当前位置:网站首页>Illustrated network: the principle behind TCP three-time handshake, why can't two-time handshake?
Illustrated network: the principle behind TCP three-time handshake, why can't two-time handshake?
2022-07-06 00:37:00 【InfoQ】
What is? TCP?
- English full name :
Transmission Control Protocol
- Chinese name :Transmission control protocol

TCP Three handshakes
Three handshakes in life

- Xiao Ming : Hello , Is it Xiaomei ?【The first handshake】
- Xiaomei : Yes , I'm Xiaomei .【The second handshake】
- Xiao Ming : well , I know you are Xiaomei .【The third handshake】
Three professional handshakes
- Server side: The server is a physical computer dedicated to running services to meet the needs of other computers

- client: The client is the computer hardware device or software that accesses the services provided by the server
- SYN: Sync serial number (Synchronize Sequence Number), This is the first packet from the client to the server , It can be described as a request to establish a connection , If SYN by 1, It means that the device needs to establish a secure connection , Otherwise not .

- ACK: confirm (Acknowledgement), Can be said to be SYN Response , If ACK by 1, The device has received SYN Message and confirm , Otherwise no .



- First step :TCP The client sends... To the server TCP SYN Packets to start the connection , The packet contains a random serial number n, It represents the serial number of the data that the client should transmitStart.

- The second step : The server receives the packet , And use its serial number (m) To respond , Its response also includes the confirmation number , That is, the serial number of the client plus 1, Here is n+1.

- The third step : The client responds to the server by sending a confirmation number , The confirmation number is the serial number of the server plus 1, Here is m+1.

TCP Analysis of three handshakes

172.16.16.128:2826212.58.226.142:80- First step : host
172.16.16.128:2826Host computer212.58.226.142:80send out [SYN] Seq=0
- The second step : host
212.58.226.142:80Host computer172.16.16.128:2826send out [SYN,ACK] Seq=0,Ack=1
- The third step : host
172.16.16.128:2826Host computer212.58.226.142:80send out [ACK] Seq=1,Ack=1
TCP window
Win=8192
The other parameters
- MSS(Maximum Segment Size), Maximum segment size .
- WS(Windows Scaling), Used to control the maximum TCP Receive window size .
TCP Why can't a second handshake establish a connection
- The server needs to confirm that the server can receive packets from the client
- The client needs to confirm that the client can receive packets from the server
- The client needs to confirm that the server can receive packets from the client
- The server needs to confirm that the client can receive packets from the server
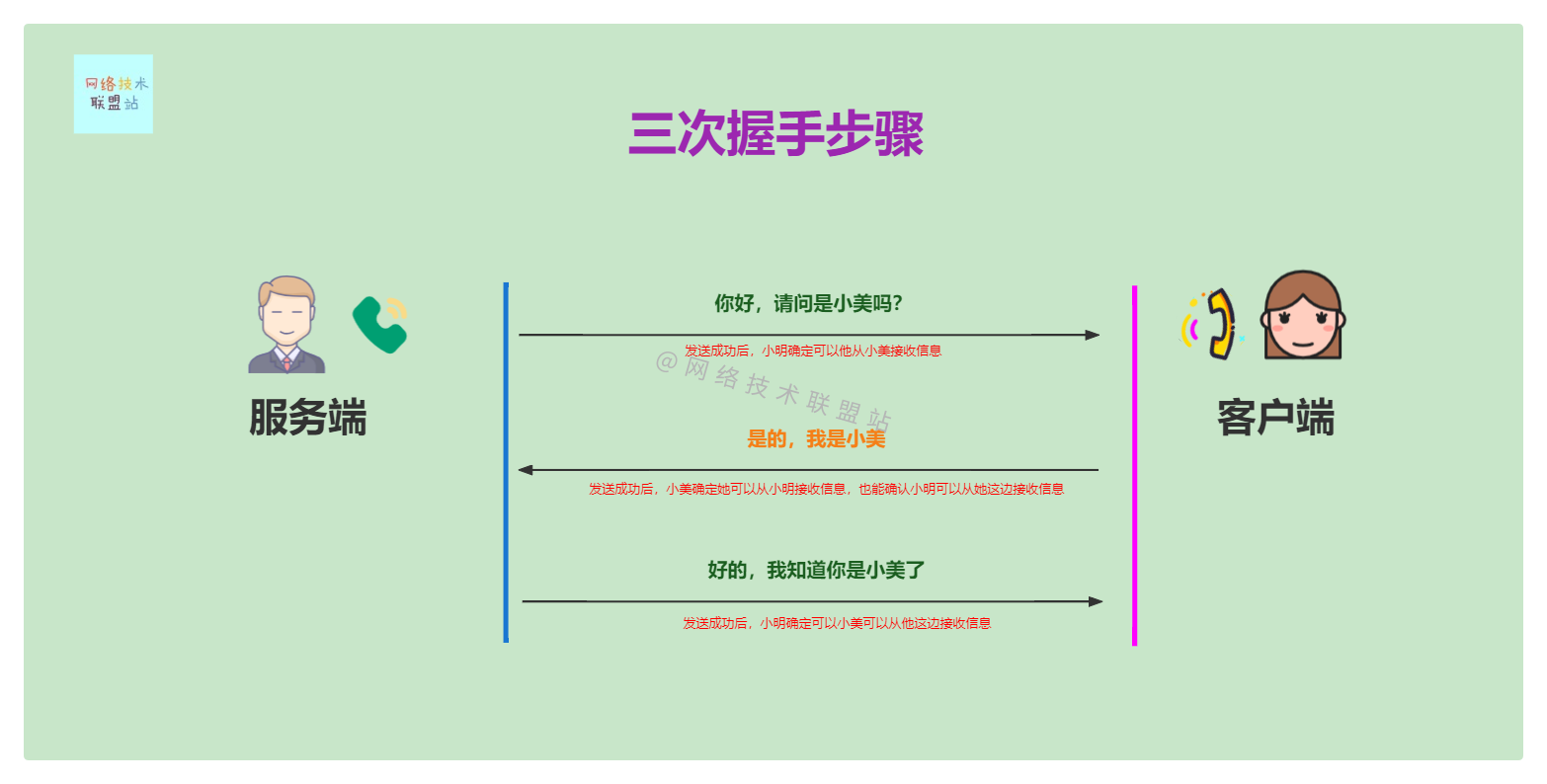
- Xiaoming asked :“ Hello , Excuse me, Shi Xiaomei ?”: After sending successfully , Xiaoming is sure that he can receive information from Xiaomei , The first condition is verified 【The server needs to confirm that the server can receive packets from the client】
- Xiaomeihui :“ Yes , I'm Xiaomei ”: After sending successfully , Xiaomei is sure that she can receive information from Xiaoming , It can also confirm that Xiao Ming can receive information from her , Verified the second 、 The third condition 【The client needs to confirm that the client can receive packets from the server】【The client needs to confirm that the server can receive packets from the client】
- Xiaoming returns :“ well , I know you are Xiaomei ”: After sending successfully , Xiaoming is sure that Xiaomei can receive information from him , Four conditions are verified 【The server needs to confirm that the client can receive packets from the server】
summary
- What is? TCP?
- TCP Three handshakes
- Three handshakes in life
- Three professional handshakes
- TCP Analysis of three handshakes
- TCP window
- The other parameters
- TCP Why can't a second handshake establish a connection
- summary
边栏推荐
- OpenCV经典100题
- Single source shortest path exercise (I)
- [groovy] XML serialization (use markupbuilder to generate XML data | set XML tag content | set XML tag attributes)
- Pointer pointer array, array pointer
- Global and Chinese market of water heater expansion tank 2022-2028: Research Report on technology, participants, trends, market size and share
- STM32 configuration after chip replacement and possible errors
- Key structure of ffmpeg -- AVCodecContext
- 电机的简介
- Classic CTF topic about FTP protocol
- LeetCode 1189. Maximum number of "balloons"
猜你喜欢
Data analysis thinking analysis methods and business knowledge -- analysis methods (II)
免费的聊天机器人API
建立时间和保持时间的模型分析
Start from the bottom structure and learn the introduction of fpga---fifo IP core and its key parameters
Search (DFS and BFS)
Spark AQE
![Atcoder beginer contest 258 [competition record]](/img/e4/1d34410f79851a7a81dd8f4a0b54bf.gif)
Atcoder beginer contest 258 [competition record]
FPGA内部硬件结构与代码的关系
![[groovy] compile time metaprogramming (compile time method injection | method injection using buildfromspec, buildfromstring, buildfromcode)](/img/e4/a41fe26efe389351780b322917d721.jpg)
[groovy] compile time metaprogramming (compile time method injection | method injection using buildfromspec, buildfromstring, buildfromcode)
![[groovy] compile time meta programming (compile time method interception | method interception in myasttransformation visit method)](/img/e4/a41fe26efe389351780b322917d721.jpg)
[groovy] compile time meta programming (compile time method interception | method interception in myasttransformation visit method)
随机推荐
LeetCode 1189. Maximum number of "balloons"
Spark AQE
Single source shortest path exercise (I)
Yolov5、Pycharm、Anaconda环境安装
Multithreading and high concurrency (8) -- summarize AQS shared lock from countdownlatch (punch in for the third anniversary)
Notepad + + regular expression replace String
[groovy] JSON string deserialization (use jsonslurper to deserialize JSON strings | construct related classes according to the map set)
LeetCode 6004. Get operands of 0
devkit入门
Spark AQE
[groovy] compile time metaprogramming (compile time method interception | find the method to be intercepted in the myasttransformation visit method)
Go learning --- read INI file
MySQL storage engine
Uniapp development, packaged as H5 and deployed to the server
anconda下载+添加清华+tensorflow 安装+No module named ‘tensorflow‘+KernelRestarter: restart failed,内核重启失败
数据分析思维分析方法和业务知识——分析方法(二)
curlpost-php
小程序技术优势与产业互联网相结合的分析
Start from the bottom structure and learn the introduction of fpga---fifo IP core and its key parameters
OpenCV经典100题