当前位置:网站首页>Chapter 8 - firewall, Chapter 9 - Intrusion Detection
Chapter 8 - firewall, Chapter 9 - Intrusion Detection
2022-06-12 07:34:00 【bugmaker.】
Chapter viii. A firewall
- Firewall concept
(1) Advanced network access control device
(2) Location : Between different network security domains
(3) function : The only way , Enforce access control policies
(4) Purpose : Prevent external network users from entering the internal network to access internal network resources by illegal means , Protect the internal network operating environment - Firewall function : Firewall can not be used as everything for network protection , Nor should it be regarded as a final solution to all security problems .
(1) Create a blocking point
(2) Implement security policies
(3) Record network activity
(4) Limit network exposure
(5) Security function implementation platform - Firewall limitations
(1) May be bypassed , for example , Dial out inside the firewall
(2) Can't guard against internal attacks
(3) Internal personnel cannot be prohibited from copying sensitive data to U On the disk .
(4) Can not prevent the administrator without security awareness from granting temporary network access rights to intruders
(5) Can not prevent the transmission of virus infected programs or files 、 Mail, etc.
(6) Do not scan files
(7) Performance bottleneck 、 Single point failure
(8) Can't guard against new network security problems . - Firewall technology
(1) Packet filtering ( The network layer ): Check the header information of each package , Decide to discard or release the packet according to a set of rules . Filter according to the access control list
(2) Circuit level gateway
(3) Application proxy firewall : Completely block network traffic , receive 、 Analyze service requests , If it is allowed, the proxy user can obtain network information , There is no direct communication between internal and external networks ; Develop special agents for each application service . The main function : Acting as a firewall ; save IP expenses ; Improve access speed .
(4) State monitoring packet filtering firewall : Adopt connection based condition monitoring mechanism ( While packet filtering , Check the correlation between packets , Treat all packets belonging to the same connection as a whole data flow , See the whole process from the initiation to the end of each connection , Form the connection status table . The check includes the link layer 、 The network layer 、 Transport layer 、 Various information of the application layer , Combine the rule table and the status table to decide whether to allow the package to pass .); Dynamic connection status table ; Support multiple protocols and applications , It can easily realize application and service expansion .
The main functions of proxy server :
(1) Acting as a firewall
(2) save IP expenses
(3) Improve access speed - Firewall architecture
(1) Shielding router structure 、
(2) Dual host Architecture
(3) Shield host Architecture
(4) Shield subnet Architecture - limitations :
(1) May be bypassed
(2) Can't guard against internal attacks
(3) It can't prevent the security conscious administrator from granting temporary network access to some intruders
(4) Can not prevent the transmission of virus infected programs or files 、 Mail, etc.
(5) Performance bottleneck 、 Single point failure
(6) Can't guard against new network security problems .
Chapter nine Intrusion detection
- IDS Reason for introduction of
(1)IDS It is the second line of defense behind the firewall ;
(2) Firewall has many shortcomings , If it can be broken , Weak protection against certain attacks , Only illegal connection requests can be rejected , But the invaders' attacks are still unknown ;
(3) Invasion is easy
(4) Prevention is ideal , But testing is necessary . - Intrusion detection : Collect and analyze information from network or system key points , Find out whether there is any behavior violating the security policy and any sign of being attacked ; Monitor the operation status of the system , Various attack attempts have been detected 、 The act or result of an attack , To ensure the confidentiality of system resources 、 Integrity and availability .
- IDS The basic structure
Three functional units :
(1) information gathering : The source is the log file of the system or network 、 The network traffic 、 Abnormal changes in system directories and files 、 Abnormal behavior in program execution
(2) Information analysis : Including pattern matching 、 Statistical analysis and integrity analysis ( For post analysis ). Pattern matching refers to comparing the collected information with the known database of network intrusion and system misuse patterns , So as to find the behavior that violates the security policy ; Statistical analysis refers to the statistics of some measurement attributes of system objects in normal use , Then it is used to communicate with the network 、 Compare system behavior , When any observed value is outside the normal range , It is thought that an invasion has occurred . Integrity analysis focuses on whether a file or object has been changed , After discovering the changed 、 This is especially useful for applications where Trojans are installed
(3) The result processing - Classification of intrusion detection : According to the analysis method, it is divided into anomaly detection model and misuse detection model ; According to the data source, it is divided into host based 、 Network based and hybrid
- Response strategy : Pop up window alarm 、E-mail notice 、 Cut off the TCP Connect 、 Execute custom program 、 Interact with other security products
- How to respond : Passive response 、 Mild active response 、 Strict and proactive response
- The development direction of intrusion detection :
(1) More effectively integrate various intrusion detection data sources , Including data collected from different systems and different sensors , Improve alarm accuracy ;
(2) Combined with manual analysis in event diagnosis , Improve judgment accuracy ;
(3) Improve the ability to detect malicious code , Include email attack ,Java,ActiveX etc. ;
(4) Adopt certain methods and strategies to enhance the interoperability and data consistency of heterogeneous systems ;
(5) Develop reliable test and evaluation standards ;
(6) Provide scientific vulnerability classification methods , Especially from the point of view of attacking object rather than attacking subject ;
(7) Provide for more advanced attacks, such as distributed attacks 、 Detection methods for denial of service attacks ;
边栏推荐
- Federated reconnaissance: efficient, distributed, class incremental learning paper reading + code analysis
- Detailed explanation of coordinate tracking of TF2 operation in ROS (example + code)
- Interview computer network - transport layer
- @DateTimeFormat @JsonFormat 的区别
- Summary of machine learning + pattern recognition learning (I) -- k-nearest neighbor method
- [tutorial] deployment process of yolov5 based on tensorflow Lite
- Unity用Shader实现UGU i图片边缘选中高亮
- Summary of machine learning + pattern recognition learning (II) -- perceptron and neural network
- 2022 G3 boiler water treatment recurrent training question bank and answers
- RT thread studio learning (x) mpu9250
猜你喜欢

Embedded gd32 code read protection

2022 electrician (elementary) examination question bank and simulation examination

Voice assistant - Introduction and interaction process

VS 2019 MFC 通过ACE引擎连接并访问Access数据库类库封装

Summary of semantic segmentation learning (II) -- UNET network

Summary of software testing tools in 2021 - unit testing tools

Golang 快速生成数据库表的 model 和 queryset
Voice assistant - Measurement Indicators

Summary of machine learning + pattern recognition learning (I) -- k-nearest neighbor method
Detailed explanation of coordinate tracking of TF2 operation in ROS (example + code)
随机推荐
Thoroughly understand the "rotation matrix / Euler angle / quaternion" and let you experience the beauty of three-dimensional rotation
Pyhon的第六天
Detailed explanation of 14 registers in 8086CPU
Vs 2019 MFC connects and accesses access database class library encapsulation through ace engine
Federated meta learning with fast convergence and effective communication
面试计算机网络-传输层
AcWing——4268. 性感素
Personalized federated learning with Moreau envelopes
Detailed explanation of 8086/8088 system bus (sequence analysis + bus related knowledge)
Esp8266 firmware upgrade method (esp8266-01s module)
Summary of machine learning + pattern recognition learning (VI) -- feature selection and feature extraction
8086/8088 instruction execution pipeline disconnection reason
Missing getting in online continuous learning with neuron calibration thesis analysis + code reading
2022 G3 boiler water treatment recurrent training question bank and answers
Arrangement of statistical learning knowledge points gradient descent, least square method, Newton method
How to stop MySQL service under Linux
In depth learning - overview of image classification related models
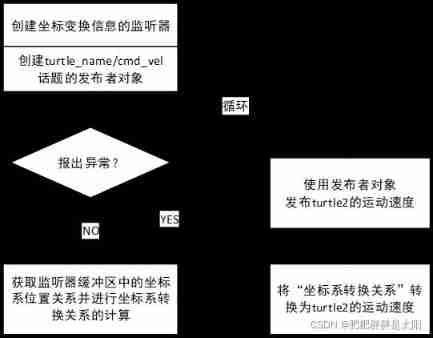
Why must coordinate transformations consist of publishers / subscribers of coordinate transformation information?
2022年G3锅炉水处理复训题库及答案
Day 5 of pyhon