当前位置:网站首页>EasyRE WriteUp
EasyRE WriteUp
2022-07-06 17:23:00 【TiggerRun】
Catalog
Question source :XCTF-Reverse Advanced -004
0x0 New knowledge
XOR Often used to set 0
XOR Reversible operation
0x1 function
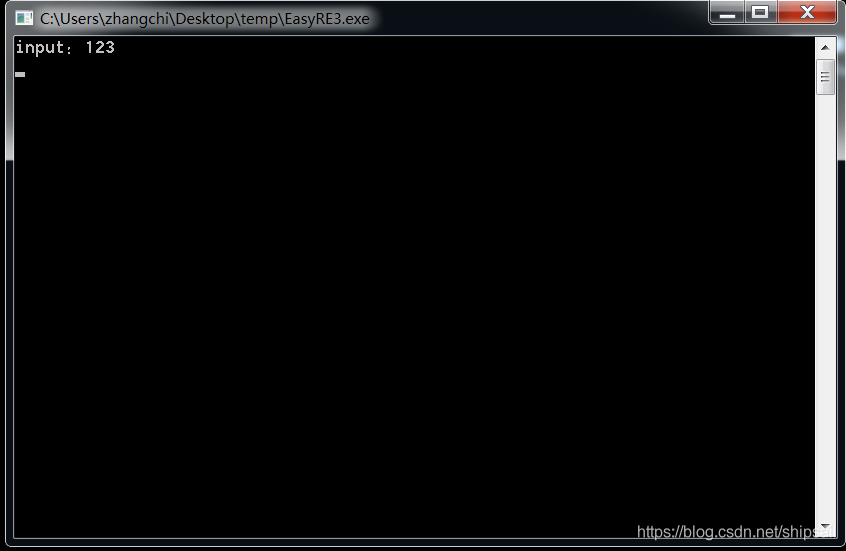
Run prompt input , Exit after entering
0x2 Check the shell
0x3 load IDA 32bit
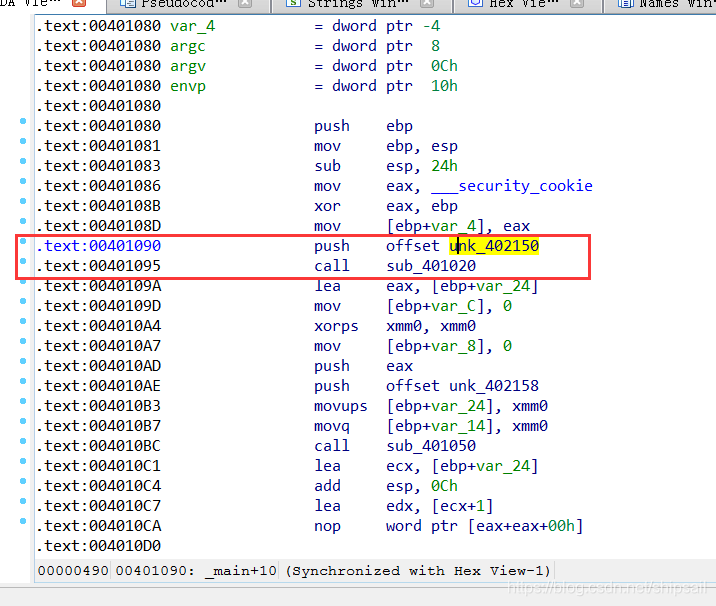
You can know sub_401020 This call yes printf()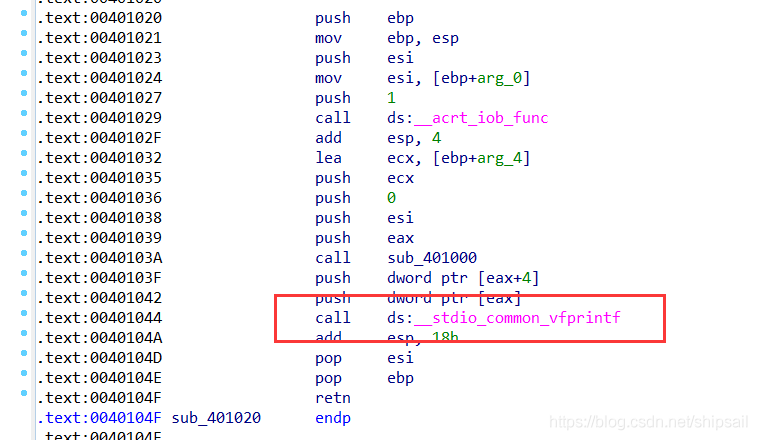
Because I'm still a little white , You can't fully understand program logic by looking at static assembly code like great gods , So I use IDA And OD Dynamic and static analysis .
0x4 close ASLR, Address alignment
I was in WIN7 Next test , So it can be closed manually ASLR Make the program run without random loading .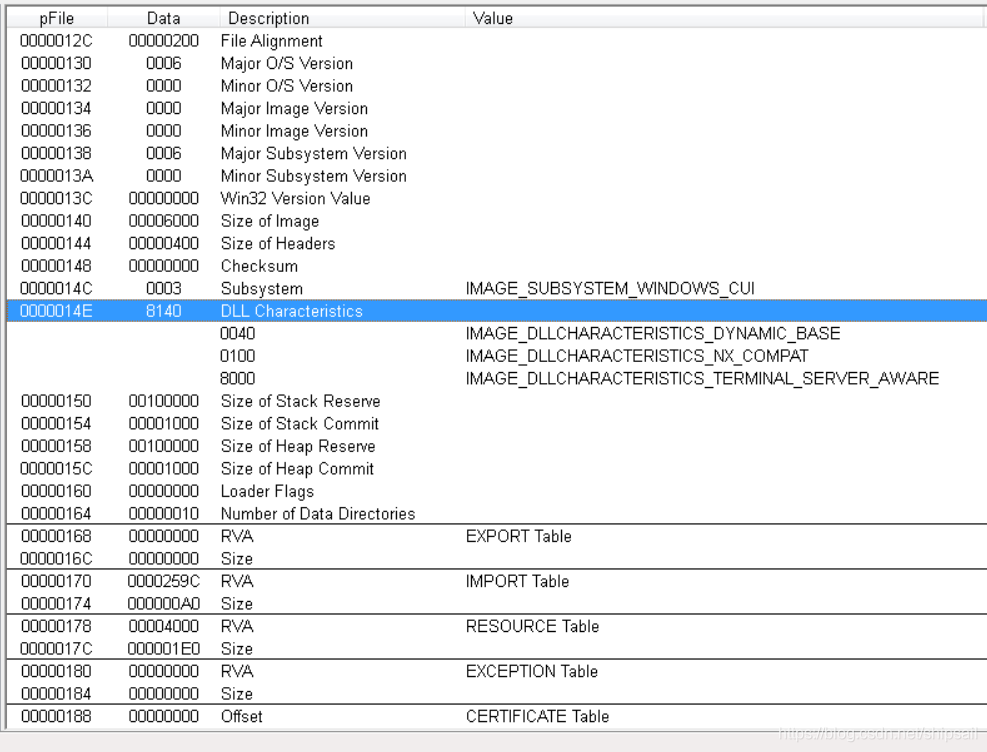
Use VIEW Auxiliary view file offset , Use WinHex Modifying data . stay Win The next data is stored in small end sequence , So you will see in the hexadecimal file 40 81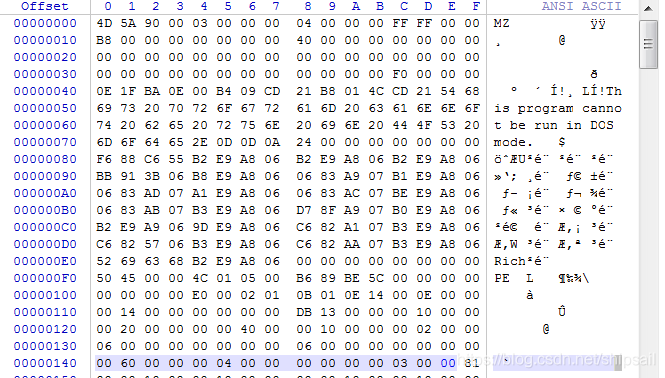
close ASLR The purpose of is to make OD Address and address in IDA Align the addresses in for easy viewing , If it will not be modified ASLR You can also pass API Locate breakpoints .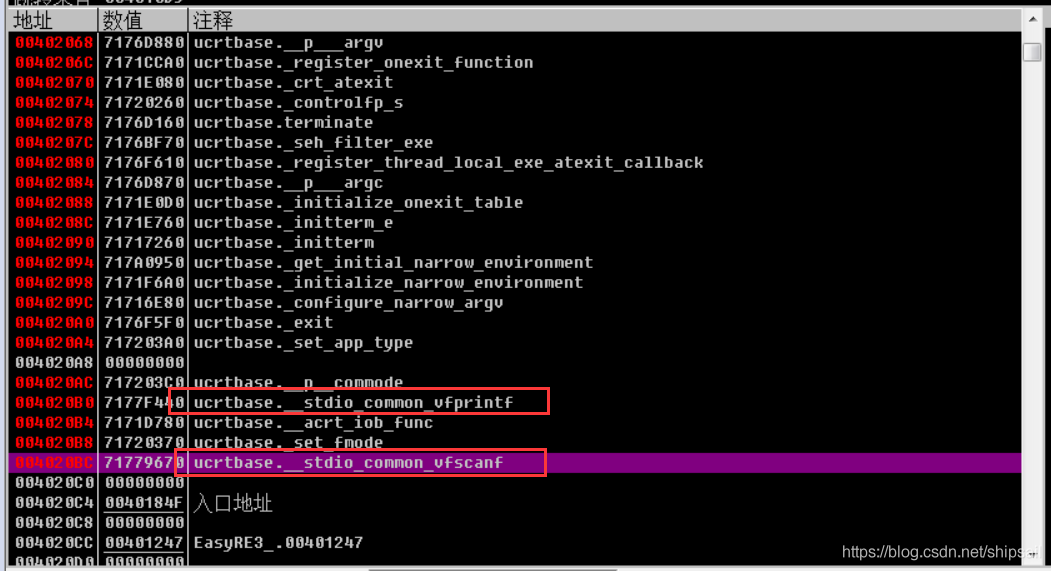
stay IAT You can see all the imported API, I found these two in IDA Functions that appear in , We need to locate the code segment where the program starts to run , As long as scanf Function header and return to the upper layer through the stack .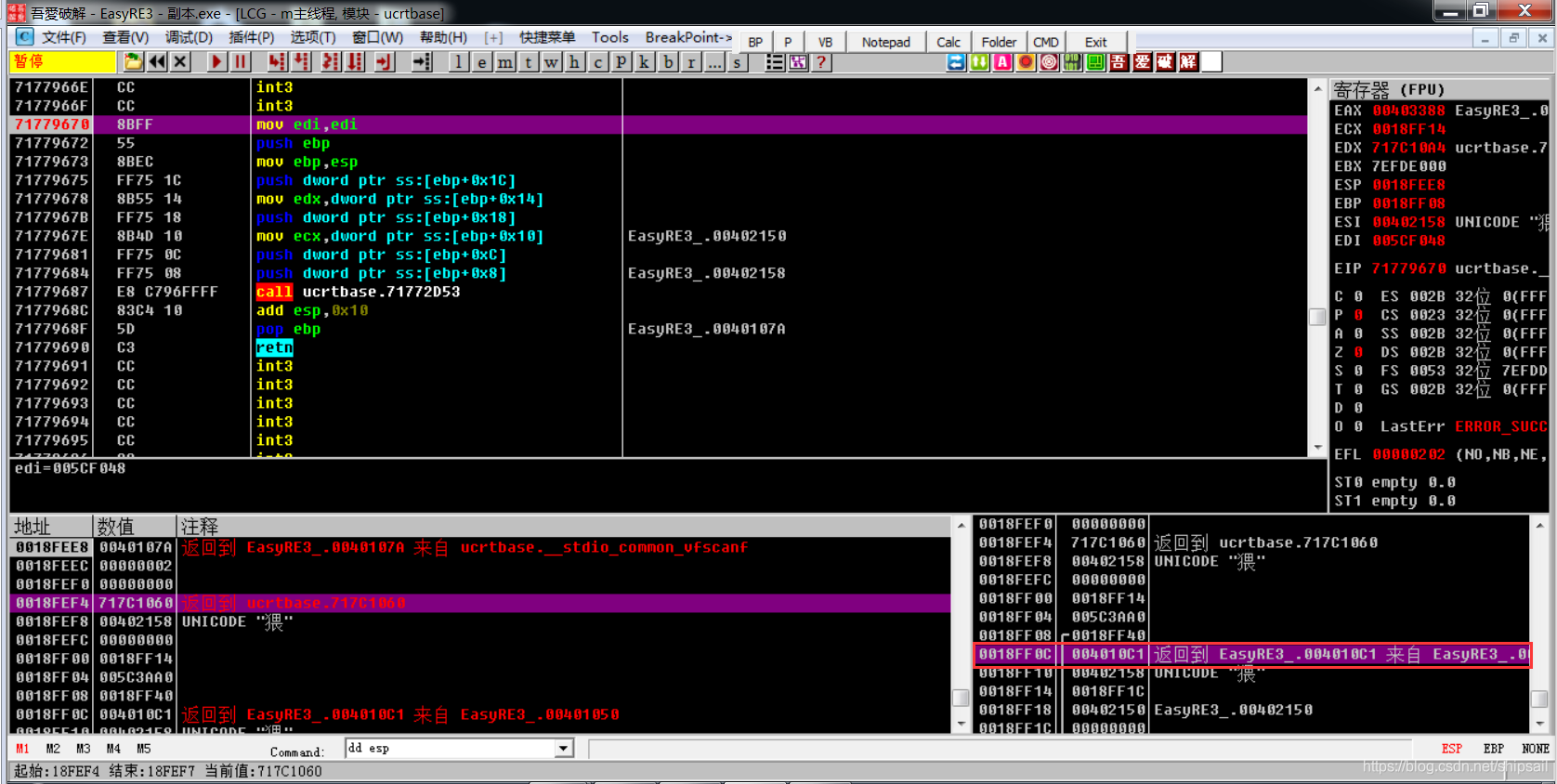
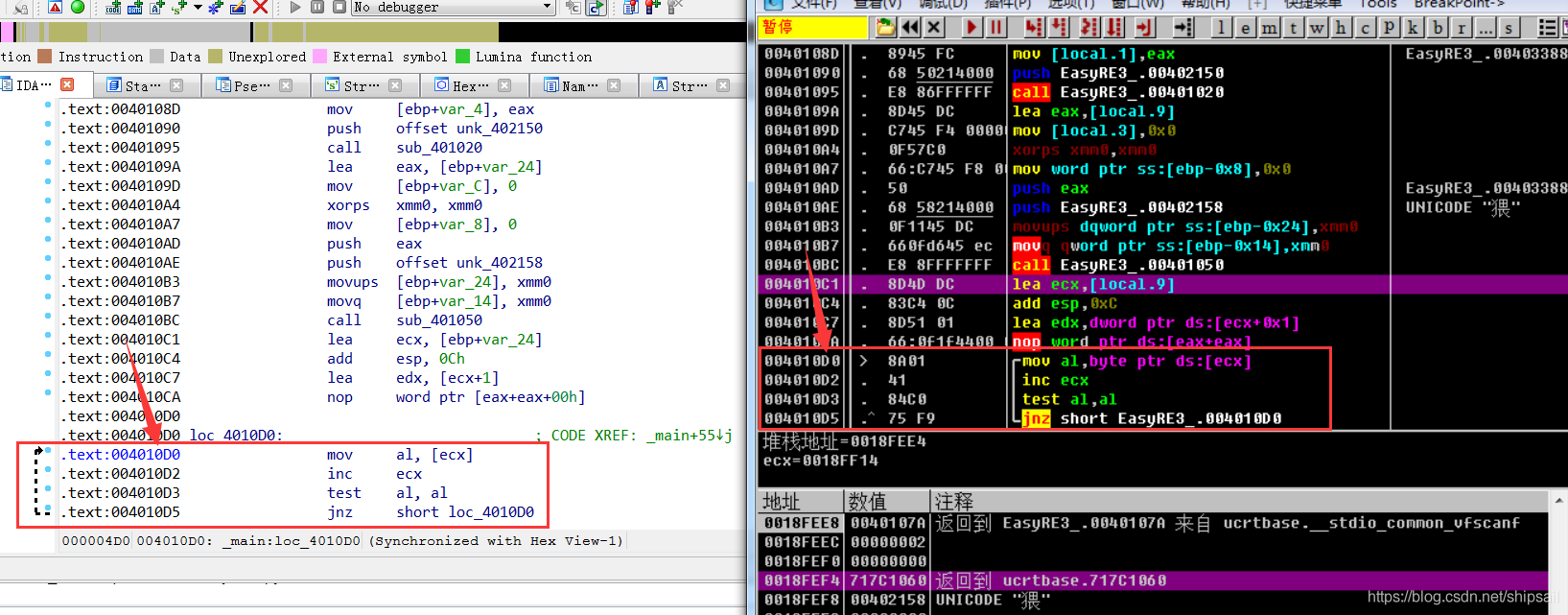
0x5 analysis
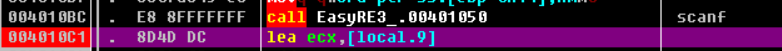
ecx Is assigned to the first address of the array (char *)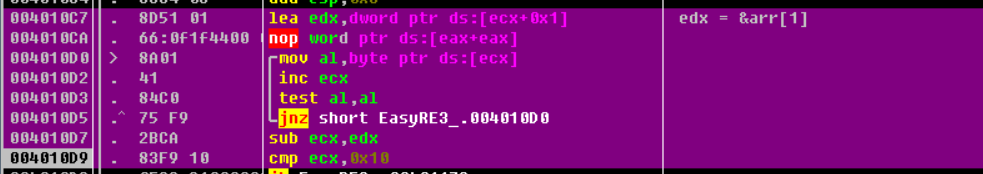
Classic string array traversal ( Say classic , In fact, only after debugging can I know that this is to take the length of the string , Hey, hey, hey ), Look again. IDA Medium Graph.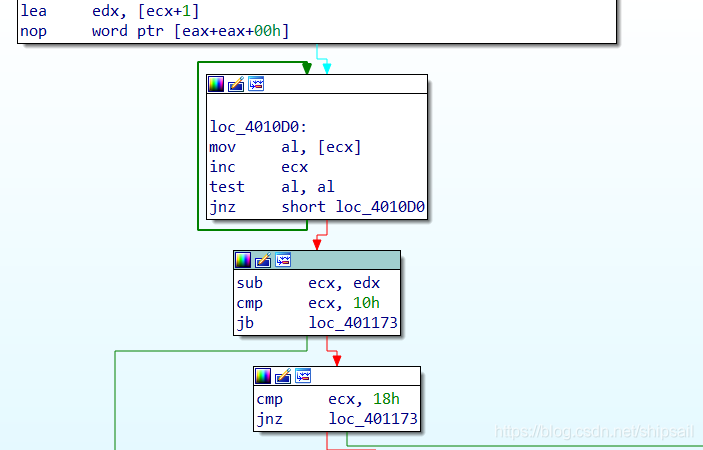
edx = ecx + 0x1
do{
al = ecx
ecx++
}while( al&al != 0)
sub ecx,edx
cmp ecx,0x10
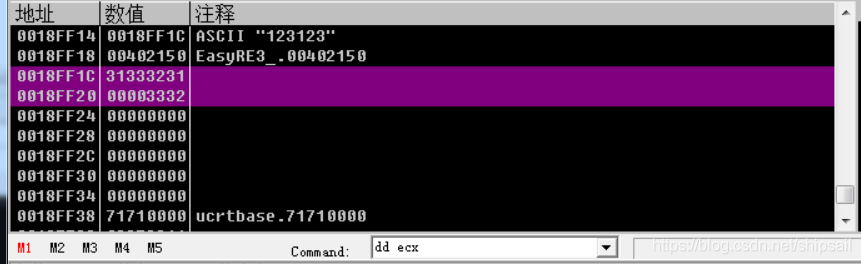
The final string length is stored in ecx in , The length must be 0x18 position
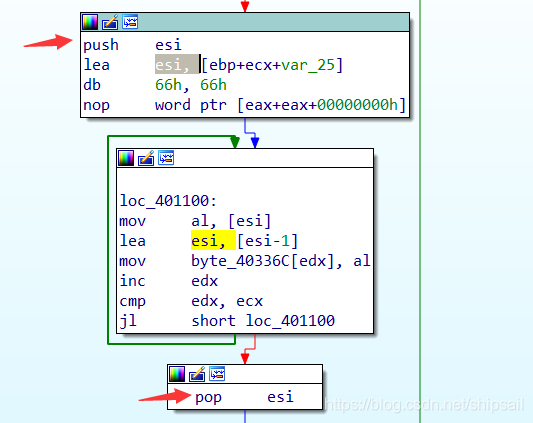
See here push esi and pop esi Temporary storage esi The state of , You can know esi Is a temporary variable .xor edx,edx XOR oneself with oneself to get the result 0x0,mov esi , ebp + ecx - 0x25 You know esi The address where the last character of the array is stored . Through the following calculation :arr[0] = ebp - 0x24arr[0x18-1] = ebp - 0x24 + ecx - 0x1
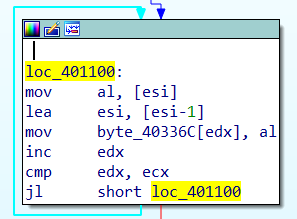
Through this cycle, we can see esi Decline ,edx Increasing , Reverse the string .
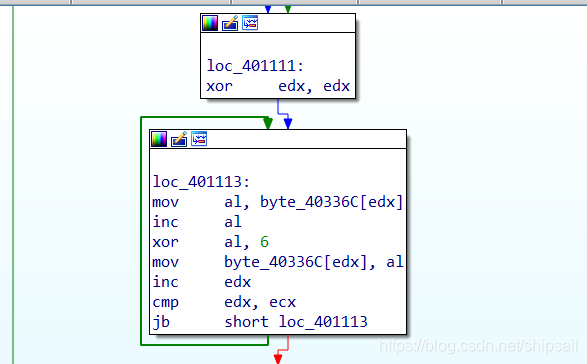
The following cycle will again edx Register set 0, For cycle counting
Add each element by itself 1 After and 0x6 Do XOR operation and save back 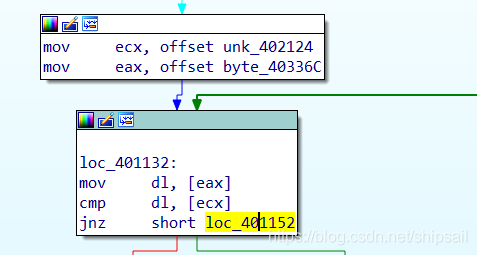
Compare two strings 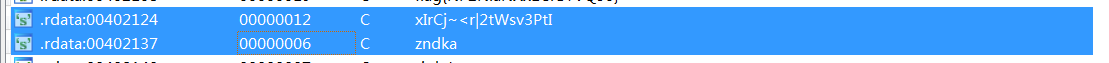
0x6 summary
- Input
- The length is limited to 0x18 namely 24 Characters
- Reverse array
- Each element is +1 ^ 6 operation
- Compare strings for equality
0x7 scripting
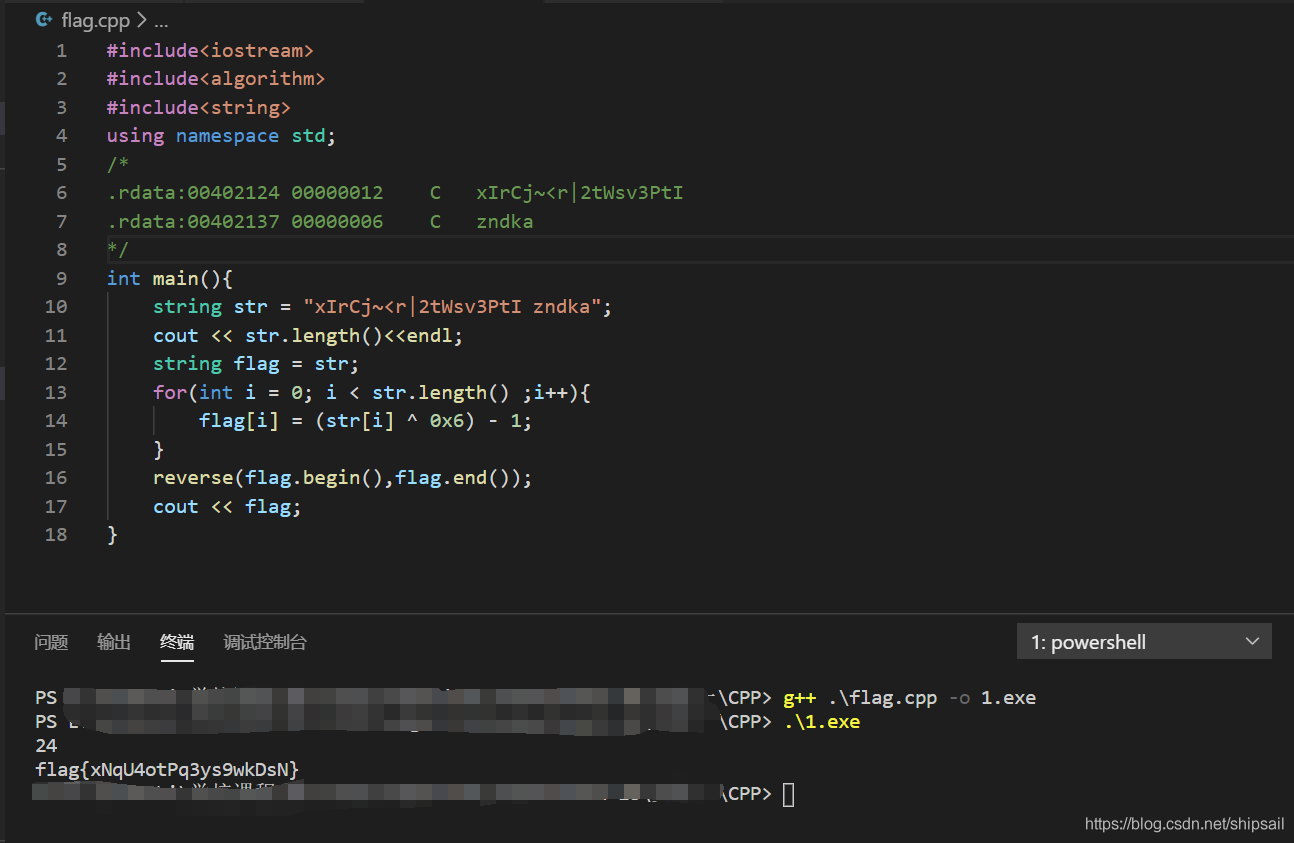
The XOR operation is reversible , Here is the fight 1bit The result of the operation 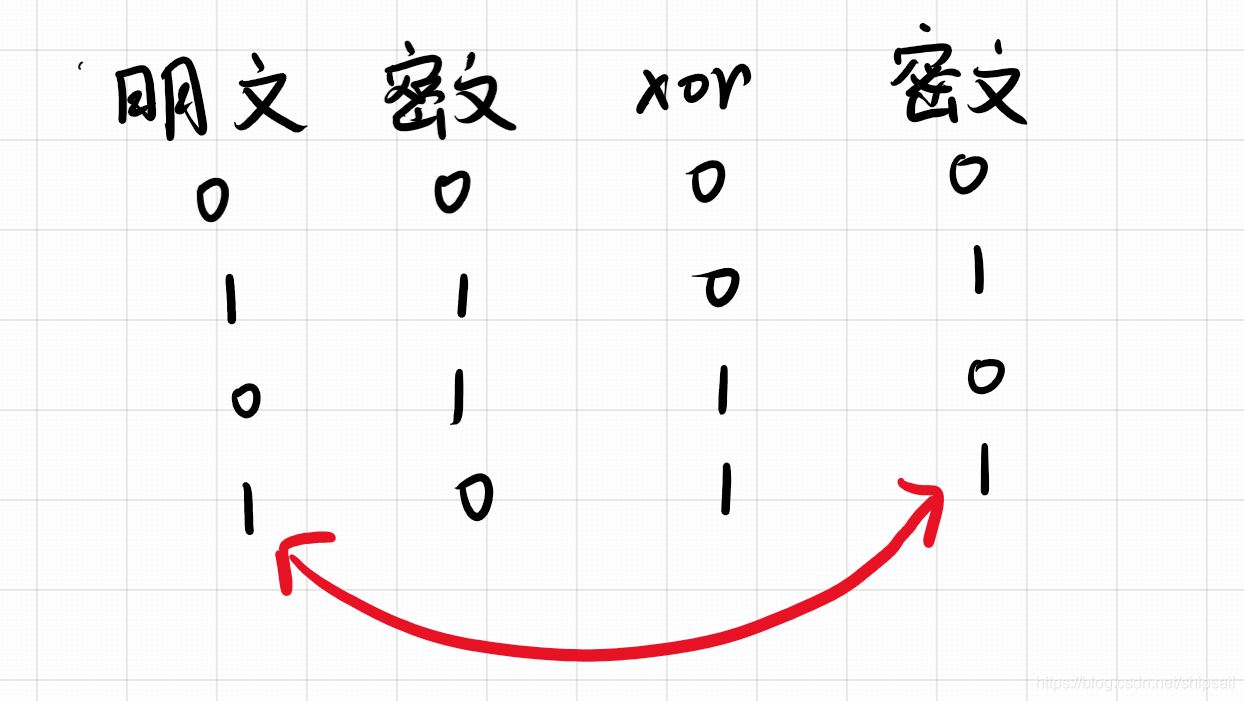
#include<iostream>
#include<algorithm>
#include<string>
using namespace std;
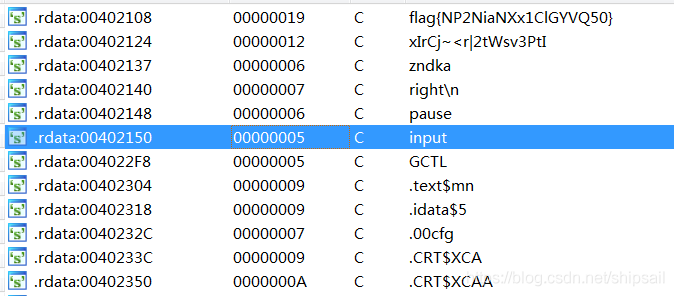
/* .rdata:00402124 00000012 C xIrCj~<r|2tWsv3PtI .rdata:00402137 00000006 C zndka */
int main(){
string str = "xIrCj~<r|2tWsv3PtIzndka";
cout << str.length()<<endl;
string flag = str;
for(int i = 0; i < str.length() ;i++){
flag[i] = (str[i] ^ 0x6) - 1;
}
reverse(flag.begin(),flag.end());
cout << flag;
}

0x8 Try IDA One click decompilation
int __cdecl main(int argc, const char **argv, const char **envp)
{
unsigned int v3; // kr00_4
signed int v4; // edx
char *v5; // esi
char v6; // al
unsigned int v7; // edx
int v8; // eax
__int128 v10; // [esp+2h] [ebp-24h]
__int64 v11; // [esp+12h] [ebp-14h]
int v12; // [esp+1Ah] [ebp-Ch]
__int16 v13; // [esp+1Eh] [ebp-8h]
sub_401020(&unk_402150, v10);
v12 = 0;
v13 = 0;
v10 = 0i64;
v11 = 0i64;
sub_401050((const char *)&unk_402158, (unsigned int)&v10);
v3 = strlen((const char *)&v10);
if ( v3 >= 0x10 && v3 == 24 )
{
v4 = 0;
v5 = (char *)&v11 + 7;
do
{
v6 = *v5--;
byte_40336C[v4++] = v6;
}
while ( v4 < 24 );
v7 = 0;
do
{
byte_40336C[v7] = (byte_40336C[v7] + 1) ^ 6;
++v7;
}
while ( v7 < 0x18 );
v8 = strcmp(byte_40336C, (const char *)&unk_402124);
if ( v8 )
v8 = -(v8 < 0) | 1;
if ( !v8 )
{
sub_401020("right\n", v10);
system("pause");
}
}
return 0;
}
You can find , To obtain the length of the 、 Reverse order, etc. , If you look directly at it at the beginning IDA The decompilation result of will be more efficient , Although the code looks a little strange … Get used to it ! I just installed it today IDA!!! Continue punching .
边栏推荐
猜你喜欢
![Case: check the empty field [annotation + reflection + custom exception]](/img/50/47cb40e6236a0ba34362cdbf883205.png)
Case: check the empty field [annotation + reflection + custom exception]
03个人研发的产品及推广-计划服务配置器V3.0

Shawshank's sense of redemption
Alibaba cloud server docker installation mysql5.5
Activit fragmented deadly pit
Flink 解析(三):内存管理
Activiti目录(五)驳回、重新发起、取消流程
arithmetic operation
CTF reverse entry question - dice
Install docker under windows10 (through Oracle VM VirtualBox)
随机推荐
CentOS7上Redis安装
Only learning C can live up to expectations top5 S1E8 | S1E9: characters and strings & arithmetic operators
How does wechat prevent withdrawal come true?
吴军三部曲见识(四) 大家智慧
MySQL字符串函数
JVM garbage collector part 1
JUnit unit test
手把手带你做强化学习实验--敲级详细
Activiti目录(一)重点介绍
MySQL string function
学习投资大师的智慧
在 vi 编辑器中的命令模式下,删除当前光标处的字符使用 __ 命 令。
Redis installation on centos7
Description of project structure configuration of idea
Akamai anti confusion
Case: check the empty field [annotation + reflection + custom exception]
Activit零零碎碎要人命的坑
Activiti directory (IV) inquiry agency / done, approved
SQL调优小记
Connect to LAN MySQL