当前位置:网站首页>Podman can learn in one piece
Podman can learn in one piece
2022-08-03 06:32:00 【Got a Pikachu】
Podman入门
什么是podman?
PodmanIs a kind of no daemon、开源的 Linux 原生工具,旨在使用开放容器倡议 ( OCI )容器和容器映像轻松查找、运行、构建、共享和部署应用程序.Podman 提供了任何使用过 Docker容器引擎的人都熟悉的命令行界面 (CLI) .大多数用户可以简单地将 Docker 别名为 Podman(别名 docker=podman),没有任何问题.与其他常见的容器引擎(Docker、CRI-O、containerd)类似,Podman 依赖于符合 OCI 的容器运行时(runc、crun、runv 等)与操作系统交互并创建正在运行的容器.这使得 Podman 创建的运行容器与任何其他常见容器引擎创建的容器几乎没有区别.
Podman 控制下的容器可以由 root 或非特权用户运行.Podman 使用libpod库管理整个容器生态系统,包括 pod、容器、容器镜像和容器卷.Podman 专注于帮助您维护和修改 OCI 容器映像的所有命令和功能,例如拉取和标记.它允许您在生产环境中创建、运行和维护这些容器和容器映像.
有一个 RESTFul API 来管理容器.我们还有一个可以与 RESTFul 服务交互的远程 Podman 客户端.我们目前支持 Linux、Mac 和 Windows 上的客户端.RESTFul 服务仅在 Linux 上受支持.
如果您完全不熟悉容器,我们建议您查看简介.对于高级用户或来自 Docker 的用户,请查看我们的教程.对于高级用户和贡献者,You can view our命令Page to obtain the Podman CLI 的非常详细的信息.最后,对于寻求如何与 Podman API 交互的开发人员,请参阅我们的 API 文档参考.
Podman工作机制
Podman 原来是 CRI-O 项目的一部分,后来被分离成一个单独的项目叫 libpod.Podman 的使用体验和 Docker类似,不同的是 Podman 没有 daemon.以前使用 Docker CLI 的时候,Docker CLI 会通过 gRPC API去跟 Docker Engine 说「我要启动一个容器」,然后 Docker Engine 才会通过 OCI Containerruntime(默认是 runc)来启动一个容器.这就意味着容器的进程不可能是 Docker CLI 的子进程,而是 DockerEngine 的子进程.
Podman 比较简单粗暴,它不使用 Daemon,而是直接通过 OCI runtime(默认也是 runc)来启动容器,所以容器的进程是podman 的子进程.这比较像 Linux 的 fork/exec 模型,而 Docker 采用的是 C/S(客户端/服务器)模型.与
C/S 模型相比,fork/exec 模型有很多优势,比如:系统管理员可以知道某个容器进程到底是谁启动的.
如果利用 cgroup 对 podman 做一些限制,那么所有创建的容器都会被限制.
SD_NOTIFY : 如果将 podman 命令放入 systemd 单元文件中,容器进程可以通过 podman 返回通知,表明服务已准备好接收任务.
socket 激活 : 可以将连接的 socket 从 systemd 传递到 podman,并传递到容器进程以便使用它们.
docker与podman的区别
Docker 和 Podman 在管理容器方面提供了类似的功能,但是 Docker 的安全漏洞可能使 Podman 对于某些管理员来说更具吸引力.
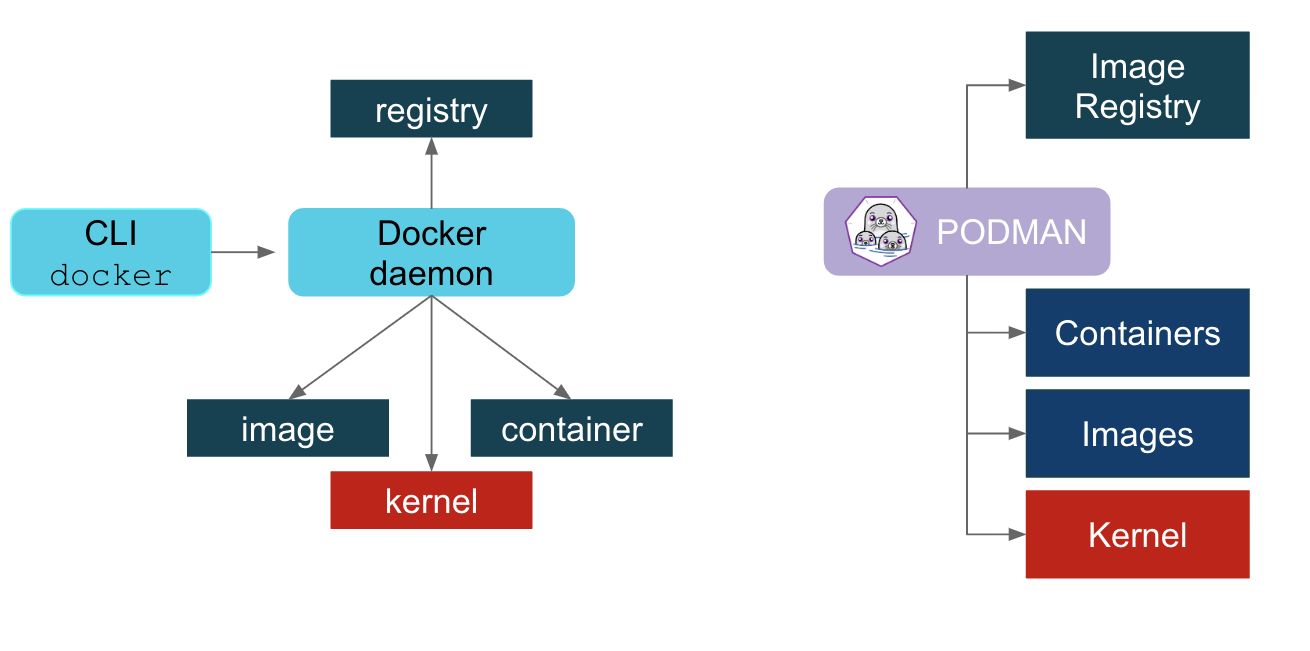
目前 Docker 已经成为许多 IT 管理员们事实上的标准,并且在开发人员中占有很大的份额. 但是,Podman 由于具有以非特权用户身份运行且无需守护进程的能力,因此与基本的 Docker 相比,它为管理员们提供了一些安全上的优势.
Docker 和 Podman 都提供许多相同的功能,例如,它们对开放式容器倡议(OCI)2 的运行时和镜像规范的支持,以及它们映射命令以创建和管理容器的能力. 但是,Docker 和 Podman 之间存在一些差异,包括安全方面的问题和对守护程序的依赖.3
考虑到 Podman 不使用守护进程来开发、管理和运行 OCI 容器,因此它必须在 Linux OS 上运行. 容器可以以 root 模式运行,也可以以非 root 运行模式运行.Docker 利用一个守护进程(该守护进程是一个持久的后台进程)来处理主机上所有容器的管理职责.Docker 依赖于客户端/服务端(C/S)架构,守护进程扮演着服务端的角色,而客户端通过命令行界面(CLI)进行通信.
Docker 使用本机 Windows 守护进程就可以很好地运行 Windows 或基于 Linux 的镜像.Podman 需要 Windows Subsystem for Linux 版本2(WSL2)才能正常运行. 因此,管理员们必须有2020年5月以后的 Windows 10 更新才能开始使用 Podman,因为这是第一个将 WSL2 作为更新的一部分的发行版.
安全
Docker 与 Podman 之间的一个重大区别涉及到安全问题. Docker 守护进程需要 root 权限,这在向用户提供 root 权限时带来了安全挑战. 这也意味着配置不当的 Docker 容器可以无限制地访问主机文件系统.管理员可以通过遵循一些基本的最佳实践来防止这种情况发生,比如仅使用来自受信任的供应商提供的容器镜像,但这种可能性仍然存在.
但是,管理员们使用 Podman 可以以非特权用户启动容器.这就使得 Podman 在锁定环境场景中具有了超越 Docker 的优势. 话虽如此,管理员们将无法以非特权用户身份在主机系统上执行任何需要 root 权限的命令.这包括映射主机上低于 1024 的任何特权端口号,以及默认的 HTTP 端口号 80.
此外,Docker 和 Podman 都使用 CLI 作为主要管理界面.但是,Docker 使用 REST API 终端与守护进程进行通信,且较旧的版本使用绑定到本机 IP 地址的 TCP socket 通信.这为跨站伪造利用提供了一个潜在的攻击面.Docker 在 0.5.2 版本中通过引入 UNIX socket 解决了这个漏洞(管理员可以使用传统的 UNIX 权限进行控制,以限制访问).考虑到 Podman 不依赖守护进程,因此不易受到此类攻击的影响.
容器编排
在容器编排方面,Kubernetes 已经成为占据主导地位的参与者.VMware 已采用 Kubernetes 作为 VM 以及连接到运行中的容器的所有其他设备的主要管理平台. Kubernetes 使用术语 pod 来定义共享某些资源的容器集合.Podman 通过实现 pod 命令,将多个容器作为一个实体进行管理,从而支持相同的概念.
同样,Docker 为容器编排提供了多个选项.Docker Swarm 是 Docker 维护的用于管理集群的本地工具.Docker 还与 Kubernetes 集成得很好,这是大多数开发团队的主流选择. 对于 Windows 部署,管理员可以选择在安装过程中启用 Kubernetes,从而可以从管理员的台式机或笔记本电脑直接访问 Kubernetes 命令.
更进一步来说,管理员可以围绕持续集成和持续部署(CI/CD)模型构建他们的应用程序,在该模型中,开发和测试工作可以基于一些简单的配置文件在任何地方进行.当管理员准备将发布推送到生产环境时,只需执行几个额外的步骤即可更改部署目标.
Podman 和 Docker 都符合 OCI 镜像标准,但仅就安全特性而言,Podman 是值得一试的.Podman 还提供了本地命令来支持 pod 的构建和测试,从而着眼于部署到一个运行 Kubernetes 的生产系统中.
部署podman与配置
LinuxVersion installation instance:
Podman 在 CentOS 7 的默认 Extras 存储库和 CentOS 8 和 Stream 的 AppStream 存储库中可用.
yum -y install podman
订阅,然后启用 Extras Channel and install Podman.
sudo subscription-manager repos --enable=rhel-7-server-extras-rpms
sudo yum -y install podman
Podmancontainer-tools与 Buildah 和 Skopeo Included in the module together.
sudo yum module enable -y container-tools:rhel8
sudo yum module install -y container-tools:rhel8
这container-tools:rhel8Is a rapid application flow,The latest scroll version contains tools.将container-tools:2.0Flow for Podman 1.6 的稳定版本.该命令yum module list container-toolsAccording to the available flow.
配置文件
[[email protected] ~]# vim /etc/containers/registries.conf
...Above the multi-line omit
# # An array of host[:port] registries to try when pulling an unqualified image, in order.
unqualified-search-registries = ["docker.io"] //修改此行
[[registry]]
prefix="docker.io"
location = "docker.mirrors.ustc.edu.cn" //Modify the three lines
...The following multi-line omit
podman常用操作
podman --help
要获得一些帮助并了解 Podman 的工作方式,您可以使用帮助:
$ podman --help
$ podman <subcommand> --help
有关更多详细信息,You can view the online help page:
$ man podman
$ man podman-<subcommand>
另请参阅Podman 故障排除指南 以查找有关如何解决常见配置错误的已知问题和提示.
[[email protected] ~]# podman --help
Manage pods, containers and images
管理豆荚,容器和图像
Usage:
用法:
podman [options] [command]
podman[选项](命令)
Available Commands:
可用命令:
attach Attach to a running container
Attach to a running container
auto-update Auto update containers according to their auto-update policy
Auto -update根据容器的自动更新策略自动更新容器
build Build an image using instructions from Containerfiles
Using a container file image building of instructions
commit Create new image based on the changed container
commitAccording to the change of the container to create a new image
container Manage containers
Container management container
cp Copy files/folders between a container and the local filesystem
cp在容器和本地文件系统之间复制文件/文件夹
create Create but do not start a container
create创建但不启动容器
diff Display the changes to the object's file system
diff显示对对象文件系统的更改
events Show podman events
events显示podman事件
exec Run a process in a running container
In a running container running processes
export Export container's filesystem contents as a tar archive
export将容器的文件系统内容导出为tar存档文件
generate Generate structured data based on containers, pods or volumes.
Generated based on the container、Pod or volume of structured data.
healthcheck Manage health checks on containers
healthcheckOperation condition of the management of container inspection
help Help about any command
helpFor any command to help
history Show history of a specified image
history显示指定图像的历史记录
image Manage images
Image processing, image
images List images in local storage
images列出本地存储中的图像
import Import a tarball to create a filesystem image
import通过导入tarballTo create the file system image
info Display podman system information
info显示podman系统信息
init Initialize one or more containers
初始化一个或多个容器
inspect Display the configuration of object denoted by ID
inspect显示IDSaid object configuration information
kill Kill one or more running containers with a specific signal
kill使用特定信号杀死一个或多个正在运行的容器
load Load image(s) from a tar archive
load从tarArchive file loading images
login Login to a container registry
login登录到容器注册表
logout Logout of a container registry
logoutContainer for cancellation of the registry
logs Fetch the logs of one or more containers
logs获取One or more containers日志
machine Manage a virtual machine
machine管理虚拟机
manifest Manipulate manifest lists and image indexes
操作清单列表和图像索引
mount Mount a working container's root filesystem
挂载一个工作容器的根文件系统
network Manage networks
Network management network
pause Pause all the processes in one or more containers
暂停一个或多个容器中的所有进程
play Play containers, pods or volumes from a structured file.
Play from a structured file container、Pod or volume.
pod Manage pods
Legume pod management
port List port mappings or a specific mapping for the container
port列出容器的端口映射或特定映射
ps List containers
ps 列表容器
pull Pull an image from a registry
pullTo extract an image from the registry
push Push an image to a specified destination
pushThe image to the specified destination
rename Rename an existing container
rename重命名现有容器
restart Restart one or more containers
restart重启一个或多个容器
rm Remove one or more containers
删除一个或多个容器
rmi Removes one or more images from local storage
rmi从本地存储中删除一个或多个映像
run Run a command in a new container
在新容器中运行命令
save Save image(s) to an archive
saveTo save the image to the archive
search Search registry for image
searchSearch image registry
secret Manage secrets
The secret of confidentiality management
start Start one or more containers
start启动一个或多个容器
stats Display a live stream of container resource usage statistics
statsDisplay real-time container resources the use of statistical information flow
stop Stop one or more containers
stop停止一个或多个容器
system Manage podman
系统管理podman
tag Add an additional name to a local image
tagAdd additional name for the local image
top Display the running processes of a container
top显示容器的运行进程
unmount Unmounts working container's root filesystem
卸载工作容器的根文件系统
unpause Unpause the processes in one or more containers
unpauseProcess in the cancellation of one or more containers
unshare Run a command in a modified user namespace
unshareIn the modified user namespace execute commands
untag Remove a name from a local image
untagDeleted from the local image a name
version Display the Podman Version Information
version显示Podman版本信息
volume Manage volumes
Volume management
wait Block on one or more containers
waitOne or more containersBlock
定义别名
[[email protected] ~]# alias docker=podman
[[email protected] ~]# podman ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
5a498cd2bbd9 docker.io/library/httpd:latest httpd-foreground 2 hours ago Up 2 hours ago 0.0.0.0:80->80/tcp optimistic_goldberg
07355b10b4ec docker.io/library/nginx:latest nginx -g daemon o... 2 hours ago Up 2 hours ago clever_shamir
[[email protected] ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
5a498cd2bbd9 docker.io/library/httpd:latest httpd-foreground 2 hours ago Up 2 hours ago 0.0.0.0:80->80/tcp optimistic_goldberg
07355b10b4ec docker.io/library/nginx:latest nginx -g daemon o... 2 hours ago Up 2 hours ago clever_shamir
podman version 查看版本号
[[email protected] ~]# podman version
Version: 3.3.1
API Version: 3.3.1
Go Version: go1.16.7
Built: Wed Nov 10 05:23:56 2021
OS/Arch: linux/amd64
podman info显示整个系统的信息
[[email protected] ~]# podman info
host:
arch: amd64
buildahVersion: 1.22.3
cgroupControllers:
- cpuset
- cpu
- cpuacct
- blkio
- memory
- devices
- freezer
- net_cls
- perf_event
- net_prio
- hugetlb
- pids
- rdma
cgroupManager: systemd
cgroupVersion: v1
conmon:
package: conmon-2.0.29-1.module_el8.5.0+890+6b136101.x86_64
path: /usr/bin/conmon
version: 'conmon version 2.0.29, commit: 84384406047fae626269133e1951c4b92eed7603'
cpus: 2
distribution:
distribution: '"centos"'
version: "8"
eventLogger: file
hostname: "103"
idMappings:
gidmap: null
uidmap: null
kernel: 4.18.0-305.3.1.el8.x86_64
linkmode: dynamic
memFree: 2451640320
memTotal: 3890188288
ociRuntime:
name: runc
package: runc-1.0.2-1.module_el8.5.0+911+f19012f9.x86_64
path: /usr/bin/runc
version: |-
runc version 1.0.2
spec: 1.0.2-dev
go: go1.16.7
libseccomp: 2.5.1
os: linux
remoteSocket:
path: /run/podman/podman.sock
security:
apparmorEnabled: false
capabilities: CAP_NET_RAW,CAP_CHOWN,CAP_DAC_OVERRIDE,CAP_FOWNER,CAP_FSETID,CAP_KILL,CAP_NET_BIND_SERVICE,CAP_SETFCAP,CAP_SETGID,CAP_SETPCAP,CAP_SETUID,CAP_SYS_CHROOT
rootless: false
seccompEnabled: true
seccompProfilePath: /usr/share/containers/seccomp.json
selinuxEnabled: false
serviceIsRemote: false
slirp4netns:
executable: /usr/bin/slirp4netns
package: slirp4netns-1.1.8-1.module_el8.5.0+890+6b136101.x86_64
version: |-
slirp4netns version 1.1.8
commit: d361001f495417b880f20329121e3aa431a8f90f
libslirp: 4.4.0
SLIRP_CONFIG_VERSION_MAX: 3
libseccomp: 2.5.1
swapFree: 4227854336
swapTotal: 4227854336
uptime: 2h 54m 23.24s (Approximately 0.08 days)
registries:
search:
- registry.fedoraproject.org
- registry.access.redhat.com
- registry.centos.org
- docker.io
- 81f6nfv3.mirror.aliyuncs.com
store:
configFile: /etc/containers/storage.conf
containerStore:
number: 2
paused: 0
running: 2
stopped: 0
graphDriverName: overlay
graphOptions:
overlay.mount_program:
Executable: /usr/bin/fuse-overlayfs
Package: fuse-overlayfs-1.7.1-1.module_el8.5.0+890+6b136101.x86_64
Version: |-
fusermount3 version: 3.2.1
fuse-overlayfs: version 1.7.1
FUSE library version 3.2.1
using FUSE kernel interface version 7.26
overlay.mountopt: nodev,metacopy=on
graphRoot: /var/lib/containers/storage
graphStatus:
Backing Filesystem: xfs
Native Overlay Diff: "false"
Supports d_type: "true"
Using metacopy: "false"
imageStore:
number: 3
runRoot: /run/containers/storage
volumePath: /var/lib/containers/storage/volumes
version:
APIVersion: 3.3.1
Built: 1636493036
BuiltTime: Wed Nov 10 05:23:56 2021
GitCommit: ""
GoVersion: go1.16.7
OsArch: linux/amd64
Version: 3.3.1
podman search 查找镜像
//精准查找dockerWarehouse official source
[[email protected] ~]# podman search apache --filter=is-official
INDEX NAME DESCRIPTION STARS OFFICIAL AUTOMATED
docker.io docker.io/library/httpd The Apache HTTP Server Project 3794 [OK]
//默认查找
[[email protected] ~]# podman search apache
INDEX NAME DESCRIPTION STARS OFFICIAL AUTOMATED
redhat.com registry.access.redhat.com/rhscl/httpd-24-rhel7 Apache HTTP 2.4 Server 0
redhat.com registry.access.redhat.com/rhscl/php-70-rhel7 PHP 7.0 platform for building and running ap... 0
redhat.com registry.access.redhat.com/openshift3/php-55-rhel7 PHP 5.5 platform for building and running ap... 0
redhat.com registry.access.redhat.com/rhscl/php-71-rhel7 PHP 7.1 available as container is a base pla... 0
redhat.com registry.access.redhat.com/ubi7/php-72 Apache 2.4 with PHP 7.2 0
redhat.com registry.access.redhat.com/ubi8/php-72 Platform for building and running PHP 7.2 ap... 0
redhat.com registry.access.redhat.com/ubi8/php-73 Platform for building and running PHP 7.3 ap... 0
redhat.com registry.access.redhat.com/ubi7/php-73 Platform for building and running PHP 7.3 ap... 0
redhat.com registry.access.redhat.com/ubi8/httpd-24 Platform for running Apache httpd 2.4 or bui... 0
redhat.com registry.access.redhat.com/rhscl/perl-526-rhel7 Perl 5.26 available as container is a base p... 0
redhat.com registry.access.redhat.com/rhscl/perl-524-rhel7 Platform for building and running Perl 5.24 ... 0
redhat.com registry.access.redhat.com/rhscl/perl-520-rhel7 Perl 5.20 platform for building and running ... 0
redhat.com registry.access.redhat.com/openshift3/perl-516-rhel7 Perl 5.16 platform for building and running ... 0
redhat.com registry.access.redhat.com/rhscl/php-72-rhel7 PHP 7.2 available as container is a base pla... 0
redhat.com registry.access.redhat.com/ubi8/perl-526 Platform for building and running Perl 5.26 ... 0
redhat.com registry.access.redhat.com/ubi8/perl-530 Platform for building and running Perl 5.26 ... 0
redhat.com registry.access.redhat.com/ubi8/php-74 Platform for building and running PHP 7.4 ap... 0
redhat.com registry.access.redhat.com/amqstreams-1-tech-preview/amqstreams10-kafkaconnect-openshift AMQ Streams image for running an Apache Kafk... 0
redhat.com registry.access.redhat.com/amqstreams-1/amqstreams10-kafka-openshift AMQ Streams image for running an Apache Kafk... 0
redhat.com registry.access.redhat.com/amqstreams-1/amqstreams10-kafkaconnect-openshift AMQ Streams image for running an Apache Kafk... 0
redhat.com registry.access.redhat.com/amqstreams-1/amqstreams10-kafkamirrormaker-openshift AMQ Streams image for running an Apache Kafk... 0
redhat.com registry.access.redhat.com/amq7/amq-streams-kafka-connect AMQ Streams image for running an Apache Kafk... 0
redhat.com registry.access.redhat.com/amq7/amq-streams-zookeeper AMQ Streams image for running an Apache Zook... 0
redhat.com registry.access.redhat.com/amqstreams-1-tech-preview/amqstreams10-kafka-openshift AMQ Streams image for running an Apache Kafk... 0
redhat.com registry.access.redhat.com/amqstreams-1-tech-preview/amqstreams10-zookeeper-openshift AMQ Streams image for running an Apache Zook... 0
docker.io docker.io/apache/airflow Apache Airflow 305
docker.io docker.io/webdevops/apache Apache container 15 [OK]
docker.io docker.io/lephare/apache Apache container 6 [OK]
podman pull 拉镜像
[[email protected] ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
[[email protected] ~]# podman pull docker.io/library/busybox
Trying to pull docker.io/library/busybox:latest...
Getting image source signatures
Copying blob 3cb635b06aa2 [--------------------------] 0.0b / 0.0b
Copying config ffe9d497c3 done
Writing manifest to image destination
Storing signatures
ffe9d497c32414b1c5cdad8178a85602ee72453082da2463f1dede592ac7d5af
[[email protected] ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
docker.io/library/busybox latest ffe9d497c324 6 days ago 1.46 MB
podman run 运行容器
[[email protected] ~]# podman run -dt -p 80:80 docker.io/library/httpd
179cf360121b45104e6ab3e7016f28e93bb61dfe33fa6f63c79ff46c592f9a7b
[[email protected] ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
179cf360121b docker.io/library/httpd:latest httpd-foreground 7 seconds ago Up 7 seconds ago 0.0.0.0:80->80/tcp unruffled_bhaskara
[[email protected] ~]# podman inspect 179cf360121b |grep -i address
"IPAddress": "10.88.0.5",
"GlobalIPv6Address": "",
"MacAddress": "ca:2a:64:71:a6:62",
"LinkLocalIPv6Address": "",
"IPAddress": "10.88.0.5",
"GlobalIPv6Address": "",
"MacAddress": "ca:2a:64:71:a6:62",
[[email protected] ~]# curl 10.88.0.5
<html><body><h1>It works!</h1></body></html>
[[email protected] ~]# curl 192.168.143.103
<html><body><h1>It works!</h1></body></html>
podman inspectl 查看容器详细信息
//-l 查看最新的容器信息,由于容器在无根模式下运行,因此不会为容器分配 IP 地址
[[email protected] ~]# podman inspect -l
...以下省略
"SandboxKey": "/run/netns/cni-dca4250d-d6c4-bb84-eda5-02bc93a3b08d",
"Networks": {
"podman": {
"EndpointID": "",
"Gateway": "10.88.0.1",
"IPAddress": "10.88.0.5",
"IPPrefixLen": 16,
"IPv6Gateway": "",
....以下省略
podman logs(查看容器日志)
[[email protected] ~]# podman logs -l
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 10.88.0.5. Set the 'ServerName' directive globally to suppress this message
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 10.88.0.5. Set the 'ServerName' directive globally to suppress this message
[Tue Dec 14 15:21:53.610480 2021] [mpm_event:notice] [pid 1:tid 139697995017536] AH00489: Apache/2.4.51 (Unix) configured -- resuming normal operations
[Tue Dec 14 15:21:53.621921 2021] [core:notice] [pid 1:tid 139697995017536] AH00094: Command line: 'httpd -D FOREGROUND'
10.88.0.1 - - [14/Dec/2021:15:24:59 +0000] "GET / HTTP/1.1" 200 45
192.168.143.103 - - [14/Dec/2021:15:25:06 +0000] "GET / HTTP/1.1" 200 45
podman top 查看容器 pid
[[email protected] ~]# podman top -l
USER PID PPID %CPU ELAPSED TTY TIME COMMAND
root 1 0 0.000 8m13.884400188s pts/0 0s httpd -DFOREGROUND
www-data 8 1 0.000 8m13.885412378s pts/0 0s httpd -DFOREGROUND
www-data 9 1 0.000 8m13.886299432s pts/0 0s httpd -DFOREGROUND
www-data 10 1 0.000 8m13.886836237s pts/0 0s httpd -DFOREGROUND
podman push 上传镜像
//登出用户
[[email protected] ~]# podman logout docker.io
Removed login credentials for docker.io
//登入用户
[[email protected] ~]# podman login docker.io
Username: hyhxy0206
Password:
Login Succeeded!
[[email protected] ~]# cat /run/user/0/containers/auth.json
{
"auths": {
"docker.io": { //镜像官网
"auth": "aHloeHkwMjA2OjEzODg2NjAwMjQ4aHku"
}
}
}
//修改镜像标签
[[email protected] ~]# podman tag docker.io/library/httpd:latest docker.io/hyhxy0206/httpd:latest
//上传镜像
[[email protected] ~]# podman push docker.io/hyhxy0206/httpd:latest
podman普通用户使用
podmanOrdinary users using the instance
//关闭防火墙和selinux
[[email protected] ~]# systemctl disable --now firewalld
[[email protected] ~]# vim /etc/selinux/config
SELINUX=disabled //修改此行
[[email protected] ~]# reboot
[[email protected] ~]# getenforce
Disabled
[[email protected] ~]# yum install -y podman
[[email protected] ~]# vim /etc/containers/storage.conf
mount_program = "/usr/bin/fuse-overlayfs" //取消注释
[[email protected] ~]# yum install -y crun
[[email protected] ~]# vim /usr/share/containers/containers.conf
runtime = "crun" //修改此行
#runtime = "runc" //修改此行
[[email protected] ~]# useradd abc
[[email protected] ~]# su - abc
[[email protected] ~]$ podman run -it busybox /bin/sh
Resolved "busybox" as an alias (/etc/containers/registries.conf.d/000-shortnames.conf)
Trying to pull docker.io/library/busybox:latest...
Getting image source signatures
Copying blob 3cb635b06aa2 done
Copying config ffe9d497c3 done
Writing manifest to image destination
Storing signatures
/ # exit
Podman 在无rootThe basic set up and use of the environment.
在允许没有 root 权限的用户运行 Podman 之前,管理员必须安装或构建 Podman 并完成以下配置.
cgroup V2 支持
cgroup V2 Linux 内核功能允许用户限制无根容器可以使用的资源量.如果您运行 Podman 的 Linux Distribution is enabled cgroup V2,You may need to change the default OCI 运行时.Some old versionrunc不能与 cgroup V2 一起使用,You might have to switch to alternative OCI 运行时crun.
//默认是有crun软件包,没有grep到需要
yum -y install crun
[[email protected] ~]# yum list all|grep crun
Repository salt-latest-repo is listed more than once in the configuration
crun.x86_64 1.0-1.module_el8.5.0+911+f19012f9 appstream
Also can use the following on the command line--runtimeOptions open for cgroup V2 的替代 OCI 运行时支持:
podman --runtime crun
或用于通过改变用于在“默认OCI运行时”的值的所有的命令containers.confAt the system level or in any document的用户级别从runtime = "runc"到runtime = "crun".
[[email protected] ~]# vim /usr/share/containers/containers.conf
.....Above the multi-line omit
runtime = "crun" # Uncomment find trip
......The following multi-line omit
管理员操作
安装 Podman
如需安装 Podman,请参阅安装说明.
构建Podman
Podman The structures, please have a look at安装说明.
安装 slirp4netns
//默认是有slirp4netns软件包,没有grep到需要
yum -y install slirp4netns
[[email protected] ~]# yum list all|grep slirp4netns
Repository salt-latest-repo is listed more than once in the configuration
slirp4netns.x86_64 1.1.8-1.module_el8.5.0+890+6b136101 @appstream
所述slirp4netnsPackage provides an unprivileged user mode network and network name space must be on the machine,In order to install forPodmanIn a rootless environment running.The package through their software package distribution,As can be at mostLinux发行版yum,dnf,apt,zypper,等等.如果没有可用的package,You can build and installslirp4netns从GitHub上.
确保fuse-overlayfs已安装
在rootless环境下使用Podman时,建议使用fuse-overlayfs而不是VFS文件系统.For all you needfuse-overlayfs可执行文件提供$PATH.
//默认是有fuse-overlayfs软件包,没有grep到需要
yum -y install fuse-overlayfs
[[email protected] ~]# yum list all|grep fuse-overlayfs
Repository salt-latest-repo is listed more than once in the configuration
fuse-overlayfs.x86_64 1.7.1-1.module_el8.5.0+890+6b136101 @appstream
配置 storage.conf文件
[[email protected] ~]# vim /etc/containers/storage.conf
....Above the multi-line omit
# Path to an helper program to use for mounting the file system instead of mounting it
# directly.
mount_program = "/usr/bin/fuse-overlayfs" //取消注释
....The following multi-line omit
/etc/subuid和/etc/subgid配置
Rootless Podman Users of required to run it in the file/etc/subuid和/etc/subgid. 的shadow-utils或newuidPackage provides about different distribution of these files and they must be installed on the system.In these files to add or update the item need to root 权限.以下是From no root Podman是如何工作的?Dan Walsh 在opensource.com上的文章
对于将被允许创建容器,更新每一个用户/etc/subuid,并/etc/subgid与看起来像以下字段用户.请注意,每个用户的值必须是唯一的.如果存在重叠,用户就有可能使用另一个用户的命名空间,并且他们可能会破坏它.
[[email protected] ~]# useradd tom
[[email protected] ~]# useradd jerry
[[email protected] ~]# cat /etc/subuid
tom:100000:65536
jerry:165536:65536
[[email protected] ~]# cat /etc/subgid
tom:100000:65536
jerry:165536:65536
这个文件的格式是 USERNAME:UID:RANGE
- 中
/etc/passwd或输出中列出的用户名getpwent. - 为用户分配的初始 UID.
- 为用户分配的 UID 范围的大小.
This means that for the userjohndoe分配了 UID 100000-165535 以及/etc/passwdFile the standard UID .注意:Network installation currently does not support this function;These files must be available locally on the main.无法使用 LDAP 或 Active Directory 进行配置.
如果您更新/etc/subuid或/etc/subgid,You need to stop the user owns all running container and terminate the user on the system run to halt the process.这可以通过使用podman system migrate命令自动完成,This command will stop all containers for the user and an end to halt the process.
该usermod程序可用于为用户分配 UID 和 GID,而不是直接更新文件.
usermod --add-subuids 200000-201000 --add-subgids 200000-201000 johndoe
grep johndoe /etc/subuid /etc/subgid
/etc/subuid:johndoe:200000:1001
/etc/subgid:johndoe:200000:1001
//Update file method,直接修改内容
[[email protected] ~]# vim /etc/subuid
To enable the privilege ping
In a non-privileged container operation of users may not be able to use thepingIn a container utility.
如果需要,The administrator must authenticate users UID 是否在/proc/sys/net/ipv4/ping_group_range文件范围内.
To change its value,Administrators can use similar call:sysctl -w "net.ipv4.ping_group_range=0 2000000".
In order to make the change remains the same,Administrators need to add a file.conf扩展名为/etc/sysctl.dcontains的文件net.ipv4.ping_group_range=0 $MAX_GID,其中$MAX_GIDIs a running container users maximum allocation GID.
//永久配置
[[email protected] ~]# vim /etc/sysctl.conf
....Above the multi-line ignore
sysctl -w "net.ipv4.ping_group_range=0 2000000" //Add the trip at the end of the day
用户操作
在无root环境中运行 Podman Most of the work required is borne by the machine administrator.
Once the administrator to complete the Settings on the machine,然后在/etc/subuid和/etc/subgidIn the user's configuration,The user can start to use they want any Podman 命令.
用户配置文件
根驻留在Podman配置文件/usr/share/containers与覆盖/etc/containers.在无root环境中,它们驻留在${XDG_CONFIG_HOME}/containers(通常~/.config/containers)中并由每个单独的用户拥有.
三个主要的配置文件是container.conf、storage.conf和registries.conf.用户可以根据需要修改这些文件.
containers.conf 容器配置
Podman reads
/usr/share/containers/containers.conf/etc/containers/containers.conf$HOME/.config/containers/containers.conf
如果它们以该顺序存在.每个文件都可以覆盖特定字段的前一个文件.
storage.conf 存储配置
在storage.conf顺序是
/etc/containers/storage.conf$HOME/.config/containers/storage.conf
在无root Podman 中,某些字段/etc/containers/storage.conf被忽略.这些字段是:
graphroot=""
container storage graph dir (default: "/var/lib/containers/storage")
Default directory to store all writable content created by container storage programs.
runroot=""
container storage run dir (default: "/run/containers/storage")
Default directory to store all temporary writable content created by container storage programs.
在无root Podman 中,These fields by default
graphroot="$HOME/.local/share/containers/storage"
runroot="$XDG_RUNTIME_DIR/containers"
[KaTeX parse error: Expected 'EOF', got '#' at position 94: …pec-latest.html#̲variables) defa…UID`.
registries.conf 注册表配置
[[email protected] ~]# vim /etc/containers/registries.conf
...Above the multi-line omit
# # An array of host[:port] registries to try when pulling an unqualified image, in order.
unqualified-search-registries = ["docker.io"] //修改此行
[[registry]]
prefix="docker.io"
location = "docker.mirrors.ustc.edu.cn" //Modify the three lines
...The following multi-line omit
registries 注册表
Read in the registry configuration in this order
/etc/containers/registries.conf/etc/containers/registries.d/*HOME/.config/containers/registries.conf
Home directory of the file should be used for according to individual need to configure the noroot Podman.By default, does not create these files.The user can copy/usr/share/containers或/etc/containers修改文件.
Authorization files 授权文件
podman login和podman logoutCommand USES the default authorization file located in the${XDG_RUNTIME_DIR}/containers/auth.json.
[[email protected] ~]# cat /run/user/0/containers/auth.json
{
"auths": {
"docker.io": {
"auth": "aHloeHkwMjA2OjEzODg2NjAwMxxxxx" //授权key
}
}
使用卷
无根 Podman 不是,Never is a;它不是setuid二进制文件,The runtime will not get any privilege.相反,Podman Use user name space to move it on a host computer(通过newuidmap和newgidmap可执行文件)And your own user in Podman Create the container shall have the right to access to the user block UID 和 GID .
If your container with root 用户运行,那么rootIn the container is actually your users on a host computer.UID / GID 1是第一个UID / GIDThe user specified in the map/etc/subuid和/etc/subgid等,If you install directory from the host into the container as a rootless user,And create in the container in the directory file as the root,You'll see that it is actually owned by your user on the host.
所以,例如,
//普通用户和root用户,Create a container hasroot权限
[[email protected] ~]$ mkdir data
[[email protected] ~]$ podman run -it -v /home/tom/data/:/data busybox /bin/sh
/ # ls
bin dev home root sys usr
data etc proc run tmp var
/ # cd data/
/data # touch abc
/data # ls -l
total 0
-rw-r--r-- 1 root root 0 Dec 15 09:02 abc
[[email protected] ~]# ll /home/tom/data/
总用量 0
[[email protected] ~]# ll /home/tom/data/
总用量 0
-rw-r--r-- 1 tom tom 0 12月 15 17:02 abc
//Container using normal permissions--userns=keep-id -v
[[email protected] ~]$ podman run -it --userns=keep-id -v /home/tom/data/:/data busybox /bin/sh
~ $ id
uid=1000(tom) gid=1000(tom)
We do realize this and how many people are going to use no root Podman Don't really match——They hope the container inside and outside UID 匹配.因此,我们提供了–userns=keep-id标志,To ensure that your users in container mapping into its own UID 和 GID.
Distinguish with no root run Podman And with no root operation of container is also very helpful.If you try to run the containerUSER不是 root,In installing a volume must be used–userns=keep-id. This is because the container users will not be able to becomerootAnd the volume to access installed.
Other considerations about the volume:
You should always offer to install the volume of the full path of the
The mount point must exist in the container
Podman 基本网络
Seemed to once they have mastered the basic knowledge of container,Network is the first they start trying to.在网络方面,Before finally reached the depths of the pool only need a few experiment.The following guide shows the Podman rootfull 和 rootless The container of the most common network Settings.Each set has a sample support.
rootfull 和 rootless 容器网络之间的差异
Podman 容器联网的指导因素之一将是容器是否由 root 用户运行.这是因为非特权用户无法在主机上创建网络接口.因此,对于 rootfull 容器,默认网络模式是使用容器网络接口 (CNI) 插件,特别是桥接插件.对于rootless,默认的网络模式是slirp4netns.由于权限有限,slirp4netns缺少CNI组网的一些功能;例如,slirp4netns 无法为容器提供可路由的 IP 地址.
Custom configure the network
- podman network create 创建网络
- 修改 /etc/cni/net.d/xxxx.conflist 配置文件
- 修改设置/usr/share/containers/containers.conf It as the default network
//创建网络
[[email protected] ~]# podman network create web
/etc/cni/net.d/web.conflist
[[email protected] ~]# podman network ls
NETWORK ID NAME VERSION PLUGINS
2f259bab93aa podman 0.4.0 bridge,portmap,firewall,tuning
4b5e57f6eb2f web 0.4.0 bridge,portmap,firewall,tuning
//修改配置文件
[[email protected] ~]# vim /etc/cni/net.d/web.conflist
.....Above the multi-line ignore
"ranges": [
[
{
"subnet": "192.168.0.0/24", //修改ip和网段
"gateway": "192.168.0.1" //修改网关
}
]
]
}
},
......The following line to ignore
//修改/usr/share/containers/containers.conf It as the default network
[[email protected] ~]# vim /usr/share/containers/containers.conf
.....Above the multi-line ignore
#default_network = "podman"
default_network = "newk" # 添加此行
.....The following line to ignore
//查看容器内ip是否修改
[[email protected] ~]# podman run -dit --name web busybox
72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da
[[email protected] ~]# podman exec -it web busybox /bin/sh
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: [email protected]: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue
link/ether da:8a:c6:88:15:99 brd ff:ff:ff:ff:ff:ff
inet 192.143.0.3/24 brd 192.143.0.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::d88a:c6ff:fe88:1599/64 scope link
valid_lft forever preferred_lft forever
/ # ping baidu.com
PING baidu.com (220.181.38.148): 56 data bytes
64 bytes from 220.181.38.148: seq=0 ttl=127 time=71.297 ms
64 bytes from 220.181.38.148: seq=1 ttl=127 time=113.138 ms
^C
--- baidu.com ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 71.297/92.217/113.138 ms
防火墙
防火墙的作用不会影响网络的设置和配置,但会影响这些网络上的流量.The most obvious is the inbound network traffic to the container of the host,这些流量通常通过端口映射传递到容器上.根据防火墙的实现,我们观察到防火墙端口由于运行带有端口映射的容器(例如)而自动打开.如果容器流量似乎无法正常工作,Please check the firewall and allow container is used on port traffic.一个常见的问题是重新加载防火墙会删除 cni iptables 规则,从而导致 rootful 容器的网络连接丢失.Podman v3 提供了 podman network reload 命令来恢复它而无需重新启动容器.
//查看防火墙 This is justweb容器
[[email protected] ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
3 194 CNI-f9a8f05c08d563e317d13b55 all -- * * 192.143.0.3 0.0.0.0/0 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain CNI-f9a8f05c08d563e317d13b55 (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 192.143.0.0/24 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
3 194 MASQUERADE all -- * * 0.0.0.0/0 !224.0.0.0/4 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
[[email protected] ~]#
//Stop the container at this time,查看防火墙规则
[[email protected] ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
//清空防火墙,重新加载防火墙,iptables -t nat -F
[[email protected] ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
[[email protected] ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 CNI-f9a8f05c08d563e317d13b55 all -- * * 192.143.0.4 0.0.0.0/0 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain CNI-f9a8f05c08d563e317d13b55 (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 192.143.0.0/24 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
0 0 MASQUERADE all -- * * 0.0.0.0/0 !224.0.0.0/4 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
[[email protected] ~]#
[[email protected] ~]# iptables -t nat -F
[[email protected] ~]# iptables --flush
[[email protected] ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain CNI-f9a8f05c08d563e317d13b55 (0 references)
pkts bytes target prot opt in out source destination
//Restart the container network can restore the rules
[[email protected] ~]# podman network reload web
72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da
[[email protected] ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 CNI-f9a8f05c08d563e317d13b55 all -- * * 192.143.0.4 0.0.0.0/0 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain CNI-f9a8f05c08d563e317d13b55 (1 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 192.143.0.0/24 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
0 0 MASQUERADE all -- * * 0.0.0.0/0 !224.0.0.0/4 /* name: "web" id: "72f20d93156c2e343e0a1631a351e9ba9b629cbfec74e017dd8a0274e34d76da" */
podman容器的开机自启
root用户
[[email protected] ~]# podman run -d -p 80:80 --name nginx nginx
24eea484af5ae4bf1b19905cfb2060d5a41209db17a74af8d83af8b948d69a4a
[[email protected] ~]# podman generate systemd --files --name nginx
/root/container-nginx.service
[[email protected] ~]# ls
anaconda-ks.cfg files minion-install.tar.gz
container-nginx.service minion-install.sh soft
[[email protected] ~]# mv container-nginx.service /usr/lib/systemd/system/
[[email protected] ~]# podman stop nginx
nginx
[[email protected] ~]# systemctl enable --now container-nginx.service
Created symlink /etc/systemd/system/multi-user.target.wants/container-nginx.service → /usr/lib/systemd/system/container-nginx.service.
Created symlink /etc/systemd/system/default.target.wants/container-nginx.service → /usr/lib/systemd/system/container-nginx.service.
[[email protected] ~]# podman ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
24eea484af5a docker.io/library/nginx:latest nginx -g daemon o... 2 minutes ago Up 6 seconds ago 0.0.0.0:80->80/tcp nginx
[[email protected] ~]# podman stop nginx
nginx
[[email protected] ~]# reboot
[[email protected] ~]# podman ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
24eea484af5a docker.io/library/nginx:latest nginx -g daemon o... 4 minutes ago Up 36 seconds ago 0.0.0.0:80->80/tcp nginx
[[email protected] ~]# curl 192.168.143.103
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
普通用户
[C:\~]$ ssh [email protected]
//启动容器
[[email protected] ~]$ podman run -dit --name nginx nginx
7d9a9a90b3227efad71536f68c3b3bfe7e96bd9cb0e088311f7a11582aaa725b
//创建目录
[[email protected] ~]$ mkdir -p ~/.config/systemd/user
[[email protected] ~]$ cd ~/.config/systemd/user/
//生成service文件
[[email protected] user]$ podman generate systemd --name nginx --files --new/home/tom/.config/systemd/user/container-nginx.service
[[email protected] user]$ ls
container-nginx.service
//Give the container set boot from rev
[[email protected] user]$ podman rm -f nginx
7d9a9a90b3227efad71536f68c3b3bfe7e96bd9cb0e088311f7a11582aaa725b
[[email protected] user]$ systemctl --user daemon-reload
[[email protected] user]$ systemctl --user enable --now container-nginx.service
Created symlink /home/tom/.config/systemd/user/multi-user.target.wants/container-nginx.service → /home/tom/.config/systemd/user/container-nginx.service.
Created symlink /home/tom/.config/systemd/user/default.target.wants/container-nginx.service → /home/tom/.config/systemd/user/container-nginx.service.
[[email protected] ~]$ podman ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
dbb54f85b26d docker.io/library/nginx:latest nginx -g daemon o... 7 seconds ago Up 7 seconds ago nginx
//重启主机
[[email protected] ~]# reboot
[C:\~]$ ssh [email protected]
[[email protected] ~]$ podman ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
ed36c3723b9c docker.io/library/nginx:latest nginx -g daemon o... 6 seconds ago Up 6 seconds ago nginx
边栏推荐
猜你喜欢
随机推荐
ZEMAX | 在设计抬头显示器(HUD)时需要使用哪些工具?
802.1AS 时钟同步原理理解
Oracle常用命令-基本命令
内网渗透信息收集
SSL证书过期后怎么办?
【个人总结】MES系统开发/管理要点
数组与字符串11-反转字符串
ZEMAX | 如何使用ZOS-API创建自定义操作数
增强光学系统设计 | Zemax 全新 22.2 版本产品现已发布!
Oracle 11g静默安装
Windos 内网渗透之Token的使用
全球一流医疗技术公司如何最大程度提高设计工作效率 | SOLIDWORKS 产品探索
2-php学习笔记之控制语句,函数
二、Exception和Error有什么区别?
大学毕业后,零基础想转行成为一名3D建模师,现在该做什么?
ZEMAX | 绘图分辨率结果对光线追迹的影响
内网渗透之PPT票据传递攻击(Pass the Ticket)
在Maya和ZBrush中制作战士模型
嘿!selenium自动下载driver版本,得知道一下
【3D建模制作技巧分享】ZBrush快捷键如何设置