当前位置:网站首页>Evolution of APK reinforcement technology, APK reinforcement technology and shortcomings
Evolution of APK reinforcement technology, APK reinforcement technology and shortcomings
2022-07-05 22:29:00 【Poor Stephen】
Mainstream reinforcement manufacturers
- Tencent legu
- 360 strengthening
- Ali gather security
- Baidu reinforcement
- Reinforcement of top image
- Netease cloud reinforcement
- Bang Bang reinforcement
- Love encryption
- Naga
- Tongfu shield reinforcement
- ...
The first generation of shells : Dynamic loading
The development process
The program is divided into loading (loader) And key logic (payload) Two parts , And packed separately
Core logic
Startup time loader Will run first , Release key logic payload, And then use java Dynamic loading technology for loading , And transfer control
deficiencies
1、payload Some need to be decompressed and released in the file system , You can get it directly
2、 Can pass hook Virtual machine keyword function , In the load payload When the dex In memory dump come out
Second generation shells : The memory is not loaded
The development process
load loader, initialization StubApplication, Load after decryption payload, Transfer control to the original appcation Of Oncreate Method , It is best to load other components normally
Core logic
1、 Interception system IO Correlation function , Such as read/write, Provide transparent encryption in these functions
2、 Directly call the functions provided by the virtual machine to load without landing , That is, memory loading .
deficiencies
1、 Perform a large number of decryption operations at startup , It's easy to get stuck or fake death
2、payload After being loaded , It's continuous in memory , Intercept key functions in memory dump It can still be obtained directly .
Third generation shells : Generation instruction extraction
The development process
First, the protection level is reduced to the function level , And then the original dex Function content in Code Item Clean up 、 Move to encrypted file separately 、 At runtime, the function content will be restored to the corresponding function body
Core logic
1、 After loading, restore the function memory to dex In the memory area
2、 The virtual machine reads dex After the document , Memory has a structure for each function , One of them only points to the content of the function Codeitem, You can modify the corresponding function content by modifying this pointer
3、 Intercept functions related to finding and executing code in the virtual machine , Return function content
deficiencies
1、 Instruction extraction scheme and virtual machine jit Optimization conflict 、 Not the best performance
2、 Still used java Virtual machine performs function content execution , It cannot resist custom virtual machines such as dexhunter
3、 Use a lot of virtual machine internal structure 、 There are compatibility issues
The fourth generation of shells : Conversion instructions
Core logic
1、dex The function of the file is marked native, The content is extracted and transformed into JNI Standard dynamic library so file 、so File by JNI and Android System interaction
2、 The content of the function body is extracted and converted into a custom instruction format 、 This format is executed using a custom receiver , Then use JNI Interact with the system
deficiencies
1、 An attacker can convert instructions /VMP The reinforcement scheme is regarded as a black box 、 Through custom JNI The interface object detects the inside of the black box 、 Record and analyze ;
2、 The four generation VMP Generally, it is used together with the third generation reinforcement technology 、 The problems of the three generations 、 The scheme still exists
The fifth generation shell :VMP Virtual machine source code protection
Core logic
1、 Based on the fourth generation solution :Java or kotlin => C++ That is to use java2cpp programme
2、 be based on LLVM Tool chain implementation so Of VMP;
3、 Through to IR Do instruction conversion , Generate custom instruction set IR => VM , app An independent execution environment is isolated internally , The core code runs under this environment ;
deficiencies
1、 Can't get rid of JNI Dependence
2、 because java2cpp It will lead to a linear increase in volume , Performance is down ;
边栏推荐
- Golang writes the opening chapter of selenium framework
- Metaverse Ape猿界应邀出席2022·粤港澳大湾区元宇宙和web3.0主题峰会,分享猿界在Web3时代从技术到应用的文明进化历程
- 南京:全面启用商品房买卖电子合同
- Search: Future Vision (moving sword)
- Metaverse Ape获Negentropy Capital种子轮融资350万美元
- Thinkphp5.1 cross domain problem solving
- FBO and RBO disappeared in webgpu
- opencv 判断点在多边形内外
- A substring with a length of three and different characters in the leetcode simple question
- Interview questions for famous enterprises: Coins represent a given value
猜你喜欢
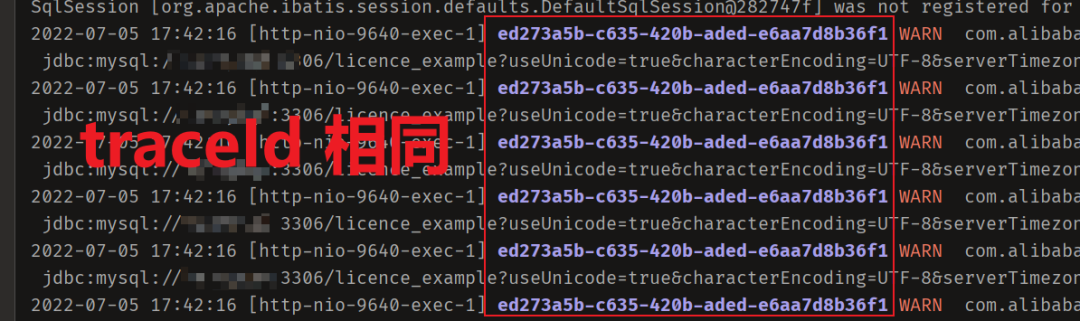
从 1.5 开始搭建一个微服务框架——日志追踪 traceId
Oracle hint understanding
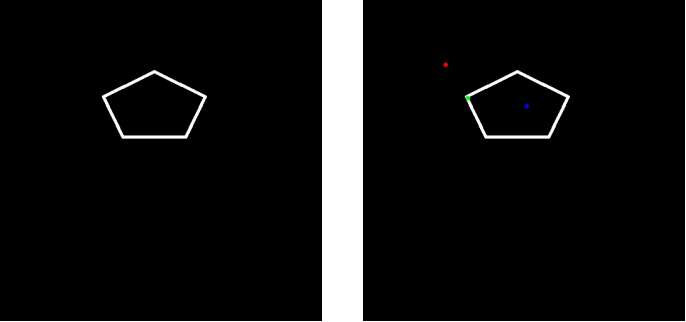
Opencv judgment points are inside and outside the polygon
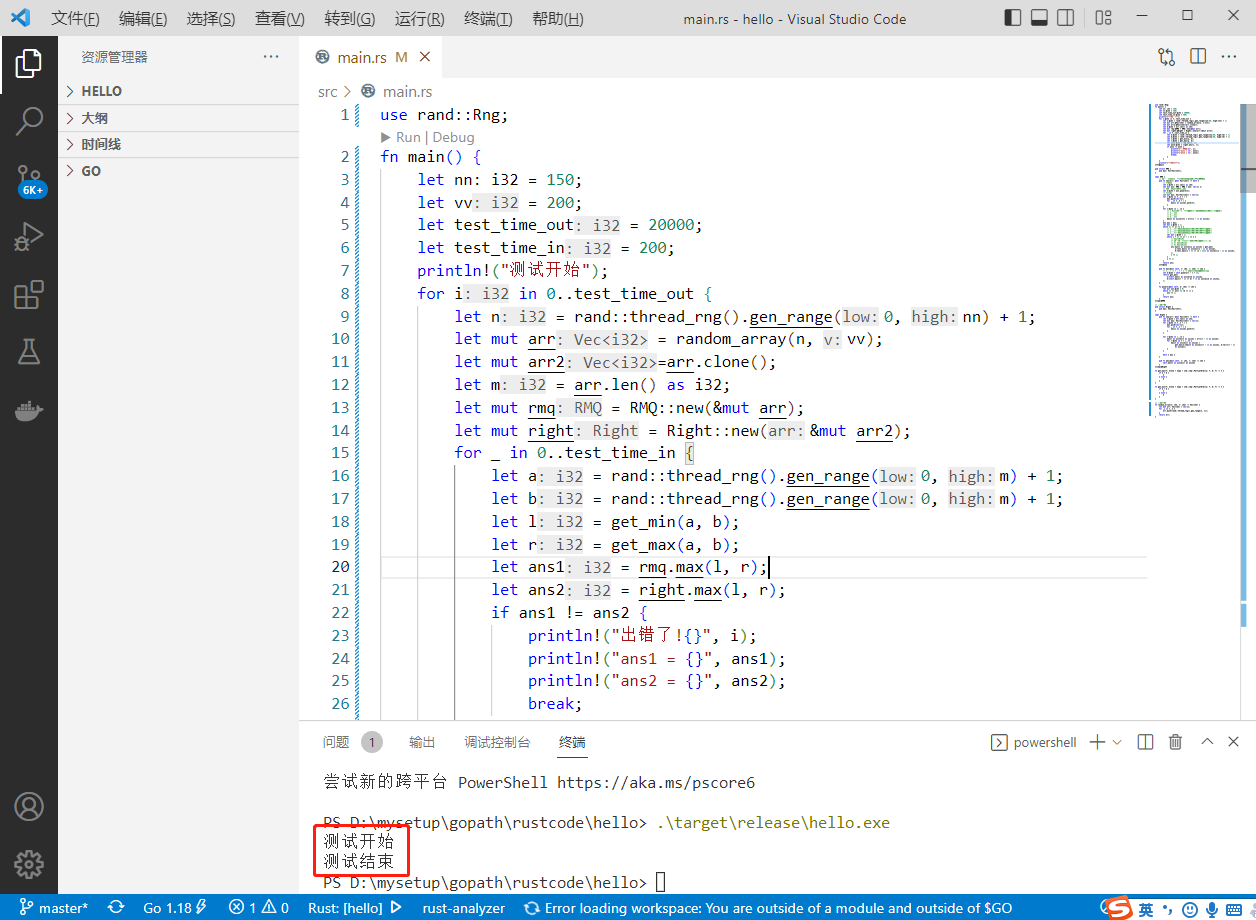
2022-07-05: given an array, you want to query the maximum value in any range at any time. If it is only established according to the initial array and has not been modified in the future, the RMQ meth
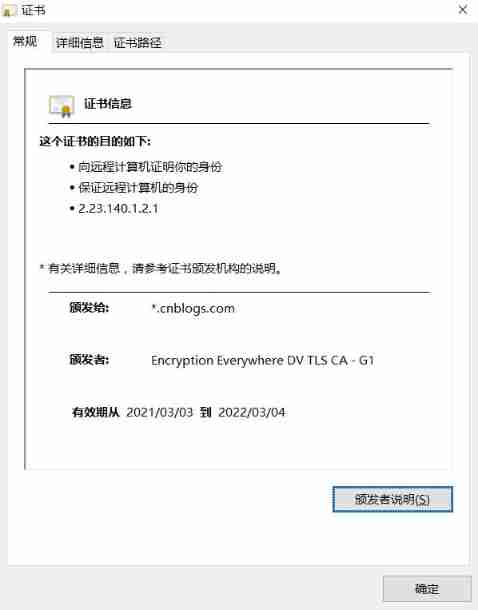
CA certificate trampled pit

What changes has Web3 brought to the Internet?
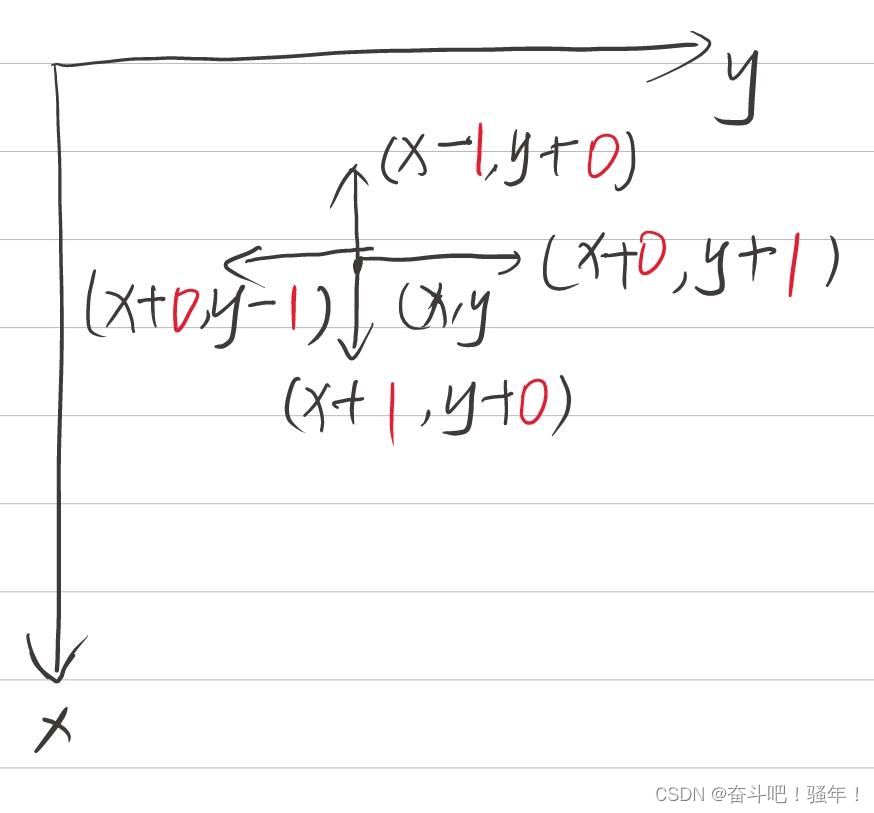
第一讲:蛇形矩阵
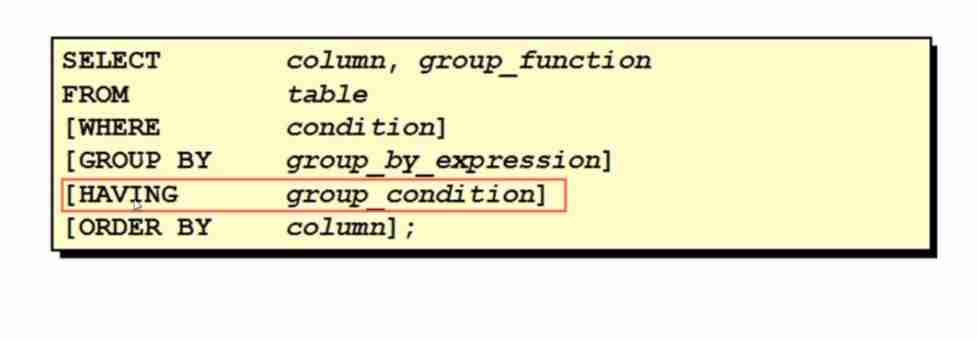
Oracle advanced query

Summary of concurrency control
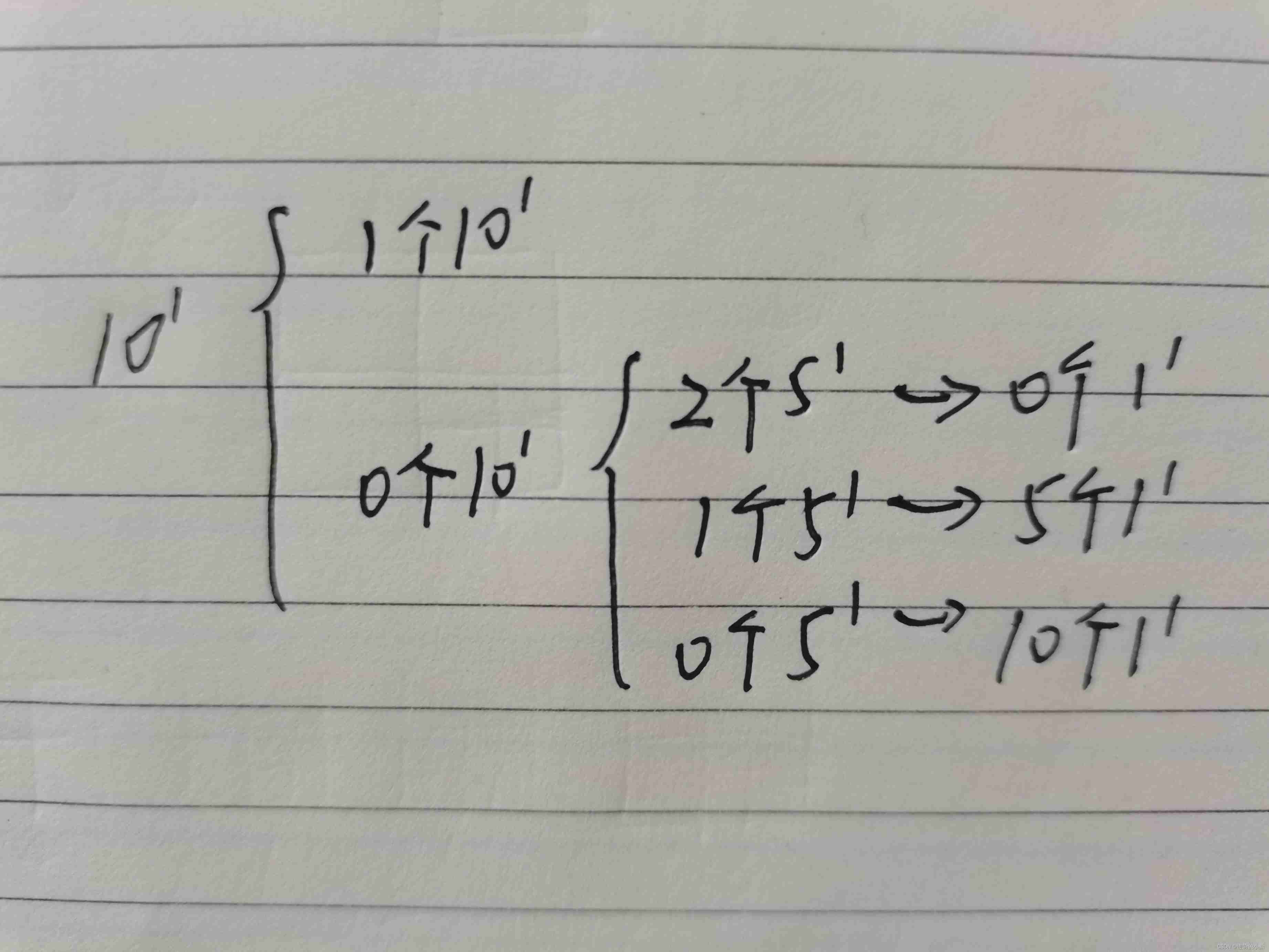
Interview questions for famous enterprises: Coins represent a given value
随机推荐
Serializability of concurrent scheduling
Calculation method of boundary IOU
90后测试员:“入职阿里,这一次,我决定不在跳槽了”
Unique occurrence times of leetcode simple questions
Win11缺少dll文件怎么办?Win11系统找不到dll文件修复方法
[groovy] mop meta object protocol and meta programming (execute groovy methods through metamethod invoke)
Solve the problem of "no input file specified" when ThinkPHP starts
Text组件新增内容通过tag_config设置前景色、背景色
MySQL actual combat 45 lecture learning (I)
344. Reverse String. Sol
Cobaltstrike builds an intranet tunnel
Some tutorials install the database on ubantu so as not to occupy computer memory?
Oracle is sorted by creation time. If the creation time is empty, the record is placed last
Wonderful review of the digital Expo | highlight scientific research strength, and Zhongchuang computing power won the digital influence enterprise award
Hcip day 16
U盘的文件无法删除文件怎么办?Win11无法删除U盘文件解决教程
Form artifact
The new content of the text component can be added through the tag_ Config set foreground and background colors
Metaverse Ape猿界应邀出席2022·粤港澳大湾区元宇宙和web3.0主题峰会,分享猿界在Web3时代从技术到应用的文明进化历程
How to create a thread