当前位置:网站首页>Bugku CTF daily question: do you want seeds? Blackmailed
Bugku CTF daily question: do you want seeds? Blackmailed
2022-07-06 07:17:00 【Hua Su Mo on the other bank】
Want seeds
Open and find it is torrent.jpg
winhex Open and find something strange , But there is no hint
An exception was found when opening the property 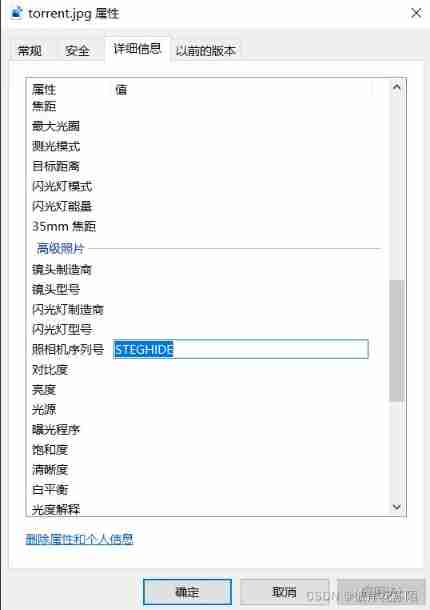
Baidu found it was a tool , Install it first , It should be hidden
After installation, I used it and found that it was hidden 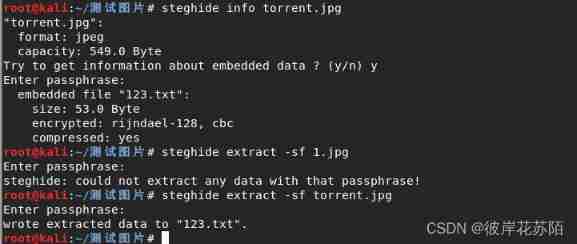
Extracted 123.txt, Open and find the network disk link , After downloading it is a compressed package
After opening, I found that I need a password , however hint.txt You can see , The discovery tip is six six six
So try it with violence , As a result, it happened 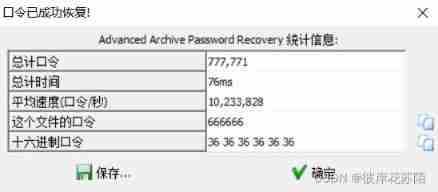
decompression 123.zip After that, I found that the height and width of the picture were obviously wrong , After modification, a paragraph of letters appeared

And then in winhex Open the last side of this picture and find a website 
After opening it, I found that it was solved by Virginia password
It is to solve the plaintext without a secret key
Throw in the obtained letters , Change the language to english Get back flag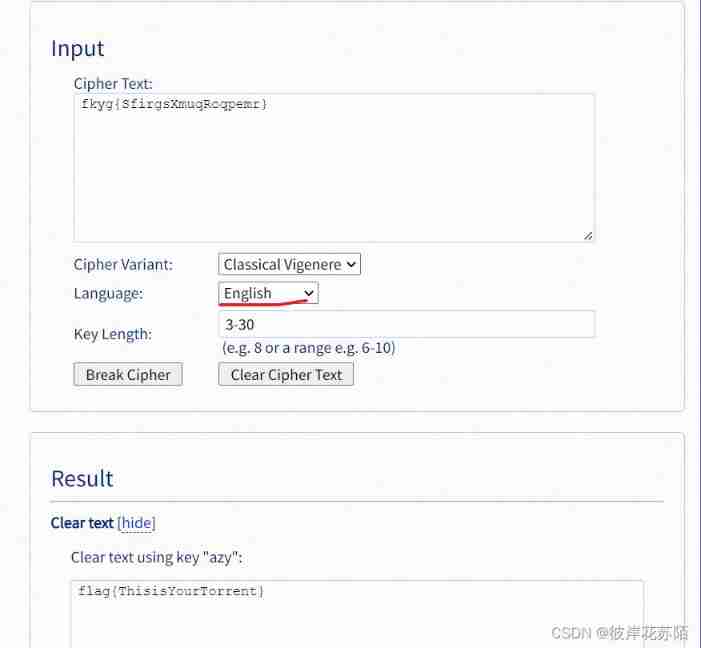
Blackmailed
Opening is a tinder file
Because the title description has :“ When checking the file, I found that the data directory of tinder was not encrypted ”
I learned on the Internet that the isolation directory of tinder is C:\ProgramData\Huorong
( Check show hidden directory above to see ProgramData Catalog )
Because the tinder file is installed on the computer , Therefore, throwing the tinder file of the title into it will show that it is in use ·, So we have to unload the tinder first , Then replace the entire file , Then install the tinder , At this time, you can see a file in the isolation directory of tinder 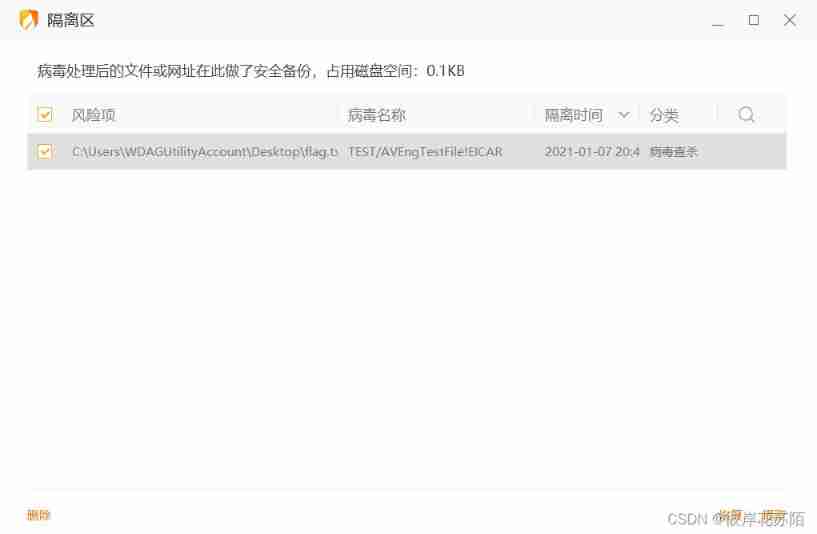
Click reply to get a flag.txt, Open it and you'll get flag
边栏推荐
猜你喜欢
MPLS experiment
学go之路(一)go的基本介绍到第一个helloworld
Depth residual network
Proteus -- Serial Communication parity flag mode
JDBC learning notes
呆错图床系统源码图片CDN加速与破解防盗链功能
A brief introduction of reverseme in misc in the world of attack and defense

The best way to learn SEO: search engine

杰理之蓝牙设备想要发送数据给手机,需要手机先打开 notify 通道【篇】
leetcode1020. 飞地的数量(中等)
随机推荐
Supervisor usage document
Leetcode 78: subset
升级版手机检测微信工具小程序源码-支持多种流量主模式
杰理之BLE【篇】
You deserve this high-value open-source third-party Netease cloud music player
C - Inheritance - polymorphism - virtual function member (lower)
UWA pipeline version 2.2.1 update instructions
Applied stochastic process 01: basic concepts of stochastic process
Uni app practical project
leetcode841. Keys and rooms (medium)
【mysql学习笔记29】触发器
Idea console color log
Chrome view page FPS
leetcode704. 二分查找(查找某个元素,简单,不同写法)
Wechat brain competition answer applet_ Support the flow main belt with the latest question bank file
Uncaught typeerror: cannot red properties of undefined (reading 'beforeeach') solution
Detailed explanation | detailed explanation of internal mechanism of industrial robot
The best way to learn SEO: search engine
树莓派3B更新vim
Simple use of JWT