当前位置:网站首页>Large scale DDoS attacks take Myanmar offline
Large scale DDoS attacks take Myanmar offline
2022-07-06 02:31:00 【zy18165754120】
At the time of the attack , The country's - Officially known as the Republic of the union of Myanmar - Is for 20 Preparing for the first real election in years .
According to the DDoS/IP Experts Arbor Networks call , since 10 month 25 Since the first attack began on August , Internet connections in Myanmar have been intermittent .
Arbor Networks The chief safety scientist of Craig Labovitz Doctor on his security blog Reported in DDoS attack , He said that the Burmese government had been 2007 The Internet link of the country was cut off in , To suppress the growing political unrest .
He said :“ In the past few days , A rapidly escalating large-scale DDoS Attacked the Ministry of Posts and telecommunications, Myanmar's main Internet provider (MPT), Disrupted most of the network traffic entering and leaving the country .”
according to Labovitz What the doctor said , Although the motive of this attack is not clear , but Twitter And some blogs are full of speculation , From blaming the Burmese government ( stay 11 month 7 Pre emptively destroy Internet connections before the Japanese election ) To the still mysterious motives of external attackers .
Arbor Networks The chief scientist of said , Myanmar Times Reports said , Since last Monday , The attack continued .
“ We estimate Myanmar's DDoS Be situated between 10 To 15 Gbps( Enough to overwhelm the country 45 Mbps T3 Hundreds of times the ground and satellite links )”, He said .
“DDoS Including for MP Address block (203.81.64.0/19、203.81.72.0/24、203.81.81.0/24 and 203.81.82.0/24) Multiple internal IP Dozens of separate attack components of the address ( for example TCP syn、rst flood) ). Attacks also seem to be fairly distributed ,ATLAS The data shows that the attack traffic spans 20 More suppliers , With a wide range of source addresses ”, He added .
according to Labovitz What the doctor said , Although for e-commerce and commercial websites DDoS Attacks are common , But geopolitically motivated large-scale attacks —— Especially needles An attack on the whole country —— Still very rare , But there are Some obvious exceptions .
“ With 10-15 Gbps The speed of , Myanmar's attack is also better than 2007 Georgia (814 Mbps) And Estonian DDoS The attack is much bigger . At the beginning of the year , Myanmar dissident website ( Hosted abroad ) I've also received DDoS attack ,” He said .
边栏推荐
- 有没有sqlcdc监控多张表 再关联后 sink到另外一张表的案例啊?全部在 mysql中操作
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13
- [coppeliasim] efficient conveyor belt
- Initial understanding of pointer variables
- [Wu Enda machine learning] week5 programming assignment EX4 - neural network learning
- ReferenceError: primordials is not defined错误解决
- Ue4- how to make a simple TPS role (II) - realize the basic movement of the role
- Is there a case where sqlcdc monitors multiple tables and then associates them to sink to another table? All operations in MySQL
- LeetCode 103. Binary tree zigzag level order transverse - Binary Tree Series Question 5
- The intelligent material transmission system of the 6th National Games of the Blue Bridge Cup
猜你喜欢
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13](/img/29/49da279efed22706545929157788f0.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13
![[postgraduate entrance examination English] prepare for 2023, learn list5 words](/img/6d/47b853e76d1757fb6e42c2ebba38af.jpg)
[postgraduate entrance examination English] prepare for 2023, learn list5 words
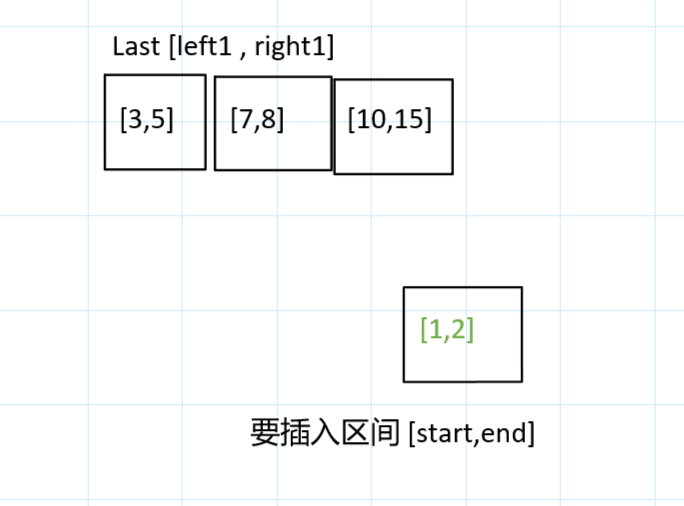
力扣今日题-729. 我的日程安排表 I

Adapter-a technology of adaptive pre training continuous learning
![[Digital IC manual tearing code] Verilog asynchronous reset synchronous release | topic | principle | design | simulation](/img/e4/890e84ab8326e029c4915163904d85.jpg)
[Digital IC manual tearing code] Verilog asynchronous reset synchronous release | topic | principle | design | simulation

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower

2022 eye health exhibition, vision rehabilitation exhibition, optometry equipment exhibition, eye care products exhibition, eye mask Exhibition
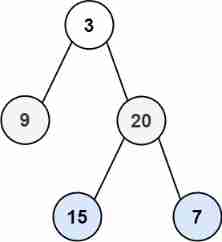
LeetCode 103. Binary tree zigzag level order transverse - Binary Tree Series Question 5
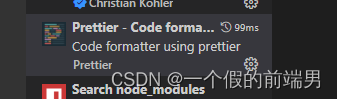
vs code保存时 出现两次格式化
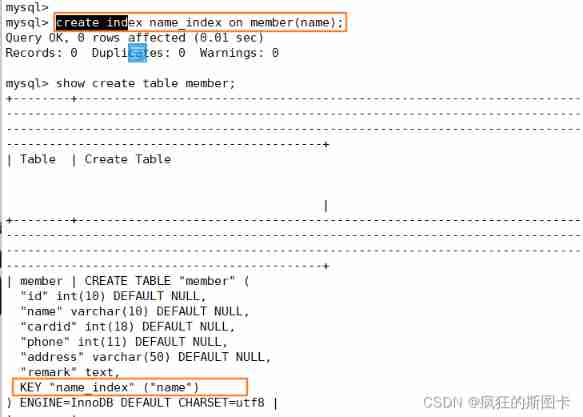
MySQL index
随机推荐
General process of machine learning training and parameter optimization (discussion)
模板_求排列逆序对_基于归并排序
[Digital IC manual tearing code] Verilog asynchronous reset synchronous release | topic | principle | design | simulation
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 6
SSM 程序集
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 24
米家、涂鸦、Hilink、智汀等生态哪家强?5大主流智能品牌分析
继承的构造函数
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11
Multiple solutions to one problem, asp Net core application startup initialization n schemes [Part 1]
2022 edition illustrated network pdf
更换gcc版本后,编译出现make[1]: cc: Command not found
How to check the lock information in gbase 8C database?
Thinking on Architecture Design (under continuous updating)
SSM assembly
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
零基础自学STM32-野火——GPIO复习篇——使用绝对地址操作GPIO
一位博士在华为的22年
[solution] every time idea starts, it will build project