当前位置:网站首页>0719RHCSA
0719RHCSA
2022-07-25 13:19:00 【Psc_ February2】
linux Types of users and groups in
linux Type of user in
- The super user —— The user is called root, It has all permissions , Only system maintenance ( for example : Establish users, etc ) Or other necessary Only use super user login , To avoid security problems in the system .
- System users ( Dummy user )—— yes Linux Users necessary for the normal operation of the system . Mainly to meet the corresponding system process The document is established at the request of the owner , for example :bin、daemon、adm、lp Waiting for users . System users cannot log in .
- Ordinary users —— To enable users to use Linux System resources , Most of our users fall into this category .
linux Type of user group in
Linux There are two types of groups in :
- Basic group ( Private group ): When establishing an account , If the group to which the account belongs is not specified , The system will create a group with the same user name , this The first group is the basic group .
- Additional group ( Public group ): Can accommodate multiple users , All users in the group have the rights owned by the group .
linux Which file stores user information in ? And what do the fields mean
User account file ——/etc/passwd
passwd It's a text file , Used to define the user account of the system , Because all users are right passwd Have the right to read , Therefore, only user accounts are defined in this file , Without saving the password .
passwd In file :
Each line defines a user account
Each line by 7 Fields make up , Use... Between fields “:” Separate , The format is as follows :
Account name : password :UID:GID: The personal data : Home directory :Shell
Field description :
Account name : The user login Linux The name of the system .
password : Previously, the location of the password was saved in an encrypted format , Now the password is saved in /etc/shadow In file , This is just a password placeholder “x” or “*”. if “x”, It means that the password has passed shadow The protection of the
UID: User's identity , It's a number , Use it to distinguish different users
GID: Identification of the basic group in which the user belongs , It's a number , Use it to distinguish different groups , The same group has the same GID.
The personal data : You can record the full name of the user 、 Address 、 Office phone 、 Personal information such as home phone .
Home directory : similar Windows Personal directory , Usually /home/username, here username Is the user name , User execution “cd~” Command, the current directory will switch to the personal home directory .
Shell: Define the number of users to activate after logging in Shell, The default is Bash Shell
linux What is the file in which the group information is stored ? And what do the fields mean ?
User group account file ——/etc/group
Every file in the system has a user and a group owner . Use “ls –l” The command can see the owner and group of each file .
Each group in the system , stay /etc/group There is a line in the file
Any user can read the user group account information profile .
The real password of the user group is saved in /etc/gshadow In profile .
group File field description :
Groupname: Group name
Passwd: Encryption password for the group
GID: The system distinguishes between different groups ID, stay /etc/passwd In domain GID Field is used to specify the basic group of users
Userlist: use “,” Separate user names , Listed are the members of the additional group .
Create the following users 、 Groups and group membership :
Create a sysmgrs Group
[[email protected] ~]# groupadd -r sysmgrs
Create user natasha At the same time specified sysmgrs As natasha Additional groups of
[[email protected] ~]# useradd natasha -G sysmgrs
Create user harry At the same time specified sysmgrs As harry Additional groups of
[[email protected] ~]# useradd harry -G sysmgrs
Create user sarah Appoint shell The type is /sbin/false( You do not have access to interactive on the system shell)
It's not sysmgrs Members of
[[email protected] ~]# useradd sarah -s /sbin/false
Set up natasha 、 harry and sarah All of your passwords are 123
[[email protected] ~]# echo 123 | passwd --stdin natasha
Changing password for user natasha.
passwd: all authentication tokens updated successfully.
[[email protected] ~]# echo 123 | passwd --stdin harry
Changing password for user harry.
passwd: all authentication tokens updated successfully.
[[email protected] ~]# echo 123 | passwd --stdin sarah
Changing password for user sarah.
passwd: all authentication tokens updated successfully.Create user lockuser, And specify home directory as /home/lock, Then lock the user
[[email protected] ~]# useradd lockuser -d /home/lock
[[email protected] ~]# passwd -l lockuser
Locking password for user lockuser.
passwd: SuccessCreate user limituser, gid by 1555,userid by 1666, Let its password in 10 Expires in days
[[email protected] ~]# groupadd -r limit -g 1555
[[email protected] ~]# useradd limituser -g 1555 -u 1666
[[email protected] ~]# passwd -n 10 limituser
Adjusting aging data for user limituser.
passwd: Success Unlock lockuser, And set that the password must be changed the next time you log in
[[email protected] ~]# passwd lockuser -u
Unlocking password for user lockuser.
passwd: Warning: unlocked password would be empty.
passwd: Unsafe operation (use -f to force)
[[email protected] ~]# passwd lockuser -e
Expiring password for user lockuser.
passwd: Success
Give Way natasha With modification harry Password permissions (sudo)
visudo
Host_Alias RHCSA=lwz
User_Alias USER11=natasha
Cmnd_Alias CHPASS=/usr/bin/passwd harry
USER RCHSA=(root) CHPASS
[[email protected] ~]# visudo
Host_Alias RHCSA = server.local
User_Alias USER11 = natasha
Cmnd_Alias CHPASS = /usr/bin/passwd harry
USER11 RHCSA=(root)CHPASS
Create user testuser And set the password , Change the user name to normaluser
[[email protected] ~]# echo 123 | passwd --stdin testuser
Changing password for user testuser.
passwd: all authentication tokens updated successfully.
[[email protected] ~]# usermod -l normaluser testuser
Delete lockuser
[[email protected] ~]# userdel -r lockuser
create a file , And give authority 611( Two ways , A kind of guoa, A kind of nnn)
[[email protected] ~]# chmod 611 file1
[[email protected] ~]# ls -l file1
-rw---x--x. 1 root root 0 Jul 15 14:38 file1
[[email protected] ~]# chmod u=rw- file1
Create directory , And give authority 755( Two ways , A kind of guoa, A kind of nnn)
[[email protected] ~]# mkdir catalogue
[[email protected] ~]# chmod 755 catalogue/
[[email protected] ~]# chmod g-w catalogue/
[[email protected] ~]# ls -dl catalogue/
drwxr-xrwx. 2 root root 6 Jul 19 19:13 catalogue/
create a file , And modify the owner and group of the file to other users
[[email protected] ~]# chown natasha:natasha file1
[[email protected] ~]# ls -l file1
-rw---x--x. 1 natasha natasha 0 Jul 15 14:38 file1
Set up suid, Set for file suid( Two ways u+s and nnnn) The way
[[email protected] ~]# chmod u+s file1
[[email protected] ~]# chmod 4777 file1
[[email protected] ~]# ls -l file1
-rwsrwxrwx. 1 natasha natasha 0 Jul 15 14:38 file1
Set up sgid, Set for file sgid( Two ways g+s and nnnn) The way
[[email protected] ~]# chmod g+s file1
[[email protected] ~]# ls -l file1
-rwsrwsrwx. 1 natasha natasha 0 Jul 15 14:38 file1
[[email protected] ~]# chmod 6777 file1
[[email protected] ~]# ls -l file1
-rwsrwsrwx. 1 natasha natasha 0 Jul 15 14:38 file1
Set up sbit, Set for directory sbit( Two ways o+t and nnnn) The way
[[email protected] ~]# chmod o+t catalogue/
[[email protected] ~]# ls -dl catalogue/
drwxr-xrwt. 2 root root 6 Jul 19 19:13 catalogue/
[[email protected] ~]# chmod 1775 catalogue/
[[email protected] ~]# ls -dl catalogue/
drwxrwxr-t. 2 root root 6 Jul 19 19:13 catalogue/
create a file , Query file acl
[[email protected] ~]# getfacl file1
# file: file1
# owner: natasha
# group: natasha
# flags: ss-
user::rwx
group::rwx
other::rwx
Set for file acl The user is testuser1 Permission is rwx
[[email protected] ~]# setfacl -m u:harry:rwx file1
[[email protected] ~]# getfacl file1
# file: file1
# owner: natasha
# group: natasha
# flags: ss-
user::rwx
user:harry:rwx
group::rwx
mask::rwx
other::rwx
Set for file acl Of mask: Permission is r-x
[[email protected] ~]# setfacl -m m:rx file1
[[email protected] ~]# getfacl file1
# file: file1
# owner: natasha
# group: natasha
# flags: ss-
user::rwx
user:harry:rwx #effective:r-x
group::rwx #effective:r-x
mask::r-x
other::rwx
边栏推荐
- The world is exploding, and the Google server has collapsed
- 0717RHCSA
- Jupyter Notebook介绍
- Redis visualizer RDM installation package sharing
- [Video] visual interpretation of Markov chain principle and Mrs example of R language region conversion | data sharing
- Convolutional neural network model -- alexnet network structure and code implementation
- C # basic learning (XXIII)_ Forms and events
- Docekr learning - MySQL 8 master-slave replication setup deployment
- Basic knowledge of binary tree
- stable_baselines快速入门
猜你喜欢

Docekr学习 - MySQL8主从复制搭建部署

Basic knowledge of binary tree

Error: cannot find or load main class XXXX

Redis visualizer RDM installation package sharing
![[300 opencv routines] 239. accurate positioning of Harris corner detection (cornersubpix)](/img/a6/c45a504722f5fd6e3c9fb8e51c6bb5.png)
[300 opencv routines] 239. accurate positioning of Harris corner detection (cornersubpix)

Jupyter Notebook介绍

Common operations for Yum and VIM
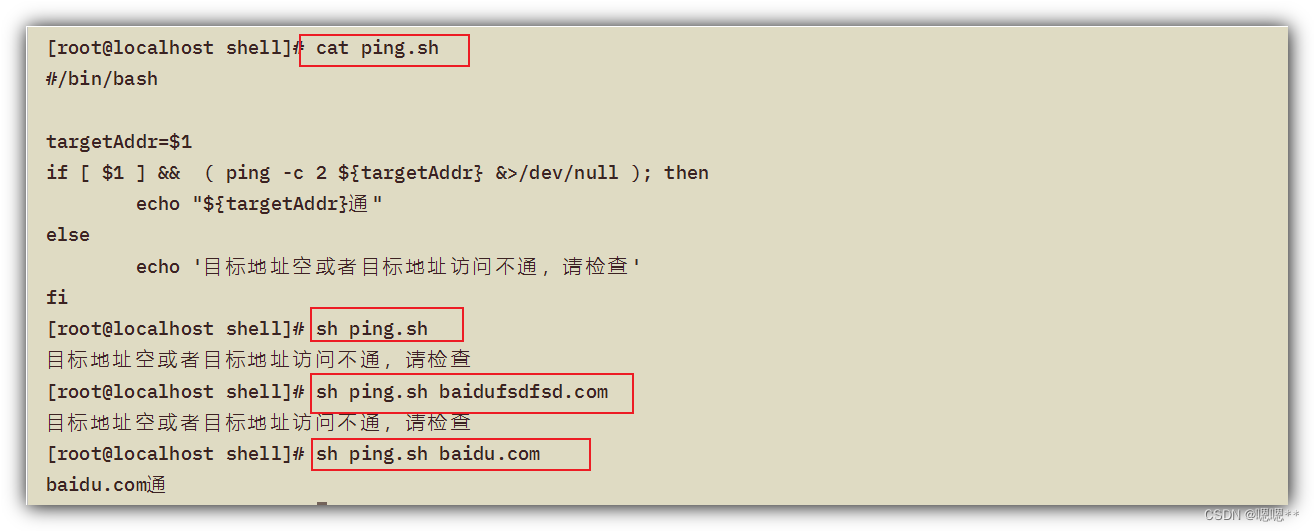
Shell common script: check whether a domain name and IP address are connected

网络空间安全 渗透攻防9(PKI)

The programmer's father made his own AI breast feeding detector to predict that the baby is hungry and not let the crying affect his wife's sleep
随机推荐
VIM tip: always show line numbers
【视频】马尔可夫链蒙特卡罗方法MCMC原理与R语言实现|数据分享
[six articles talk about scalablegnn] around www 2022 best paper PASCA
Business visualization - make your flowchart'run'(3. Branch selection & cross language distributed operation node)
机器学习强基计划0-4:通俗理解奥卡姆剃刀与没有免费午餐定理
如何理解Keras中的指标Metrics
Online Learning and Pricing with Reusable Resources: Linear Bandits with Sub-Exponential Rewards: Li
0719RHCSA
OAuth,JWT ,OIDC你们搞得我好乱啊
Machine learning strong foundation program 0-4: popular understanding of Occam razor and no free lunch theorem
若依如何实现用户免密登录配置方法?
Excel录制宏
Emqx cloud update: more parameters are added to log analysis, which makes monitoring, operation and maintenance easier
yum和vim须掌握的常用操作
央行数研所穆长春:数字人民币可控匿名是维护公众利益和金融安全的客观需要
B树和B+树
【重温SSM框架系列】15 - SSM系列博文总结【SSM杀青篇】
Convolutional neural network model -- alexnet network structure and code implementation
外围系统调用SAP的WebAPI接口
The migration of arm architecture to alsa lib and alsa utils is smooth