当前位置:网站首页>Fast parsing intranet penetration escorts the document encryption industry
Fast parsing intranet penetration escorts the document encryption industry
2022-07-07 08:07:00 【Fast parsing】
With the rapid development of information technology , People's demand for information security comes one after another , Talent competition 、 market competition 、 The financial crisis has brought great risks to the development of enterprises and institutions , Internal theft 、 The hacker attacks 、 Unconscious leak and other secret stealing methods have become between people 、 Potential safety hazards between enterprises . The traditional three aspects of information security ( A firewall 、 Intrusion detection 、 Anti virus ) As the infrastructure of network construction of enterprises and institutions , It is far from meeting the security needs of users . Document encryption Industry position Nowadays, the main force of information security protection , This kind of technology Encrypt the data itself , Whether it's off the operating system , Or illegally leave the safe environment , User data itself is secure , The dependence on the environment is relatively small . Strong market demand , yes In recent years Document encryption industry The fundamental source of rapid development ; The continuous injection of funds has become another powerful driving force for document encryption enterprises . Protect a large number of internal confidential documents , Yes Improve the value of the enterprise's own intranet , Enhance the market competitiveness of enterprise business , Realize the sustainable and steady development of the enterprise Of great significance .

The main challenges faced by the document encryption industry mainly include the following aspects :1. High server costs . Traditional solutions need to rent servers , Enterprises bear heavy costs 、 Low cost performance , Even if the enterprise has a public network ip, You still need to do port mapping in the router , It is equivalent to that the intranet resources are exposed on the public network , Increase the risk of being attacked . High security requirements . You need to connect to the client enterprise server , And open the server document , At the same time, ensure that documents will not be stolen , High requirements for data transmission security , In the transmission process, we should not only be stable, but also prevent privacy leakage .3. There are various personalized needs . The client enterprise server configuration is different 、 The development environment is diverse , In the network communication, there are many kinds of structures coexisting , There is an urgent need for highly adaptable solutions .
Fast parsing intranet penetration technology can provide Document encryption industry Provide reasonable solutions .1. stay company Website server installation Jinwanwei quick parsing client .2. Log in to jinwanwei quick parsing client , Add mapping on the client side , Map the internal network port to the external network .3. Customer enterprise Personnel can access the system according to the generated domain name , Get the encryption policy , The data will also be synchronously transmitted to the headquarters server .
Fast parsing intranet penetration can help the document encryption industry achieve Low cost Receive visitors . Avoid high-cost lines and server rental cost , Reduce Business costs ; No You need to do port mapping in the router , Customers and employees can Realize remote access . Multiple protections . Bank level data Transmission encryption , Security data Security , High brand guarantee stability , guarantee Full encryption protection , Prevent leaks . Personalized service support . Intelligent product upgrade , Full agreement support , according to Client enterprise server configuration 、 The development environment is diverse sex May adopt Personalized service programme .
边栏推荐
- 贝叶斯定律
- 【数字IC验证快速入门】13、SystemVerilog interface 和 program 学习
- 调用 pytorch API完成线性回归
- Linux Installation MySQL 8.0 configuration
- JS quick start (I)
- Linux server development, redis source code storage principle and data model
- The zblog plug-in supports the plug-in pushed by Baidu Sogou 360
- Topic not received? Try this
- [UVM practice] Chapter 2: a simple UVM verification platform (2) only driver verification platform
- 快解析内网穿透为文档加密行业保驾护航
猜你喜欢

快解析内网穿透为文档加密行业保驾护航
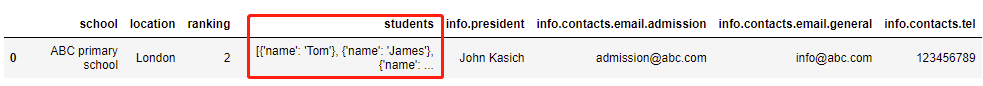
json 数据展平pd.json_normalize
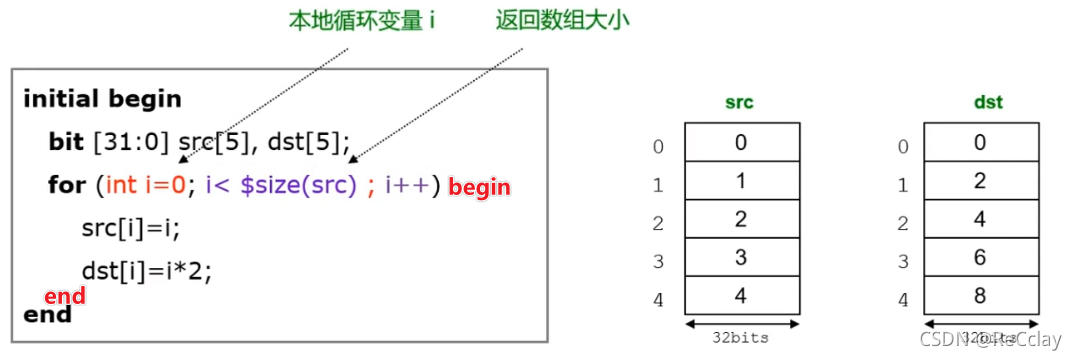
【数字IC验证快速入门】14、SystemVerilog学习之基本语法1(数组、队列、结构体、枚举、字符串...内含实践练习)
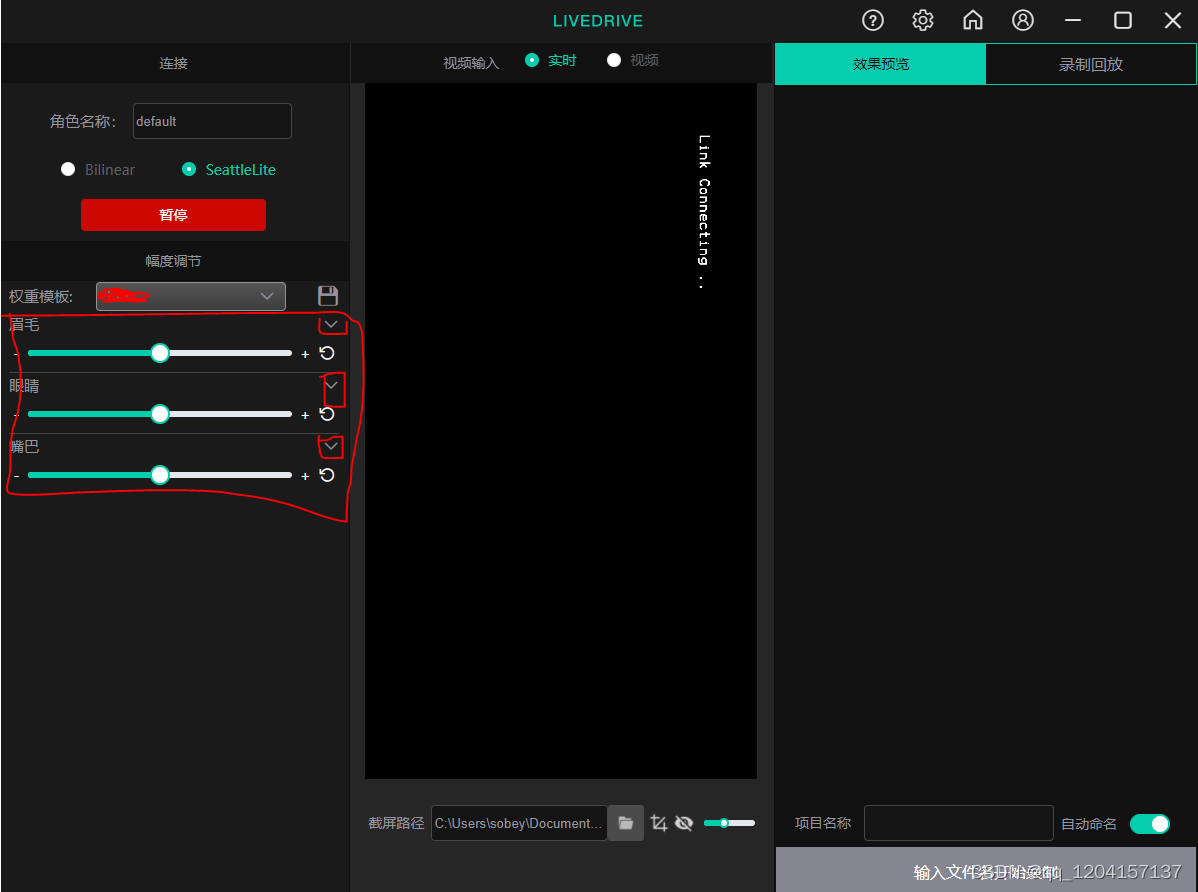
Avatary的LiveDriver试用体验
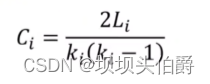
复杂网络建模(一)

3D reconstruction - stereo correction

Niu Mei's mathematical problem --- combinatorial number

2022 recurrent training question bank and answers of refrigeration and air conditioning equipment operation

2022 Inner Mongolia latest advanced fire facility operator simulation examination question bank and answers
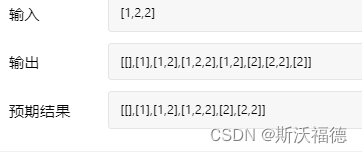
Leetcode 90: subset II
随机推荐
These five fishing artifacts are too hot! Programmer: I know, delete it quickly!
QT learning 28 toolbar in the main window
offer收割机:两个长字符串数字相加求和(经典面试算法题)
DNS server configuration
[UVM basics] summary of important knowledge points of "UVM practice" (continuous update...)
探索干货篇!Apifox 建设思路
The element with setfieldsvalue set is obtained as undefined with GetFieldValue
Content of string
[UVM foundation] what is transaction
Empire CMS collection Empire template program general
The legend about reading the configuration file under SRC
追风赶月莫停留,平芜尽处是春山
快解析内网穿透助力外贸管理行业应对多种挑战
海信电视开启开发者模式
2022年全国最新消防设施操作员(初级消防设施操作员)模拟题及答案
Summary of redis functions
C语言队列
3D reconstruction - stereo correction
CTF daily question day43 rsa5
Roulette chart 2 - writing of roulette chart code