当前位置:网站首页>[reverse] repair IAT and close ASLR after shelling
[reverse] repair IAT and close ASLR after shelling
2022-07-06 17:22:00 【TiggerRun】
0x1 seek OEP
OEP Eight methods … It's not specific here …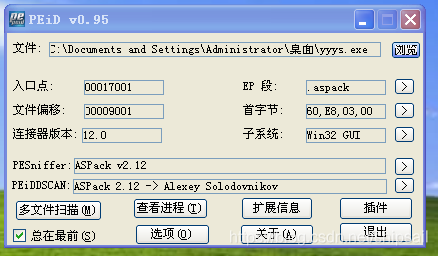
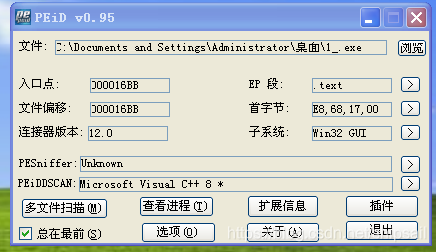
0x2 Shell program IAT
If the program cannot run normally after shelling (XP Environmental Science ), It may be because the import table is corrupted , Need manual repair .
adopt PC Study of file format , You can know the import table RVA In the optional header DataDirectory Array
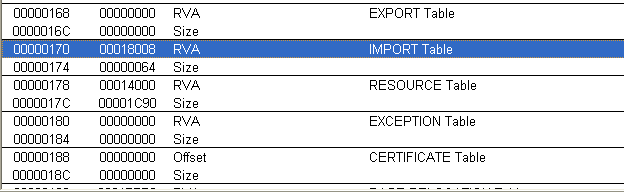
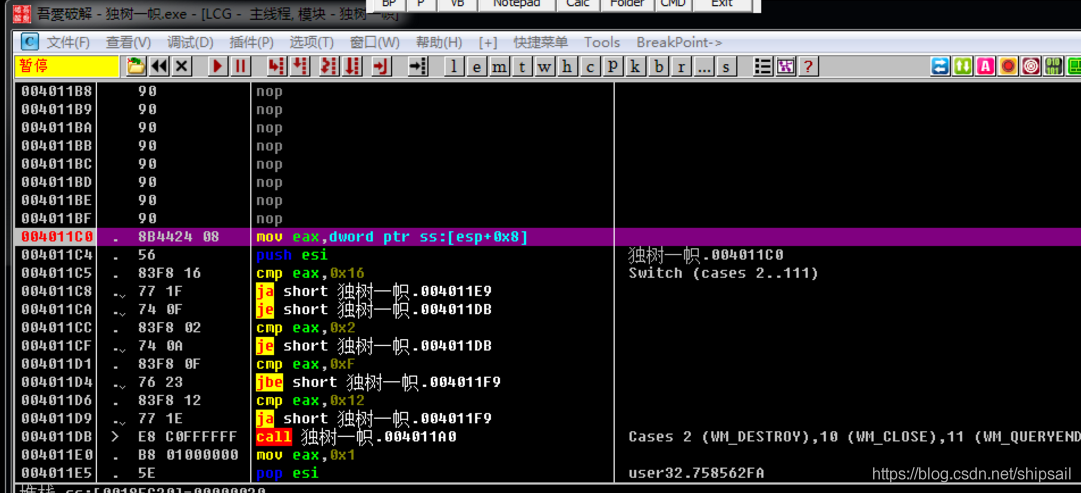
The picture shows the shelling program DESCRIPTOR The migration 18008, size 64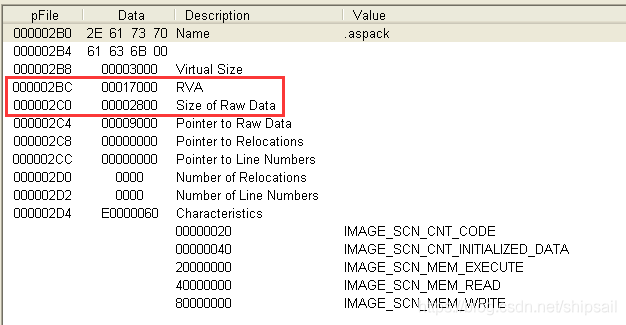
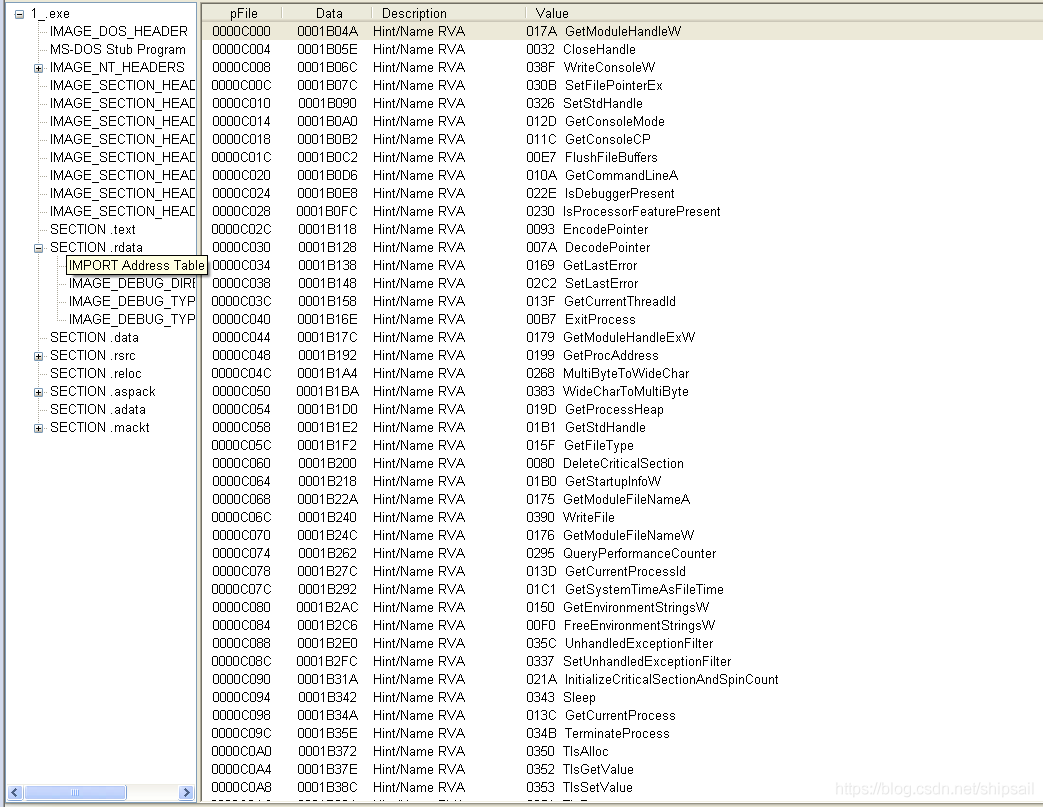
Locate according to the information in the section header IAT In the 6 A section .aspack in
Through the known virtual offset and physical offset of the node, we can calculate DESCRIPTOR Location in file .
offset = A008
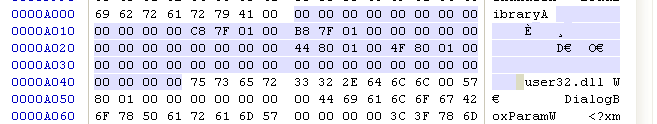
Find the location of the exported table , You can know that two DLL file , Can be calculated separately Name and IAT The migration
NAME(1) = 9FC8
NAME(2) = A044
IAT(1) = 9FB8
IAT(2) = A04F
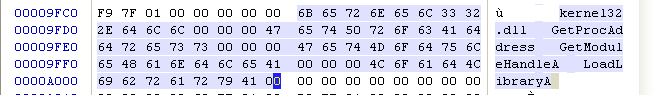

Of course, if it's right PC The head doesn't understand , Can use PE View To view the .
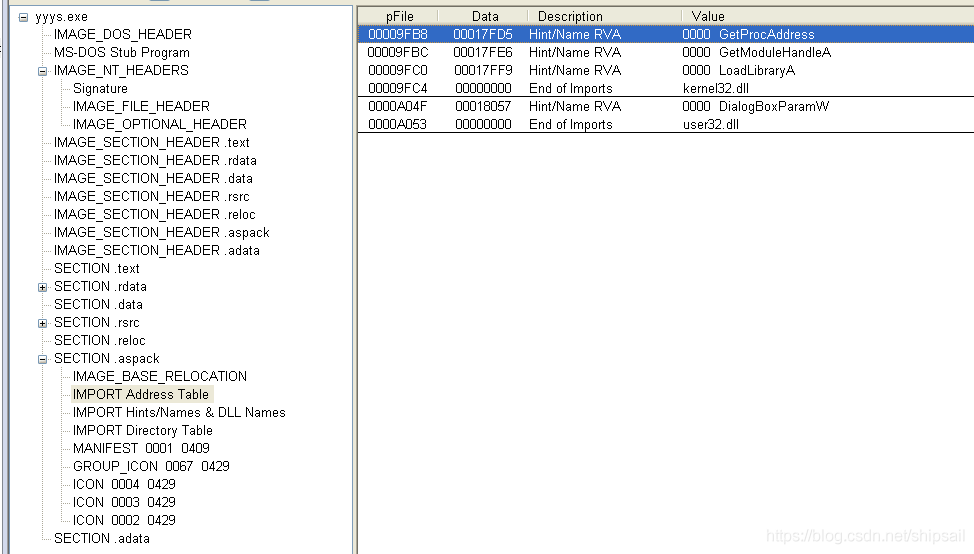
In this way, you can clearly see the functions imported by the shelled program at startup
0x3 The principle of runtime compression
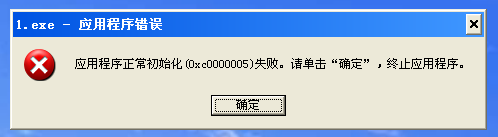
There may be questions , Why do you need to repair manually after shelling IAT.
IAT It is mainly used for DLL Relocation of files ,IAT Compared with 16 position dos Program You no longer need to include library files , Instead, map in the form of a table . If IAT inaccurate , Then the program cannot execute the functions of the related Library .
The compression shell compresses the section , hold IAT Change to shell itself IAT, In the last step of decompression, it will be restored IAT Make the program run normally , Therefore, shelling needs to be done IAT Repair of .
adopt OD Check the after run program IAT.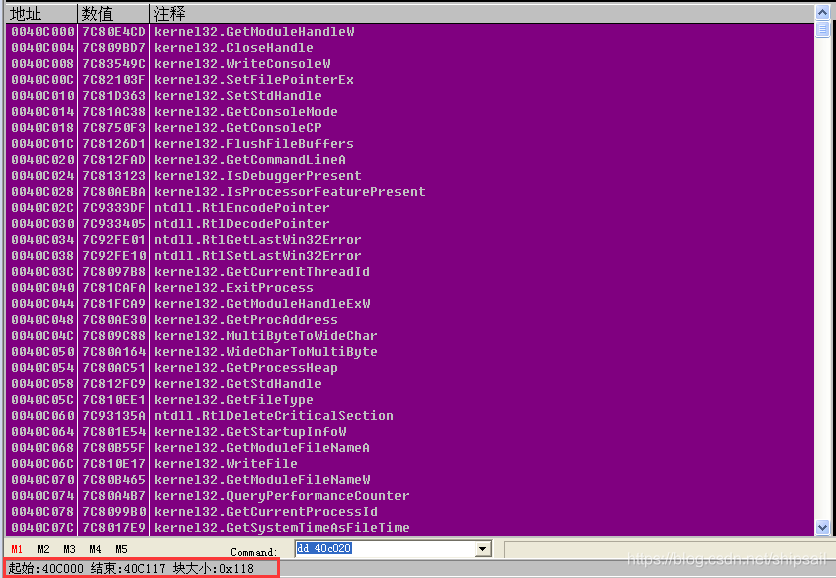
Compared with the shell program IAT, After running the shell program, the real IAT Much more , If we only shelled , Instead of IAT Repair of ( As shown in the figure below )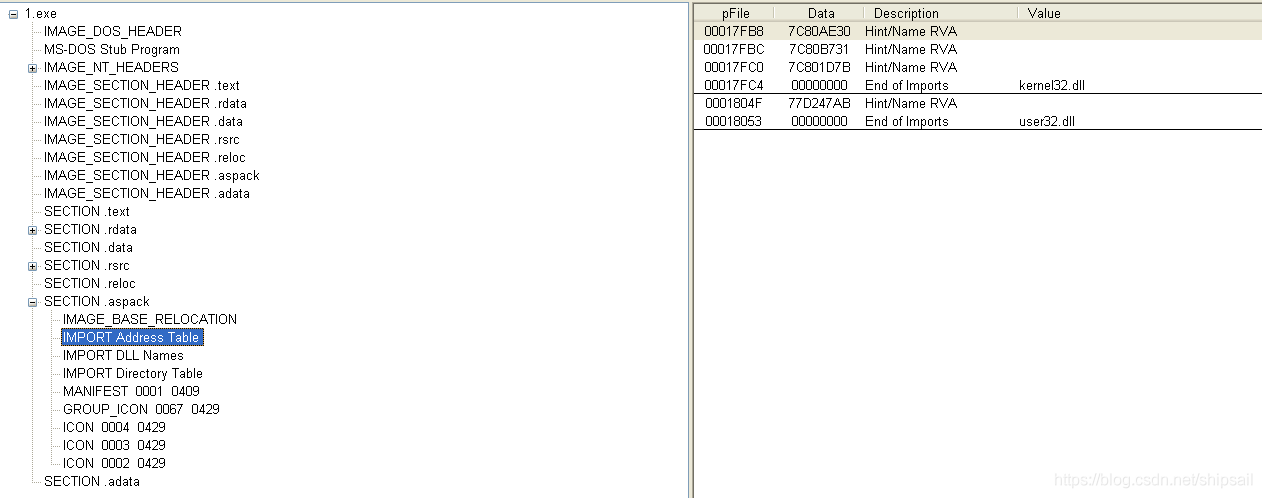
programmatic IAT Is damaged
0x4 IAT Repair
Use ImportREC Tools , Load in OEP The program process 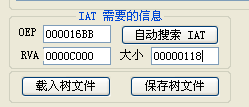
Correctly filled IAT Information 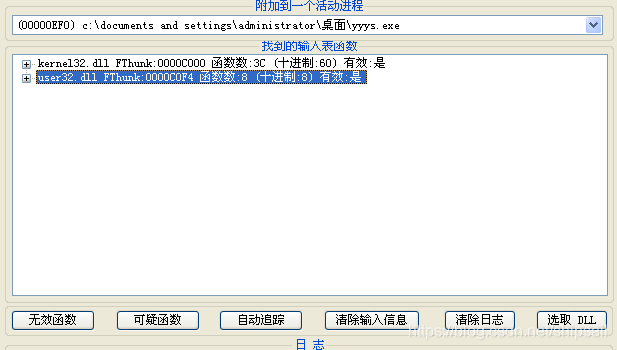
Get... In memory IAT Information , Then delete the invalid function and transfer it to the shelled program , The program can run normally .
0x5 Shelling program cannot be in WIN7 The above platforms are running
windows vista / win7 The system starts to use ASLR Technology prevents overflow attacks . Make each loader load to a random virtual address .ASLR Rely on the relocation table to locate , about EXE Procedure , Relocation is optional , By closing ASLR Can solve .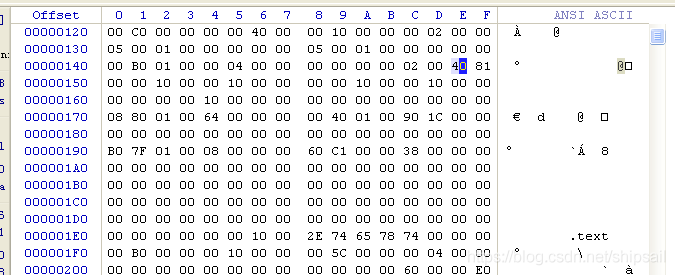
take 40 81 Change it to 00 81
边栏推荐
- À propos de l'utilisation intelligente du flux et de la carte
- 唯有學C不負眾望 TOP5 S1E8|S1E9:字符和字符串&&算術運算符
- Some feelings of brushing leetcode 300+ questions
- ByteDance overseas technical team won the championship again: HD video coding has won the first place in 17 items
- Flink源码解读(一):StreamGraph源码解读
- Coursera cannot play video
- Assembly language segment definition
- Only learning C can live up to expectations Top1 environment configuration
- 唯有学C不负众望 TOP5 S1E8|S1E9:字符和字符串&&算术运算符
- JVM之垃圾回收器上篇
猜你喜欢
随机推荐
[VNCTF 2022]ezmath wp
DOS 功能调用
High performance mysql (Third Edition) notes
数据仓库建模使用的模型以及分层介绍
Introduction to spring trick of ByteDance: senior students, senior students, senior students, and the author "brocade bag"
Use of mongodb in node
微信防撤回是怎么实现的?
[VNCTF 2022]ezmath wp
Activit零零碎碎要人命的坑
SQL tuning notes
控制转移指令
8086 内存
vscode
Notes on how the network is connected
Connect to LAN MySQL
Koa Middleware
SQL调优小记
Flink 解析(三):内存管理
JVM之垃圾回收器下篇
CentOS7上Redis安装