当前位置:网站首页>Sharing of source code anti disclosure scheme under burning scenario
Sharing of source code anti disclosure scheme under burning scenario
2022-07-06 07:25:00 【Cnsidna. No.1】
How to prevent disclosure of source code
Various embedded R & D and platform software R & D industries , Each has its own core data and core documents , User data and other sensitive information , These information data have the following commonalities :
It belongs to the core confidential information , In case of leakage, it will have a bad impact on
There are many types of core data , Source code data , Employees have high computer skills
A lot of data is in the business system , It's not a document
If you don't control , Designers and users can easily copy the data through various ways , Cause leakage .
Common secret related ways for R & D personnel
Because R & D personnel are more proficient in computers than ordinary office personnel , In addition to the common network , mail ,U disc ,QQ And other data diffusion methods , There are many other methods that are very easy for developers ( Not listed completely ):
Physical method :
Network cable direct connection , Unplug the network cable from the wall , Then connect directly to an uncontrolled computer ;
winPE start-up , Via CD or U Discoid winPE start-up , Even directly ISO The image starts .
virtual machine , Through installation VMWare virtual machine , Use peripherals in the virtual machine U disc , The Internet .
Other uncontrolled computers , That is, copy the data to other uncontrolled computers in the network , transit
Upload online , By building an upload server on the public network , Bypass Internet Behavior Management
Data distortion :
Write a console program , Print the code to DOS On the console, and then save the screen information as ;
Write the code to Log Log file , Or write code to shared memory , Then another program reads away .
Write interprocess communication program , Pass the code through socket, news ,LPC,COM,mutex, Shear plate , Pipeline and other interprocess communication methods , Transfer to send the data ;
adopt IIS/Tomcat etc. web The parser transfers , Publish the code data as a web page , Then browse the browser and save as , Or just write txt box , Copy all the code during initialization ;
Peripheral transfer
For embedded development scenarios , You can use the serial port ,U mouth , The network port burns the code to the equipment and leaks the secret
SDC Sandbox anti disclosure software
Developed by shenxinda SDC Sandbox leak proof products , Adopt kernel defense in depth , It is a driver level anti disclosure Software . Do not encrypt files , A sandbox is like a container , The container contains our confidential information . The documents we work on are all in sandboxes . The sandbox is completely isolated from ordinary computers . You might ask , What if I want to access the Internet , All programs to access the Internet are launched from the tray , Such as browser , Chat software, etc .SDC The sandbox is divided into the following parts : The management end , Confidential end , Documents are sent out , client .
The management end : Sandbox Control Center , Control all clients . The control of the client covers all aspects . Let me give you a few control functions : Reverse screenshot When someone wants to view some confidential information of the company remotely to the employee's computer ,SDC The client will control the remote software , Remote people see a black screen . But the computers on the staff side are in normal use . If you can control, you can let go . clipboard In sandbox mode, employees want to copy and paste company data such as files to the Internet through the clipboard ,SDC Sandbox is controlled , You can control the maximum number of clipping words .
Confidential end : Escort the server , Ordinary computers do not have access to confidential servers . Only sandbox computers can access , Do not encrypt the company's data , Protect data to the greatest extent .
client : Normal mode and sandbox mode . All software installation should be in sandbox mode . Work must be in sandbox mode , Because all the working data are on the encrypted disk , Sandbox can only be accessed in encrypted mode . In sandbox mode, it is isolated from the outside world . To access the Internet, only programs launched from the tray can , And follow the principle of only getting in and not getting out , Can get files from the Internet to the sandbox computer , However, to send documents from this machine to the Internet, you have to go through document approval .
Documents are sent out : A file distribution system is installed on a computer . The of this computer ip That is, the address where the document is sent out . Each sandbox employee matches an account number for sending out files . The specific approval method is not cumbersome here .

边栏推荐
- (4) Web security | penetration testing | network security web site source code and related analysis
- Oracle database 11gr2 uses TDE transparent data encryption to report an error ora28353. If you run to close the wallet, you will report an error ora28365. If you run to open the wallet, you will repor
- Word delete the contents in brackets
- Project GFS data download
- 烧录场景下的源代码防泄密方案分享
- OpenJudge NOI 2.1 1661:Bomb Game
- OpenJudge NOI 2.1 1749:数字方格
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- C语言 简单易懂的高精度加法
- SSM学习
猜你喜欢

QT color is converted to string and uint
![When the Jericho development board is powered on, you can open the NRF app with your mobile phone [article]](/img/3e/3d5bff87995b4a9fac093a6d9f9473.png)
When the Jericho development board is powered on, you can open the NRF app with your mobile phone [article]
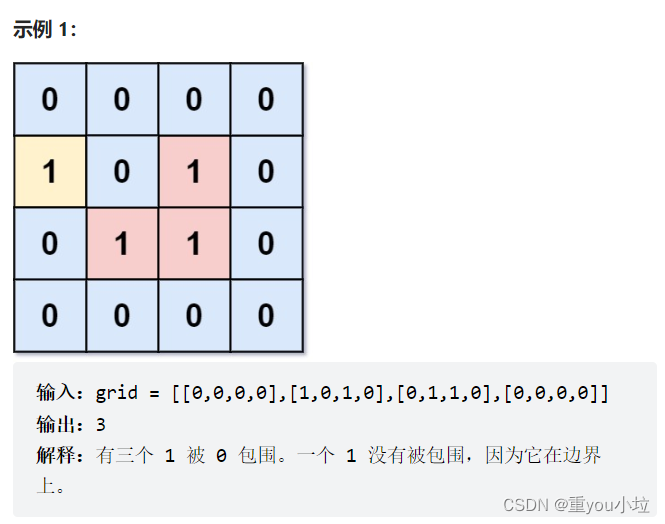
leetcode1020. Number of enclaves (medium)
![Ble of Jerry [chapter]](/img/00/27486ad68bf491997d10e387c32dd4.png)
Ble of Jerry [chapter]
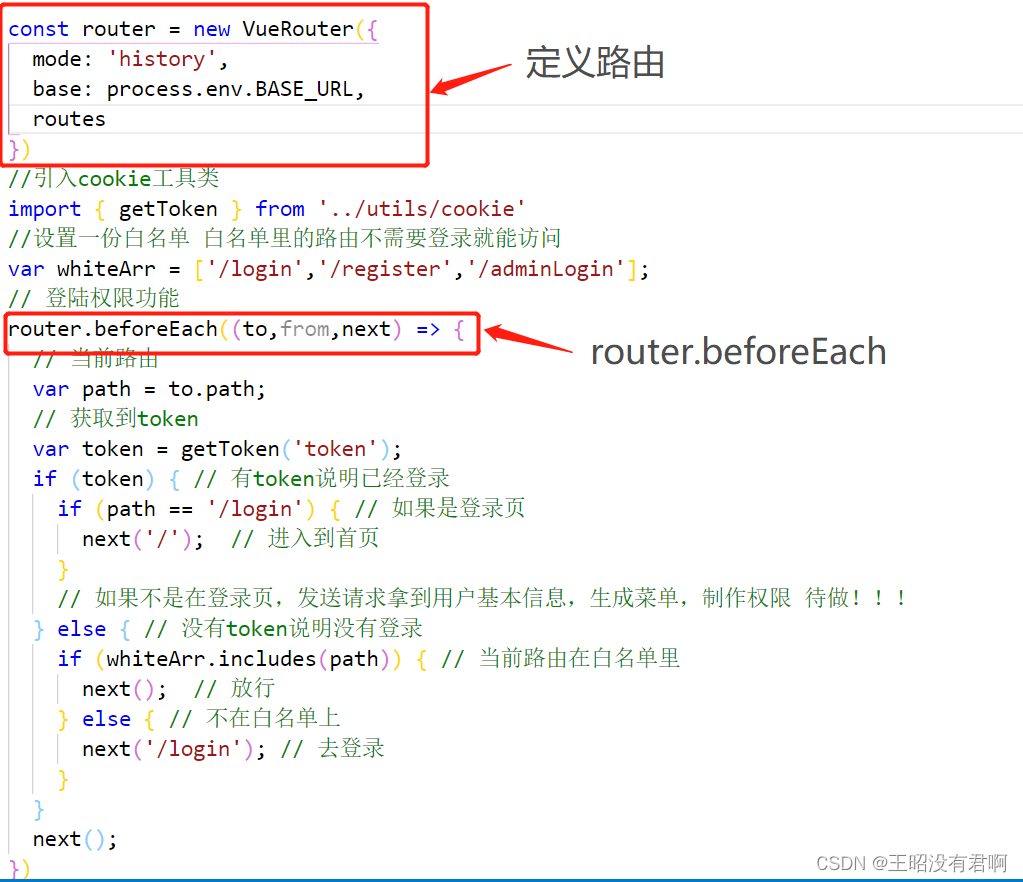
Uncaught TypeError: Cannot red propertites of undefined(reading ‘beforeEach‘)解决方案
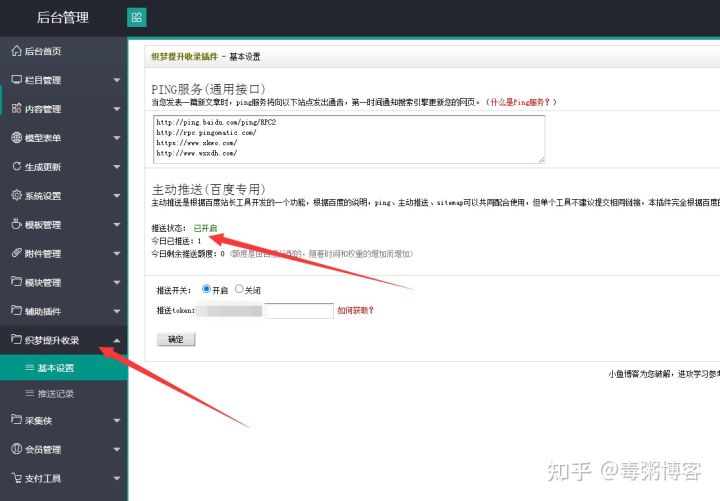
The first Baidu push plug-in of dream weaving fully automatic collection Optimization SEO collection module

The author is dead? AI is conquering mankind with art
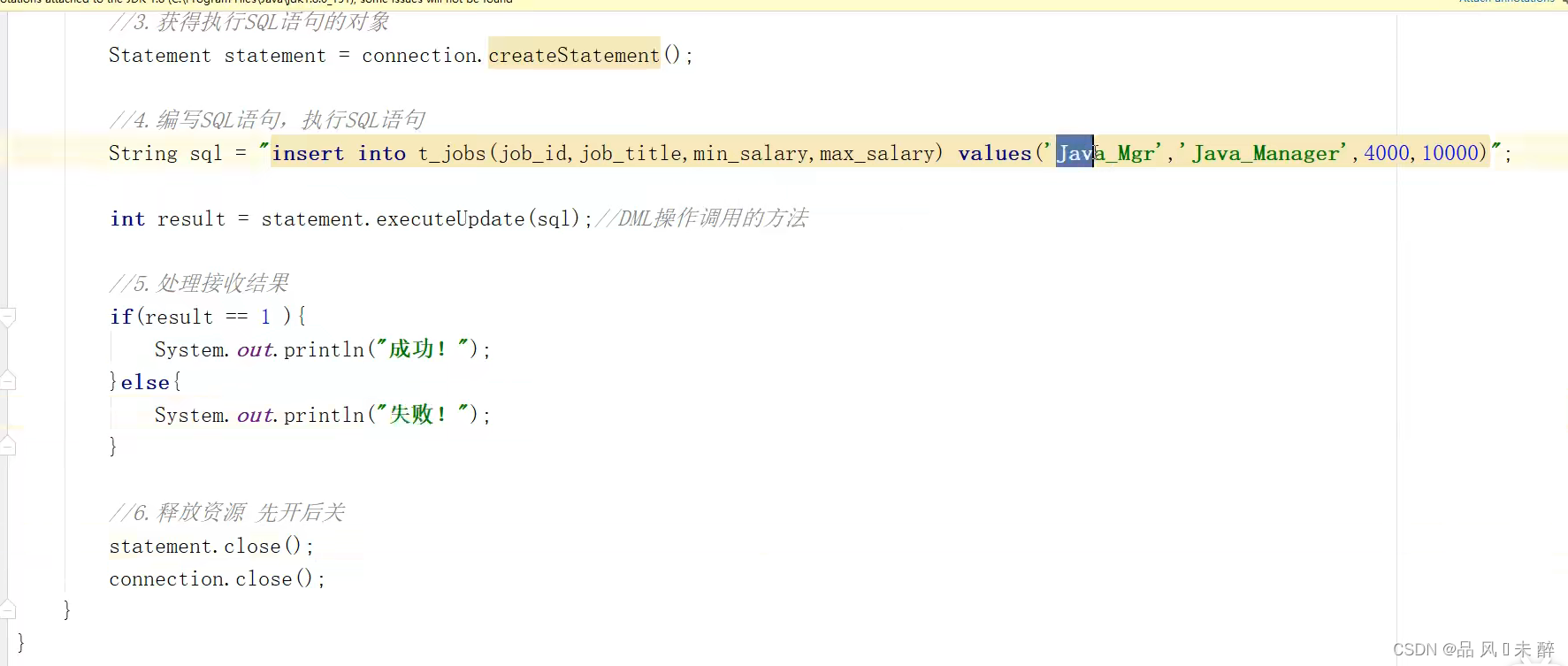
JDBC学习笔记
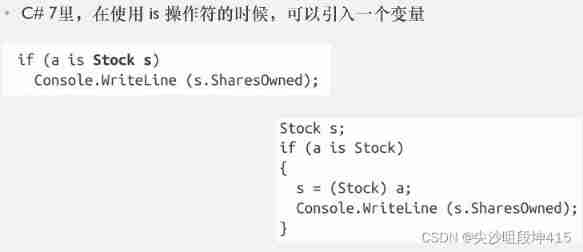
C - Inheritance - polymorphism - virtual function member (lower)
【MySQL学习笔记32】mvcc
随机推荐
Jerry's ad series MIDI function description [chapter]
Uncaught TypeError: Cannot red propertites of undefined(reading ‘beforeEach‘)解决方案
Raspberry pie 3B update VIM
杰理之开发板上电开机,就可以手机打开 NRF 的 APP【篇】
Structure summary of SystemVerilog integrable model
OpenJudge NOI 2.1 1749:数字方格
Ble of Jerry [chapter]
#systemverilog# 可综合模型的结构总结
Uni app third party package configuration network request
Solution to the problem of breakthrough in OWASP juice shop shooting range
TypeScript接口与泛型的使用
Twelve rules for naming variables
qt颜色与字符串、uint相互转换
How are the open source Netease cloud music API projects implemented?
Excel的相关操作
SEO学习的最好方式:搜索引擎
js对象获取属性的方法(.和[]方式)
【JDBC】快速入门教程
How to delete all the words before or after a symbol in word
树莓派串口登录与SSH登录方法