当前位置:网站首页>How to protect user privacy without password authentication?
How to protect user privacy without password authentication?
2022-07-05 13:00:00 【51CTO】
In the Internet world , Verifying user identity is a common and important scenario , The most widely used method is account password verification . As developers' requirements for authentication security continue to improve , In addition, users pay more attention to privacy and convenience in the process , Authentication methods are gradually diversified , With dynamic token 、 SMS verification code 、 Biometric authentication and other methods . This article mainly from the perspective of security , Discuss the security vulnerabilities of several common authentication methods , Provide more advantageous solutions for developers .
The security risks of common authentication methods are as follows :
 How to protect user privacy without password authentication ?_ developer](/img/3d/9f2e67992be026bac91e26b4371e7a.jpg)
Since both static and dynamic password authentication methods have vulnerabilities , Then whether authentication can be independent of passwords ?
Actually , Long ago , Someone began to imagine “ Password-free login ”. Of course ,“ Password-free login ” It does not mean that there is no password , Instead, use a new authentication method , To replace the existing password authentication system .HMS Core Online Fast Authentication Service (HMS Core FIDO) Based on this starting point , It provides a more advantageous solution for developers : User authentication without password , Provide local biometric authentication and online fast authentication capabilities , It can be used for user login 、 Purchase payment and other scenarios , meanwhile , Through system integrity detection and key verification mechanism , To ensure that the verification results are safe and reliable . The implementation process is as follows .
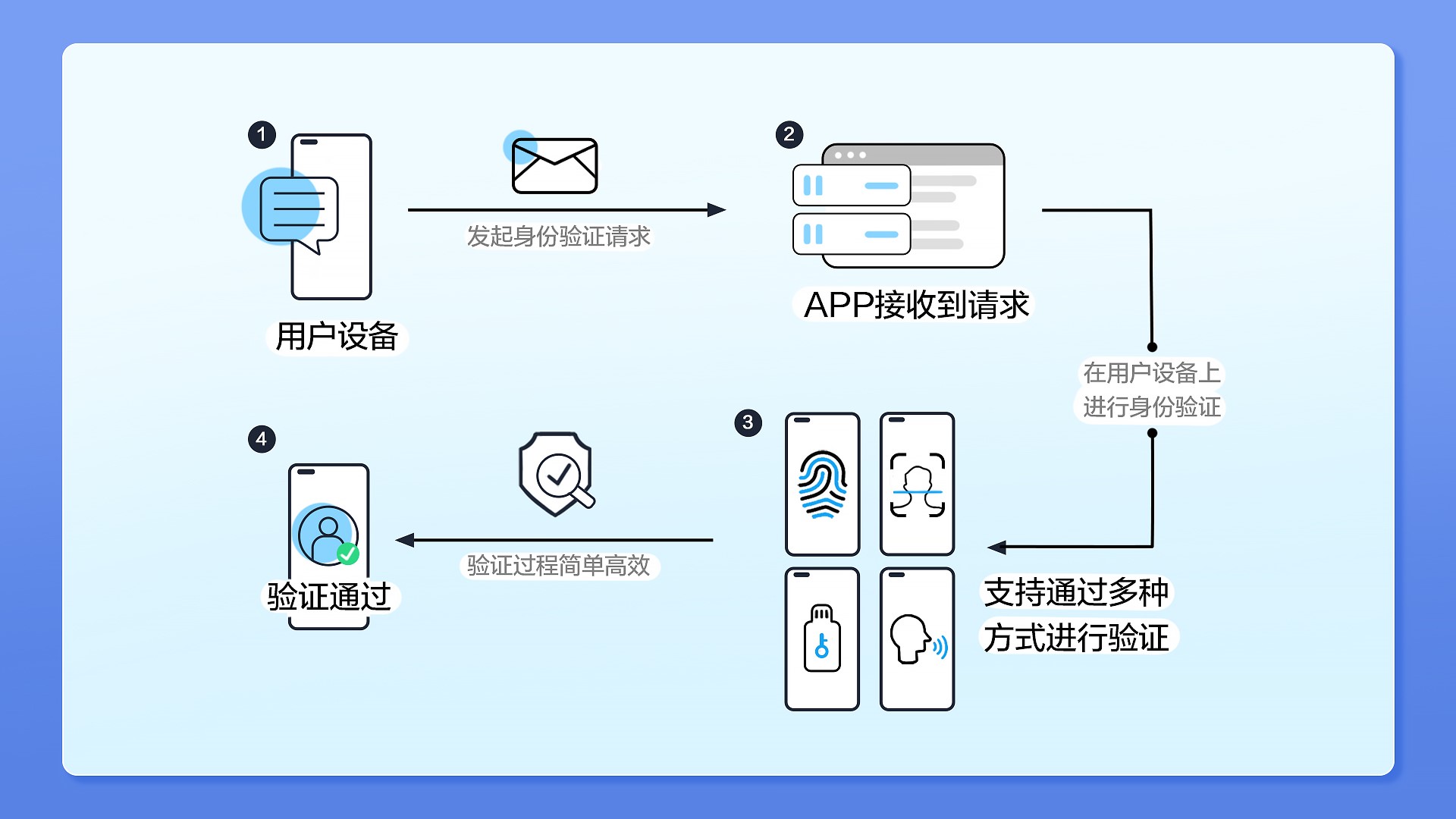 How to protect user privacy without password authentication ?_ Authentication _02](/img/27/14cf0c0c38c7627be08cd656bf3222.jpg)
In terms of security , First , HMS Core FIDO It avoids the user entering the account password manually , Therefore, there is no need to worry about the risk of account password disclosure .
secondly , Use HMS Core FIDO It not only improves the user experience , At the same time, it also reduces the deployment cost of Internet service providers .
Last , The user biometric information used in the verification process will never leave the user's device , It can only be used after unlocking locally , Therefore, there is no need to worry about leaking user data from the server .
In addition to providing secure authentication ,HMS Core FIDO It can also help developers optimize the user experience .
HMS Core FIDO The protocol is always designed around protecting users' privacy , These protocols do not provide information that can be used to track users on Internet platforms , If biometric technology is adopted , User biometric information will never leave the user device . This is compared with the traditional biometric authentication , Great improvements have been made in security and privacy protection , Because traditional biometric authentication will collect user data to the server , Once the server data leaks , There will be serious consequences . From the user's point of view , The privacy experience has been greatly improved .
During authentication , The user operation is simple , The process is smooth and uninterrupted , Don't spend too much time waiting , For example, accept the verification code 、 Enter the password, etc .
HMS Core FIDO Application scenarios of
at present ,FIDO Technology has been developed by global equipment manufacturers 、 Widespread recognition of Internet service providers , Including some large banks and other financial institutions 、 Government network platform, etc , Mature application in high security scenarios involving capital changes , Such as : Shopping websites or App Purchase payment 、 Digital currency transfer 、 Mobile Banking ( Online Banking Service ) Large transactions in , wait . Take the use process for example ,App Check whether the device supports when the user logs in HMS Core FIDO, If the support ,App It can guide users to open fingerprints or 3D Face login , Users only need to verify their fingerprints or 3D Face can be . HMS Core FIDO Is based on FIDO Standardize the open capabilities for developers at home and abroad , It can help Internet service providers to make the authentication process more secure 、 It's simpler , At the same time, it can also gain a better user experience .FIDO Its full name is Fast Identity Online standard , By FIDO The alliance has launched and continues to maintain a set of authentication framework protocols , It uses standard public key cryptography , Provide a more powerful authentication method .
Click to enter HMS Core FIDO Official website , Experience high-quality authentication capabilities .
Learn more >>
visit Official website of Huawei developer Alliance
obtain Development guidance document
Huawei mobile service open source warehouse address : GitHub
Pay attention to our , The first time to understand HMS Core Latest technical information ~
边栏推荐
- 滴滴开源DELTA:AI开发者可轻松训练自然语言模型
- [cloud native] event publishing and subscription in Nacos -- observer mode
- 【云原生】Nacos中的事件发布与订阅--观察者模式
- 百日完成国产数据库opengausss的开源任务--openGuass极简版3.0.0安装教程
- Simply take stock reading notes (1/8)
- Why is your next computer a computer? Explore different remote operations
- Difference between JUnit theories and parameterized tests
- 研究:数据安全工具在 60% 的情况下无法抵御勒索软件
- 逆波兰表达式
- RHCAS6
猜你喜欢
About the single step debugging of whether SAP ui5 floating footer is displayed or not and the benefits of using SAP ui5
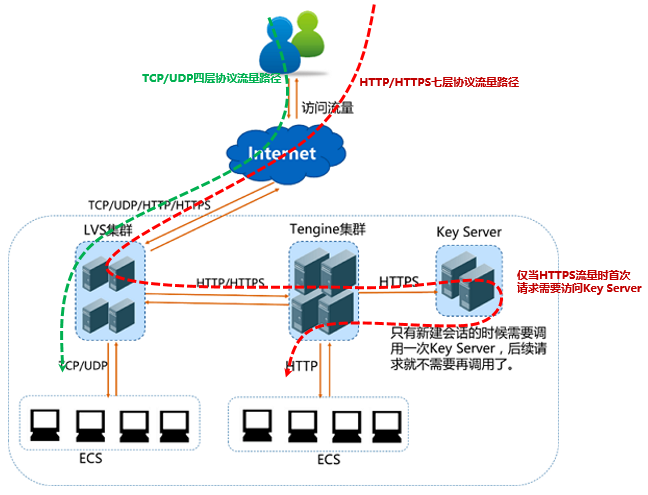
阿里云SLB负载均衡产品基本概念与购买流程
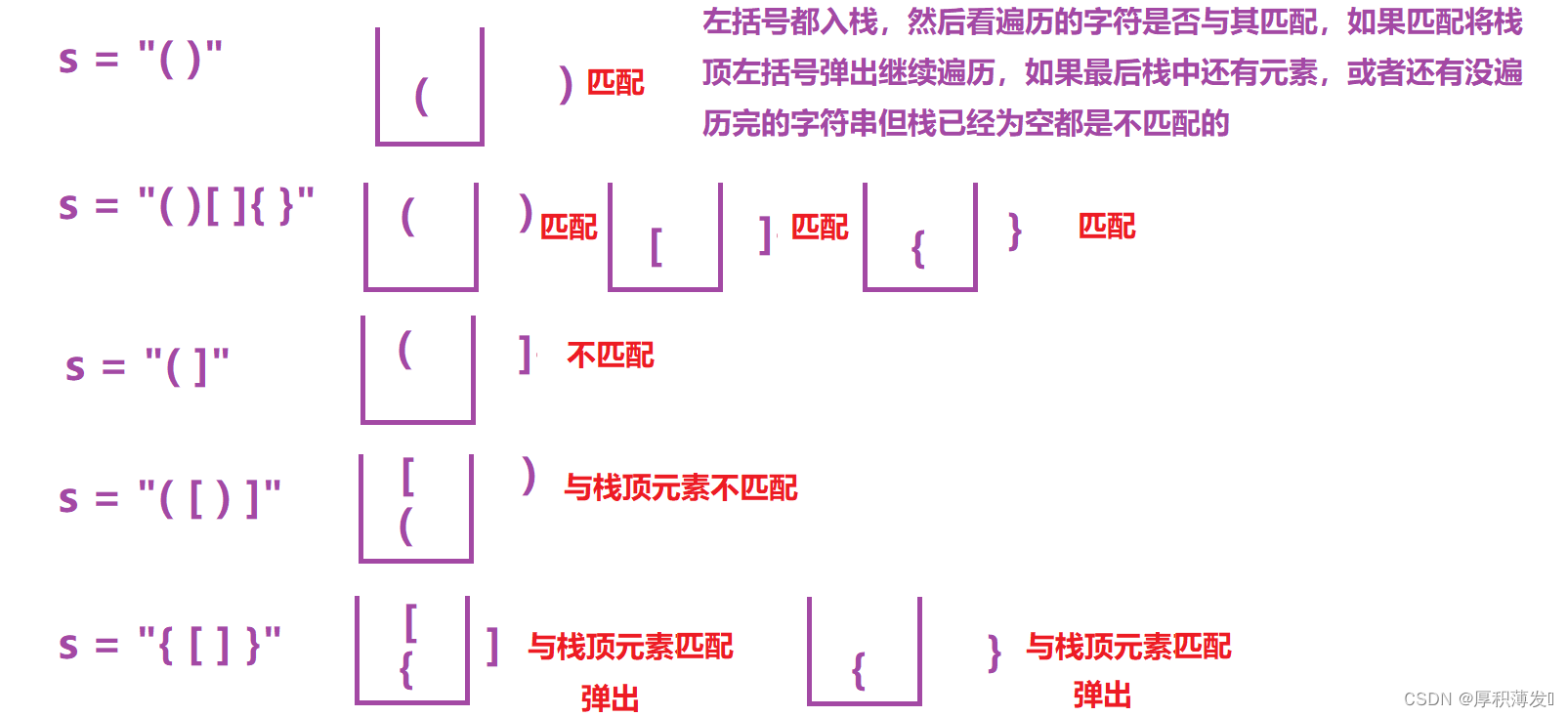
LeetCode20.有效的括号
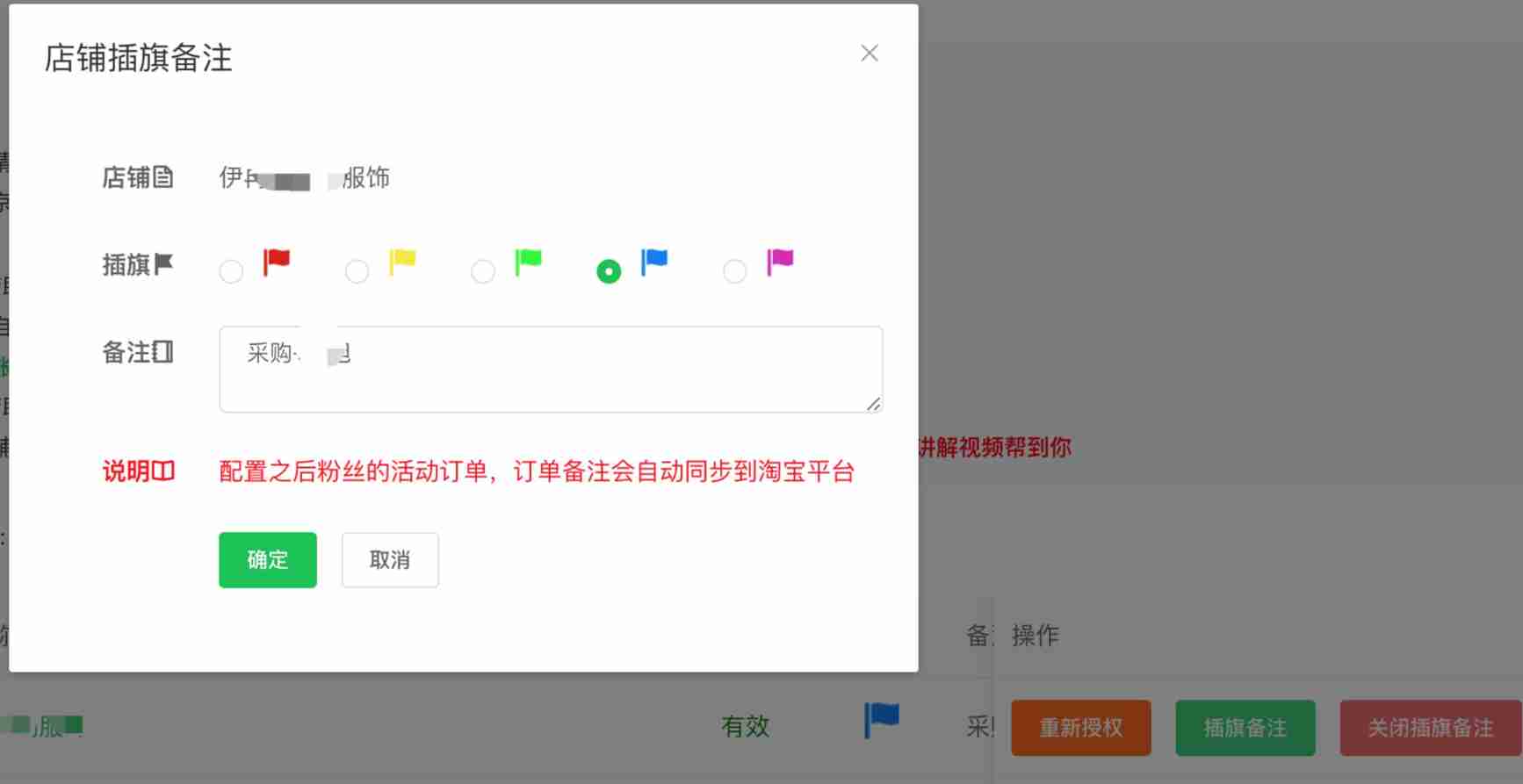
Taobao, pinduoduo, jd.com, Doudian order & Flag insertion remarks API solution
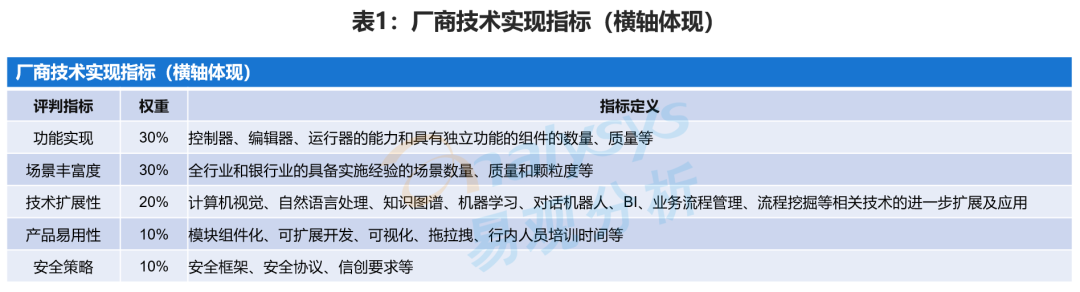
Le rapport de recherche sur l'analyse matricielle de la Force des fournisseurs de RPA dans le secteur bancaire chinois en 2022 a été officiellement lancé.
开发者,云原生数据库是未来吗?
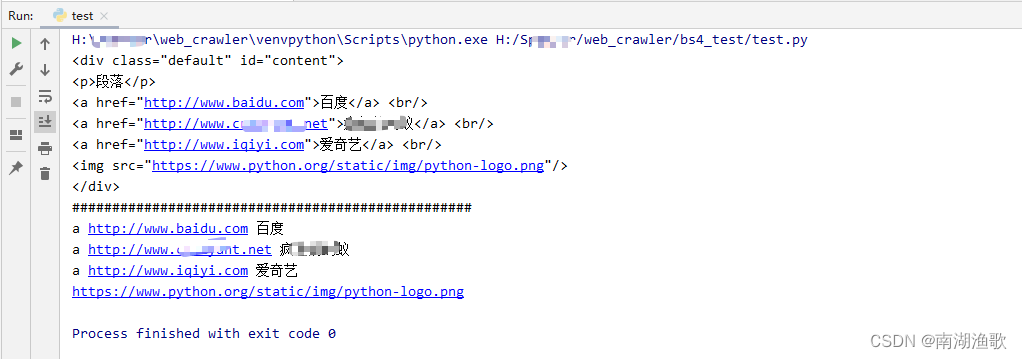
简单上手的页面请求和解析案例
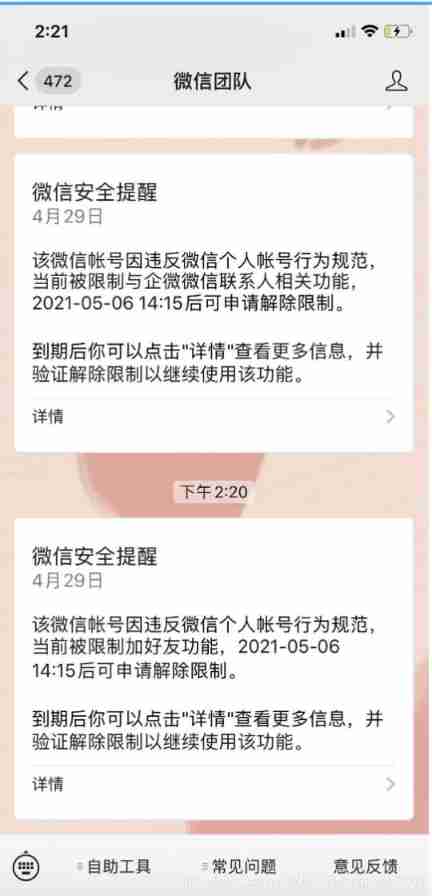
What if wechat is mistakenly sealed? Explain the underlying logic of wechat seal in detail
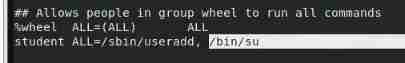
RHCSA5

RHCSA7
随机推荐
Rasa Chat Robot Tutorial (translation) (1)
Oppo Xiaobu launched Obert, a large pre training model, and promoted to the top of kgclue
Simply take stock reading notes (4/8)
RHCSA3
函数的默认参数&函数参数的多种方法
阿里云SLB负载均衡产品基本概念与购买流程
Four common problems of e-commerce sellers' refund and cash return, with solutions
Simply take stock reading notes (2/8)
Insmod prompt invalid module format
10 minute fitness method reading notes (1/5)
Compilation principle reading notes (1/12)
Hiengine: comparable to the local cloud native memory database engine
JXL notes
2021.12.16-2021.12.20 empty four hand transaction records
I met Tencent in the morning and took out 38K, which showed me the basic smallpox
The solution of outputting 64 bits from printf format%lld of cross platform (32bit and 64bit)
无密码身份验证如何保障用户隐私安全?
155. 最小栈
Install rhel8.2 virtual machine
Difference between JUnit theories and parameterized tests