当前位置:网站首页>Game attack and defense world reverse
Game attack and defense world reverse
2022-07-07 08:09:00 【Day-3】
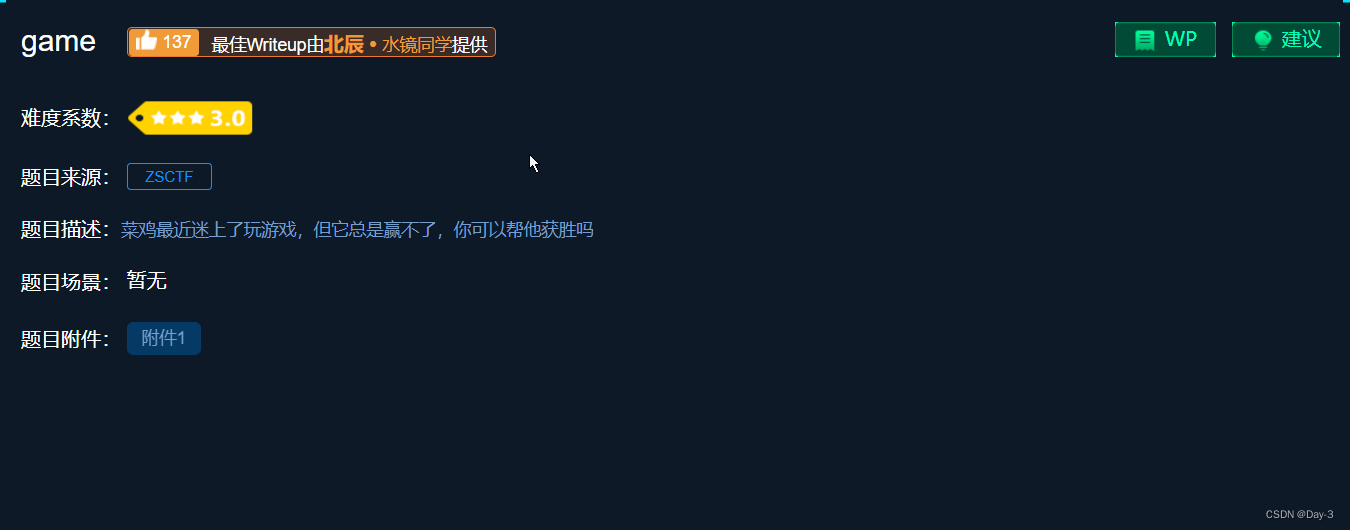
Check the operation file .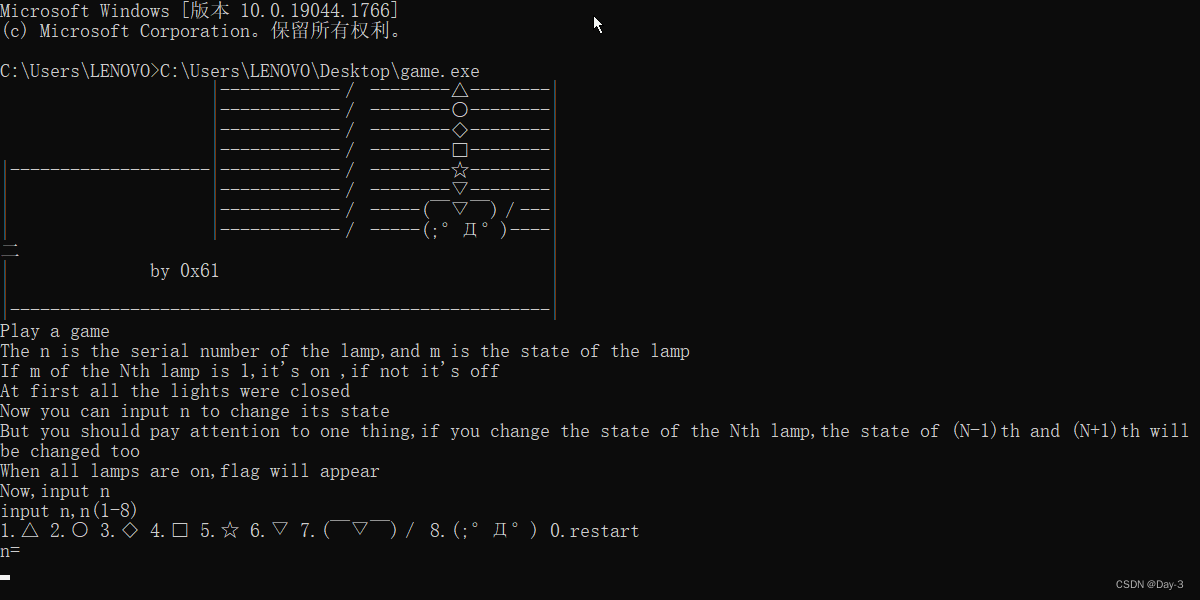
A little game , Several lights must be on .
Drag in IDA View the reassembly code in .
int __cdecl main_0(int argc, const char **argv, const char **envp)
{
char v4; // [esp+0h] [ebp-FCh]
char v5; // [esp+0h] [ebp-FCh]
char v6; // [esp+0h] [ebp-FCh]
char v7; // [esp+0h] [ebp-FCh]
char v8; // [esp+0h] [ebp-FCh]
char v9; // [esp+0h] [ebp-FCh]
char v10; // [esp+0h] [ebp-FCh]
char v11; // [esp+0h] [ebp-FCh]
char v12; // [esp+0h] [ebp-FCh]
char v13; // [esp+0h] [ebp-FCh]
char v14; // [esp+0h] [ebp-FCh]
char v15; // [esp+0h] [ebp-FCh]
char v16; // [esp+0h] [ebp-FCh]
char v17; // [esp+0h] [ebp-FCh]
char v18; // [esp+0h] [ebp-FCh]
char v19; // [esp+0h] [ebp-FCh]
char v20; // [esp+0h] [ebp-FCh]
char v21; // [esp+0h] [ebp-FCh]
char v22; // [esp+0h] [ebp-FCh]
char v23; // [esp+0h] [ebp-FCh]
int i; // [esp+DCh] [ebp-20h]
int v25; // [esp+F4h] [ebp-8h] BYREF
printf((int)&unk_50B110, v4);
printf((int)&unk_50B158, v5);
printf((int)&unk_50B1A0, v6);
printf((int)&unk_50B1E8, v7);
printf((int)&unk_50B230, v8);
printf((int)&unk_50B278, v9);
printf((int)&unk_50B2C0, v10);
printf((int)&unk_50B308, v11);
printf((int)&unk_50AFD0, v12);
printf((int)"| by 0x61 |\n", v13);
printf((int)"| |\n", v14);
printf((int)"|------------------------------------------------------|\n", v15);
printf(
(int)"Play a game\n"
"The n is the serial number of the lamp,and m is the state of the lamp\n"
"If m of the Nth lamp is 1,it's on ,if not it's off\n"
"At first all the lights were closed\n",
v16);
printf((int)"Now you can input n to change its state\n", v17);
printf(
(int)"But you should pay attention to one thing,if you change the state of the Nth lamp,the state of (N-1)th and (N+1"
")th will be changed too\n",
v18);
printf((int)"When all lamps are on,flag will appear\n", v19);
printf((int)"Now,input n \n", v20);
while ( 1 )
{
while ( 1 )
{
printf((int)"input n,n(1-8)\n", v21);
sub_459418();
printf((int)"n=", v22);
sub_4596D4("%d", &v25);
printf((int)"\n", v23);
if ( v25 >= 0 && v25 <= 8 )
break;
printf((int)"sorry,n error,try again\n", v21);
}
if ( v25 )
{
sub_4576D6(v25 - 1);
}
else
{
for ( i = 0; i < 8; ++i )
{
if ( (unsigned int)i >= 9 )
j____report_rangecheckfailure();
byte_532E28[i] = 0;
}
}
j__system("CLS");
sub_458054();
if ( byte_532E28[0] == 1
&& byte_532E28[1] == 1
&& byte_532E28[2] == 1
&& byte_532E28[3] == 1
&& byte_532E28[4] == 1
&& byte_532E28[5] == 1
&& byte_532E28[6] == 1
&& byte_532E28[7] == 1 )
{
sub_457AB4();
}
}
}
It's not hard to see. sub_457AB4() It contains flag Function of , Get into .
The result of this function is Flag, Modify the program :
#include <stdio.h>
#include <string.h>
int main()
{
int i; // [esp+D0h] [ebp-94h]
char v3[57]; // [esp+DCh] [ebp-88h] BYREF
char v4[57]; // [esp+120h] [ebp-44h]
printf((int)"done!!! the flag is ");
v4[0] = 18;
v4[1] = 64;
v4[2] = 98;
v4[3] = 5;
v4[4] = 2;
v4[5] = 4;
v4[6] = 6;
v4[7] = 3;
v4[8] = 6;
v4[9] = 48;
v4[10] = 49;
v4[11] = 65;
v4[12] = 32;
v4[13] = 12;
v4[14] = 48;
v4[15] = 65;
v4[16] = 31;
v4[17] = 78;
v4[18] = 62;
v4[19] = 32;
v4[20] = 49;
v4[21] = 32;
v4[22] = 1;
v4[23] = 57;
v4[24] = 96;
v4[25] = 3;
v4[26] = 21;
v4[27] = 9;
v4[28] = 4;
v4[29] = 62;
v4[30] = 3;
v4[31] = 5;
v4[32] = 4;
v4[33] = 1;
v4[34] = 2;
v4[35] = 3;
v4[36] = 44;
v4[37] = 65;
v4[38] = 78;
v4[39] = 32;
v4[40] = 16;
v4[41] = 97;
v4[42] = 54;
v4[43] = 16;
v4[44] = 44;
v4[45] = 52;
v4[46] = 32;
v4[47] = 64;
v4[48] = 89;
v4[49] = 45;
v4[50] = 32;
v4[51] = 65;
v4[52] = 15;
v4[53] = 34;
v4[54] = 18;
v4[55] = 16;
v4[56] = 0;
memcpy(v3, "{ ", 2);
v3[2] = 18;
v3[3] = 98;
v3[4] = 119;
v3[5] = 108;
v3[6] = 65;
v3[7] = 41;
v3[8] = 124;
v3[9] = 80;
v3[10] = 125;
v3[11] = 38;
v3[12] = 124;
v3[13] = 111;
v3[14] = 74;
v3[15] = 49;
v3[16] = 83;
v3[17] = 108;
v3[18] = 94;
v3[19] = 108;
v3[20] = 84;
v3[21] = 6;
memcpy(&v3[22], "`S,yhn _uec{", 12);
v3[34] = 127;
v3[35] = 119;
v3[36] = 96;
v3[37] = 48;
v3[38] = 107;
v3[39] = 71;
v3[40] = 92;
v3[41] = 29;
v3[42] = 81;
v3[43] = 107;
v3[44] = 90;
v3[45] = 85;
v3[46] = 64;
v3[47] = 12;
v3[48] = 43;
v3[49] = 76;
v3[50] = 86;
v3[51] = 13;
v3[52] = 114;
v3[53] = 1;
strcpy(&v3[54], "u~");
for (i = 0; i < 56; ++i)
{
v3[i] ^= v4[i];
v3[i] ^= 0x13u;
}
printf("%s\n", v3);
return 0;
}
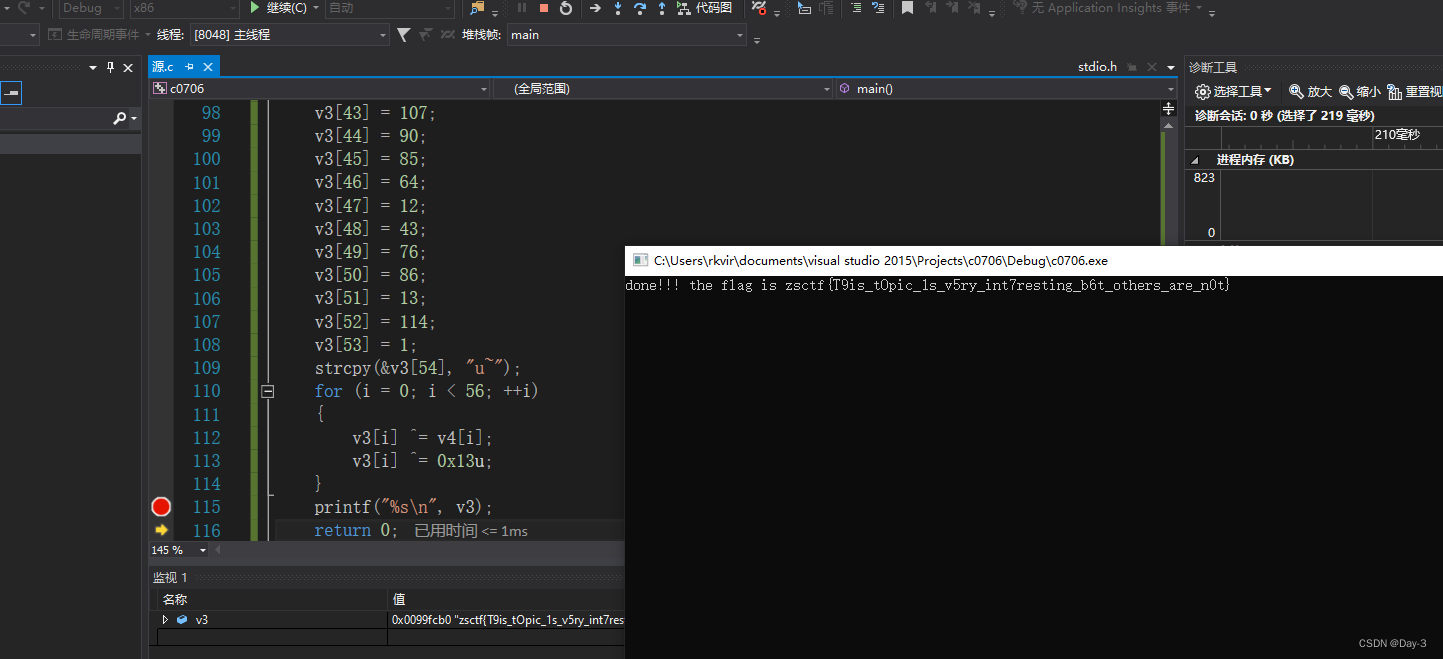
obtain Flag.
边栏推荐
- [VHDL parallel statement execution]
- ZCMU--1492: Problem D(C语言)
- Fast parsing intranet penetration escorts the document encryption industry
- 2022 recurrent training question bank and answers of refrigeration and air conditioning equipment operation
- Binary tree and heap building in C language
- buureservewp(2)
- 【数字IC验证快速入门】12、SystemVerilog TestBench(SVTB)入门
- 通俗易懂单点登录SSO
- 芯片 設計資料下載
- 2022 tea master (intermediate) examination questions and mock examination
猜你喜欢
Linux server development, MySQL index principle and optimization
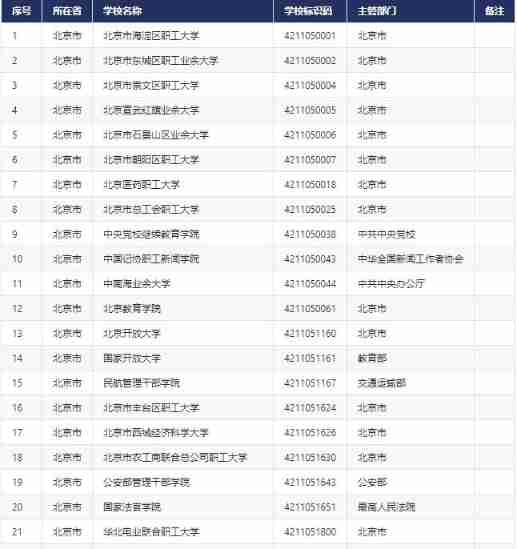
Cnopendata list data of Chinese colleges and Universities
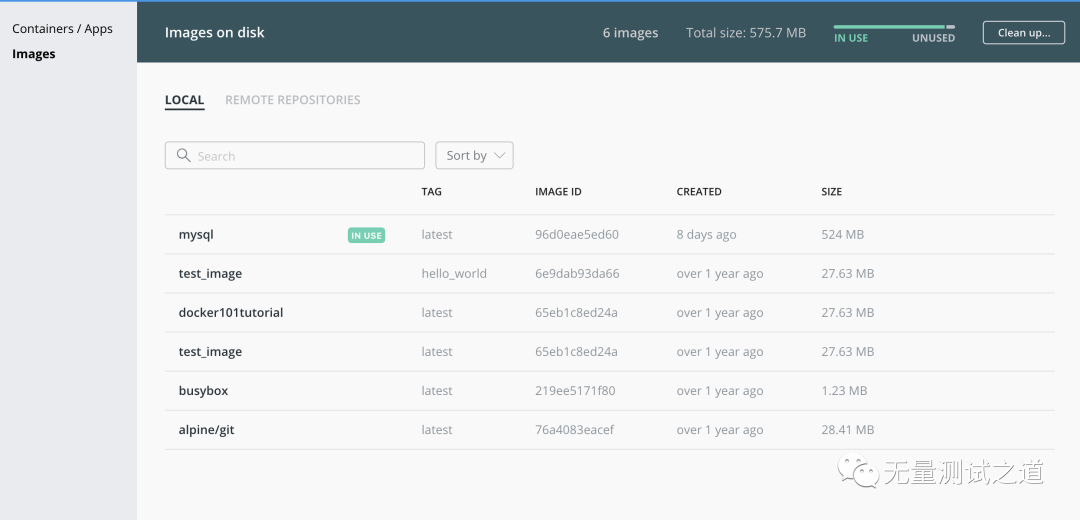
Who has docker to install MySQL locally?
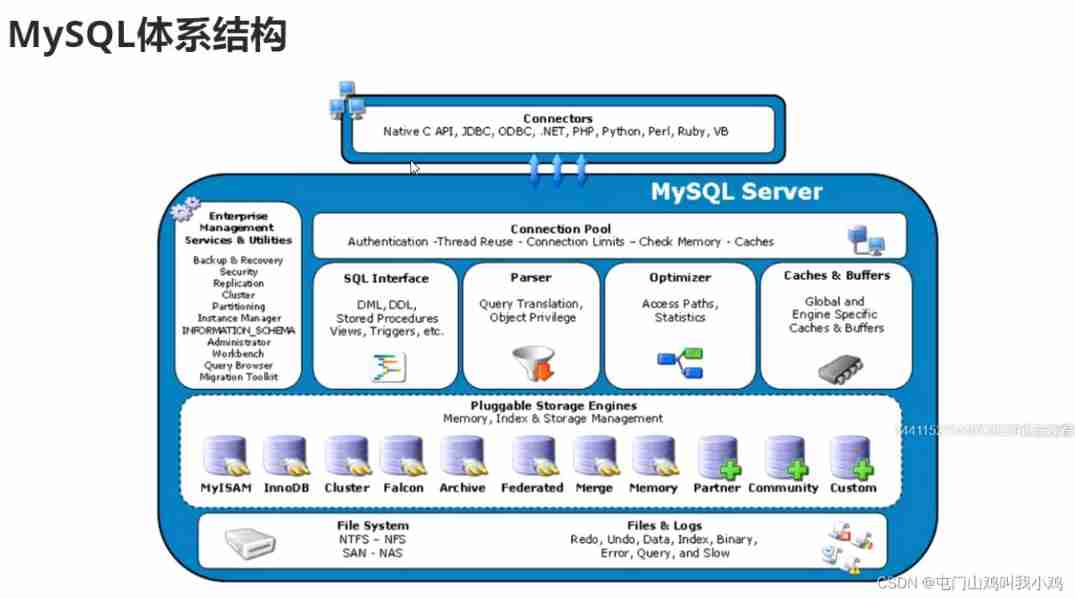
Linux server development, SQL statements, indexes, views, stored procedures, triggers

LeetCode简单题之判断一个数的数字计数是否等于数位的值
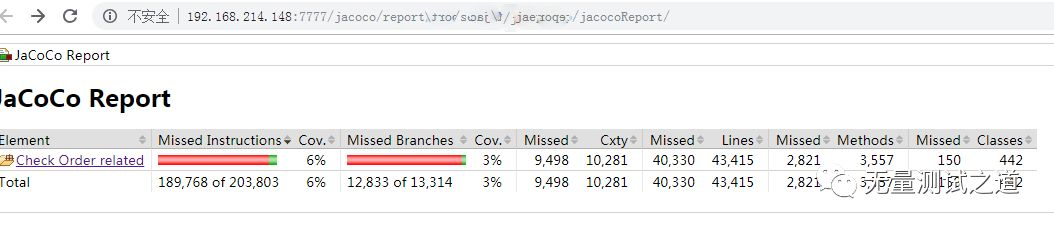
Quickly use Jacobo code coverage statistics
【数字IC验证快速入门】11、Verilog TestBench(VTB)入门

海信电视开启开发者模式
Thinkcmf6.0 installation tutorial
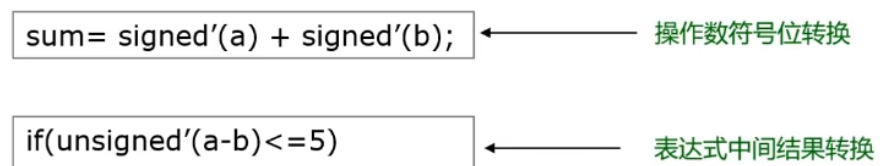
【數字IC驗證快速入門】15、SystemVerilog學習之基本語法2(操作符、類型轉換、循環、Task/Function...內含實踐練習)
随机推荐
2022 recurrent training question bank and answers of refrigeration and air conditioning equipment operation
[matlab] when matrix multiplication in Simulink user-defined function does not work properly, matrix multiplication module in module library can be used instead
2022 National latest fire-fighting facility operator (primary fire-fighting facility operator) simulation questions and answers
追风赶月莫停留,平芜尽处是春山
Blob 对象介绍
Relevant data of current limiting
Chip information website Yite Chuangxin
Content of string
offer收割机:两个长字符串数字相加求和(经典面试算法题)
Summary of redis functions
Paddlepaddle 29 dynamically modify the network structure without model definition code (relu changes to prelu, conv2d changes to conv3d, 2D semantic segmentation model changes to 3D semantic segmentat
Find the mode in the binary search tree (use medium order traversal as an ordered array)
Myabtis_Plus
[Matlab] Simulink 自定义函数中的矩阵乘法工作不正常时可以使用模块库中的矩阵乘法模块代替
Force buckle 145 Binary Tree Postorder Traversal
[step on the pit series] H5 cross domain problem of uniapp
Dedecms collects content without writing rules
LeetCode中等题之我的日程安排表 I
Pytorch(六) —— 模型调优tricks
Merging binary trees by recursion