当前位置:网站首页>The most robust financial products in 2022
The most robust financial products in 2022
2022-07-04 12:17:00 【Koufu Q & A】
Take the answer 1:
Take the answer 2:
边栏推荐
- Four sorts: bubble, select, insert, count
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
- Some summaries of the 21st postgraduate entrance examination 823 of network security major of Shanghai Jiaotong University and ideas on how to prepare for the 22nd postgraduate entrance examination pr
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8
- Local MySQL forget password modification method (Windows) [easy to understand]
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13
- [the way of programmer training] - 2 Perfect number calculation
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23
- Haproxy cluster
- [Chongqing Guangdong education] National Open University spring 2019 2727 tax basis reference questions
猜你喜欢
TCP fast retransmission sack mechanism
Summary of Shanghai Jiaotong University postgraduate entrance examination module firewall technology
Experiment 7. IPv6
Method of setting default items in C # ComboBox control code
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 17](/img/85/2635afeb2edeb0f308045edd1f3431.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 17
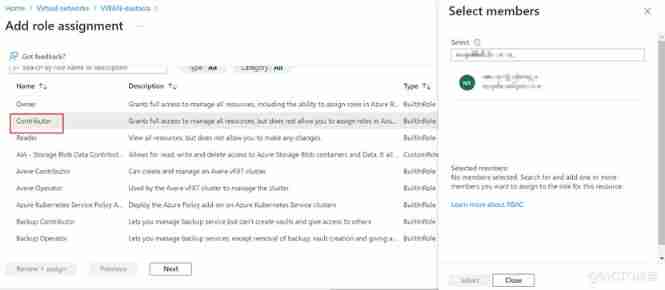
Realize cross tenant Vnet connection through azure virtual Wan
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 6](/img/38/51797fcdb57159b48d0e0a72eeb580.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 6
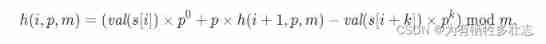
Review of week 278 of leetcode II
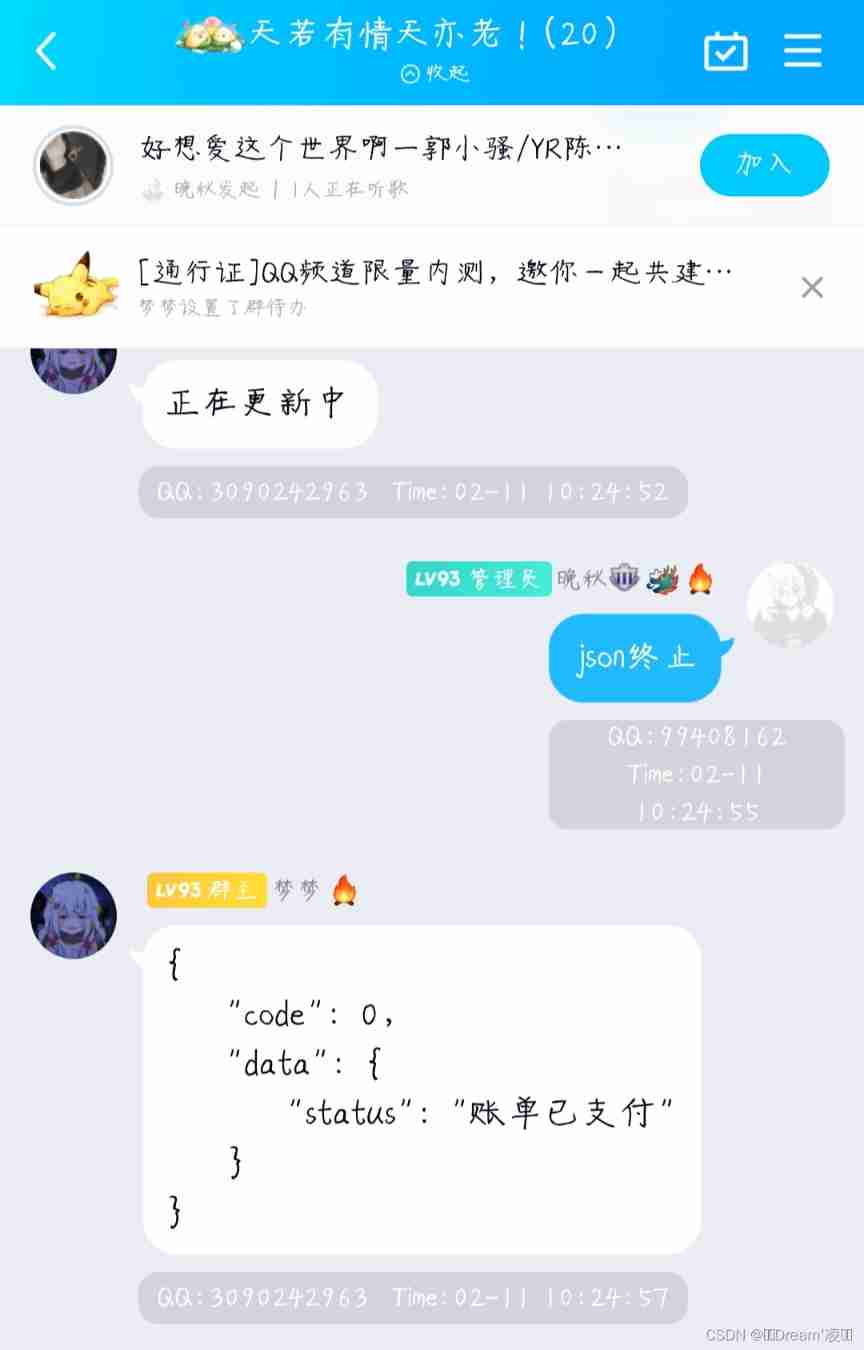
QQ group collection
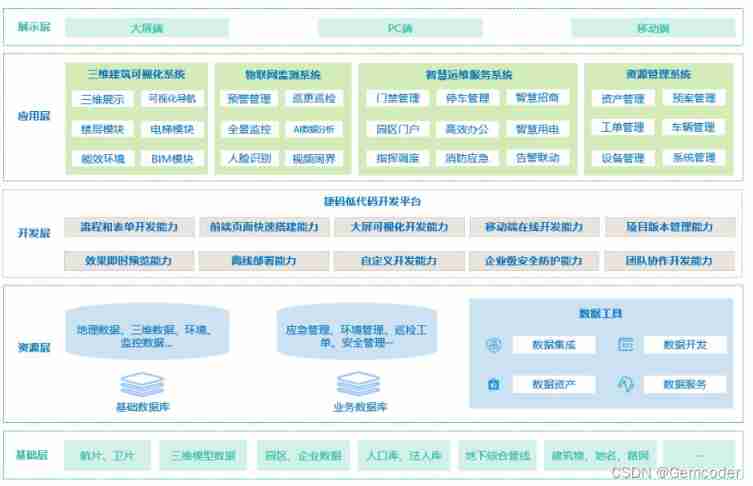
Enter the smart Park, and change begins here
随机推荐
JD home programmers delete databases and run away. Talk about binlog, the killer of MySQL data backup
[solve the error of this pointing in the applet] SetData of undefined
What if the chat record is gone? How to restore wechat chat records on Apple Mobile
Definition and method of string
Classification and application of AI chips
About the use of URL, href, SRC attributes
[Chongqing Guangdong education] National Open University spring 2019 2727 tax basis reference questions
Common tips
. Does net 4 have a built-in JSON serializer / deserializer- Does . NET 4 have a built-in JSON serializer/deserializer?
IPv6 experiment
QQ group administrators
VPS installation virtualmin panel
2021-08-09
CSDN documentation specification
Video analysis
Googgle guava ImmutableCollections
Review of week 278 of leetcode II
'using an alias column in the where clause in PostgreSQL' - using an alias column in the where clause in PostgreSQL
Application of slice
No response after heartbeat startup