当前位置:网站首页>Learn JVM garbage collection 05 - root node enumeration, security points, and security zones (hotspot)
Learn JVM garbage collection 05 - root node enumeration, security points, and security zones (hotspot)
2022-07-05 12:15:00 【The king of early rising】
Catalog
What is root node enumeration ?
Root node enumeration
What is root node enumeration ?
Judge the life and death of the object according to the method of reachability analysis , We need to find every starting point . This search process is called root node enumeration .
How it works
up to now , All garbage collector root node enumeration operations must pause the user thread . In other words, it will face similar problems to memory defragmentation “Stop The World” .
Virtual machines have a way to directly get where object references exist . stay HotSpot in , Through a group called OopMap The implementation of the data structure of . Information about references will be recorded here .
safer
OopMap Will make information records at specific locations , These locations are called safety points .
The emergence of safety points , It also gives the thread a proper time to stop , When the program is executed , To execute above the safe point, stop .
selection
If there are many safety points , that OopMap It will be great. , The memory overhead becomes larger .
Few safety points , The waiting time of the garbage collector will be very long .
The selection of safety points requires a standard : With method calls 、 Loop jump 、 Abnormal jump, etc. , Instruction sequence reuse The instructions of the function will produce a safety point .
Why? ?
The selection of safe point location is basically based on “ Whether the program has the characteristics of long execution ” As the standard Make the selected , Because the execution time of every instruction is very short , The program is unlikely to be executed for a long time due to the length of instruction stream “ Long execution ” The most obvious feature of instruction sequence is the reuse of instruction sequence , For example, method calls 、 Loop jump 、 Abnormal jump All belong to instruction sequence reuse , So only instructions with these functions can produce safe points .
Thread the interrupt
Here the so-called thread interrupt , It means that the implementation makes the thread run to the nearest safe point and then stop . There are two ways to achieve
Active interrupt 、 Preemptive interrupt
Active
In a safe place , Set up a Polling flag bit , When interruptions are needed , Set to true .
When a thread executes an instruction to a safe point , The polling flag bit will be checked . If it's true , Then the thread suspends itself , Implementation interrupt .
besides , It also needs to be set on the instructions that need to allocate memory Polling flag bit . Ensure that garbage collection is performed before allocating memory .
Preemptive ( Almost no use )
This is a kind of almost useless .
When the garbage collector raises an interrupt , Stop all threads , See which thread is not on the safe point , Wake up it . Let it run to safety .
The safety area
When the thread is not running ( such as Sleep The state or Blocked state ) when , Can't go to a safe place to hang up . The safe area is to solve this matter .
What is a safe area ?
Refers to in a piece of program code , There are no quoted relationship changes , That is, it is safe to interrupt threads anywhere in this area .
How to solve the problem
When a thread enters a safe zone , Will mark themselves in a safe area . At this point, virtual machines don't have to worry about them during garbage collection .
When you go out, you will ask whether the virtual machine has completed the root node enumeration ( Or other stages in the garbage collection process that need to pause the user thread ). If it's done , The thread continues to execute . If not completed , The program to stop , Wait for instructions to leave the safe area .
That's all for the canto .
Keep early hours , take care . The king of early rising wishes you a thousand miles a day
边栏推荐
- Intern position selection and simplified career development planning in Internet companies
- Why learn harmonyos and how to get started quickly?
- Seven polymorphisms
- Application of a class of identities (vandermond convolution and hypergeometric functions)
- Simply solve the problem that the node in the redis cluster cannot read data (error) moved
- HiEngine:可媲美本地的云原生内存数据库引擎
- 强化学习-学习笔记3 | 策略学习
- Reinforcement learning - learning notes 3 | strategic learning
- JS for loop number exception
- 跨平台(32bit和64bit)的 printf 格式符 %lld 输出64位的解决方式
猜你喜欢
Redis master-slave mode
Pytorch MLP

Pytorch weight decay and dropout
MySQL transaction
ABAP table lookup program

What is digital existence? Digital transformation starts with digital existence
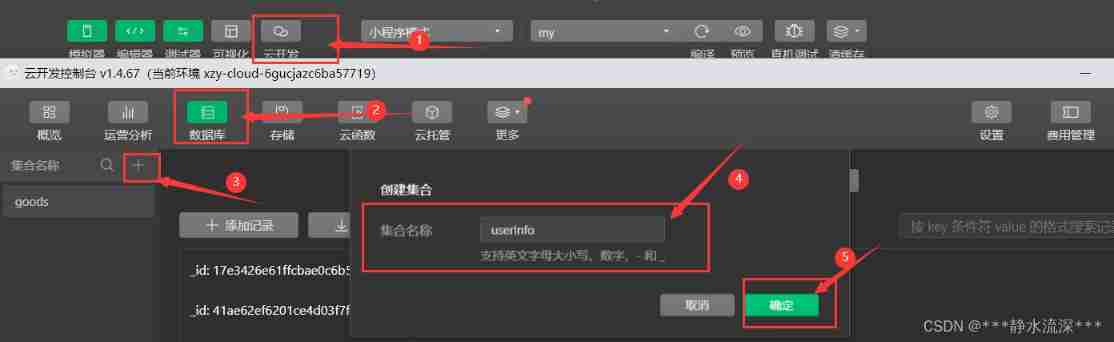
Simple production of wechat applet cloud development authorization login
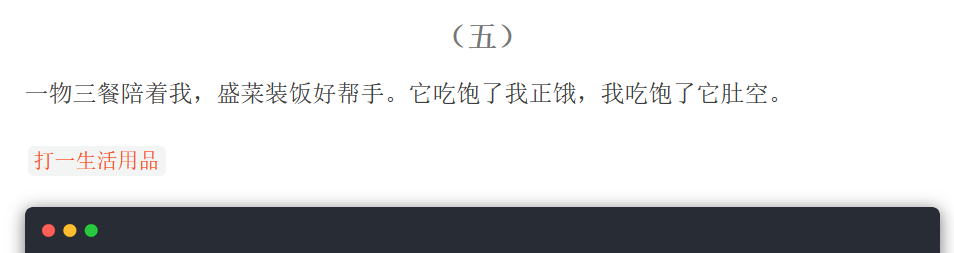
Riddle 1
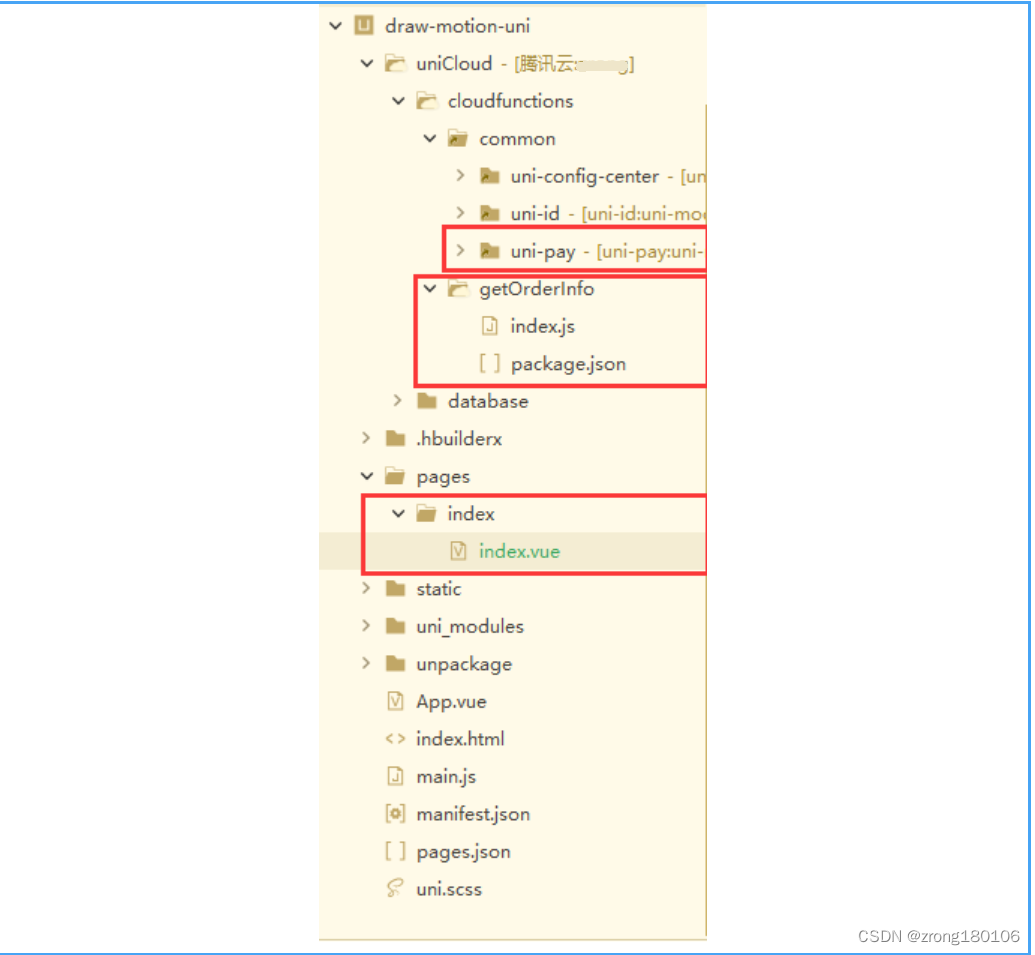
Uniapp + unicloud + Unipay realize wechat applet payment function
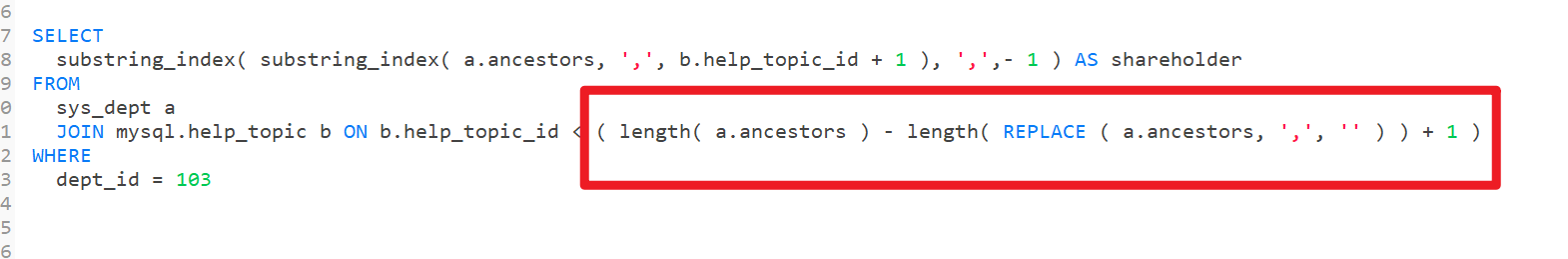
MySQL splits strings for conditional queries
随机推荐
[HDU 2096] 小明A+B
Vscode shortcut key
GPS數據格式轉換[通俗易懂]
Error modulenotfounderror: no module named 'cv2 aruco‘
Get data from the database when using JMeter for database assertion
byte2String、string2Byte
Deep discussion on the decoding of sent protocol
A guide to threaded and asynchronous UI development in the "quick start fluent Development Series tutorials"
Linux Installation and deployment lamp (apache+mysql+php)
Ncp1342 chip substitute pn8213 65W gallium nitride charger scheme
Understand kotlin from the perspective of an architect
语义分割实验:Unet网络/MSRC2数据集
Course design of compilation principle --- formula calculator (a simple calculator with interface developed based on QT)
Select drop-down box realizes three-level linkage of provinces and cities in China
vscode快捷键
Swift - add navigation bar
Video networkState 属性
Redis cluster (master-slave) brain crack and solution
信息服务器怎么恢复,服务器数据恢复怎么弄[通俗易懂]
Riddle 1