当前位置:网站首页>Chapter 4 - key management and distribution
Chapter 4 - key management and distribution
2022-06-12 07:34:00 【bugmaker.】
- Key lifetime : produce 、 Storage 、 Distribute 、 Use 、 to update 、 revoke 、 The destruction
- Secret key classification
Primary secret key : Encryption and decryption data .
Second level secret key : Secret key encryption secret key , Protect the primary secret key .
Master key : Protect the secondary secret key . - Secret key distribution technology : Direct distribution 、 Key distribution center mode 、Diffie-Hellman Method 、 Hierarchical secret key assignment
- Key distribution center mode
technological process :KDC( Key distribution center ) Share a second level with each user ( Secret key encryption ) Secret key , The user to KDC Request session key ,KDC Generate session key ,KDC Use the secret key to encrypt the session secret key and distribute it to the user
advantage : The user does not save the work key , One report and one secret can be realized
shortcoming : Large traffic , Better identification function is required , To identify KDC And the user - Public key cryptosystem allocates secret keys
(1) towards B Send the generated public key and A The identity of the
(2)B After receiving the message , Generate session key Ks, Add... With public key Pass the secret to A
(3)A Decrypt with the private key to get Ks problem : May be passed off as - Public key management solution
Public key disclosure : No need for confidentiality , The list must be complete
Bind the public key to the identity
Guaranteed by a trusted third party
Other user authentication certificates - Public key certificate : Users exchange their public keys through public key certificates
data structure : User ID 、 Public key 、CA Signature
Certificate type : In terms of use : Signing certificate and encryption certificate
From the perspective of end users : System certificate and user certificate - PKI— Public key infrastructure : An infrastructure established to manage public keys and certificates .
PKI Logical structure of
- Certification body (CA): Be responsible for issuing user secret keys or certificates 、 to update 、 abolish 、 Certification and other management work , Divided into public CA And private CA
- CA function : Issue certificate 、 Annulment certificate 、 Certificate update 、 Certificate authentication and secret key management .
- PKI Architecture of : single CA structure 、 level CA structure 、 cross CA structure
边栏推荐
- Detailed explanation of TF2 command line debugging tool in ROS (parsing + code example + execution logic)
- Non IID data and continuous learning processes in federated learning: a long road ahead
- RT thread studio learning summary
- LeetCode34. 在排序数组中查找元素的第一个和最后一个位置
- 2022年G3锅炉水处理复训题库及答案
- Arrangement of statistical learning knowledge points gradient descent, least square method, Newton method
- Question bank and answers of special operation certificate examination for safety management personnel of hazardous chemical business units in 2022
- VS 2019 MFC 通过ACE引擎连接并访问Access数据库类库封装
- Detailed explanation of coordinate tracking of TF2 operation in ROS (example + code)
- Shortcut key modification of TMUX and VIM
猜你喜欢

Missing getting in online continuous learning with neuron calibration thesis analysis + code reading

Thyristor, it is a very important AC control device

Use of gt911 capacitive touch screen
Non IID data and continuous learning processes in federated learning: a long road ahead

Nine project management issues that PM should understand
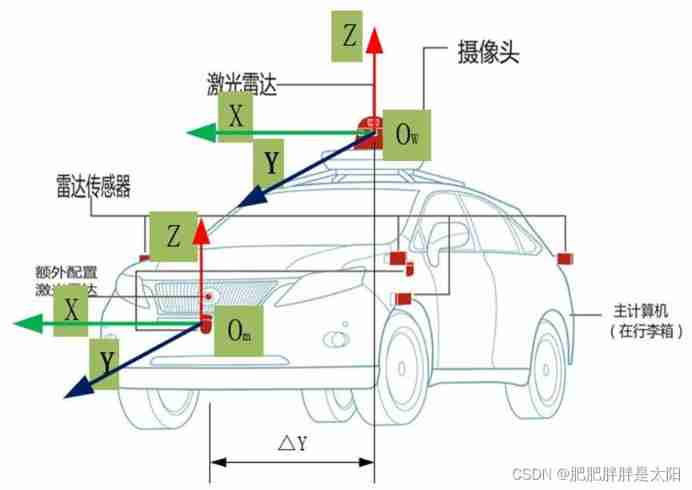
The most understandable explanation of coordinate transformation (push to + diagram)
LED lighting experiment with simulation software proteus

Explain ADC in stm32

2022起重机械指挥考试题模拟考试平台操作
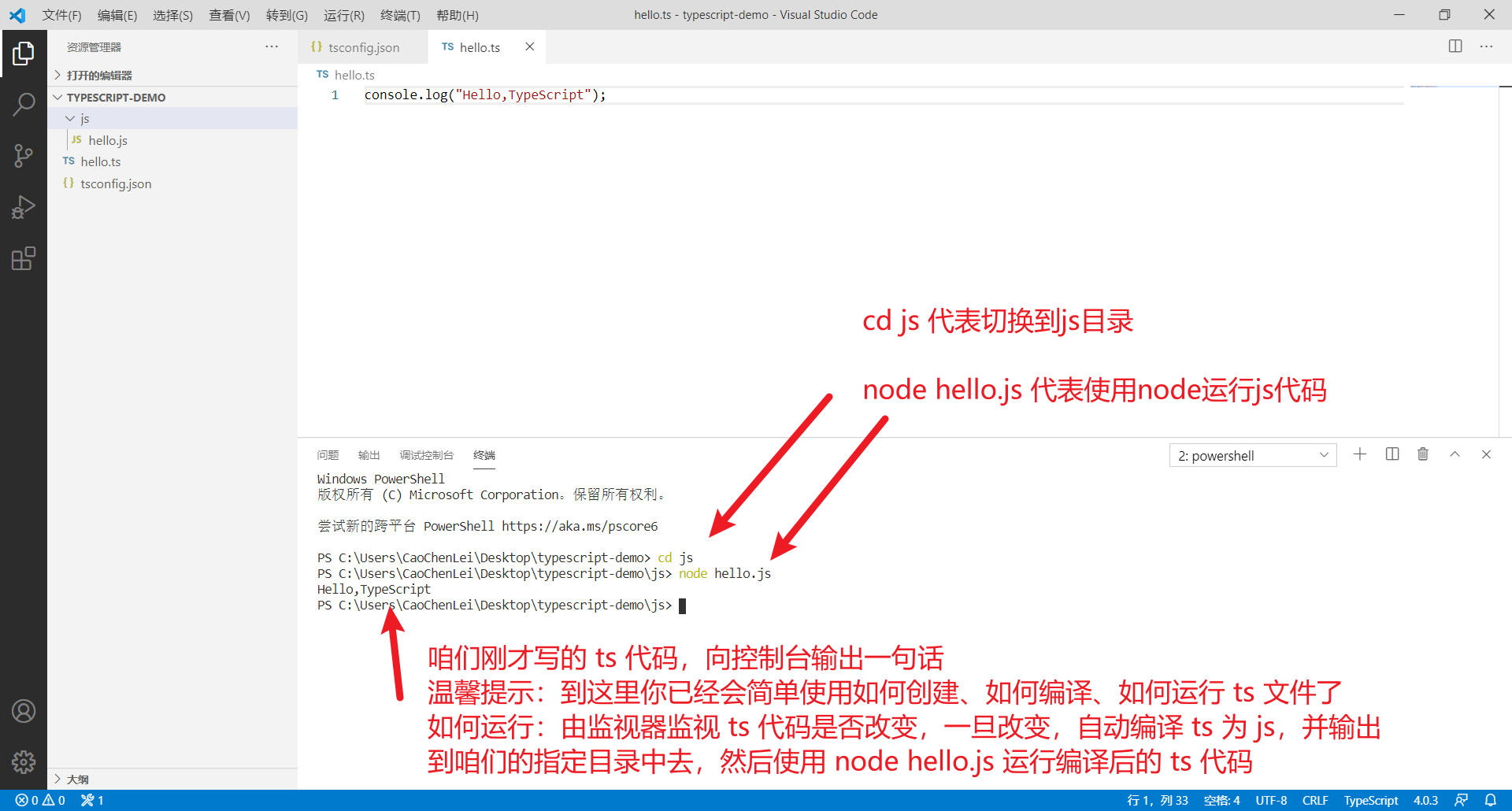
Complete set of typescript Basics
随机推荐
Installation and use of eigen under vs2017
Gd32f4 (5): gd32f450 clock is configured as 200m process analysis
R语言glm函数构建泊松回归模型(possion)、epiDisplay包的poisgof函数对拟合的泊松回归模型进行拟合优度检验、即模型拟合的效果、验证模型是否有过度离散overdispersion
Thyristor, it is a very important AC control device
RT thread studio learning (I) new project
Pyhon的第四天
Learning to continuously learn paper notes + code interpretation
[yolo-v5 learning notes]
2022年危险化学品经营单位安全管理人员特种作业证考试题库及答案
Pyhon的第六天
FCPX插件:简约线条呼出文字标题介绍动画Call Outs With Photo Placeholders for FCPX
Study on display principle of seven segment digital tube
TypeScript基础知识全集
Vs 2019 MFC connects and accesses access database class library encapsulation through ace engine
5 lines of code identify various verification codes
Acwing - 4269 school anniversary
Modelarts培训任务1
Detailed principle of 4.3-inch TFTLCD based on warship V3
[college entrance examination] prospective college students look at it, choose the direction and future, and grasp it by themselves
R语言rnorm函数生成正太分布数据、使用epiDisplay包的summ函数计算向量数据的描述性统计汇总信息并可视化有序点图(名称、有效值个数、均值、中位数、标准差、最大值、最小值)