当前位置:网站首页>Flash encryption process and implementation of esp32
Flash encryption process and implementation of esp32
2022-07-07 23:33:00 【Little river god is tangled】
List of articles
Preface
After a project is completed , To prevent secondary burning or firmware piracy , Usually program encryption , It's like STM32 Of flash Write protection 、 only ID Program encryption is similar to .
Lexin provides us flash Encryption scheme ,flash The encryption function is used to encrypt and ESP32 Off chip for use flash The content in . Enable flash After the encryption function , Firmware will be burned in clear text , Then encrypt the data at the first startup . therefore , Physical read flash Will not be able to recover most flash Content .
One 、 Be careful
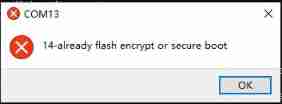
Please familiarize yourself with this article and try to do the encryption experiment , Because encryption is one-time , It may cause the module to become... Due to encryption “ Soft brick ”, After encryption , Will not be available flash_download_tool Tool for firmware burning , You'll get a hint like this :
Two 、flash The encryption process
hypothesis eFuse The value is in the default state , And the boot loader of the firmware is compiled to support flash encryption , be flash The specific process of encryption is as follows :
When the first power on reset ,flash All data in is unencrypted ( Plaintext ).ROM Boot loader loads firmware boot loader .
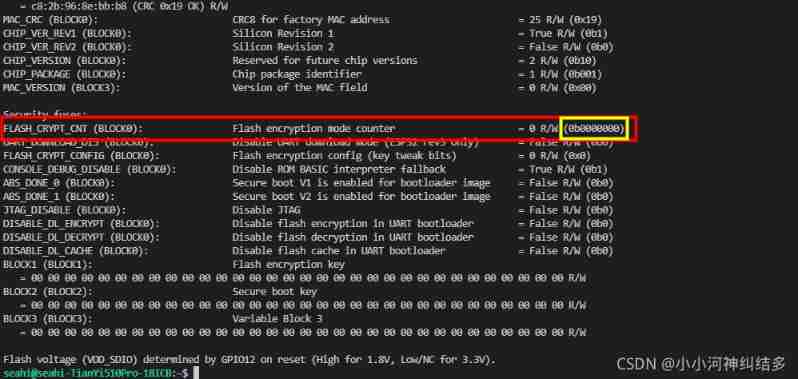
The boot loader of the firmware will read FLASH_CRYPT_CNT eFuse value (0b0000000). Because the value is 0( Even digit ), The boot loader for the firmware will be configured and enabled flash Encryption block , At the same time FLASH_CRYPT_CONFIG eFuse The value of is programmed to 0xF.
The boot loader of the firmware uses RNG( Random number generation ) Module generation AES-256 A key , And then write it in flash_encryption eFuse in . because flash_encryption eFuse Write and read protection bits have been set , You will not be able to access the key through the software .Flash The encryption operation is completely completed in hardware , The key cannot be accessed through software .
Flash The encryption block will encrypt flash The content of ( Boot loader for firmware 、 Applications 、 And marked with “ encryption ” Mark the partition ). In place encryption may take some time ( For large partitions, it takes up to one minute ).
The firmware boot loader will be in FLASH_CRYPT_CNT (0b0000001) Set the first available bit in to encrypt the encrypted flash Mark the content . Set an odd number of bits .
about Development mode , The firmware boot loader only sets DISABLE_DL_DECRYPT and DISABLE_DL_CACHE Of eFuse position , In order to UART Boot loader reburning encrypted binaries . Besides , FLASH_CRYPT_CNT Of eFuse Bits are not write protected .
about Release pattern , Firmware boot loader settings DISABLE_DL_ENCRYPT、DISABLE_DL_DECRYPT and DISABLE_DL_CACHE Of eFuse Position as 1, To prevent UART Boot loader decrypts flash Content . It's also write protected FLASH_CRYPT_CNT eFuse position . To modify this behavior , see also Enable UART Boot loader encryption / Decrypt .
Restart the device to start the encrypted image . The firmware boot loader calls flash Decrypt the block flash Content , Load the decrypted content into IRAM in .
In short : After the encrypted program starts , First, it will be encrypted by the program boot . Encryption takes time , After encryption is successful , Will be able to FLASH_CRYPT_CNT From 0x0 Turn into 1 or 0xf, Finally start executing the user program .
3、 ... and 、 Encryption mode
Flash There are two modes of encryption , One is the development model 、 The other is the production mode .
3.1 Development mode encryption
Since it's encryption , That must require a key , Lexin also provides us with two methods of encryption or generation of keys :
3.1.1 Use ESP32 The generated key is encrypted
Using this encryption method , The key is unique , And invisible . The key will not be saved in the system file , It will only be randomly generated and burned to efuse Partition .
Be careful :
Before doing the encryption experiment , And ensure that the module does not do any encryption , The query instruction of encryption status is ,(PORT Is the serial port number ):
espefuse.py -p PORT summary
This article will be hello_world Routine as an example to encrypt , stay hello_world Run in directory :
idf.py menuconfig
Do the following :
- Enable at startup flash encryption
- Select publishing mode ( Note that once the publishing mode is selected ,DISABLE_DL_ENCRYPT and DISABLE_DL_DECRYPT eFuse The bit will be programmed at ROM Disable in download mode flash Encryption hardware )
- choice UART ROM Download mode ( It is recommended to permanently disable ) ( Note that this option is only available in CONFIG_ESP32_REV_MIN Level set to 3 when (ESP32 V3) You can use .) The default option is to keep enabled UART ROM Download mode , However, it is recommended to disable this mode permanently , To reduce the options available to attackers .
- Select the boot loader log with the appropriate level of detail
- Save the configuration and exit

And then run directly :
idf.py flash monitor
Screenshot of successful encryption :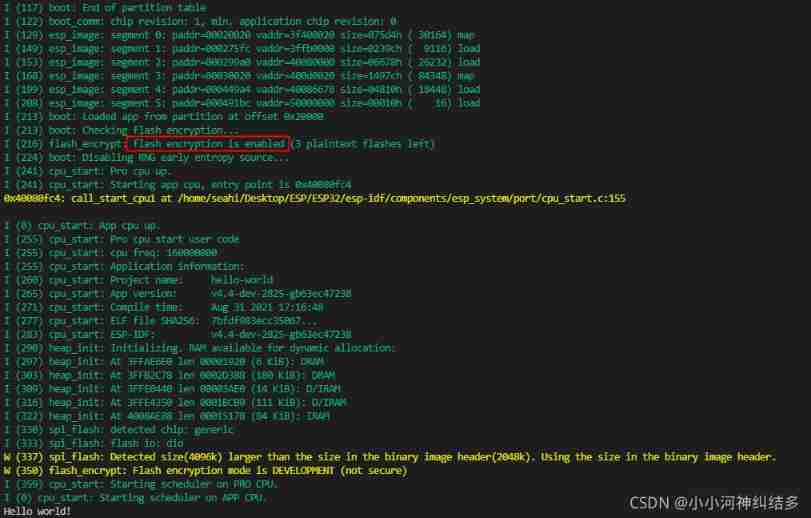
Then we can take a look at :FLASH_CRYPT_CNT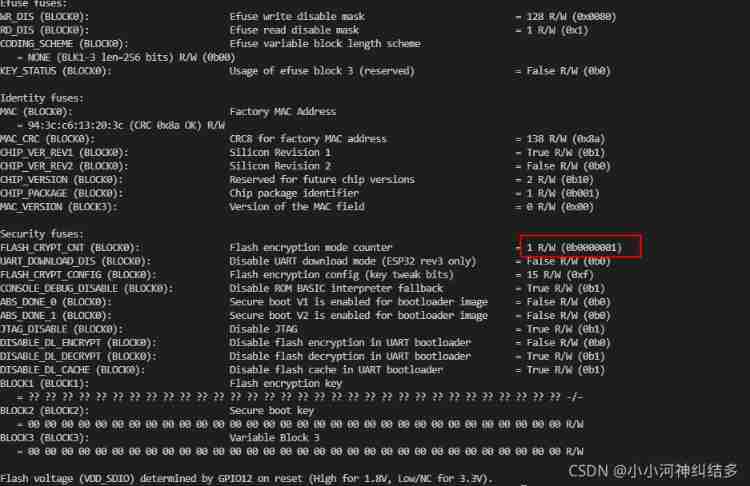
You can see ,FLASH_CRYPT_CNT The value of is set to 1; It means that it has been successfully encrypted .
3.1.2 Use the self generated key for encryption
Using the self generated key is actually the step of burning the key , Key generation instruction :
espsecure.py generate_flash_encryption_key my_flash_encryption_key.bin
I suggest saving the key in a separate file , Prevent false deletion . After generating the key , Use the following command to burn the key :
espefuse.py --port PORT burn_key flash_encryption my_flash_encryption_key.bin
next step , It can be based on 3.1.1 Configuration burning in
3.2 Production mode encryption
Use the development mode , Can still be used idf.py Script burning , It's just a limit on the number of times , But you can turn off encryption :
espefuse.py burn_efuse FLASH_CRYPT_CNT
However, the encrypted burning of production mode has no chance of repeated burning , It is usually used in mass production , Because it's disposable , After burning, you can only pass OTA To upgrade the program . Its configuration is as follows :
Use it directly :
idf.py flash monitor
So , The blogger's module becomes “ Soft brick ”: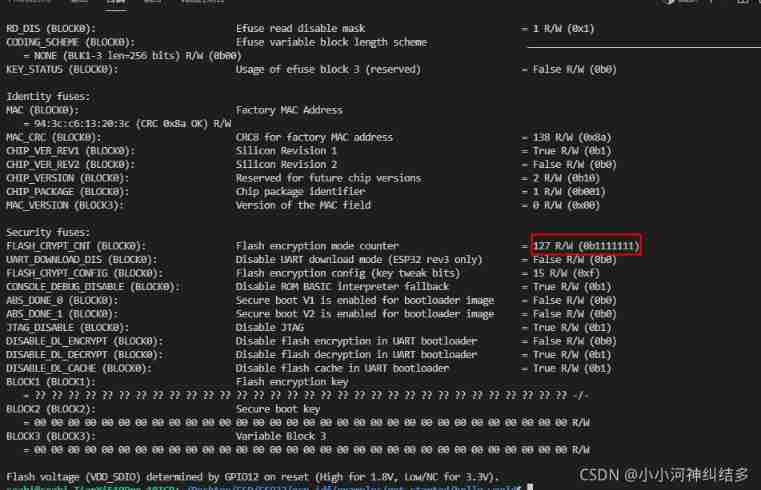
For more information, please skip :
https://docs.espressif.com/projects/esp-idf/zh_CN/latest/esp32/security/flash-encryption.html#flash-encryption-status
Welcome to your attention : Anxinko Technology
边栏推荐
猜你喜欢
![MATLAB signal processing [Q & A essays · 2]](/img/be/0baa92767c3abbda9b0bff47cb3a75.png)
MATLAB signal processing [Q & A essays · 2]
Map operation execution process
Right click the idea file to create new. There is no solution to create new servlet
Explain

S2b2b mall solution of intelligent supply chain in packaging industry: opening up a new ecosystem of e-commerce consumption
在软件工程领域,搞科研的这十年!
Solve the problem of duplicate request resource paths /o2o/shopadmin/o2o/shopadmin/getproductbyid

2022注册测绘师备考开始 还在不知所措?手把手教你怎么考?

B_ QuRT_ User_ Guide(36)

re1攻防世界逆向
随机推荐
【7.4】25. K 个一组翻转链表
POJ2392 SpaceElevator [DP]
IDEA 2021.3. X cracking
S2b2b mall solution of intelligent supply chain in packaging industry: opening up a new ecosystem of e-commerce consumption
B_QuRT_User_Guide(37)
Given an array, such as [7864, 284, 347, 7732, 8498], now you need to splice the numbers in the array to return the "largest possible number."
First week of July
MySQL Index Optimization Practice I
B_ QuRT_ User_ Guide(38)
System design overview
Opencv scalar passes in three parameters, which can only be displayed in black, white and gray. Solve the problem
深入理解Mysql锁与事务隔离级别
B_ QuRT_ User_ Guide(36)
As a new force, chenglian premium products was initially injected, and the shares of relevant listed companies rose 150% in response
SRM supplier cloud collaborative management platform solution for building materials industry to realize business application scalability and configuration
系统设计概述
Live server usage
PHP uses Alibaba cloud storage
Sequence of entity layer, Dao layer, service layer and controller layer
Summary of common methods of object class (September 14, 2020)