当前位置:网站首页>[C language] MD5 encryption for account password
[C language] MD5 encryption for account password
2022-07-03 02:47:00 【I&You】
Give the account password MD5 encryption
The source code parsing
//md5 Encrypt user password
UtlMd5_t ctx;
unsigned char serverDigest[16];
utl_md5_init(&ctx);
//md5 initialization
utl_md5_update(&ctx, "admin", strlen("admin"));
// Pass the encrypted information to the initialized MD5 Structure , No return value
// Cross account
utl_md5_update(&ctx, "debug_get_vs_status", strlen("debug_get_vs_status"));
// Transmit control instructions
utl_md5_update(&ctx, "admin123", strlen("admin123"));
// Pass the code
utl_md5_final(&ctx, serverDigest);
// convert to 32 Bit 16 Base string
int i=0;
unsigned char decrypt32[64]={
0};
char temp[8]={
0};
for(i=0;i<16;i++)
{
sprintf(temp,"%02x",serverDigest[i]);// Convert hex to string %x=0x6b ==> %s="6b"
strcat((char *)decrypt32,temp);
}
// Last generated decrypt32 That is to say md5 Encrypted password :"6be7c69c5cdf177753270cf390ef1e90"
// Successfully sent
/*
Content-Length: 133
Content-Type: application/json;charset=utf-8
Connection: close
{
"method": "debug_get_vs_status",
"param": {
},
"user": {
"name": "admin",
"digest": "6be7c69c5cdf177753270cf390ef1e90"
}
} Send successfully length 251!
Response message header :
*******************************
HTTP/1.1 200 OK
Content-Length: 1640
Content-Type: application/json;charset=utf-8
Connection: close
*/
Source download
边栏推荐
- Deep learning: multi-layer perceptron and XOR problem (pytoch Implementation)
- From C to capable -- use the pointer as a function parameter to find out whether the string is a palindrome character
- [flutter] example of asynchronous programming code between future and futurebuilder (futurebuilder constructor setting | handling flutter Chinese garbled | complete code example)
- A2L file parsing based on CAN bus (2)
- Compréhension simple de SVG
- How to return ordered keys after counter counts the quantity
- Interview stereotyped version
- Two dimensional format array format index subscript continuity problem leads to return JSON format problem
- 【翻译】后台项目加入了CNCF孵化器
- [hcia]no.15 communication between VLANs
猜你喜欢
Build a private cloud disk cloudrev

Random shuffle note

Mathematical statistics -- Sampling and sampling distribution

Today, it's time to copy the bottom!

Matlab tips (24) RBF, GRNN, PNN neural network
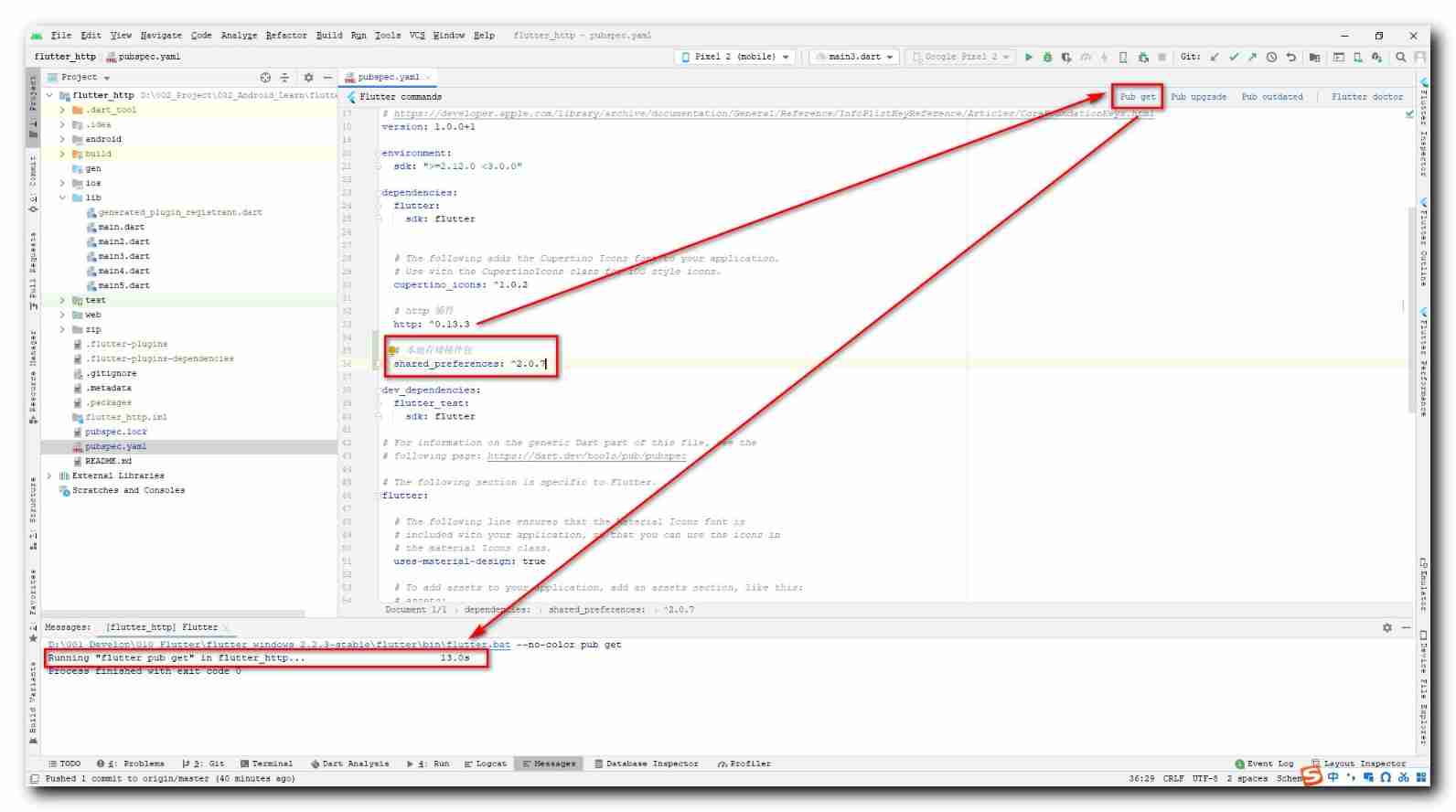
【Flutter】shared_ Preferences local storage (introduction | install the shared_preferences plug-in | use the shared_preferences process)

xiaodi-笔记
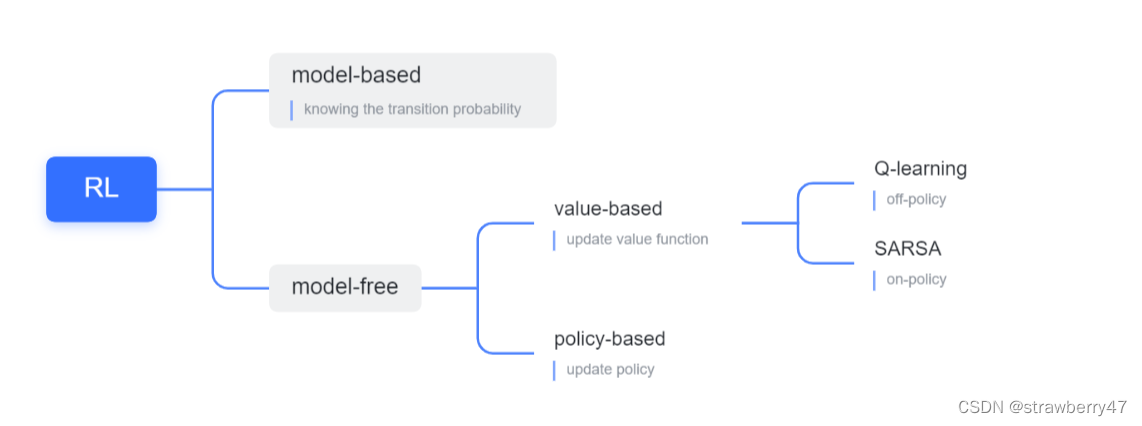
Deep reinforcement learning for intelligent transportation systems: a survey paper reading notes

where 1=1 是什么意思
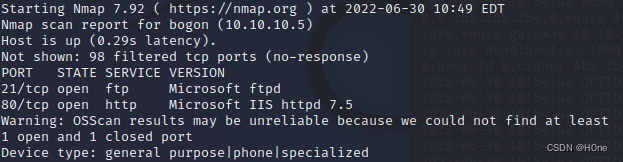
HTB-Devel
随机推荐
Can netstat still play like this?
Le processus de connexion mysql avec docker
The difference between left value and right value in C language
MATLAB小技巧(24)RBF,GRNN,PNN-神经网络
Apple releases MacOS 11.6.4 update: mainly security fixes
The solution of "the required function is not supported" in win10 remote desktop connection is to modify the Registry [easy to understand]
js根据树结构查找某个节点的下面的所有父节点或者子节点
SQL statement
[shutter] banner carousel component (shutter_wiper plug-in | swiper component)
Can netstat still play like this?
ASP. Net core 6 framework unveiling example demonstration [02]: application development based on routing, MVC and grpc
当lambda没有输入时,是何含义?
Check log4j problems using stain analysis
sql server 查詢指定錶的錶結構
Deep learning: multi-layer perceptron and XOR problem (pytoch Implementation)
Deep Reinforcement Learning for Intelligent Transportation Systems: A Survey 论文阅读笔记
[translation] modern application load balancing with centralized control plane
Gbase 8C system table PG_ cast
面试项目技术栈总结
内存泄漏工具VLD安装及使用