当前位置:网站首页>SQL injection Less42 (POST type stack injection)
SQL injection Less42 (POST type stack injection)
2022-07-31 22:52:00 【HUAWEI CLOUD】
Pre-knowledge: SQL Injection Less38 (Stacked Injection)
The page of this question is similar to secondary injection, but we can't register users, so we can't use secondary injection.
White box audit, view code
$username = mysqli_real_escape_string($con1, $_POST["login_user"]);$password = $_POST["login_password"];Only the username is escaped, but not the password, so the password is a breakthrough
Test the password with a passcode' or 1=1#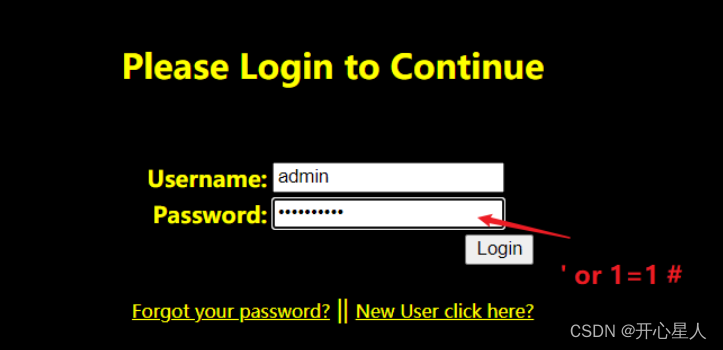
But why do we enter admin but log in as Dumb.
Because the SQL here is
SELECT * FROM users WHERE username='admin' and password='' or 1=1 #' And the priority of and is higher than or.So this statement is equivalent to
select * from users where 1Then the result is the entire users table.And Dumb is in the first row, so it is Dumb that is logged in.
Use password for stack injection
Enter the username at will
Password';drop table users;
https://blog.csdn.net/weixin_43901998/article/details/107566100
边栏推荐
- server certificate verification failed. CAfile: /etc/ssl/certs/ca-certificates.crt CRLfile: none failed
- 【Acwing】The 62nd Weekly Game Solution
- SQL注入 Less38(堆叠注入)
- Interview assault 69: TCP reliable?Why is that?
- [QNX Hypervisor 2.2 User Manual]9.14 set
- 【ACM】2022.7.31训练赛
- The latest masterpiece!Alibaba just released the interview reference guide (Taishan version), I just brushed it for 29 days
- The difference between adding or not adding the ref keyword when a variable of reference type is used as a parameter in a method call in C#
- iNeuOS industrial Internet operating system, equipment operation and maintenance business and "low-code" form development tools
- UserAgent resolution
猜你喜欢

Efficient Concurrency: A Detailed Explanation of Synchornized's Lock Optimization

Payment module implementation

ICML2022 | 深入研究置换敏感的图神经网络
I don't know what to do with sync issues
![[Code Hoof Set Novice Village 600 Questions] Leading to the combination of formulas and programs](/img/91/63d4f7869e0a55d19701c5ca5c9ed8.png)
[Code Hoof Set Novice Village 600 Questions] Leading to the combination of formulas and programs
【ACM】2022.7.31训练赛
Judging decimal points and rounding of decimal operations in Golang
(26)Blender源码分析之顶层菜单的关于菜单

flowable workflow all business concepts
SQL27 View user details of different age groups
随机推荐
基于simulink的Passive anti-islanding-UVP/OVP and UFP/OFP被动反孤岛模型仿真
Network security - crack WiFi through handshake packets (detailed tutorial)
Collation of knowledge points in Ningbo University NBU IT project management final exam
Bika LIMS open source LIMS set - use of SENAITE (detection process)
C#中引用类型的变量做为参数在方法调用时加不加 ref 关键字的不同之处
(26)Blender源码分析之顶层菜单的关于菜单
Structure of the actual combat battalion module eight operations
UOS统信系统 - WindTerm使用
Golang must know the Go Mod command
server certificate verification failed. CAfile: /etc/ssl/certs/ca-certificates.crt CRLfile: none failed
无状态与有状态的区别
程序进程和线程(线程的并发与并行)以及线程的基本创建和使用
【FPGA教程案例43】图像案例3——通过verilog实现图像sobel边缘提取,通过MATLAB进行辅助验证
Program processes and threads (concurrency and parallelism of threads) and basic creation and use of threads
"SDOI2016" Journey Problem Solution
C程序设计-方法与实践(清华大学出版社)习题解析
What is customer profile management?
Payment module implementation
登录业务实现(单点登录+微信扫码+短信服务)
Qualcomm cDSP simple programming example (to query Qualcomm cDSP usage, signature), RK3588 npu usage query