当前位置:网站首页>Alpha Beta Pruning in Adversarial Search
Alpha Beta Pruning in Adversarial Search
2022-07-02 07:23:00 【Drizzle】
Alpha Beta Pruning in Adversarial Search
Minimax Implementation
def max-value(state):
initialize v = -∞
for each successor of state:
v = max(v, min-value(successor))
return v
def min-value(state):
initialize v = +∞
for each successor of state:
v = min(v, max-value(successor))
return v
V ( s ) = m a x ( V ( s ′ ) ) s ′ ∈ s u c c e s s o r ( s ) V(s) = max(V(s')) s' \in successor(s) V(s)=max(V(s′))s′∈successor(s)
V ( s ′ ) = m i n ( V ( s ) ) s ∈ s u c c e s s o r ( s ′ ) V(s') = min(V(s)) s \in successor(s') V(s′)=min(V(s))s∈successor(s′)
Alpha Beta Pruning
General configuration (MIN version)
We’re computing the MIN-VALUE at some node n
We’re looping over n’s children
n’s estimate of the childrens’ min is dropping
Who cares about n’s value? MAX
Let α \alpha α be the best value that MAX can get at any choice point along the current path from the root
If n becomes worse than α \alpha α, MAX will avoid it, so we can stop considering n’s other children (it’s already bad enough that it won’t be played)
MAX version is symmetric
Examples

To start with, we know nothing about the bounds, so we set α = − ∞ , β = ∞ \alpha = - \infty, \beta = \infty α=−∞,β=∞.
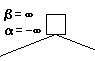
Then we passing along the bounds to the child, child’s child…
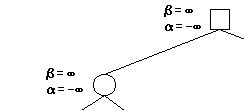
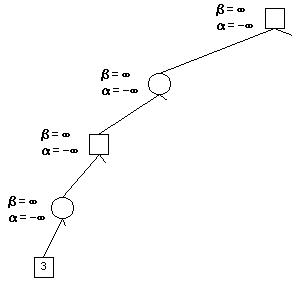
Now we reach at the level: depth of 4. We run our evaluation functions here.
An evaluation function is like:
Ideal function: returns the actual minimax value of the position
In practice: typically weighted linear sum of features: E v a l ( s ) = w 1 f 1 ( s ) + ⋅ ⋅ ⋅ + w n f n ( s ) Eval(s) = w_1f_1(s) + \cdot\cdot\cdot + w_nf_n(s) Eval(s)=w1f1(s)+⋅⋅⋅+wnfn(s).
We get value 3, since this is a min node, we now know the minmax value must be less than or equal to 3, thus, we set β = 3 \beta = 3 β=3.
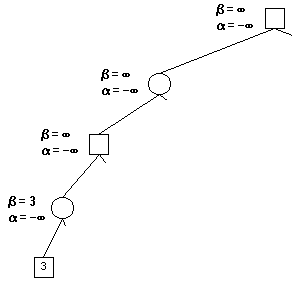
Next child in depth 4 is value 17, while 17 > 3, we ignore this child.
All children handled, we return to depth 3. we have β = 3 \beta = 3 β=3 here, so we can set α = 3 \alpha = 3 α=3 at the depth 2 node.

We pass along the bounds of depth2 to next child of depth3.
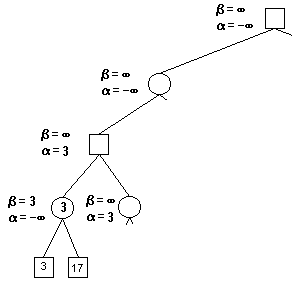

At this moment, we get α = 3 a n d β = 2 , α > β \alpha = 3 \space and \space \beta = 2, \alpha > \beta α=3 and β=2,α>β.
If these values are to change, children values would be greater than 3 and less than 2, which is impossible. We can prune any children and return.
We do these steps recursively, we will reach this:

Some pictures and ideas comes from h t t p s : / / w w w . c s . u c l a . e d u / https://www.cs.ucla.edu/ https://www.cs.ucla.edu/.
Two Quiz
notice: I do not have answers.
边栏推荐
- MapReduce与YARN原理解析
- ORACLE EBS中消息队列fnd_msg_pub、fnd_message在PL/SQL中的应用
- Message queue fnd in Oracle EBS_ msg_ pub、fnd_ Application of message in pl/sql
- ORACLE EBS接口开发-json格式数据快捷生成
- [introduction to information retrieval] Chapter 1 Boolean retrieval
- Oracle EBS数据库监控-Zabbix+zabbix-agent2+orabbix
- view的绘制机制(三)
- MySQL组合索引加不加ID
- Analysis of MapReduce and yarn principles
- Oracle段顾问、怎么处理行链接行迁移、降低高水位
猜你喜欢
【Ranking】Pre-trained Language Model based Ranking in Baidu Search

腾讯机试题

Two table Association of pyspark in idea2020 (field names are the same)
使用Matlab实现:Jacobi、Gauss-Seidel迭代

MapReduce concepts and cases (Shang Silicon Valley Learning Notes)
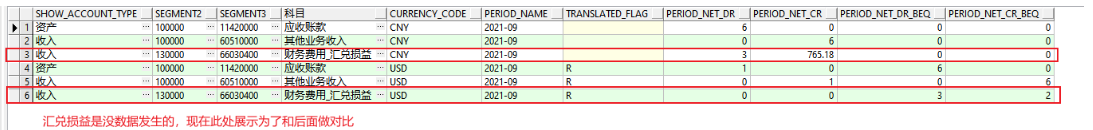
Changes in foreign currency bookkeeping and revaluation general ledger balance table (Part 2)
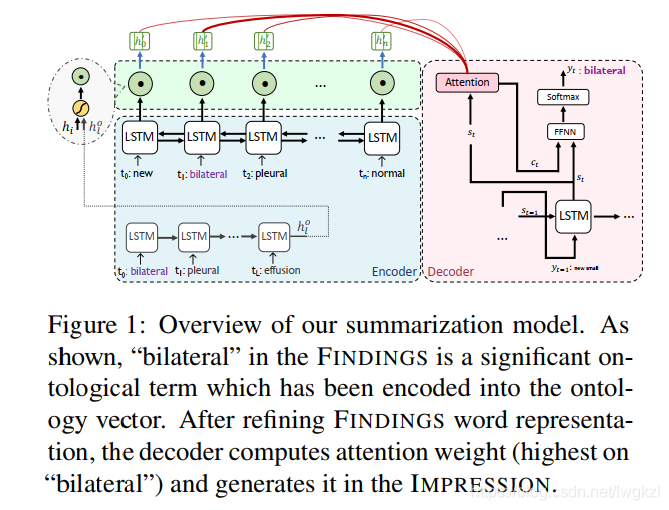
【MEDICAL】Attend to Medical Ontologies: Content Selection for Clinical Abstractive Summarization

Alpha Beta Pruning in Adversarial Search
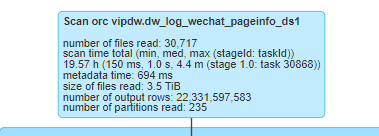
Spark SQL task performance optimization (basic)

Oracle EBS数据库监控-Zabbix+zabbix-agent2+orabbix
随机推荐
Get the uppercase initials of Chinese Pinyin in PHP
CRP implementation methodology
Oracle apex 21.2 installation and one click deployment
mapreduce概念和案例(尚硅谷学习笔记)
MySQL无order by的排序规则因素
Proteus -- RS-232 dual computer communication
Explanation of suffix of Oracle EBS standard table
Illustration of etcd access in kubernetes
ssm垃圾分类管理系统
Find in laravel8_ in_ Usage of set and upsert
华为机试题
实现接口 Interface Iterable<T>
SSM学生成绩信息管理系统
CONDA creates, replicates, and shares virtual environments
Typeerror in allenlp: object of type tensor is not JSON serializable error
One field in thinkphp5 corresponds to multiple fuzzy queries
ssm人事管理系统
矩阵的Jordan分解实例
【MEDICAL】Attend to Medical Ontologies: Content Selection for Clinical Abstractive Summarization
ORACLE EBS中消息队列fnd_msg_pub、fnd_message在PL/SQL中的应用