当前位置:网站首页>Introduction to golang garbage collection
Introduction to golang garbage collection
2022-07-03 20:14:00 【alwaysrun】
List of articles
The core of garbage collection is to mark which memory is still in use ( Is quoted to ), Which memory is no longer used ( It's not quoted ), Reclaim unreferenced memory , For subsequent memory allocation .
Garbage collection
Common garbage collection algorithms :
- Reference count : Maintain a reference count for each object , When the object that references the object is destroyed , Quote count minus 1; When the reference counter is 0 When the object is recycled .
- advantage : Objects can be recycled quickly , There will be no memory exhaustion or until a certain threshold is reached .
- shortcoming : It doesn't handle circular references very well , And maintain reference counts in real time , There is also a price .
- Representative language :Python、PHP、Swift
- Mark - eliminate : Traverse all referenced objects from the root variable , The referenced object is marked as ” Cited ”, Those that are not marked are recycled .
- advantage : Solved the shortcoming of reference counting .
- shortcoming : need STW, That is to stop the program temporarily .
- Representative language :Golang( It adopts three color marking method )
- Generational collection : Divide the generation space according to the life cycle of the object , Long life cycle into the elderly , The new generation is short , Different generations have different recycling algorithms and frequency .
- advantage : Good recycling performance
- shortcoming : Algorithm is complicated
- Representative language :JAVA
go Garbage collection
Garbage collection starts from root Object starts scanning , hold root The memory referenced by the object is marked “ Cited ”( Need to recursively handle pointers ); After all the marks are made , All unmarked identifiers are unassigned .
stay span There is a bit mark for allocating memory in the structure :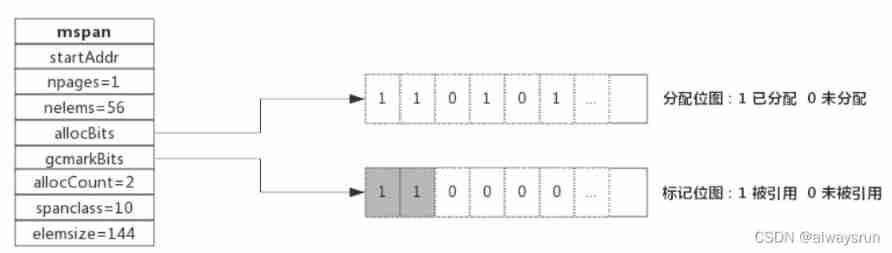
gcmarkBits Record each memory tag , Its structure and allocaBits Exactly the same as ; At the end of the mark , take allocBits Point to gcmarkBits,gcmarkBits Reassign at next mark .
Tricolor notation ( There are three states in the recycling process ):
- gray : The object is still waiting in the tag queue ;
- black : Object has been marked (gcmarkBits The corresponding bit is 1)
- white : The object is not marked (gcmarkBits The corresponding bit is 0), Will be GC Recycle .
Recycling optimization
STW(StopTheWorld) Is to stop all goroutine, Concentrate on garbage collection , Wait until the garbage collection is over goroutine.
Write barriers (Write Barrier): It's Jean goroutine And GC Means to run simultaneously ; stay GC At a specific time , When the pointer is turned on, the pointer will be marked with ( This round is not recycled );
auxiliary GC(Mutator Assist):GC In the process of execution , if goroutine Need to allocate memory , Then let this goroutine Take part GC The job of .
trigger
When the memory allocation reaches the threshold : threshold = The last time GC Memory allocation * Memory growth rate
The memory growth rate is determined by GOGC control , The default is 100, That is, it starts when the memory is doubled GC.
Trigger regularly : By default , The longest 2 Minutes to trigger GC.
runtime.GC(), Can be triggered manually GC.
Escape analysis
Escape analysis (Escape analysis) It means that the compiler decides the memory allocation location ; The compiler determines whether to escape according to whether the object is externally referenced by the function :
- If there is no reference outside the function , Put it on the stack first ( Big object , When the stack storage capacity is exceeded , Will be put in the heap );
- If there is a reference outside the function , It must be in the pile ;
The parameter of the function is interface type , It is difficult to determine the specific type during compilation , There will also be escape ; Local variables referenced in closures will also produce escape ;
- Allocating memory on the stack is more efficient than allocating memory in the heap
- Memory allocated on the stack is not required GC Handle
- The memory allocated on the heap will be handed over to GC Handle
- The purpose of escape analysis is to determine whether the internal allocation address is stack or heap
- Escape analysis is completed in the compilation phase
Passing pointers can reduce the copy of the underlying value , Can improve efficiency , But if the amount of data copied is small , Due to the pointer passing, there will be escape , The heap may be used , It may also increase GC The burden of , So passing pointers doesn't have to be efficient .
Code optimization
To improve performance , Need to reduce the allocation of objects ( Increase reuse , Reduce GC pressure ):
- Reduce object allocation :
- Reuse objects as much as possible ;
- When there are many small objects , Consider encapsulating it into a large object ( adopt struct Combine objects ,GC At the time of scanning , Just judge whether the whole object is valid );
- slice And map Wait for pre allocated memory ;
- string And byte[] When switching between , It will involve memory reallocation and data replication , Try to reduce ;
- Avoid a large number of string connection operations ( adopt + Connect ):
- fmt.Sprintf: Easy to splice strings ;
- strings.Join: Convenient concatenation of string arrays ;
- strings.Builder: Convenient string connection , Try to pre allocate capacity ;
- Slice try to pre allocate capacity : Reduce append Memory reallocation and data replication caused by automatic growth in the process ;
- Clean up in time ( adopt defer Close handle, etc );
边栏推荐
- unittest框架基本使用
- unittest框架基本使用
- How to do Taobao full screen rotation code? Taobao rotation tmall full screen rotation code
- Global and Chinese market of rubidium standard 2022-2028: Research Report on technology, participants, trends, market size and share
- Meso tetra [P - (p-n-carbazole benzylidene imino)] phenylporphyrin (tcipp) /eu (tcipp) [pc( α- 2-oc8h17) 4] and euh (tcipp) [pc (a-2-oc8h17) 4] supplied by Qiyue
- 2.3 other data types
- Test panghu was teaching you how to use the technical code to flirt with girls online on Valentine's Day 520
- Global and Chinese market of two in one notebook computers 2022-2028: Research Report on technology, participants, trends, market size and share
- Don't be afraid of no foundation. Zero foundation doesn't need any technology to reinstall the computer system
- AcWing 1460. Where am i?
猜你喜欢

The 29th day of force deduction (DP topic)

Based on laravel 5.5\5.6\5 X solution to the failure of installing laravel ide helper

AcWing 1460. Where am i?

MPLS configuration

Xctf attack and defense world crypto advanced area best_ rsa
2022 Xinjiang latest construction eight members (standard members) simulated examination questions and answers

2.2 integer
Use of aggregate functions

Derivation of decision tree theory

How to improve data security by renting servers in Hong Kong
随机推荐
Use of CMD command
Basic command of IP address configuration ---ip V4
unittest框架基本使用
Global and Chinese market of liquid antifreeze 2022-2028: Research Report on technology, participants, trends, market size and share
2022-06-27 advanced network engineering (XII) IS-IS overhead type, overhead calculation, LSP processing mechanism, route revocation, route penetration
P5.js development - setting
Unittest framework is basically used
Class loading process
Use of aggregate functions
How to set the system volume programmatically- How to programmatically set the system volume?
Xctf attack and defense world crypto advanced area best_ rsa
47. Process lock & process pool & Collaboration
5. MVVM model
4. Data splitting of Flink real-time project
2022-06-28 advanced network engineering (XIII) IS-IS route filtering, route summary, authentication, factors affecting the establishment of Isis neighbor relations, other commands and characteristics
JMeter connection database
Exercises of function recursion
10 smart contract developer tools that miss and lose
FPGA 学习笔记:Vivado 2019.1 工程创建
HCIA-USG Security Policy