当前位置:网站首页>[network security interview question] - how to penetrate the test file directory through
[network security interview question] - how to penetrate the test file directory through
2022-07-06 02:43:00 【LexSaints】
4.6. Directory traversal
4.6.1. brief introduction
Directory traversal ( Also known as directory traversal /directory traversal/path traversal) By using ../ And so on directory control sequence or file absolute path to access any file and directory stored on the file system , Especially the application source code 、 The configuration file 、 Important system files, etc .
4.6.2. Attack load
4.6.2.1. URL Parameters
../..\..;/
4.6.2.2. Nginx Off by Slash
https://vuln.site.com/files../
4.6.2.3. UNC Bypass
\\localhost\c$\windows\win.ini
4.6.3. Filter around
Single replacement
...//
- URL code
16 position Unicode code
\u002e
Super long UTF-8 code
\%e0%40%ae
4.6.4. defense
In the process of file operation API front , User input should be filtered . Whitelist can be used under strong rules , Only alphanumeric characters are allowed .
If the rule allows more characters , It is best to use the current operating system path normalization function to normalize the path , To filter , Finally, make relevant calls .
4.6.5. Reference link
- Directory traversal by portswigger
- Path Traversal by OWASP
- path normalization
- Breaking Parser Logic: Take Your Path Normalization Off and Pop 0days Out defcon
Recommended reading
【 Resource Recommendation 】
Special system for penetration test
- kali-linux-e17-2019.1a-amd64.iso System image
- kali-linux-e17-2019.1a-amd64.iso System image _kalilinux Mirror image -Linux Document resources -CSDN download
- kali-linux-2018.4-amd64 operating system
- kali-linux-2018.4-amd64 operating system _amdkalilinux-Linux Document resources -CSDN download
- manjaro-xfce-17.1.7-stable-x86_64.iso System image
- manjaro-xfce-17.1.7-stable-x86_64.iso System image _manjaro Image download ,manjaro System download -Linux Document resources -CSDN download
- WiFi Special infiltration system nst-32-11992.x86_64.iso Operating system image
- nst-32-11992.x86_64.iso Operating system image .zip_ Explanation and actual combat of common password cracking tools -Linux Document resources -CSDN download
- Parrot-security-4.1_amd64.iso Operating system image
- Parrot-security-4.1_amd64.iso Operating system image _ParrotSecurity-Linux Document resources -CSDN download
- manjaro-xfce-17.1.7-stable-x86_64 operating system
- manjaro-xfce-17.1.7-stable-x86_64 operating system _manjaroxfce Installation tutorial -Linux Document resources -CSDN download
- cyborg-hawk-linux-v-1.1 operating system
- cyborg-hawk-linux-v-1.1 operating system _cyborghawk Virtual machine installation tutorial -Linux Document resources -CSDN download
Penetration test related tools
- Practical column of penetration test
- 【kali Commonly used tools 】 Online behavior monitoring tool
- Internet behavior tools _ Explanation and actual combat of common password cracking tools - Network security document resources -CSDN download
- 【kali Commonly used tools 】 Caught tools Charles Windows64 position Free version
- Caught tools CharlesWindows64 Bit free version _ Explanation and actual combat of common password cracking tools - Network monitoring document resources -CSDN download
- 【kali Commonly used tools 】 Graphic printing tool stamp.zip
- Graphic printing tool stamp.zip_intext:LexSaints- Manufacturing document resources -CSDN download
- 【kali Commonly used tools 】brutecrack Tools [WIFIPR Chinese version ] And wpa/wpa2 Dictionaries
- brutecrack Tools [WIFIPR Chinese version ] And wpa/wpa2 Dictionaries _wifipr course - Other document resources -CSDN download
- 【kali Commonly used tools 】EWSA 5.1.282- Bag breaking tools
- 【kali Commonly used tools 】EWSA5.1.282- Bag breaking tools _kali Bag running tool - Manage software document resources -CSDN download
- 【kali Commonly used tools 】Realtek 8812AU KALI Network card driver and installation tutorial
- 【kali Commonly used tools 】Realtek8812AUKALI Network card driver and installation tutorial _kalirtl8812au,kali install 8812au drive - Network device document resources -CSDN download
- 【kali Commonly used tools 】 Wireless signal search tool _kali to update
- 【kali Commonly used tools 】 Wireless signal search tool _kali to update _kali to update - Internet document resources -CSDN download
- 【kali Commonly used tools 】inssider Signal test software _kali Commonly used tools
- 【kali Commonly used tools 】inssider Signal test software _kali Commonly used tools - Network management software document resources -CSDN download
- 【kali Commonly used tools 】MAC Address modification tool Protect the terminal from exposure
- 【kali Commonly used tools 】MAC The address modification tool protects the terminal from exposure _mac Modifier -Linux Document resources -CSDN download
- 【kali Commonly used tools 】 Script management tools php and jsp page Receive command parameters Execute... On the server side
- Script management tools php and jsp The page receives command parameters and executes them on the server side _intext:LexSaints- Network security document resources -CSDN download
- Java Realize photos GPS location 【 Full script 】
- ReadPicExif.zip-Java Document resources -CSDN download
- Python Realize photos GPS location 【 Full script 】
- python Locate the exact location of the photo, complete code script _ How to locate the location through photos -Python Document resources -CSDN download
- The goddess forgot the photo album password python20 Line code open 【 Full script 】
- The goddess forgot the photo album password python20 Line code open .py_keepalive_timeout-Python Document resources -CSDN download
- python Modify the background color of the certificate 、 size 、 background 、 Cutout 【 Complete source code 】
- python Modify the background color of the certificate 、 size 、 background 、 Cutout 【 Complete source code 】_python Change the color of the certificate -Python Document resources -CSDN download
python actual combat
- 【python actual combat 】 Ex girlfriend wedding ,python Crack the wedding scene WIFI, Changed the name to
- 【python actual combat 】 Encrypted from my ex girlfriend “520 happy .pdf“, I use python After cracking , But found
- 【python actual combat 】 Last night, , I use python Help the little sister next door P ID Photo Selfie , And found that ...
- 【python actual combat 】 My girlfriend worked overtime in the middle of the night and took a selfie python Boyfriend uses 30 Line of code found the amazing secret
- 【python actual combat 】python you TM Too skinny —— Just so 30 One line of code can record every move of the keyboard
- 【python actual combat 】 I forgot the password of the goddess album , I only use Python Yes 20 Line code ~~~
【pygame Development practice development 30 example Complete source code 】
【pygame Game development column , Get the full source code + course 】
- Come and learn together pygame Well Game development 30 example ( Two )—— Tower defense game
- Come and learn together pygame Well Game development 30 example ( Four )—— Tetris games
- Practical column of penetration test
- Windows AD/Exchange Management column
- Linux High performance server architecture
- PowerShell Automation column
CSDN Official learning recommendation ↓ ↓ ↓
- CSDN Out of Python Full stack knowledge map , too strong , I recommend it to you !
边栏推荐
- 2345文件粉碎,文件强力删除工具无捆绑纯净提取版
- Microservice registration and discovery
- 米家、涂鸦、Hilink、智汀等生态哪家强?5大主流智能品牌分析
- 一位博士在华为的22年
- 力扣今日題-729. 我的日程安排錶 I
- Number conclusion LC skimming review - 1
- Accident index statistics
- 2.13 simulation summary
- Bigder: I felt good about the 34/100 interview, but I didn't receive the admission
- 微服务间通信
猜你喜欢
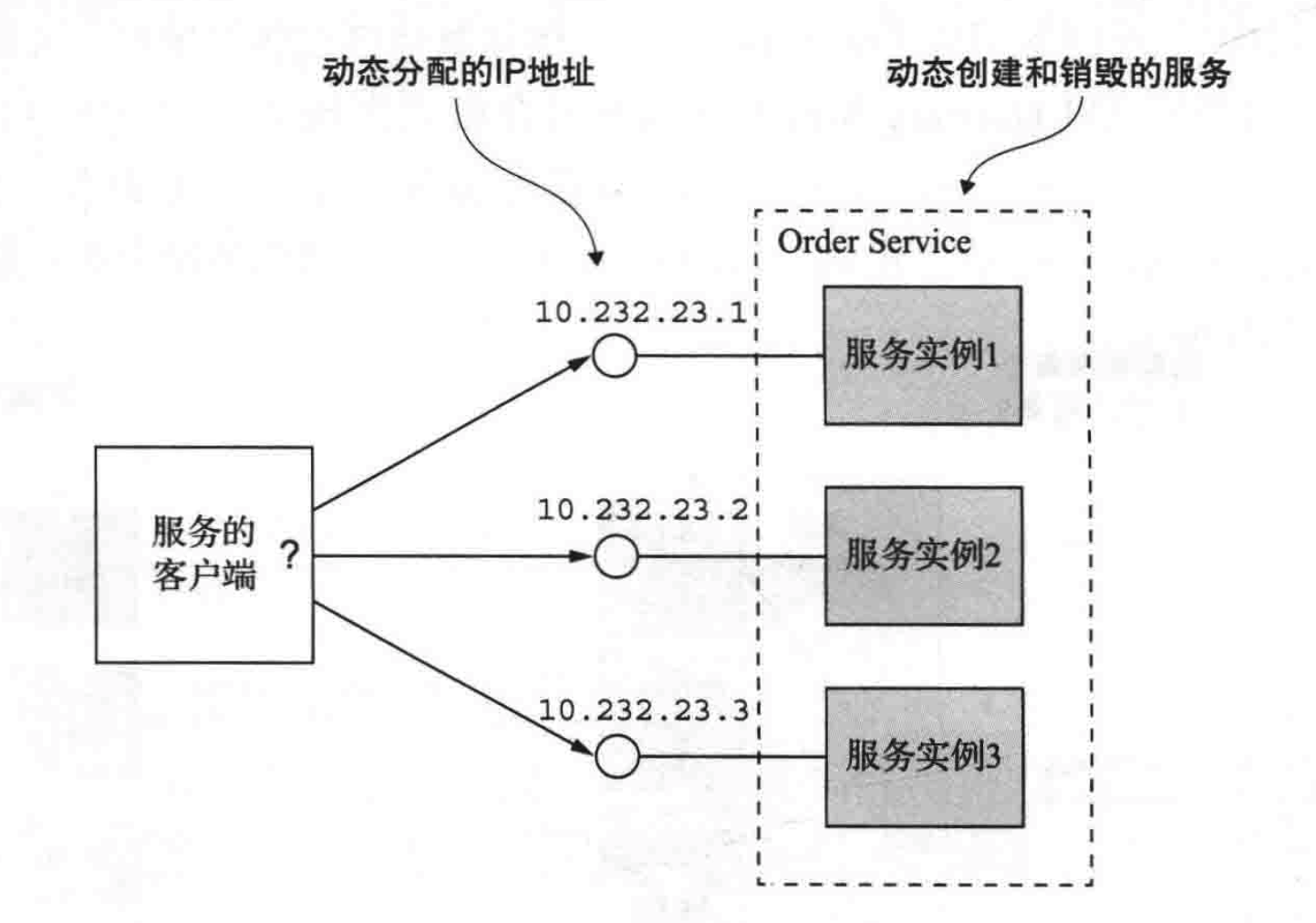
Microservice registration and discovery

C language - Blue Bridge Cup - promised score

一位博士在华为的22年
Pure QT version of Chinese chess: realize two-man, man-machine and network games
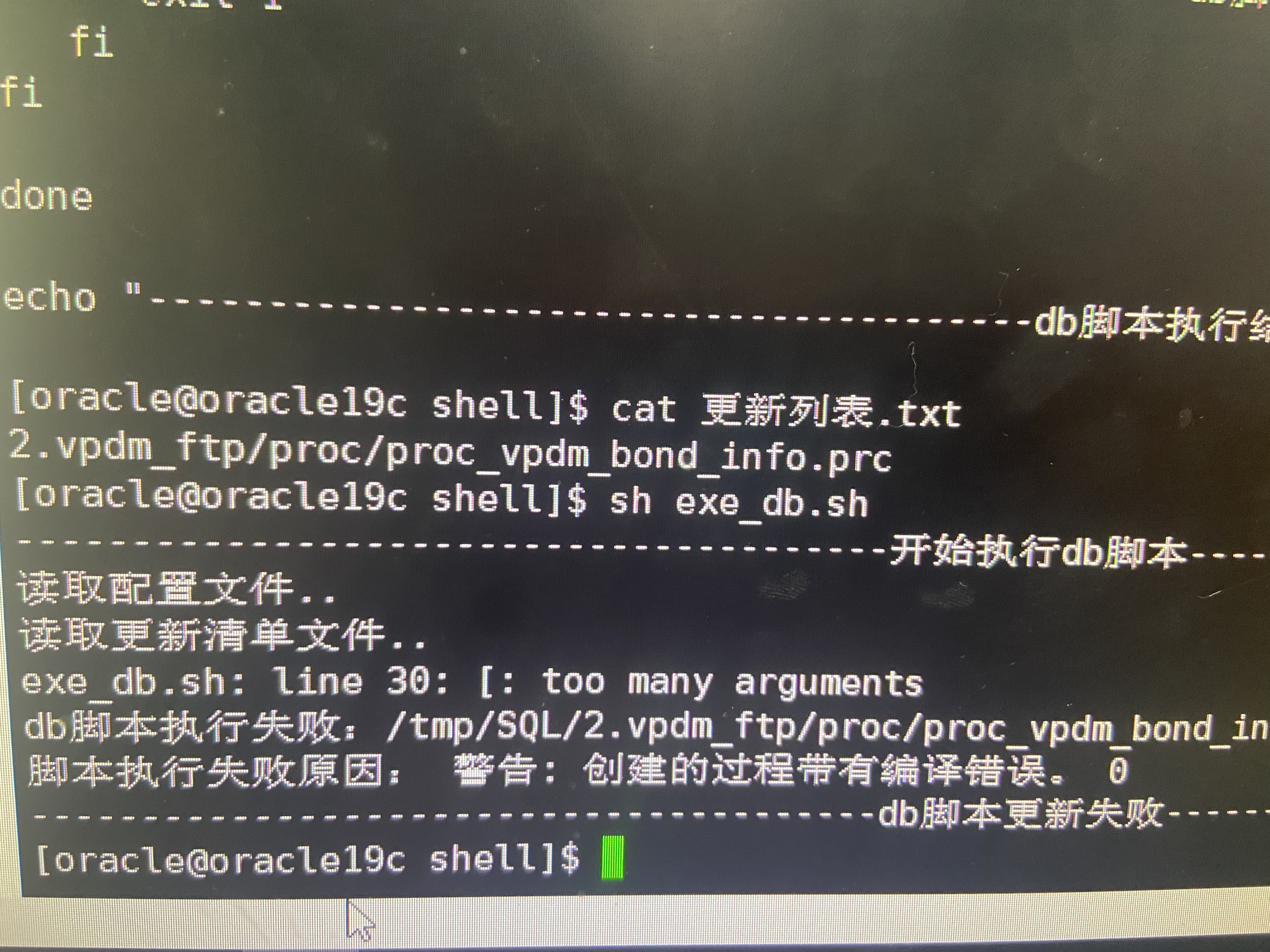
Shell script updates stored procedure to database
解决:AttributeError: ‘str‘ object has no attribute ‘decode‘

Network Security Learning - Web vulnerabilities (Part 1)
The third level of C language punch in

High number_ Vector algebra_ Unit vector_ Angle between vector and coordinate axis
Qt发布exe软件及修改exe应用程序图标
随机推荐
[matlab] access of variables and files
Shell script updates stored procedure to database
Day 50 - install vsftpd on ceontos6.8
Pat 1046 shortest distance (20 points) simulation
JS events (add, delete) and delegates
继承的构造函数
会员积分营销系统操作的时候怎样提升消费者的积极性?
Microsoft speech synthesis assistant v1.3 text to speech tool, real speech AI generator
Is there a case where sqlcdc monitors multiple tables and then associates them to sink to another table? All operations in MySQL
Accident index statistics
【若依(ruoyi)】设置主题样式
Trends in DDoS Attacks
"Hands on learning in depth" Chapter 2 - preparatory knowledge_ 2.3 linear algebra_ Learning thinking and exercise answers
Briefly describe the implementation principle of redis cluster
Building the prototype of library functions -- refer to the manual of wildfire
构建库函数的雏形——参照野火的手册
RobotFramework入门(二)appUI自动化之app启动
RobotFramework入门(三)WebUI自动化之百度搜索
Which ecology is better, such as Mi family, graffiti, hilink, zhiting, etc? Analysis of five mainstream smart brands
Bigder:34/100 面试感觉挺好的,没有收到录取