当前位置:网站首页>What are the technical differences in source code anti disclosure
What are the technical differences in source code anti disclosure
2022-07-07 12:01:00 【cnsinda_ sdc】
With the popularization and development of computer and network technology , Great changes have taken place in the office mode and business flow of companies and enterprises .
The world has 60% People are mainly engaged in the generation of information 、 Service work of processing and storage and related technologies . Creation of a large amount of data information 、 Storage 、 Revolutionary changes have taken place in the way of transmission and sharing , Mainly in the following three aspects :
1、 Market competition and technological innovation by means of informatization and traditional mechanized production ;
2、 Replace paper media archives with information-based means to preserve enterprise business information , It includes the core secrets related to the core competitiveness of the enterprise , The accumulation of business information forms the core competence of the enterprise , Help enterprises stay ahead , The leakage of core competence information will inevitably lead to the decline of enterprises ;
3、 Informatization means fully permeate the whole process of enterprise management .
This involves a problem : How to protect confidential company information , Security of electronic documents ! Most enterprises just take a lot of measures to prevent hacker attacks , The problems that have come out one after another make the enterprise bosses more headache , That's it :
1、 How to prevent employees from copying and taking away confidential information without authorization ?
2、 How to prevent design drawings 、 Confidential information such as program source code is disclosed to competitors ?
3、 How to enable employees to efficiently share enterprise knowledge while protecting the security of confidential documents ?
Survey results show that ,68% Every year 6 Sensitive data loss events ;
20% Every year 22 The above electronic documents have been leaked ;
75% The leak of the secret comes from the intentional act of internal employees ; The average loss caused by each disclosure of electronic documents is 50 Thousands of dollars .
In the past cases of enterprise leakage , Due to the difficulty of obtaining evidence , And the limitations of existing laws , The losses of enterprises are often huge and irreparable . In the face of deliberate disclosure by insiders , Firewall in enterprise network 、 Intrusion detection and all kinds of file encryption and other technical means can not play a real preventive role . Protect confidential electronic documents by seeking more perfect technical means , It is the inevitable choice of the enterprise .
For these needs, how should we choose the appropriate software ?
One : Common encryption mode in the market
Transparent encryption : The design idea of transparent encryption is based on windows File system ( Filter ) drive (IFS) technology , Working in windows Kernel layer . When we install computer hardware , Always install its driver , Such as a printer 、U Disk drive . File system driver is a virtual driver that treats files as a device . When an application operates on a suffix file , The file driver will monitor the operation of the program , And change its operation mode , So as to achieve the effect of encryption .
Environment encryption : The design idea of environment encryption is that the client is in secret related occasions , Start an encrypted sandbox , A sandbox is a container , Classified software , Throw the file into the container for encryption . And this container is transparent , Users don't feel its existence . Adopt the most advanced disk filter drive , File filter driver , Network filter driver and other kernel level in-depth encryption anti disclosure technologies , Each module only makes the one they are best at , So it's very stable . People who don't enter sandbox mode and those who enter sandbox mode are divided into two spaces , Cut off from each other , So don't worry about leaks .
Two : The stability of the product
No stability, no application , After reading a wide range of encryption software of domestic brands , Many people are attracted by the peripheral functions of encryption software and ignore the functionality of encryption software itself . The first thing to ask is BS Architecture 、 There is no desktop control 、 Can you push it remotely 、 Can it be compatible LINUX、MAC And so on . I think these fancy features can really add to the application , But ignore the core stability of encryption software , Talking about functionality is the misunderstanding of encryption software selection .
No access to encryption software , Experience in selecting management software , It's easy to ignore the stability of encryption software . I think software development should be more mature , Can guarantee stability , Encryption software is different from management software , It involves WINDOWS Bottom drive , It can realize encryption protection , It is very difficult to ensure the stability of the system in development . Most of the management software is relatively stable , But there are few products that can really achieve stability of encryption software .
Encryption software is not stable, several performance
1: Destroy file
Destroying drawings and documents is the first enemy of encryption software , It often happens in transparent encryption software . Transparent encryption software is running , Accidentally damaged the file , So that the file can't be typed , This is the last thing customers want to happen , But it happened . In the early development stage of encryption software industry, many software have this problem , It's now , It is also common for the so-called famous encryption software to destroy files . Transparent encryption software will never destroy files , That's almost impossible . Just destroy the drawings under some environmental conditions , What's the probability . But once something like file destruction happens , It is a headache for enterprises , Maybe that document is the result of a department or a project team spending a week or more , This problem will not appear in environmental encryption .
This problem is very important to the design industry , Companies that need drawings and documents , It needs to be carefully considered when selecting models . If you don't choose a good product , It is not only not helpful for future use , And create a lot of problems , Affect the normal work of employees .
2: Frequent conflicts with the operating system
Blue screen crash and other phenomena , This is also a typical problem in the use of the company . This frequent system conflict drives users crazy , It will directly lead customers to give up the idea of using encryption software . If the encryption kernel is developed by ourselves , The solution is relatively simple , Just keep mending BUG The process of , The more customers of software applications ,BUG The more solved , The system gradually stabilized . If a few simple of encryption software BUG It's too late to solve , We should suspect that it is not independently developed , Some manufacturers buy other people's cores or OEM Other people's things , It doesn't have the ability to control the encryption kernel at all , Some small problems , It's very hard to solve .
The customer used encryption software and crashed 、 A series of problems such as slow speed , Is it your own software problem ? not always ! On the one hand, some employees are emotionally disgusted with encryption software , In addition, the computer maintenance of small and medium-sized enterprises is not standardized , A little problem without analysis is attributed to encryption software . Therefore, our implementers spend a lot of time investigating the source of the conflict , Or prove your innocence , Or find out the cause of the problem for troubleshooting .
How can we find a stable encryption software , This is really hard , First, test and try it out by yourself , The test is simply to use the function of the software , But it cannot reflect the overall stability of the software . If conditions permit , It's best to install it on your computer and use it normally for a period of time , This can test the basic stability of an encryption software . If you can't continue your trial , Is it necessary to sell such products . But to prove whether a product is really stable , It still depends on whether it has mass applications , There are at least hundreds of customers , There are more than thousands of sites , To test that a product is really stable .
3、 ... and : Product compatibility
The stability and compatibility of products are inseparable , For example, the stability under the system , In fact, it is compatible with all kinds of software , Operating system compatibility . We classify it as the basic stability of software , It's actually compatibility . What we're talking about here is more about compatibility with other management software or hardware applications . This is very important , A very stable encryption software , If you can't integrate well with other systems , The project may end up stuck .
1: ERP、PDM、OA And other management software .
Transparent encryption software : To ensure that it can be used in an encrypted environment ,ERP The exported file is automatically encrypted ,ERP Can read encrypted files , And ensure the normal operation of the system , That's all right. .PDM The integration of is relatively complex , There are also many customer requirements , Some customers require full ciphertext , Encrypt in and out , And can preview with built-in browser normally 、 By PDM The system reads normally . And some customers ask to enter PDM when , Automatic file decryption ; Out PDM The file is automatically encrypted when the system is running .CS Architecturally PDM It's relatively easy to integrate ,BS Architecturally PDM It's much harder , There may be more problems . Follow BS framework PDM equally ,OA There are many problems , especially WebOFFICE The problem of , At present, there are still few products that can follow WEBOFFICE Good integration . Due to the limitations of transparent encryption , Therefore, the integration of management software is worse than environmental encryption .
Environment encryption software : The integration of environmental encryption software and management software is better , Because the encryption mode is different , The integration with management software will be more easily recognized by customers , Environment encryption can be seamlessly integrated with management software .ERP、PDM Include OA And other management software , Whether it's CS Architecture is still BS The architecture is compatible . The only thing that can be done is the client PC Or credible PC To access the management software , It does not affect the normal browsing of the built-in browser , You can choose whether to encrypt the outgoing file . In terms of compatible management software , Environment encryption software is better .
2: Technical drawings 、 Documents and other encryption protection
Since you want to encrypt the drawing , It must involve design customers and machining center customers in manufacturing industry , At present, the most common customer is CNC design 、 Design Institute 、 research institute 、 Advertising companies, etc . The cumbersome thing about drawing design is that NC needs to import drawings into relevant equipment , Then it is processed by the equipment .
Transparent encryption software : A better solution is to send encrypted files to the machine through software , Automatic decryption during transportation . Due to the frequent integration with machining centers , The software of the machining center is varied , So the workload is still relatively large , And the settings can be customized by users , If this cannot be customized , That's a headache , Once you meet a similar customer , It will be painful .
Environment encryption software : The solution of environment encryption is to send the drawing to the machining center , Because environment encryption is not for process control , Therefore, there will be no problem of being unable to customize due to the variety of software , When the directed decryption of the drawing is sent to the machining center , You can also do monitoring backup , Because the status of plaintext is required for sending to the monitoring center , In the process of sending, for more security , You can make a monitoring backup and audit these documents sent to the machining center in the future , In case of random sending of other key data .
3: Encryption protection for source code
Encrypt source code , This kind is usually software development companies , Hardware product R & D manufacturer , Website development ,APP Development, etc . The customer needs to automatically decrypt when writing the chip , Most electronic enterprises need to burn and debug embedded boards or other hardware peripherals . The customer requests to encrypt the program source code . And automatically decrypt when writing to the chip . This requires the encryption software to support source code encryption , It also requires that the encryption software can automatically decrypt the output ( Similar to drawing Machining Center ).
Transparent encryption software : In the process of source code encryption , Many processes call the source code , Like a machining center , Need custom tools , Some encryption software needs to use the task manager to see what process has called , Write it down by yourself , Then do integration , This is very backward , And some software can't be customized . This will encounter the same problem as the machining center , Once there is such a customer , Or the needs in this regard , It's bound to become a headache . There are also some website development customers , Local debugging is required , After encryption, local debugging cannot see the content .
Environment encryption software : In the development process , Environment encryption can be based on its own design advantages , It is easy to protect the source code . When the user is debugging , Trusted settings can be made for hardware , The source code is sent to a specific device in clear text , Enable users to debug and call normally . If users are not confident about the security of decentralized information , You can set up a white list , Document recording hardware debugging , For later review , Go back to the source .
These are some key points in the selection of encryption software products , These points are also the criteria for judging the performance of an encryption software . You can refer to the above points , The ability of each software to measure , Help enterprises find a suitable encryption software .
At the end, I will also recommend a software for your reference .
Use appropriate encryption software , You need to judge according to your needs . From easy to use , Multi terminal control , Do not affect work efficiency SDC Sandbox is very suitable for R & D companies . Use the principle of sandbox to protect the normal operation of source code in the environment , And will not be leaked out of the environment . This kind of software is currently available in our company , It still works , It does not affect the development and use of employees . You can see SDC Sandbox look .
边栏推荐
- What is high cohesion and low coupling?
- [filter tracking] comparison between EKF and UKF based on MATLAB extended Kalman filter [including Matlab source code 1933]
- Fleet tutorial 14 basic introduction to listtile (tutorial includes source code)
- 超标量处理器设计 姚永斌 第8章 指令发射 摘录
- R Language Using Image of magick package Mosaic Function and Image La fonction flatten empile plusieurs images ensemble pour former des couches empilées sur chaque autre
- 《通信软件开发与应用》课程结业报告
- MATLAB实现Huffman编码译码含GUI界面
- Blog moved to Zhihu
- zero-shot, one-shot和few-shot
- Zhou Yajin, a top safety scholar of Zhejiang University, is a curiosity driven activist
猜你喜欢
Mise en œuvre du codage Huffman et du décodage avec interface graphique par MATLAB
Visual Studio 2019 (LocalDB)\MSSQLLocalDB SQL Server 2014 数据库版本为852无法打开,此服务器支持782版及更低版本
In my limited software testing experience, a full-time summary of automation testing experience
从工具升级为解决方案,有赞的新站位指向新价值
Problem: the string and characters are typed successively, and the results conflict
STM32F1与STM32CubeIDE编程实例-MAX7219驱动8位7段数码管(基于SPI)
Hi3516全系统类型烧录教程
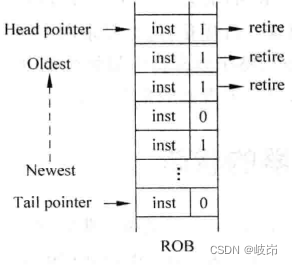
Superscalar processor design yaoyongbin Chapter 10 instruction submission excerpt
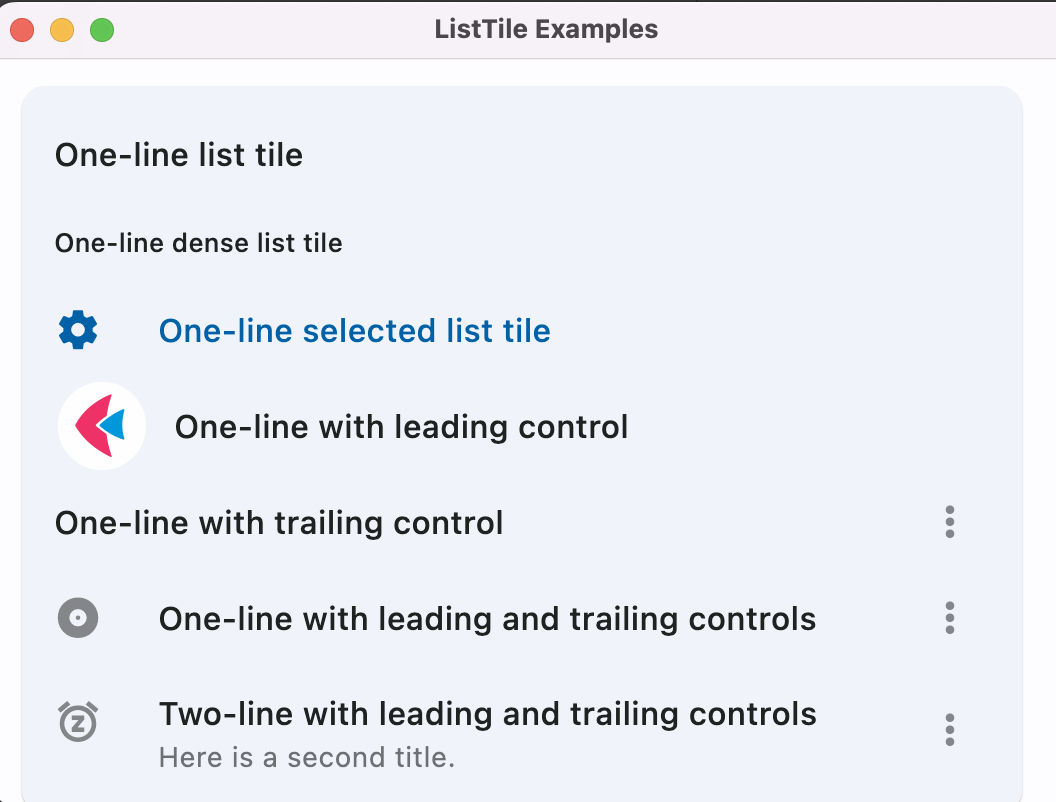
Fleet tutorial 14 basic introduction to listtile (tutorial includes source code)
SwiftUI 4 新功能之掌握 WeatherKit 和 Swift Charts
随机推荐
清华姚班程序员,网上征婚被骂?
Steps of redis installation and self startup configuration under CentOS system
【滤波跟踪】基于matlab扩展卡尔曼滤波EKF和无迹卡尔曼滤波UKF比较【含Matlab源码 1933期】
Poor math students who once dropped out of school won the fields award this year
Flet教程之 14 ListTile 基础入门(教程含源码)
In depth learning autumn recruitment interview questions collection (1)
Detailed explanation of debezium architecture of debezium synchronization
powershell cs-UTF-16LE编码上线
[filter tracking] strapdown inertial navigation simulation based on MATLAB [including Matlab source code 1935]
Use references
Swiftui tutorial how to realize automatic scrolling function in 2 seconds
Rationaldmis2022 array workpiece measurement
Visual Studio 2019 (LocalDB)\MSSQLLocalDB SQL Server 2014 数据库版本为852无法打开,此服务器支持782版及更低版本
Unity 贴图自动匹配材质工具 贴图自动添加到材质球工具 材质球匹配贴图工具 Substance Painter制作的贴图自动匹配材质球工具
Flet教程之 19 VerticalDivider 分隔符组件 基础入门(教程含源码)
人大金仓受邀参加《航天七〇六“我与航天电脑有约”全国合作伙伴大会》
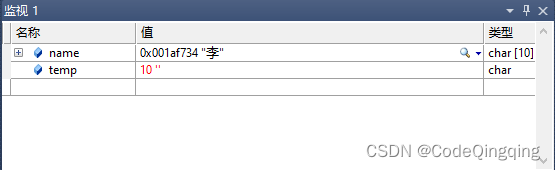
Problem: the string and characters are typed successively, and the results conflict
Ask about the version of flinkcdc2.2.0, which supports concurrency. Does this concurrency mean Multiple Parallelism? Now I find that mysqlcdc is full
111.网络安全渗透测试—[权限提升篇9]—[Windows 2008 R2内核溢出提权]
Basic introduction to the 16 tabs tab control in the fleet tutorial (the tutorial includes source code)