwp3WDdWTVFMK1NUVFA4UXNRSFo2djdpRlFOL3g3Vk1XT3BMOEp6TDdIaGdJV3JzdkxlV1pubDh5N1J3WnZIbm9zCkY3dkliUm00L1Y1YzZHeFFQZXk5RXVmWUw4ejRGMWhSeUc2ZjJnWU1jV25NSWpnaUh2dTA3cStuajFORkh4YVkKa2ZSSERia01YaUcybU42REtyL3RtQT09Ci0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K
kind: Secret
metadata:
creationTimestamp: "2022-06-10T12:06:22Z"
name: it666-tls
namespace: default
resourceVersion: "2264722"
uid: 16f8a4b6-1600-4ded-8458-b0480ce075ba
type: kubernetes.io/tls
Configure domain name usage certificate
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: itlanson-ingress
namespace: default
spec:
tls:
- hosts:
- itlanson.com
secretName: itlanson-tls
rules:
- host: itlanson.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: my-nginx-svc
port:
number: 80
Configure the certificate , Access to the domain name , Will default to https
5、 ... and 、 The speed limit
Annotations - NGINX Ingress Controller
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-222333
namespace: default
annotations: ## annotation
nginx.ingress.kubernetes.io/limit-rps: "1" ### Current limiting configuration
spec:
defaultBackend: ## As long as the mapping path is not specified
service:
name: php-apache
port:
number: 80
rules:
- host: it666.com
http:
paths:
- path: /bbbbb
pathType: Prefix
backend:
service:
name: cluster-service-222
port:
number: 80
6、 ... and 、 Grayscale Publishing -Canary
Used to be able to use k8s Of Service coordination Deployment Deploy canaries . The principle is as follows
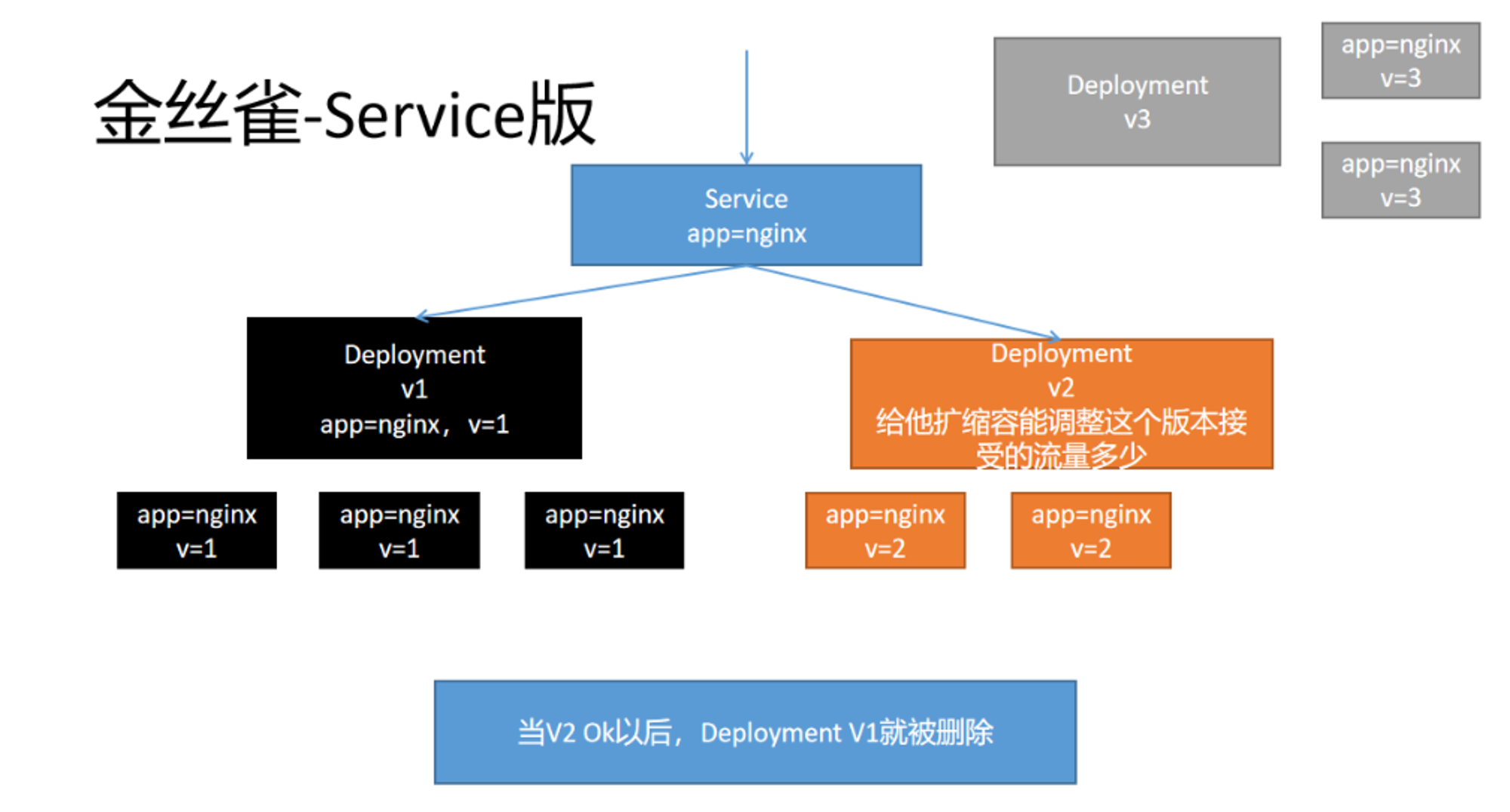
shortcoming :
Cannot customize grayscale logic , For example, specify the user to perform grayscale analysis
Now you can use Ingress Go gray . The principle is as follows
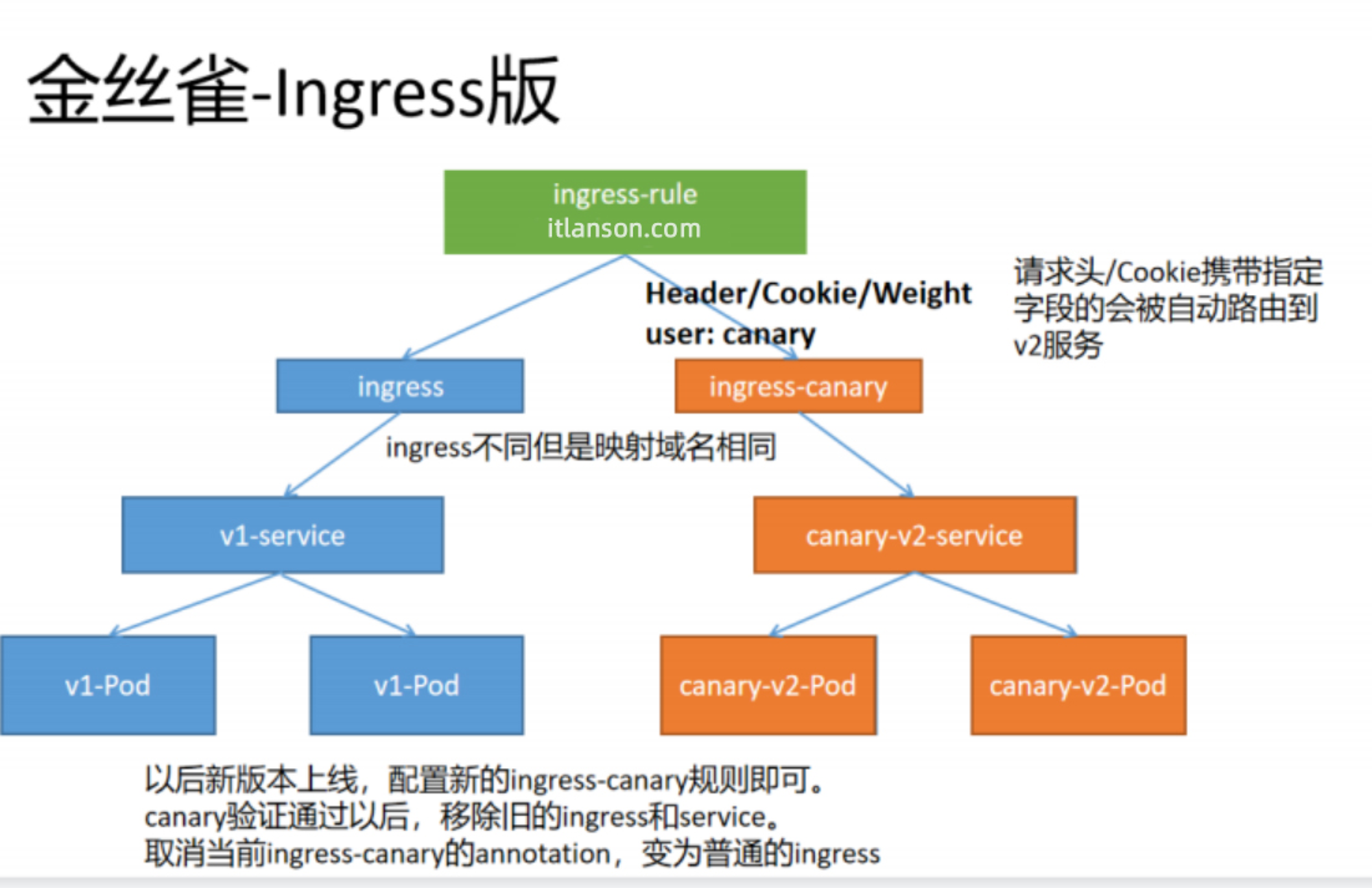
## Use the following file to deploy two service edition .v1 Version returns nginx Default page ,v2 Version returns 11111
apiVersion: v1
kind: Service
metadata:
name: v1-service
namespace: default
spec:
selector:
app: v1-pod
type: ClusterIP
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: v1-deploy
namespace: default
labels:
app: v1-deploy
spec:
selector:
matchLabels:
app: v1-pod
replicas: 1
template:
metadata:
labels:
app: v1-pod
spec:
containers:
- name: nginx
image: nginx
---
apiVersion: v1
kind: Service
metadata:
name: canary-v2-service
namespace: default
spec:
selector:
app: canary-v2-pod
type: ClusterIP
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: canary-v2-deploy
namespace: default
labels:
app: canary-v2-deploy
spec:
selector:
matchLabels:
app: canary-v2-pod
replicas: 1
template:
metadata:
labels:
app: canary-v2-pod
spec:
containers:
- name: nginx
image: registry.cn-hangzhou.aliyuncs.com/lanson_k8s_images/nginx-test:env-msg
7、 ... and 、 Conversation retention -Session Affinity
https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/#session-affinityhttps://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/#session-affinity First visit ,ingress-nginx It will return to the browser Cookie, In the future, the browser will take this Cookie, Make sure the visit is always before arrival Pod;
## Deploy one or three Pod Of Deployment And set up Service
apiVersion: v1
kind: Service
metadata:
name: session-affinity
namespace: default
spec:
selector:
app: session-affinity
type: ClusterIP
ports:
- name: session-affinity
port: 80
targetPort: 80
protocol: TCP
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: session-affinity
namespace: default
labels:
app: session-affinity
spec:
selector:
matchLabels:
app: session-affinity
replicas: 3
template:
metadata:
labels:
app: session-affinity
spec:
containers:
- name: session-affinity
image: nginx
Write a session friendly ingress
### Use each request to carry the same cookie, To identify whether it is the same session
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: session-test
namespace: default
annotations:
nginx.ingress.kubernetes.io/affinity: "cookie"
nginx.ingress.kubernetes.io/session-cookie-name: "itlanson-session"
spec:
rules:
- host: it666.com
http:
paths:
- path: / ### If the same function of this path under this domain name has been configured before , Take effect for the last time
pathType: Prefix
backend:
service:
name: session-affinity ###
port:
number: 80
边栏推荐
- 【主流Nivida显卡深度学习/强化学习/AI算力汇总】
- [upsampling method opencv interpolation]
- Technology sharing | common interface protocol analysis
- 15 methods in "understand series after reading" teach you to play with strings
- leetcode:1200. Minimum absolute difference
- Programmers are involved and maintain industry competitiveness
- 【SingleShotMultiBoxDetector(SSD,单步多框目标检测)】
- Zcmu--1390: queue problem (1)
- Ncp1342 chip substitute pn8213 65W gallium nitride charger scheme
- 【L1、L2、smooth L1三类损失函数】
猜你喜欢
COMSOL -- establishment of geometric model -- establishment of two-dimensional graphics

中非 钻石副石怎么镶嵌,才能既安全又好看?
7.2 daily study 4
【L1、L2、smooth L1三类损失函数】
![[upsampling method opencv interpolation]](/img/6b/5e8f3c2844f0cbbbf03022e0efd5f0.png)
[upsampling method opencv interpolation]
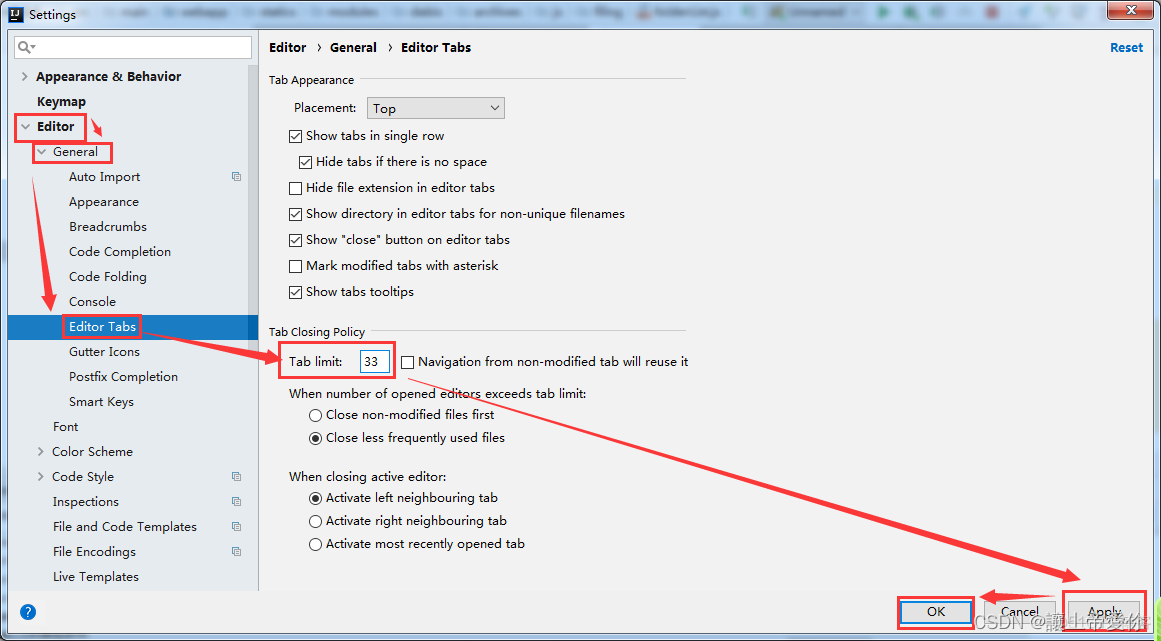
idea设置打开文件窗口个数
![[mainstream nivida graphics card deep learning / reinforcement learning /ai computing power summary]](/img/1a/dd7453bc5afc6458334ea08aed7998.png)
[mainstream nivida graphics card deep learning / reinforcement learning /ai computing power summary]
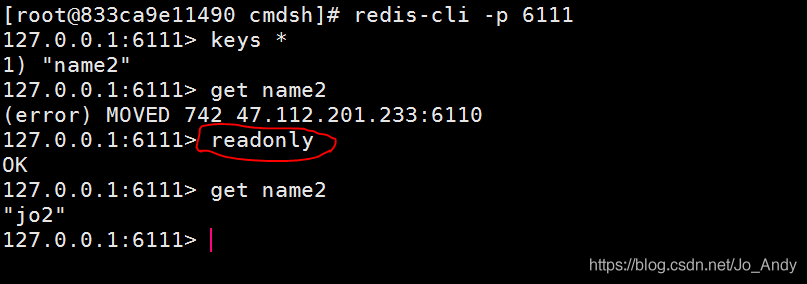
简单解决redis cluster中从节点读取不了数据(error) MOVED
iTOP-3568开发板NPU使用安装RKNN Toolkit Lite2
![[calculation of loss in yolov3]](/img/8c/1ad99b8fc1c5490f70dc81e1e5c27e.png)
[calculation of loss in yolov3]
随机推荐
紫光展锐全球首个5G R17 IoT NTN卫星物联网上星实测完成
【 YOLOv3中Loss部分计算】
Open3D 网格(曲面)赋色
redis集群中hash tag 使用
redis主从中的Master自动选举之Sentinel哨兵机制
COMSOL -- establishment of geometric model -- establishment of two-dimensional graphics
13.(地图数据篇)百度坐标(BD09)、国测局坐标(火星坐标,GCJ02)、和WGS84坐标系之间的转换
pytorch-权重衰退(weight decay)和丢弃法(dropout)
Mongodb replica set
【yolov3损失函数】
What does cross-border e-commerce mean? What do you mainly do? What are the business models?
《看完就懂系列》15个方法教你玩转字符串
yolov5目標檢測神經網絡——損失函數計算原理
【无标题】
【云原生 | Kubernetes篇】Ingress案例实战(十三)
7.2 daily study 4
ACID事务理论
1.php的laravel创建项目
[crawler] Charles unknown error
百问百答第45期:应用性能探针监测原理-node JS 探针